Threat Detection Marketplace Version 4.13.0 Is Released
On June 30, 2021, we released Threat Detection Marketplace version 4.13.0 to add new cutting-edge features and polish the existing functionality of our Detection as Code platform. With this latest update, we introduce the support for the new Splunk Alerts content type, provide important content quality enhancements, improve the Content Preview page functionality, and proceed with Cyber Library enrichment alongside other platform upgrades.
Support for Splunk Alerts
At SOC Prime, we are continuously broadening the support for various SIEM, EDR, and NTDR language formats to make sure our Detection as Code platform delivers cross-tool content tailored to the majority of security solutions. With this latest release, we’ve added the support for Splunk Alerts in addition to Queries. The Uncoder.IO online Sigma rule converter now supports Splunk Alerts and allows generating translations to this language format.
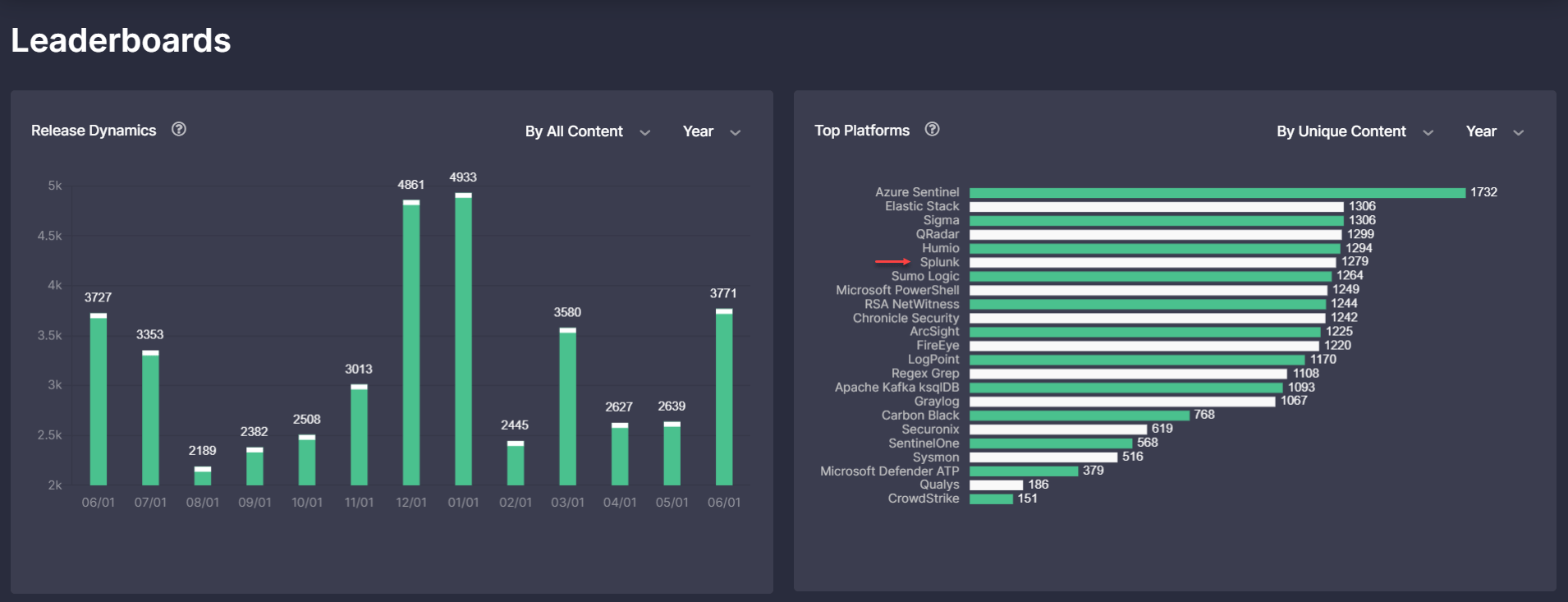
Threat Detection Marketplace customers leveraging Splunk can now streamline their search experience by applying this content type from the Platform filter options.
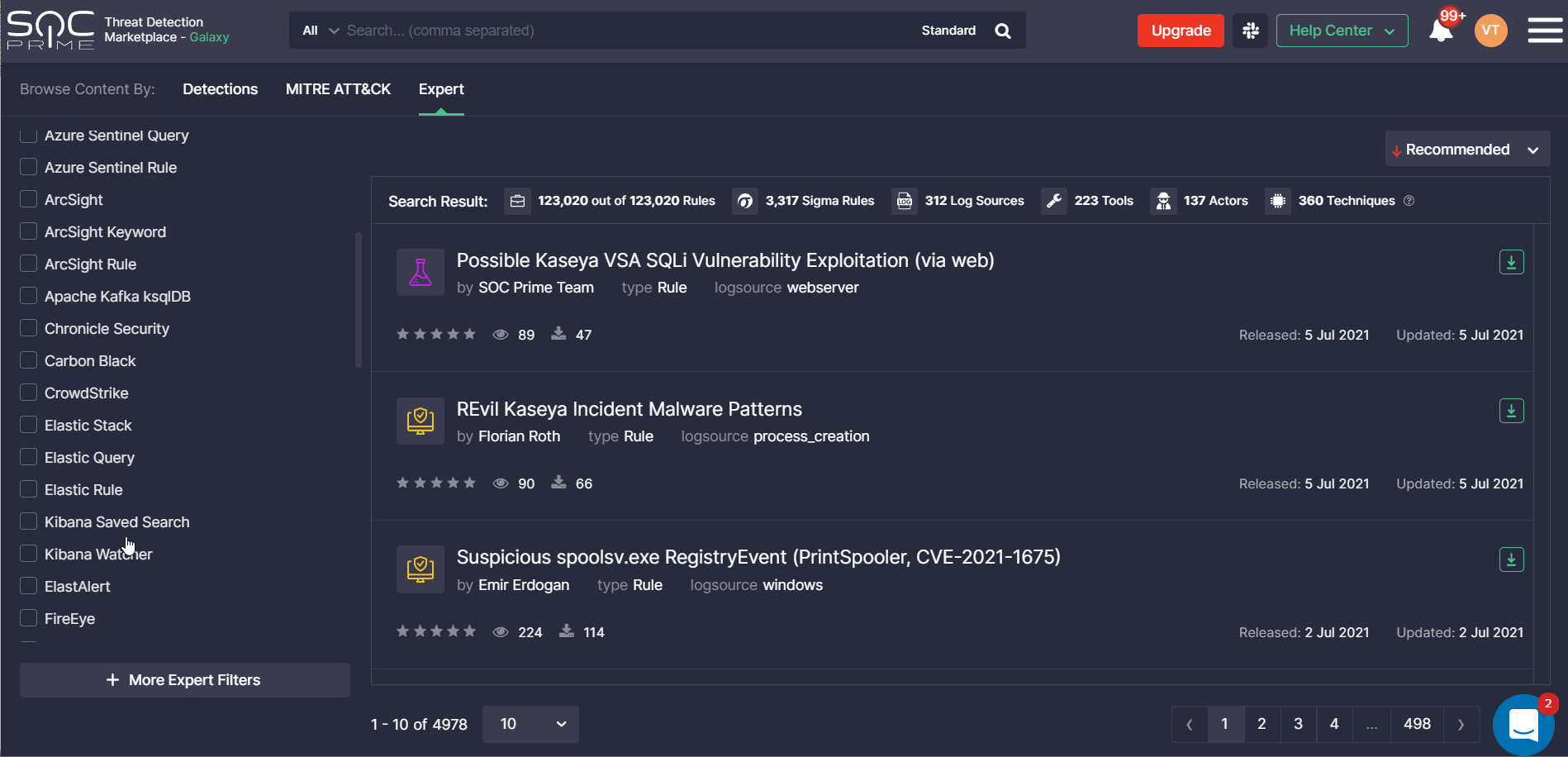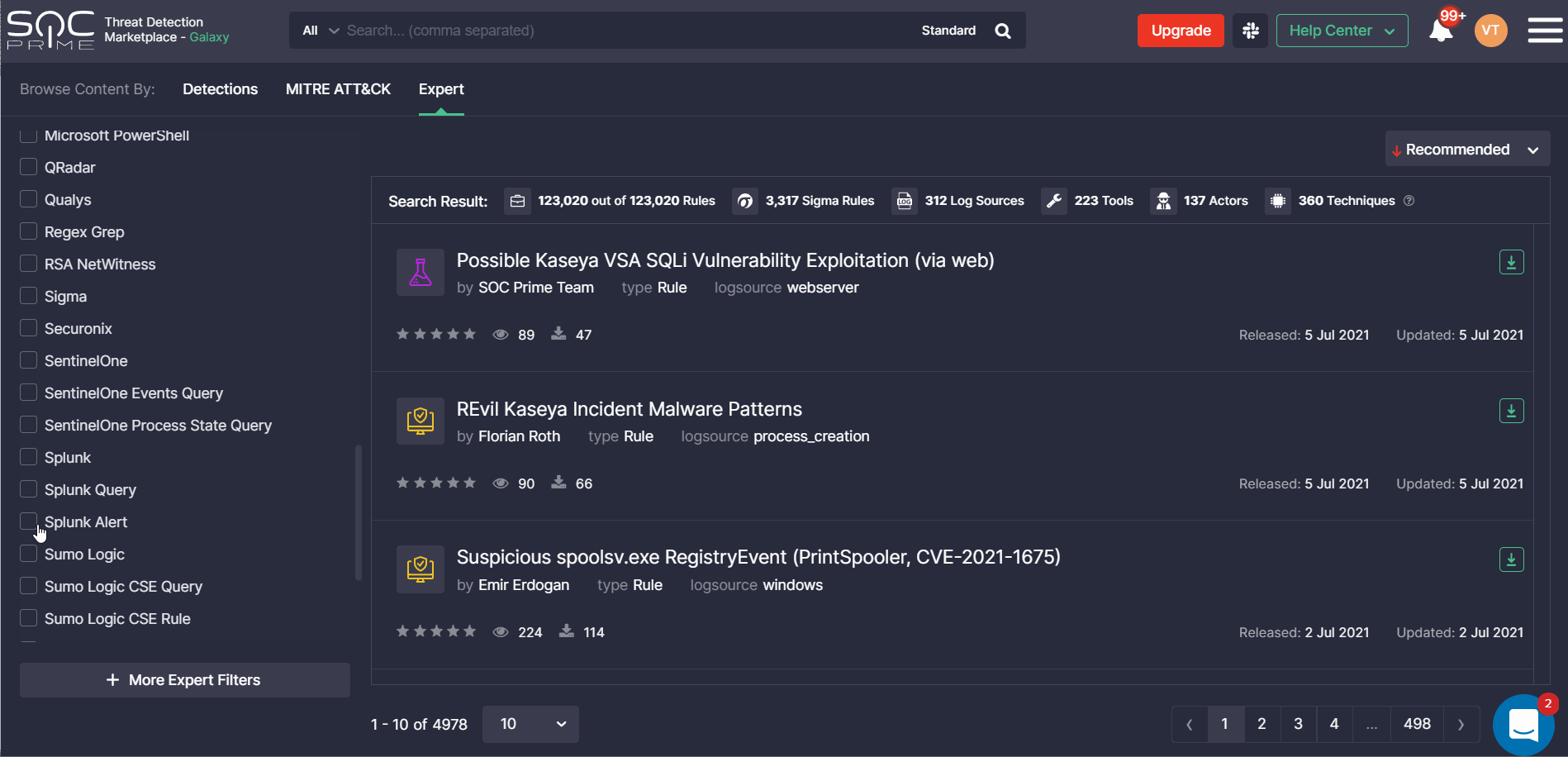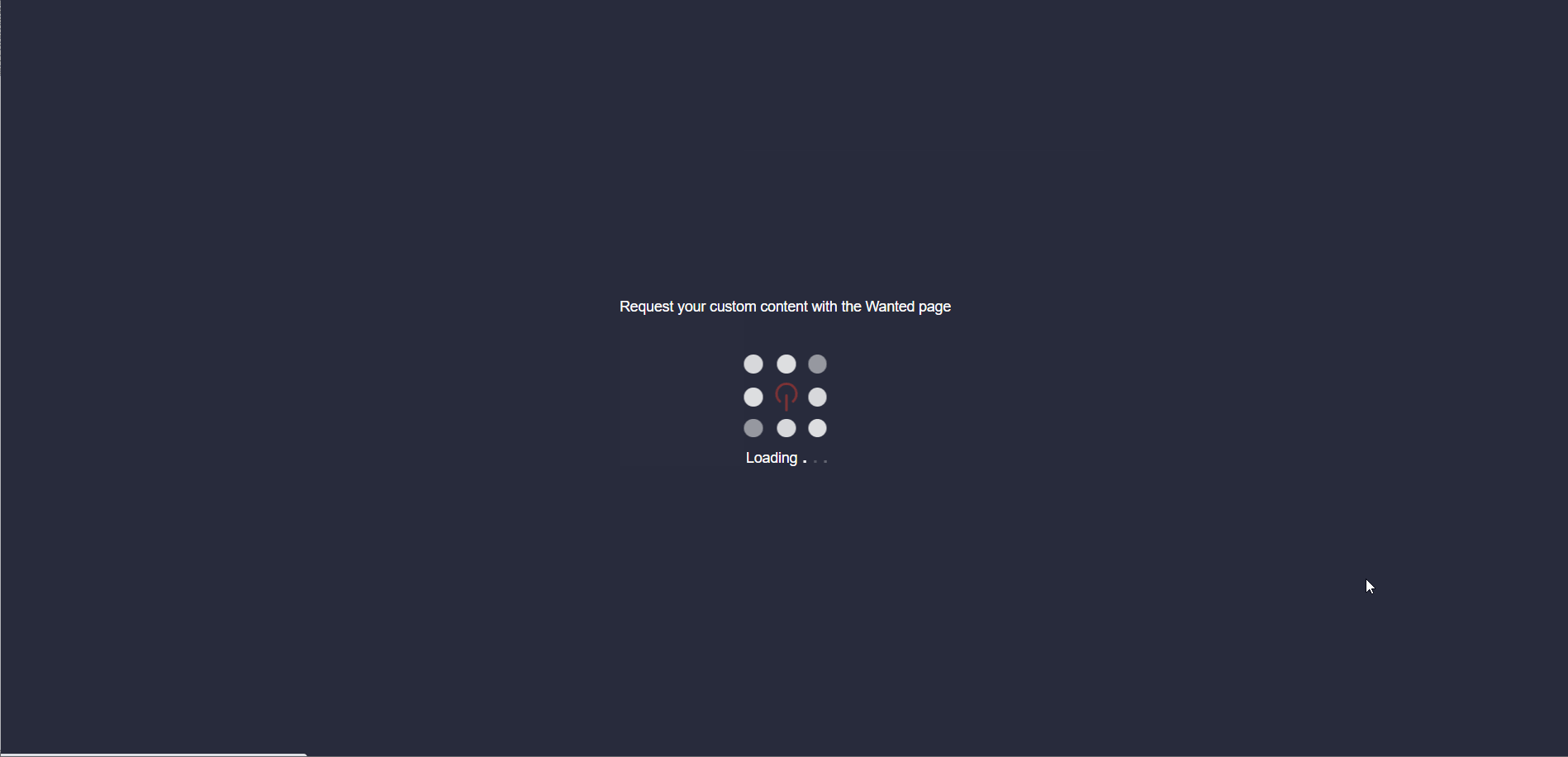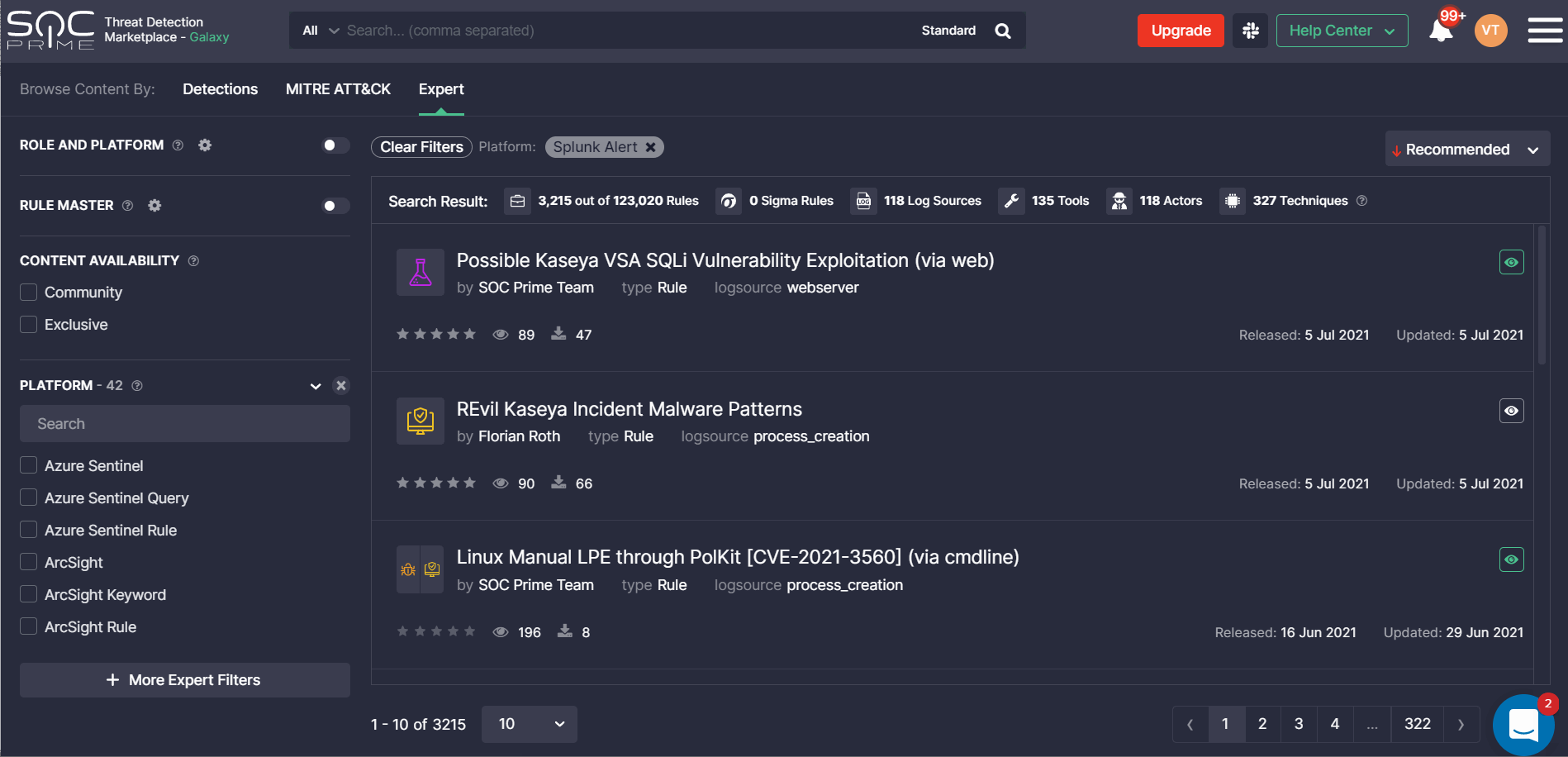
When drilling down to a certain rule from the filtered list, security performers will see at once the Splunk Alert tab selected with the source code converted to this language format.
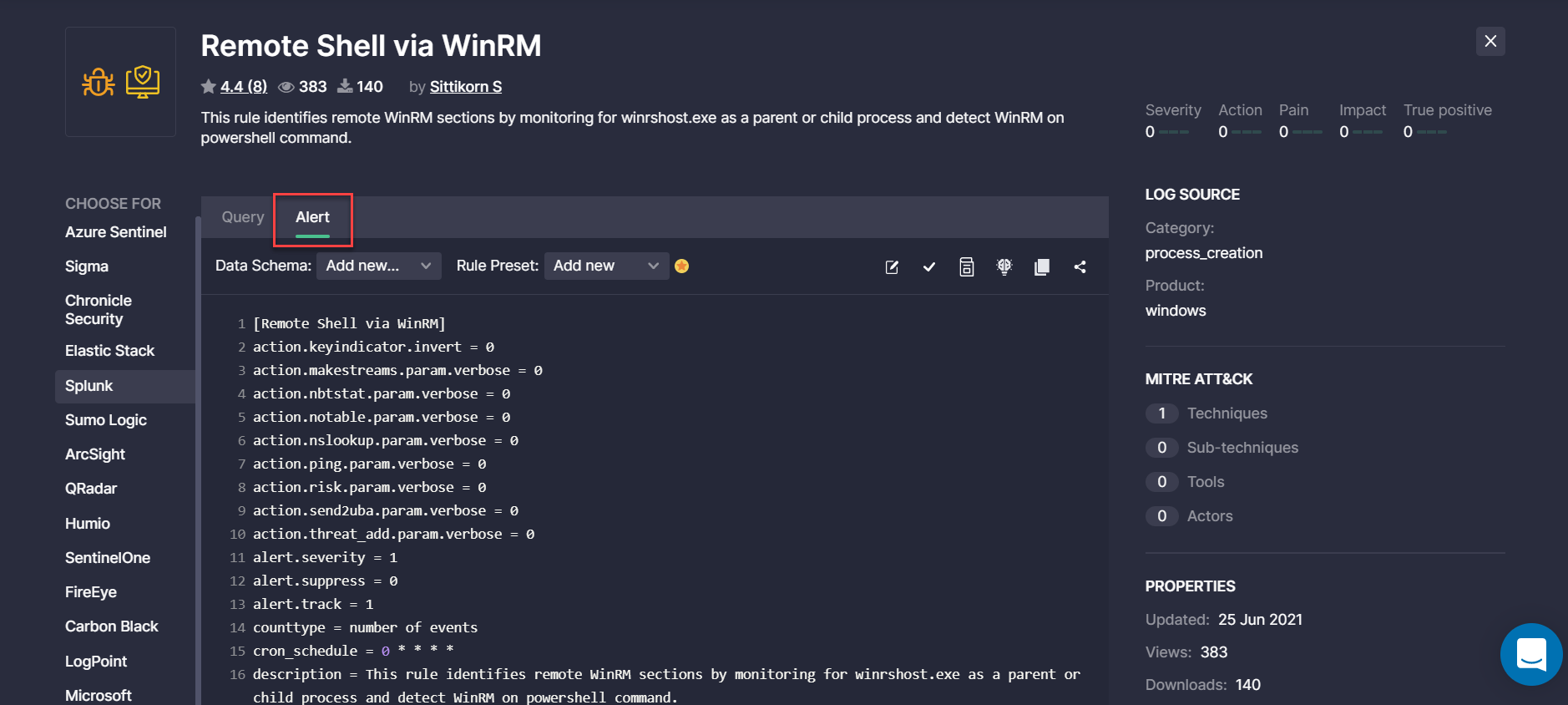
The statistics on available translations over the selected time period on the Top Platforms bar chart of the Leaderborads page now display the total number of Splunk content, including Queries and the recently added Alerts.
