Threat Detection Marketplace 4.9.0: Continuous Content Management Updates
To boost your threat detection speed and power continuous threat coverage, we are constantly mastering our Continuous Content Management (CCM) module for Threat Detection Marketplace. The latest platform release brings in major upgrades to the CCM functionality that ensure even more streamlined content streaming directly to the security tool of your choice. Particularly, the improvements expand the list of supported security platforms, enhance search functionality, promote Custom Field Mapping functions, and provide prominent updates to the Content Lists page.
Support for Google Chronicle
At SOC Prime, we’re continuously broadening the support for various SIEM, EDR, and NTDR solutions in use. With this latest Threat Detection Marketplace release v.4.9.0, we’ve added the support for Google Chronicle to enable continuous content streaming of YARA-L detections directly into the customer’s Chronicle instance.
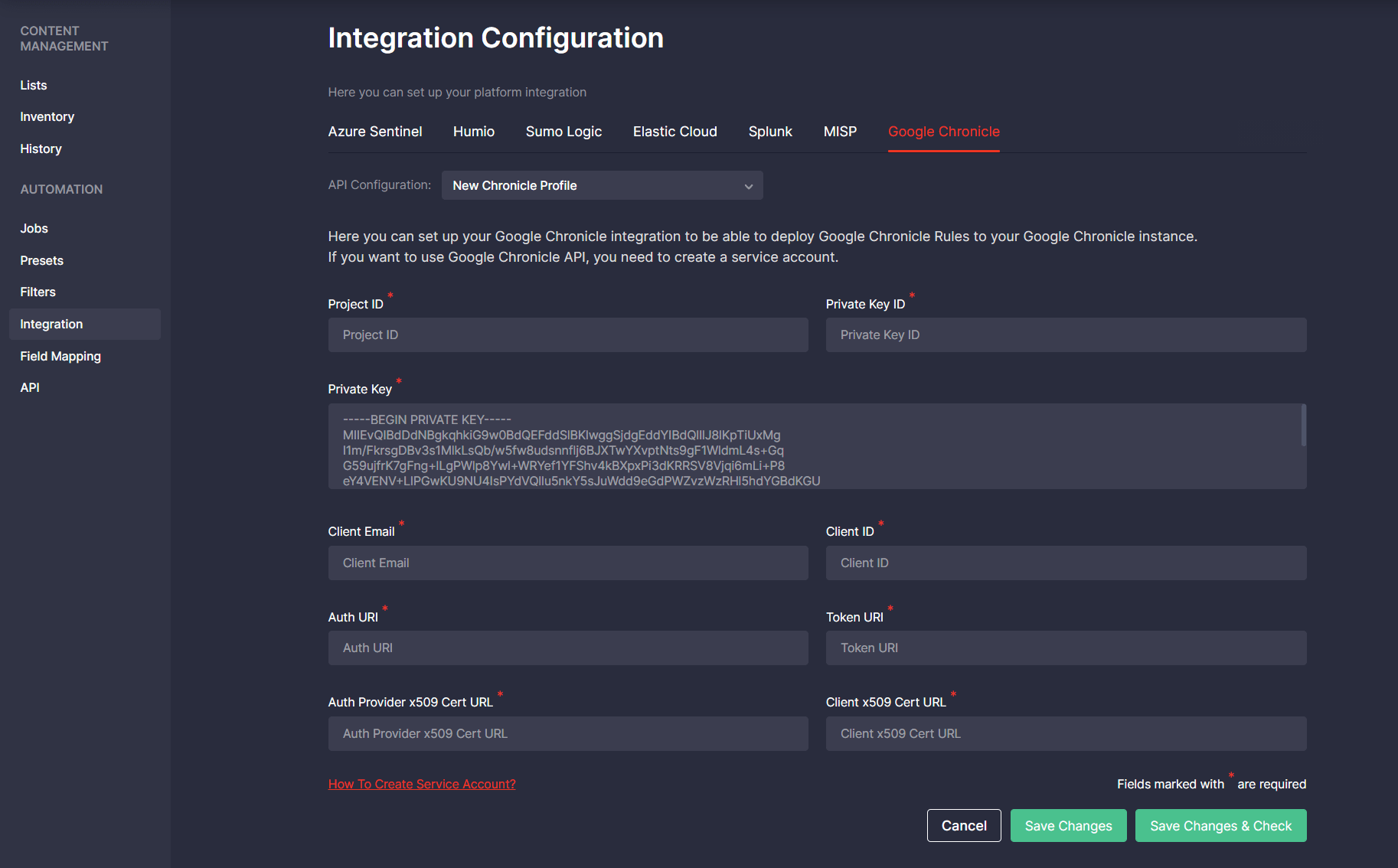
The initial use of the CCM module requires setting up integration with the Google Chronicle cloud-native environment by selecting Integration Configuration > Google Chronicle. To automatically stream rules via the Google Chronicle API, security performers need to create a service account following these guidelines. To check whether user credentials are valid, click the Save Changes & Check button after filling in all the required fields.