Content Quality Enhancements
At SOC Prime, we’re constantly striving to improve the content quality when translating Sigma behavior-based detections to various SIEM, EDR, and NTDR language formats.
Alternative Translation Improvements for Elastic
To enable a seamless cross-platform threat detection experience, we’ve recently resolved alternative translation issues on the back end related to the Elastic Stack language format, more specifically addressing the following options:
- ci-winlogbeat6
- Ci-winlogbeat7
As part of these improvements, we’ve also resolved the issue with a lack of case-insensitive keywords for the Elastic Stack translations.
Google Chronicle Mapping Improvements
With this Threat Detection Marketplace release, we’ve made the corresponding mapping improvements to Google Chronicle translations, more specifically:
- Added a new mapping string: TargetData: target.registry.registry_value_data
- Replaced the selectiontarget.file.hash.target.file.sha1 field with another custom field — selection.target.file.sha1 to ensure smooth translation generation
Humio Translation Issue
With this latest platform update, we’ve improved the logic for Humio translations that contain multiple boolean values in brackets. This issue affected Sigma rules containing complex detection logic based on multiple operators, such as condition: a AND (b or c) when converted to the Humio language format with brackets in the translation syntax.
Functionality Improvements
To enable the most intuitive threat detection experience, we continuously master Threat Detection Marketplace and proceed with the feature enhancements. The latest version 4.13.0 provides major updates to the Content Preview page and Cyber Library.
Content Preview Page Updates
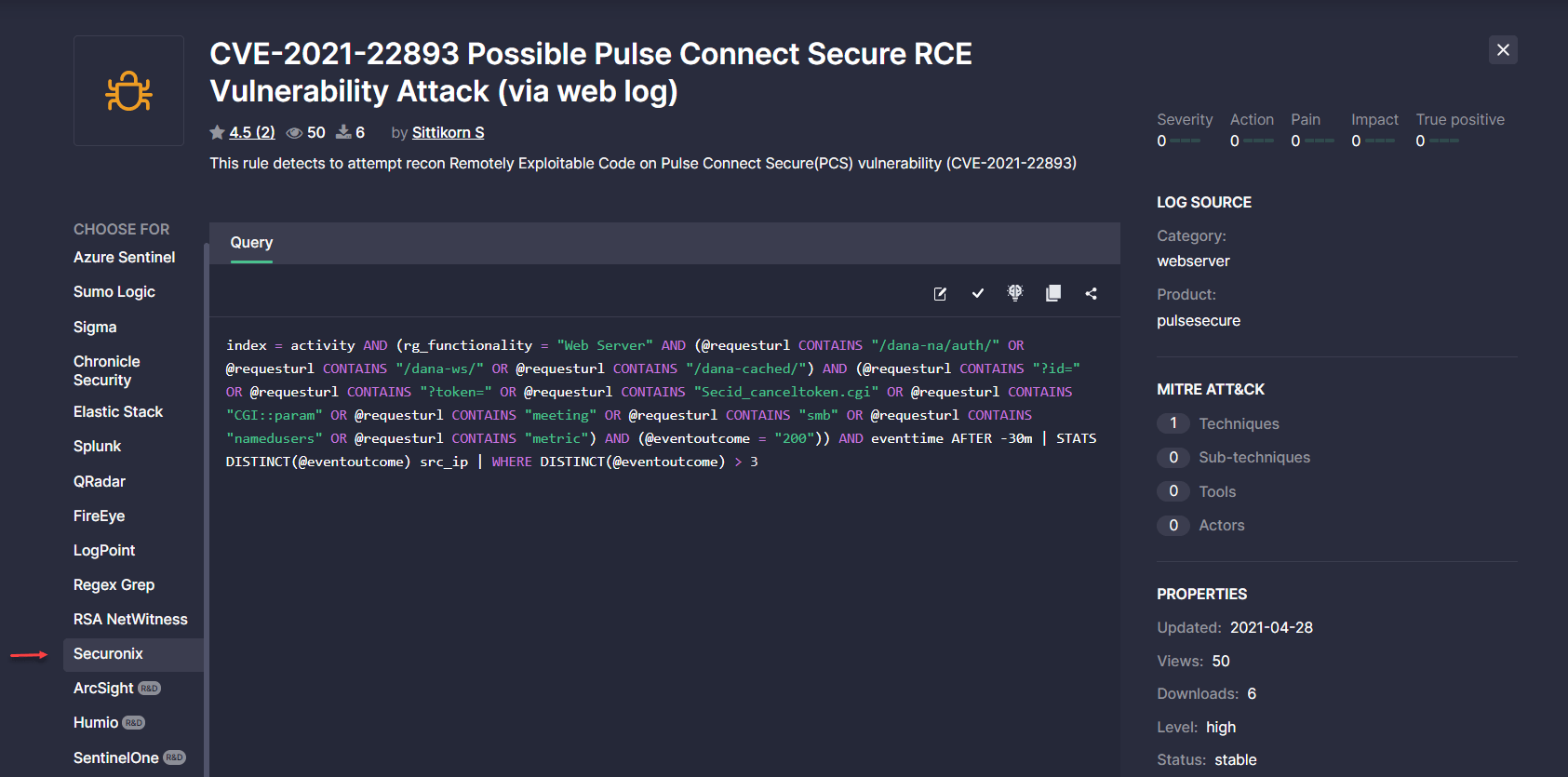
During the latest Threat Detection Marketplace upgrade, we’ve added the ability to show the platform selected in the user profile Role and Platform section as well as after filtering by the certain security solution on the Content page. These enhancements enable security performers to see the corresponding platform selected once they land at the content item page.
Before this update, if the selected platform was at the end of the Choose for left-hand-side menu, it was hidden by the Show More button. Now the Choose for menu appears in the expanded view mode for such cases, and the auto-scrolling functionality enables getting to the platform of the user choice on the fly.
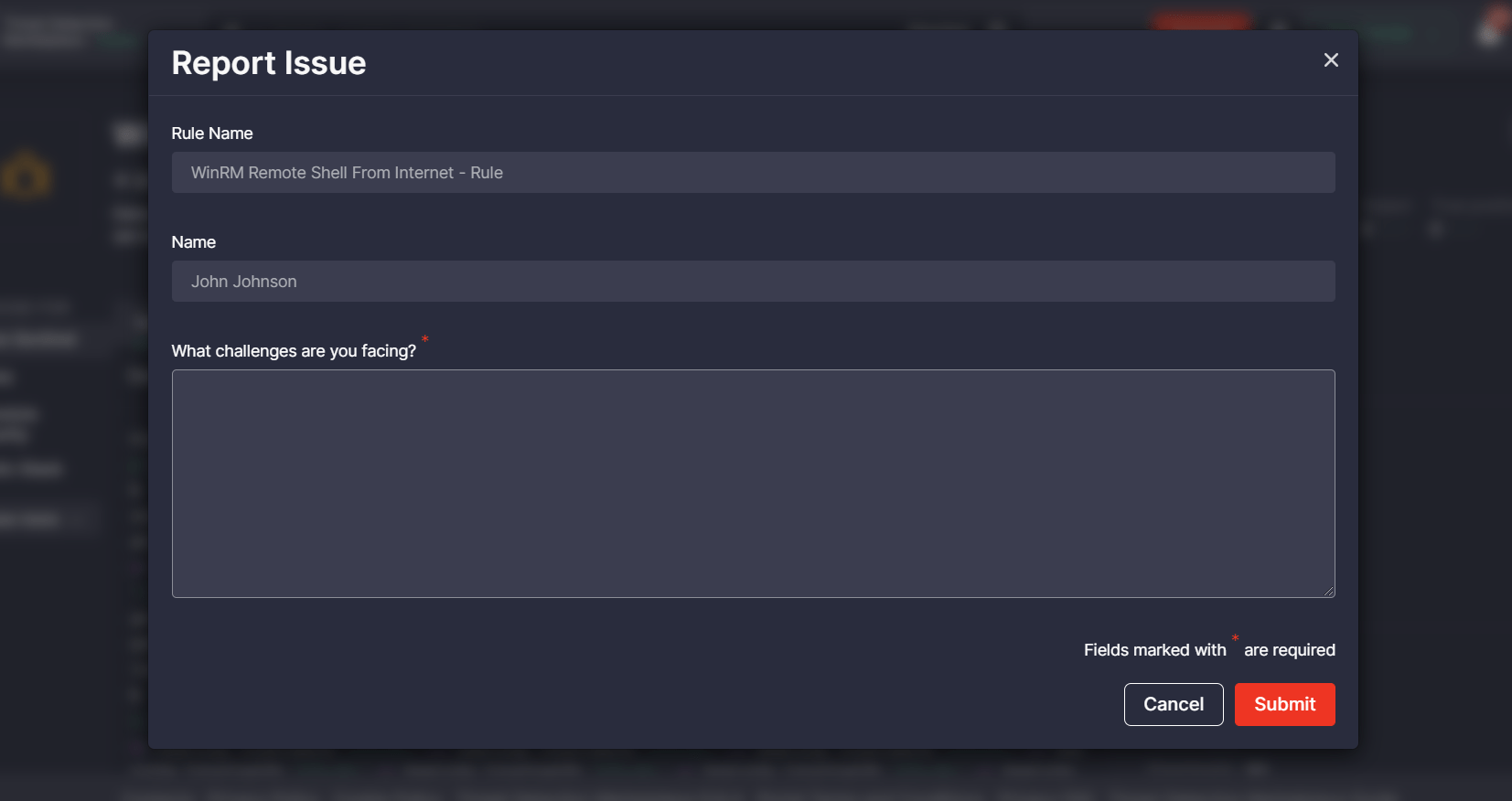
Additionally, with this release, we’ve made localization improvements to the user-facing functionality on the content item page that allows submitting an issue related to the viewed content available for the selected language format. Security performers facing a certain issue with such content items can now click the renamed Report Issue button under the source code window. In line with the button localization improvements, we’ve also changed the following:
- Hint next to the button prompting a user to report an issue
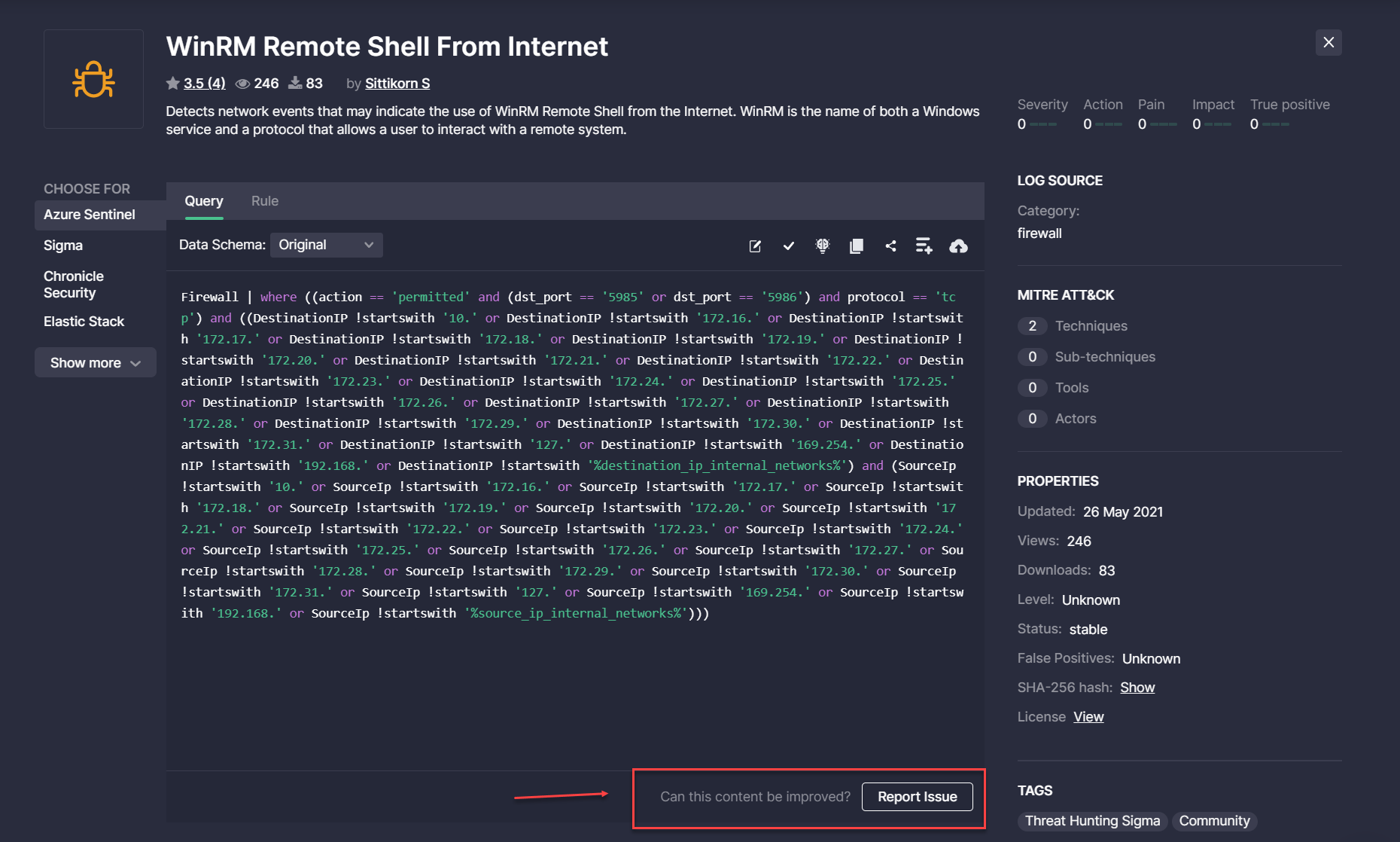
- Localizations on the Report Issue pop-up displayed when clicking the corresponding button
Link to Cyber Library in Threat Detection Marketplace and Back to Platform
To enable seamless transition between Threat Detection Marketplace and Cyber Library, we’ve implemented crosslinking for the platform navigation panels. Security performers can now go to the SOC Prime’s educational space with a single click from the Threat Detection Marketplace Help Center menu and then seamlessly return to the Detection as Code platform by clicking the Threat Detection Marketplace button right at their fingertips.
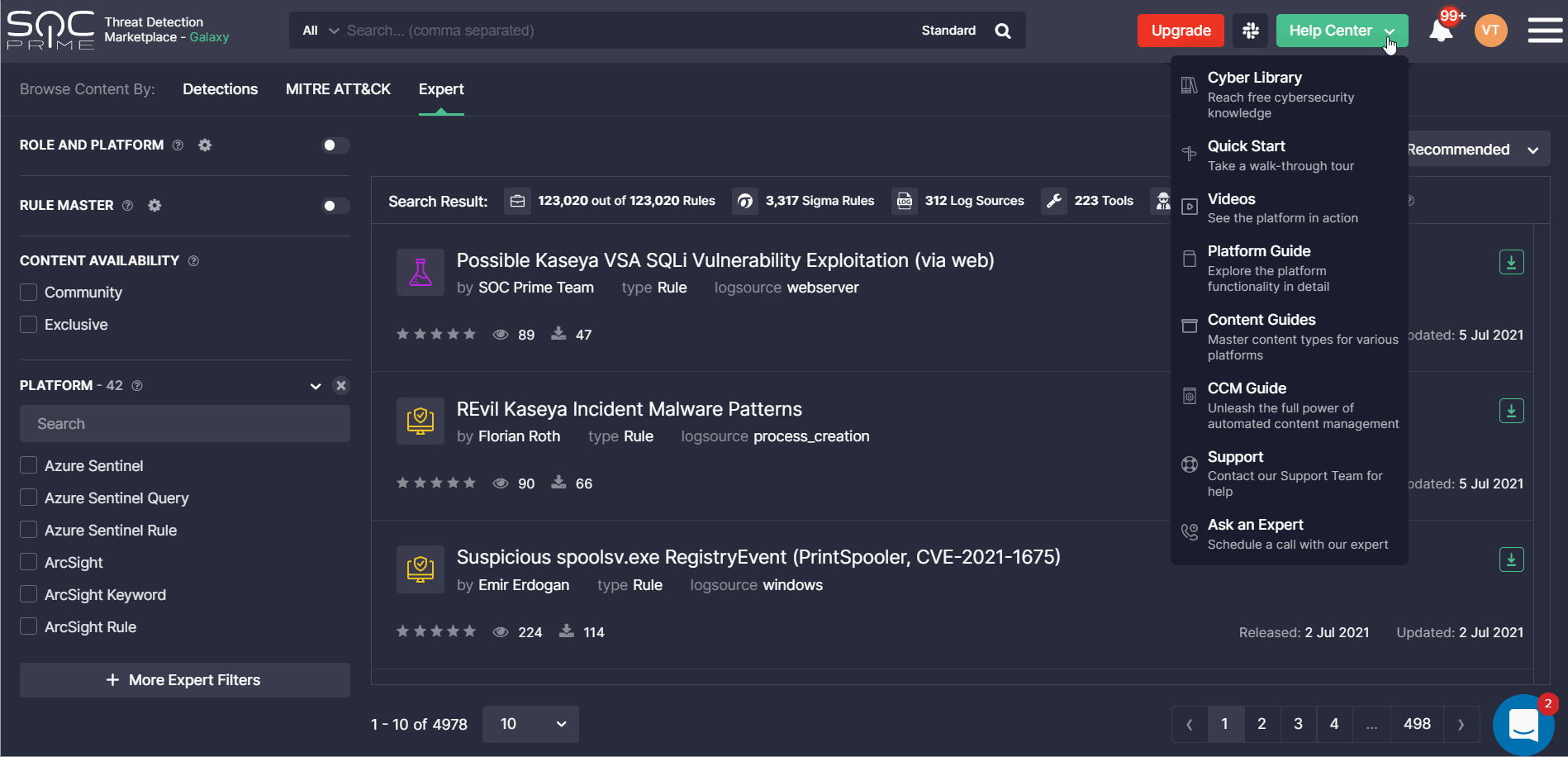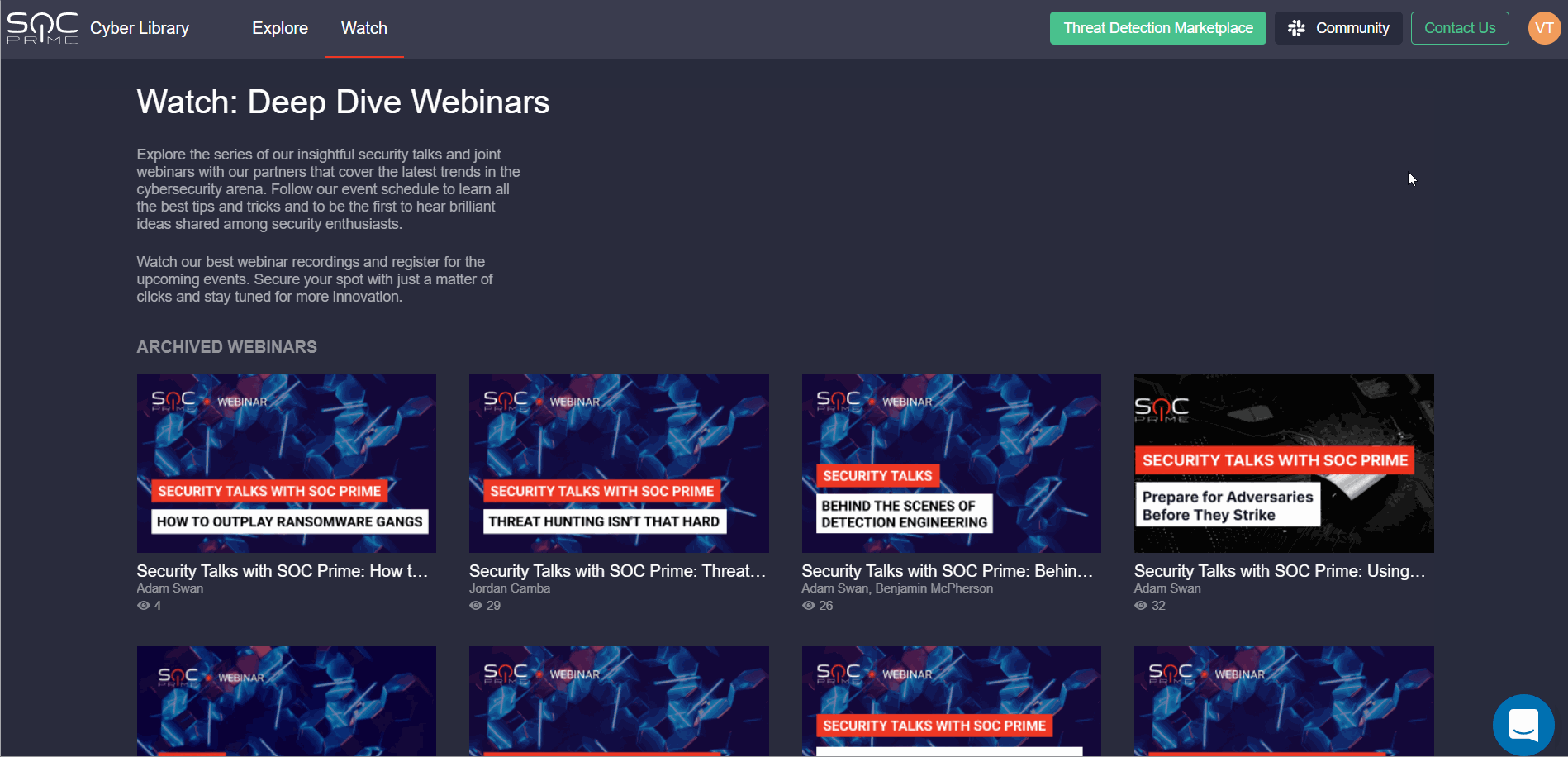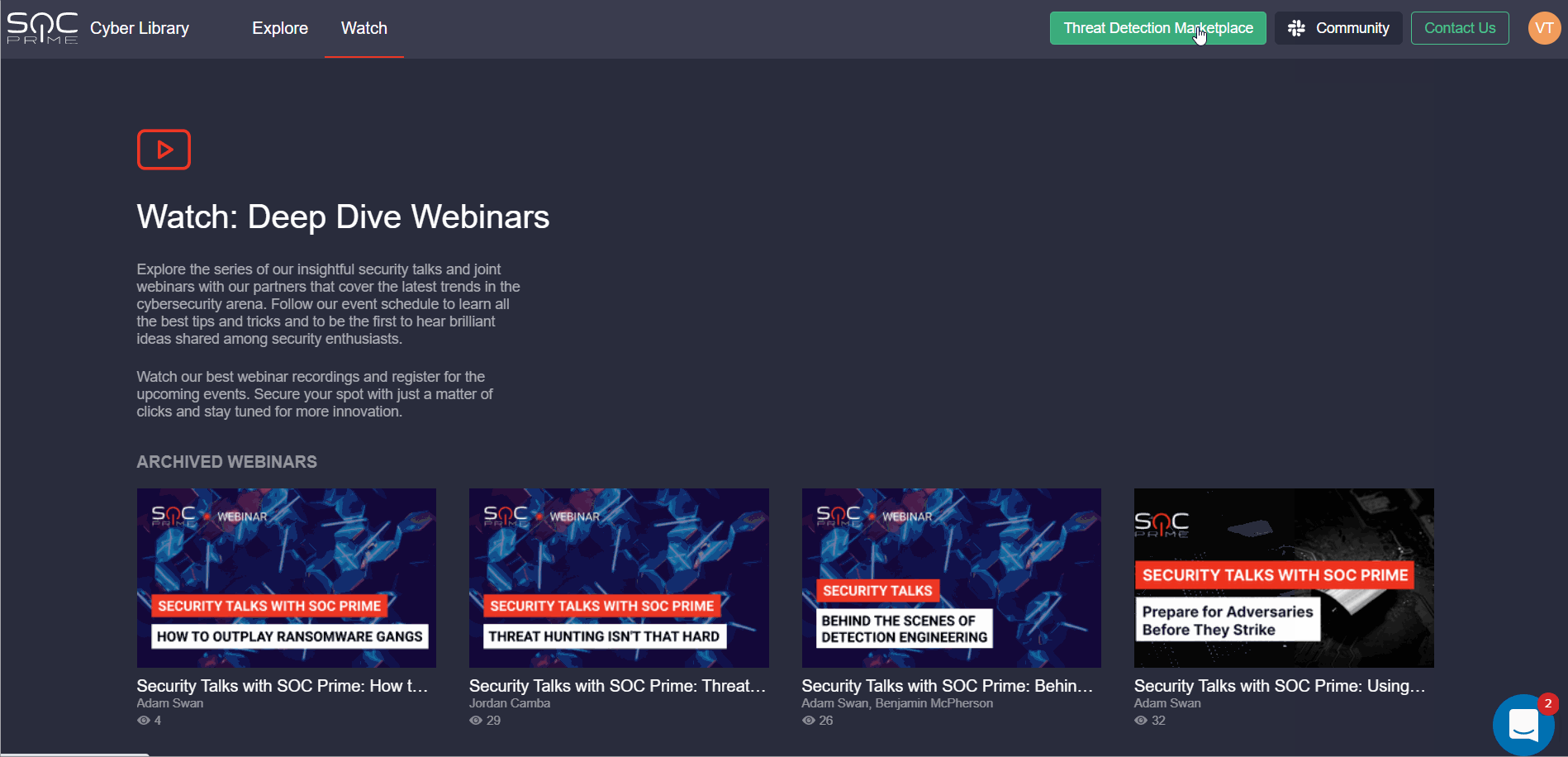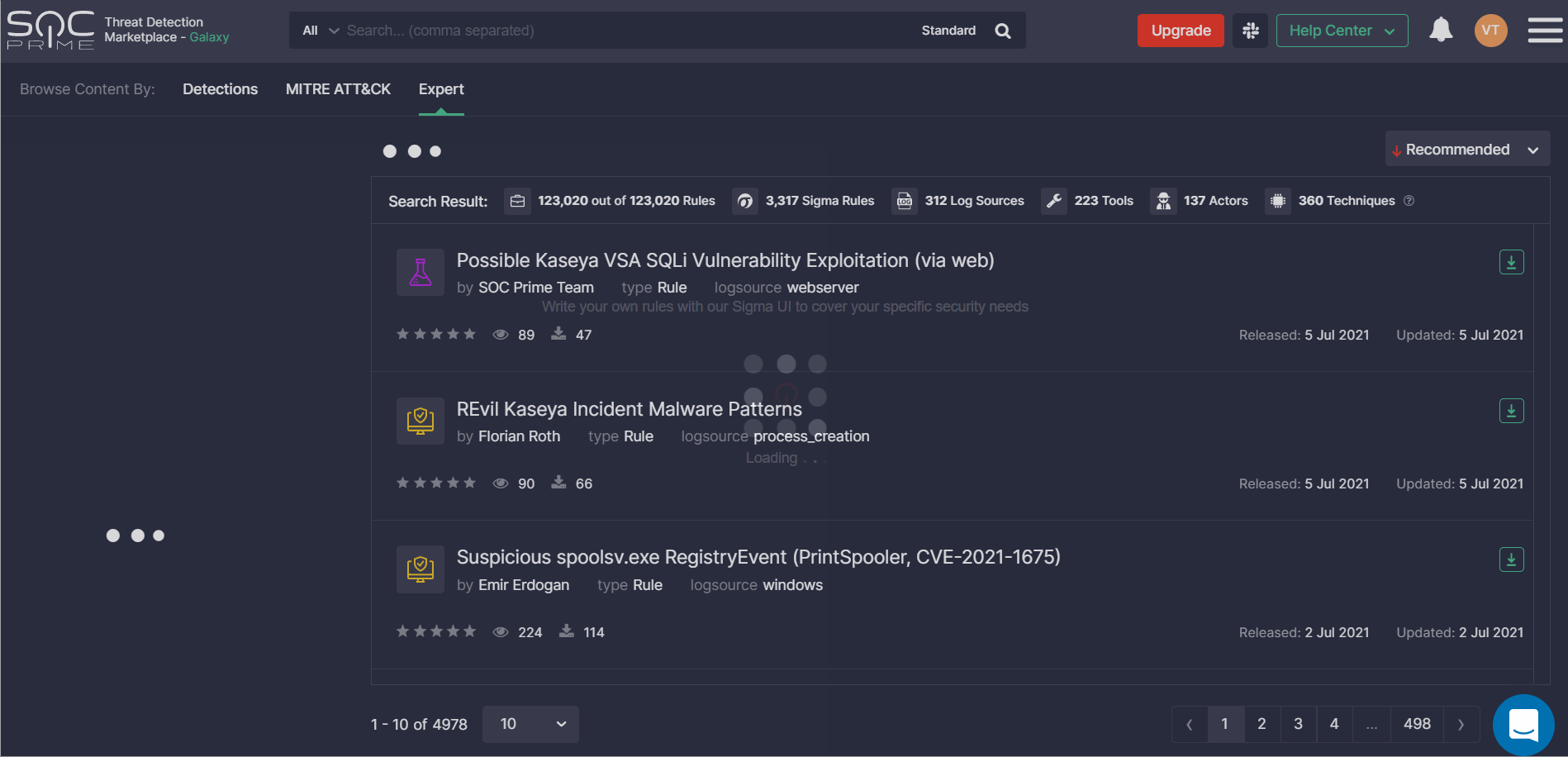
The transition between Threat Detection Marketplace and Cyber Library doesn’t require filling in any additional credentials making the user experience even simpler and more streamlined.
Cyber Library Enrichment: How-to Guide for QRadar Rule Packs
To deliver the most personalized experience to our QRadar customers, we’ve enriched our Cyber Library with a new insightful how-to guide on installing and configuring QRadar Rule Packs in the customer’s environment. Cyber Library users can find this guide in the Explore section by selecting QRadar from the list of available platforms.
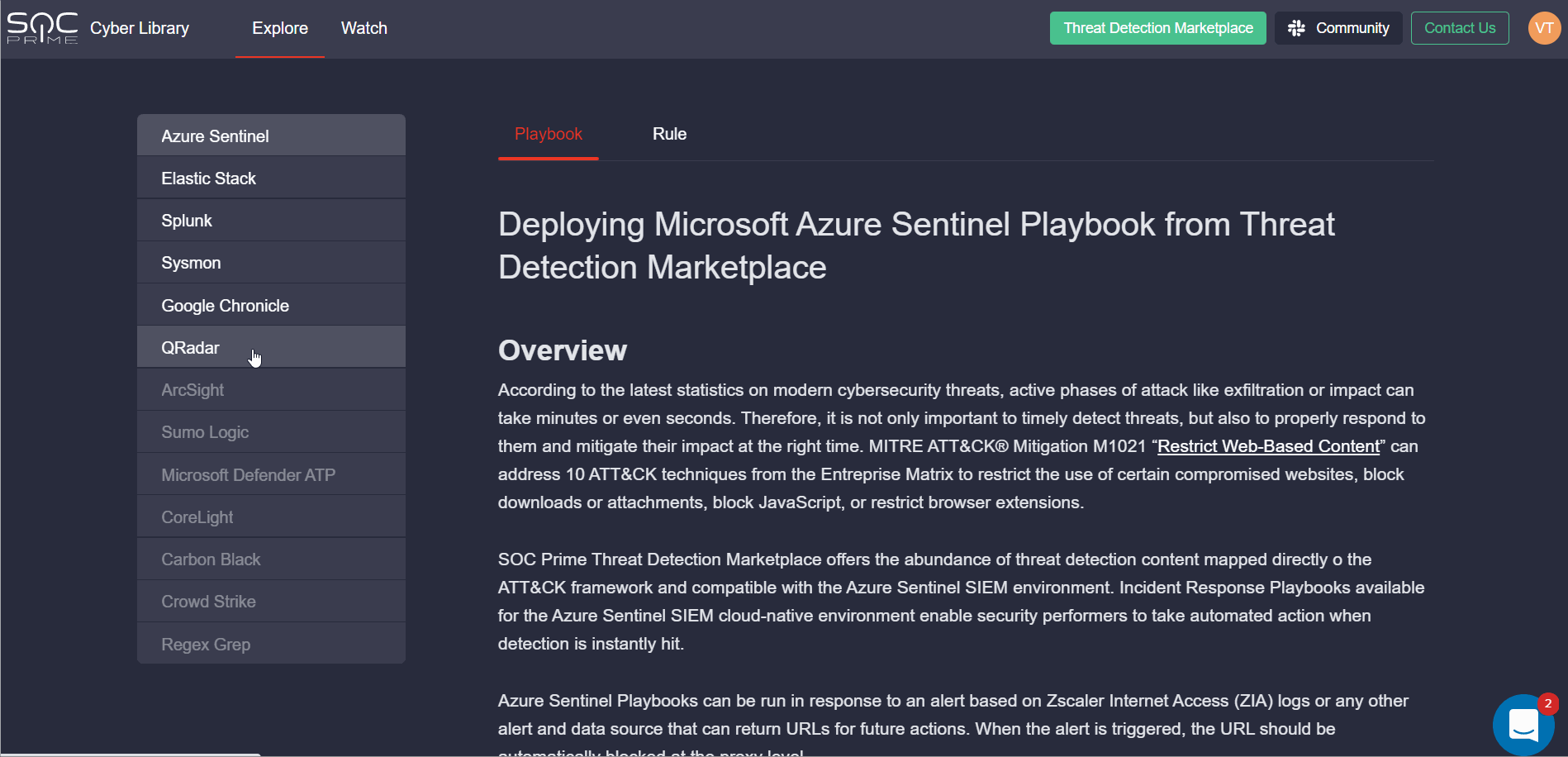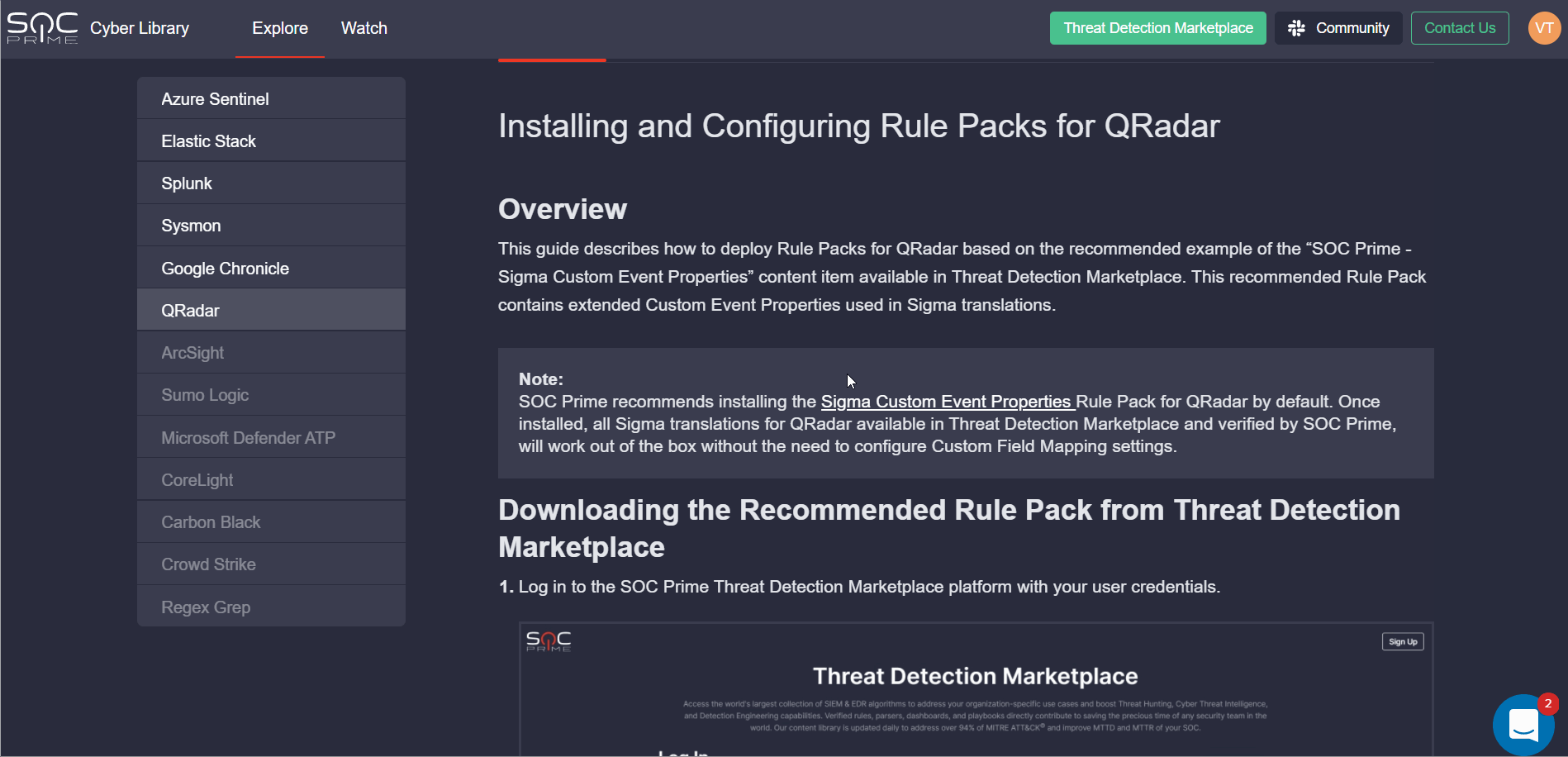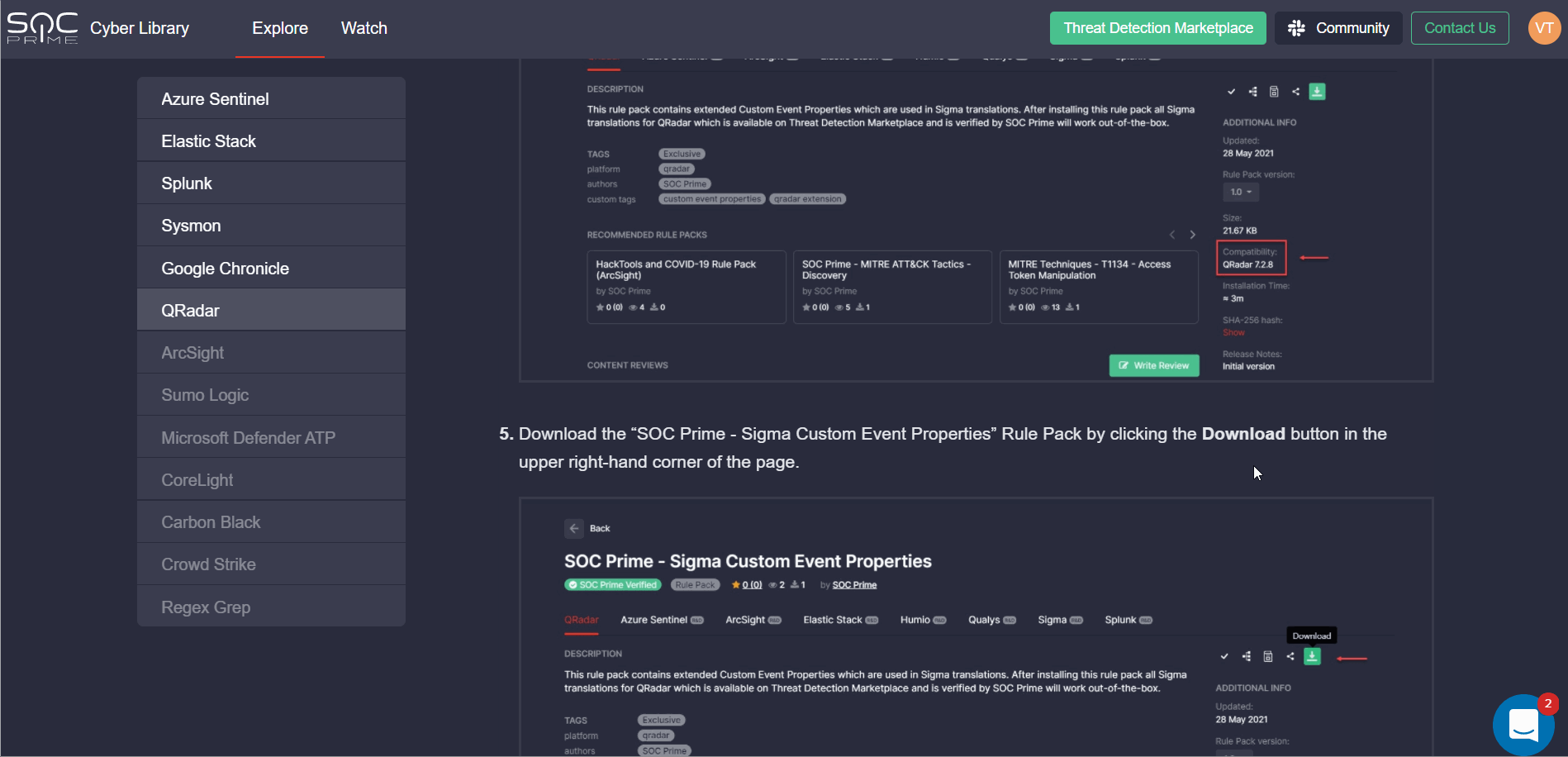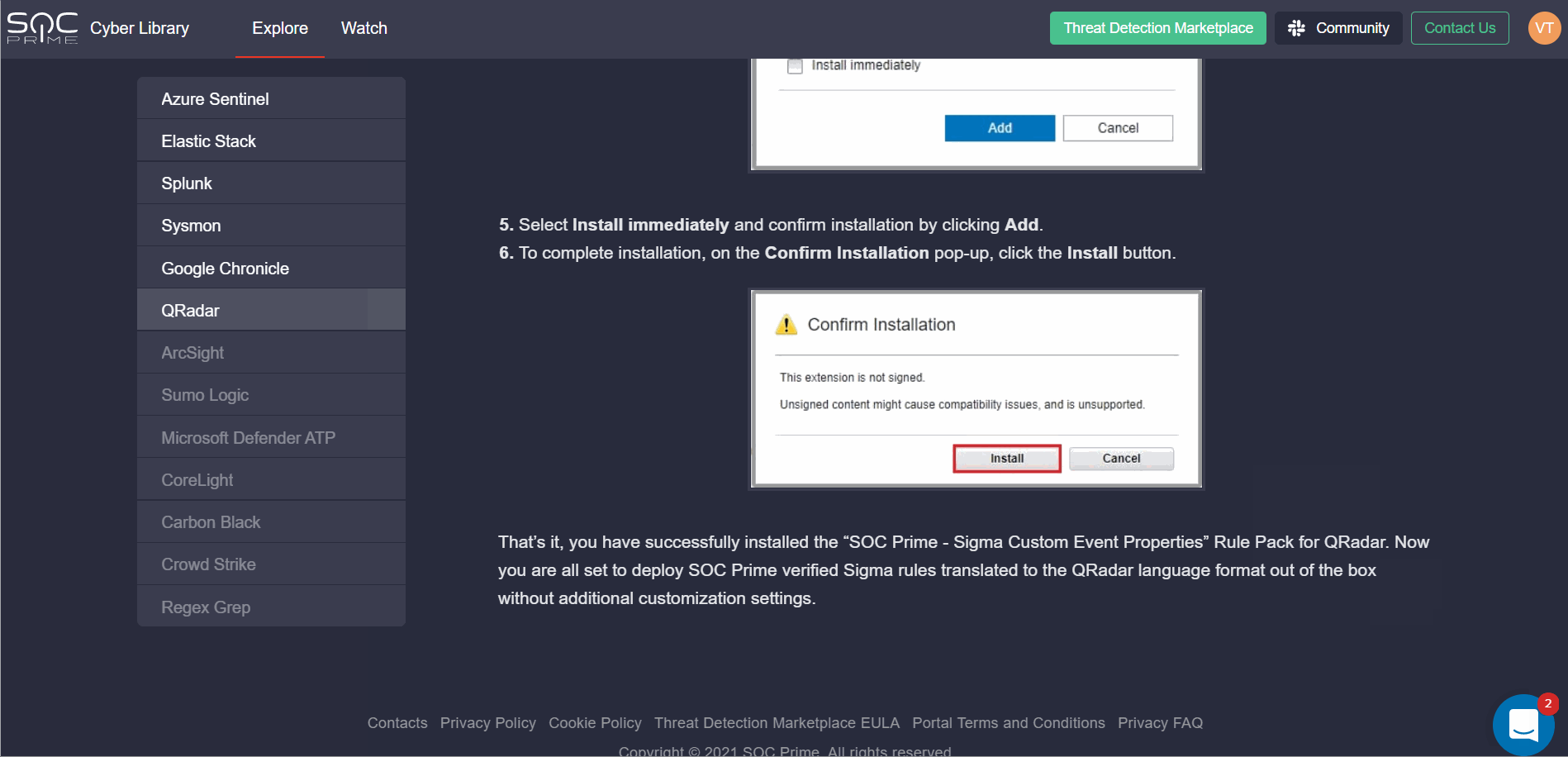
Note: SOC Prime recommends installing the Sigma Custom Event Properties Rule Pack for QRadar by default. Once installed, all Sigma translations for QRadar available in Threat Detection Marketplace and verified by SOC Prime, will work out of the box without the need to configure Custom Field Mapping settings.
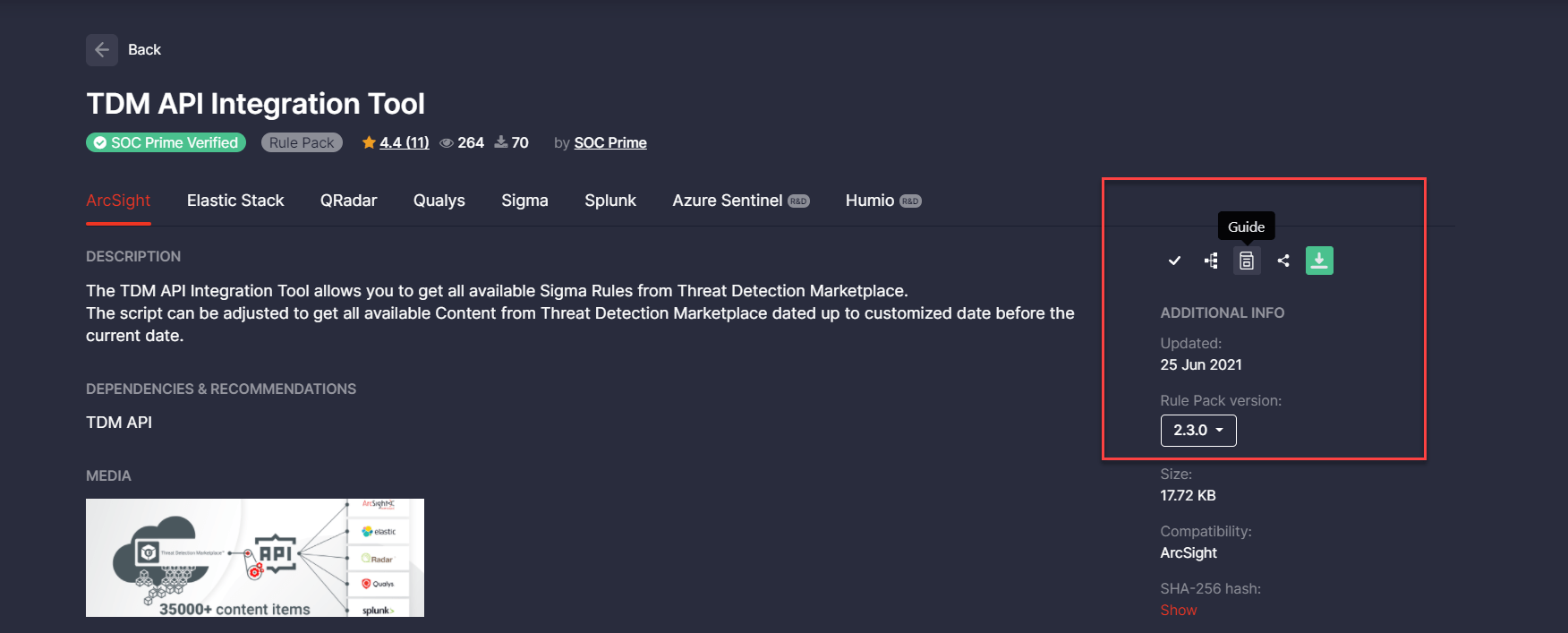
Threat Detection Marketplace API Integration Tool Guide v. 2.3.0
To keep Threat Detection Marketplace users informed on the latest API changes, we’ve updated the TDM API Integration Tool guide to its latest version 2.3.0. The key updates are as follows:
- Added a new /content-list endpoint, which allows downloading content lists from the Continuous Content Management (CCM) module in Threat Detection Marketplace
- Added new outputs for the following platforms:
- Splunk
- Elastic
- Kafka
- Fixed minor issues
Bug Fixes & Improvements
With this release, we’ve made the following bug fixes and improvements to Threat Detection Marketplace:
- User experience improvements:
-
- Fixed the issues on the Dashboard page when drilling down to the pop-ups that displayed wrong content statistics or no matching records.
- Fixed the issue with the rule presets when applied to Google Chronicle that occasionally appeared and displayed a server error.
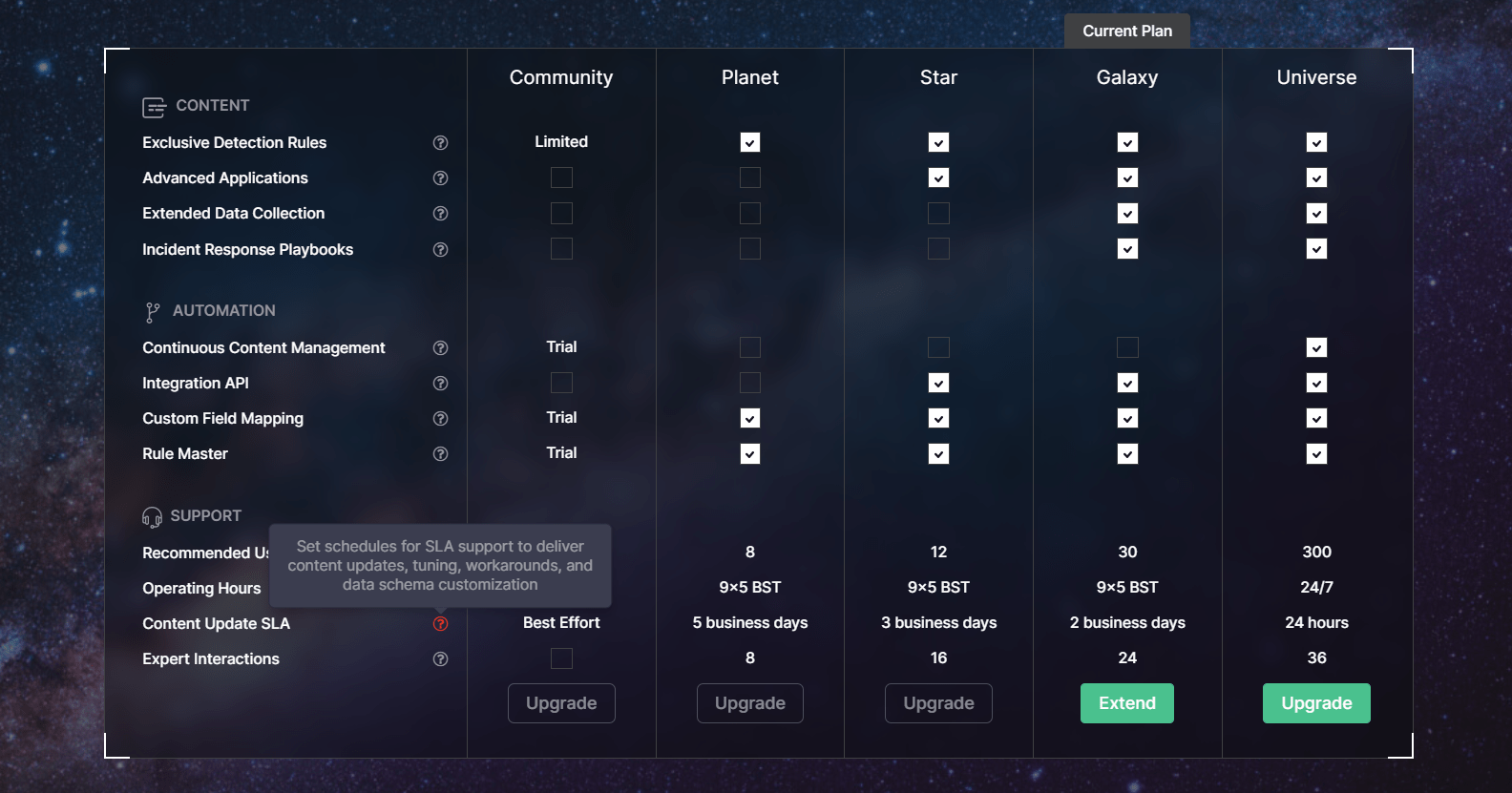
- Updated the tooltip description on the Upgrade page for the Content Update SLA capability:
-
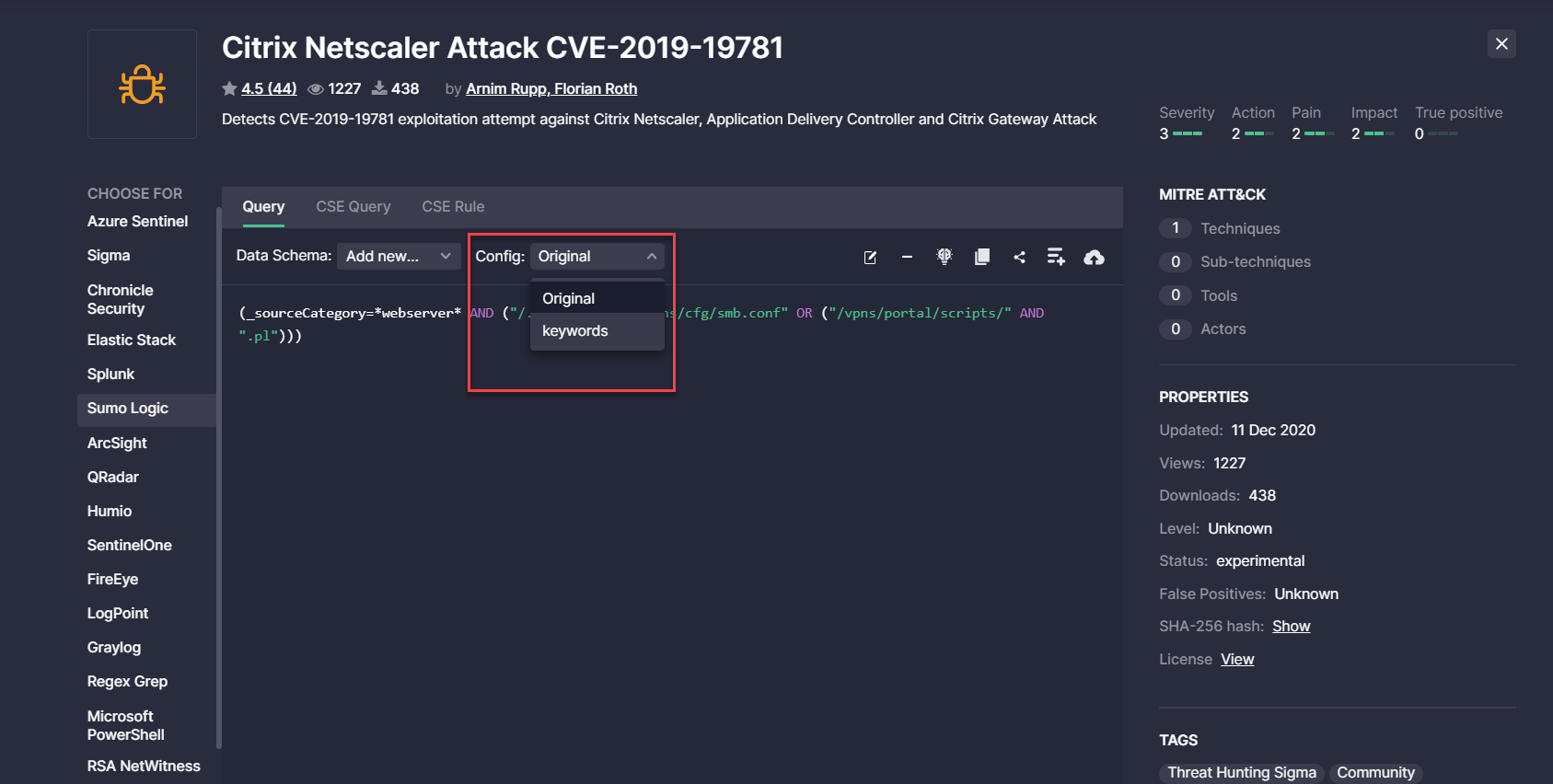
- Fixed the issue with the duplicate alternative translation options displayed in the Config drop-down list for Sumo Logic content types. After fixing the issue, only unique alternative translation options are available for this platform:
-
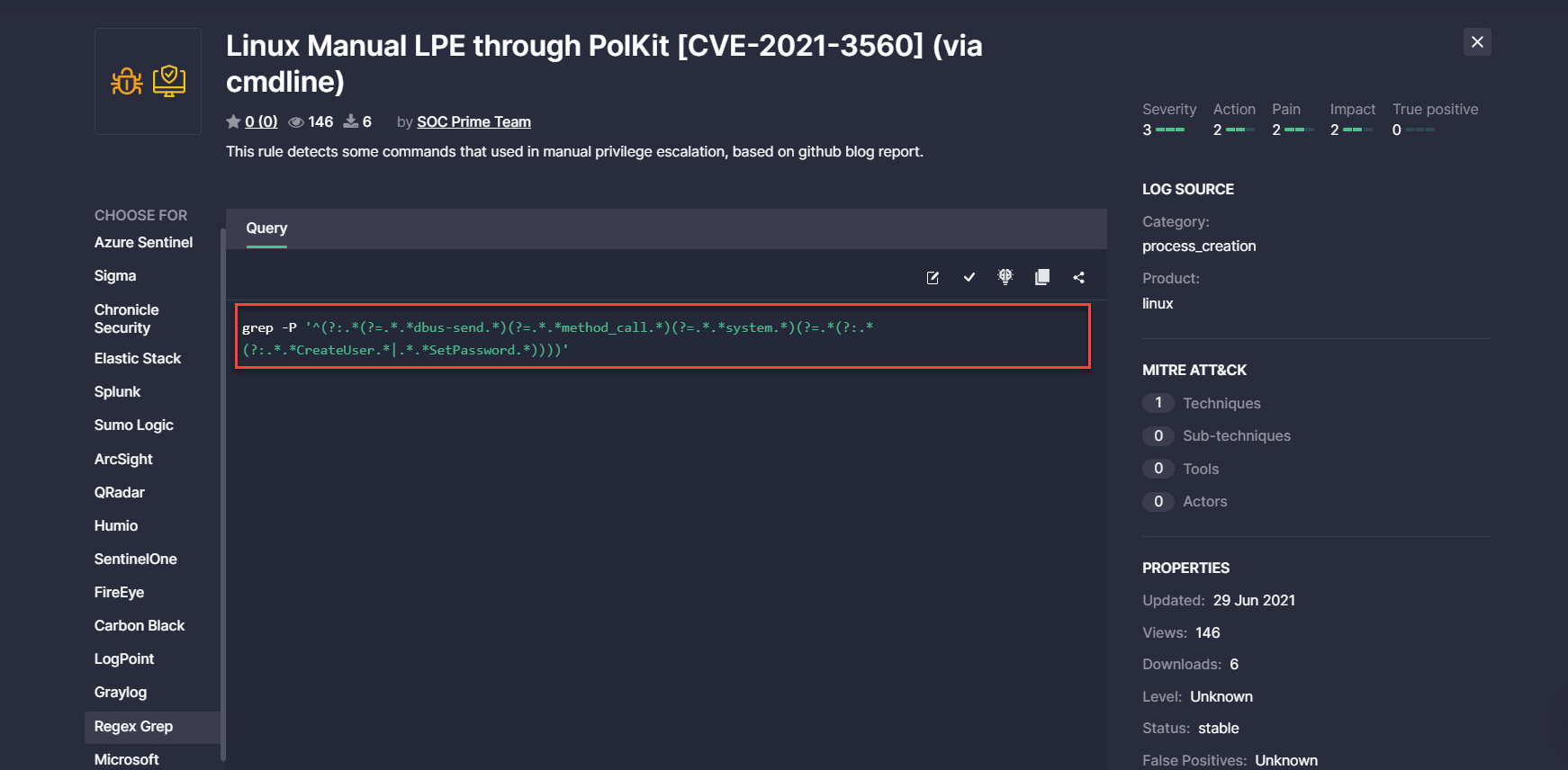
- Removed the line number that was displayed for the Regex Grep Queries and was redundant for the single-line content source code:
2. On the Content page > Detections view mode
-
- Added a hint showing a full content name and its description when hovering over the elements. This enables security performers to capture at a glance the identifying content details, which is a valuable user experience improvement to content items that cannot display their full name and description due to the layout restrictions.
- Fixed the wrong layout issues
Subscribe to Threat Detection Marketplace, the world-leading Detection as Code platform for SOC content that provides access and support to 100,000+ detection and response algorithms for 20+ market-leading SIEM, EDR, and NTDR technologies. Want to craft your own detections and share them with the global community of cyber defenders? Join our Threat Bounty Program!