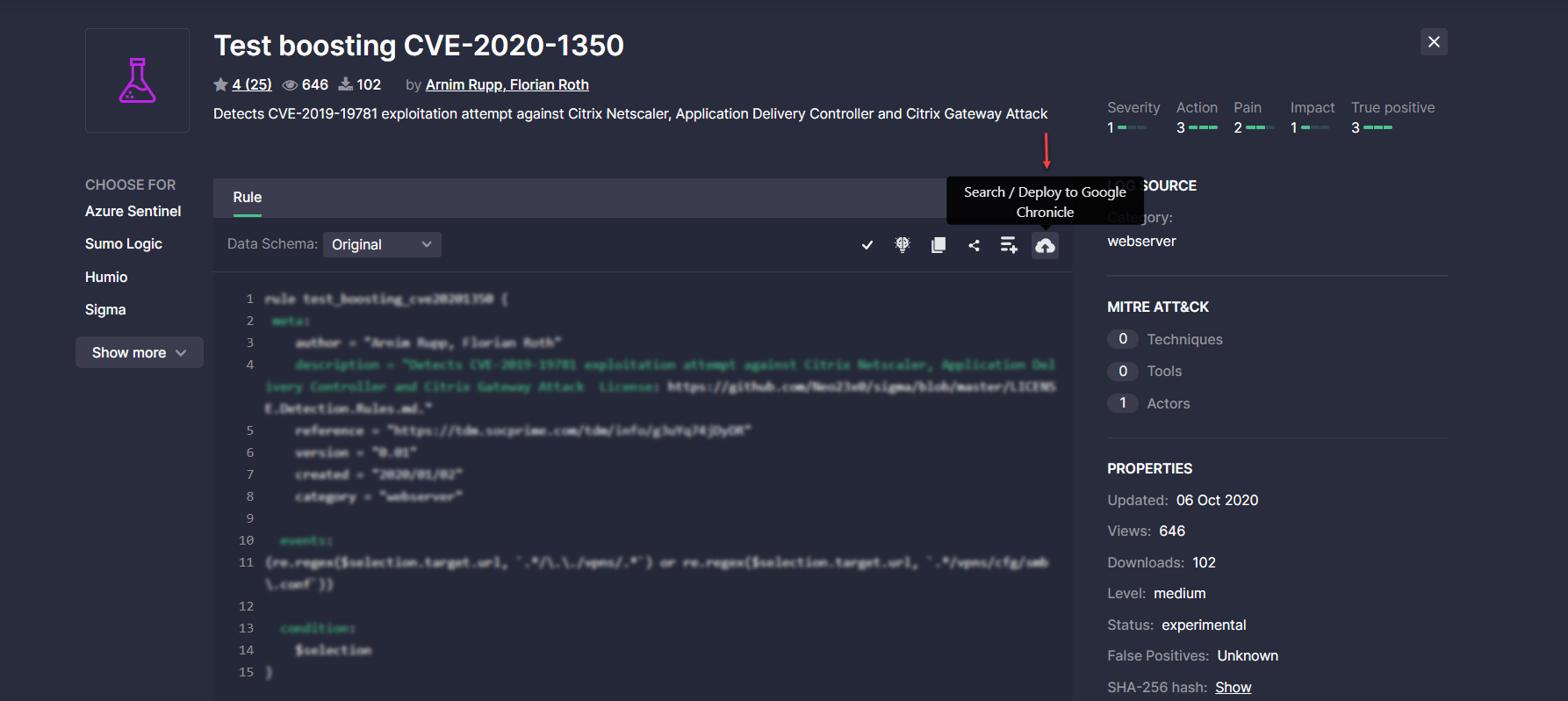
After setting up all the required integration configurations, Threat Detection Marketplace users can deploy rules to their Google Chronicle instance:
- Manually right from the content item page by clicking the Search / Deploy to Google Chronicle button
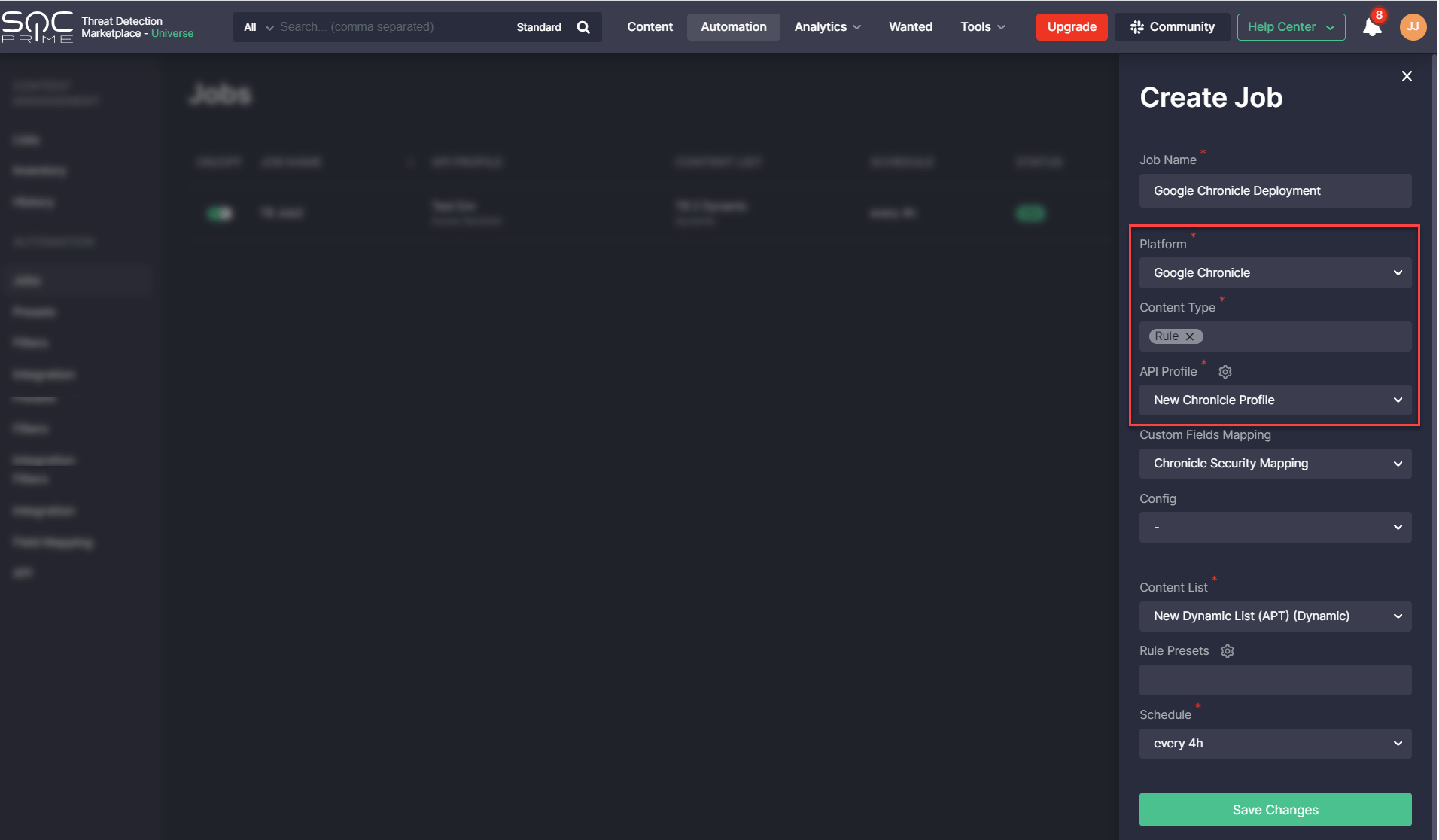
- Via automatically scheduled jobs by linking a certain job to the Google Chronicle platform, Rule content type, and the configured API profile
After deploying content to the Google Chronicle instance, security performers can then view the deployment results on the History page.
Also, on the Inventory page, Chronicle customers can track the deployment status and date of the last content deployment, content source and contributor, and other details for the Google Chronicle instance. Also, the same actions are available for the selected Google Chronicle content items as for other platforms supported by the CCM module:
- Disable
- Enable
- Add content to the inventory list
- Delete
Content Lists Updates
This Threat Detection Marketplace release v.4.9.0 introduces major user experience enhancements to the content list functionality, more specifically:
- Brand-new look and feel of the Content Lists page
- Content limits for dynamic lists
- Content list streaming via API
- New content list type
Brand-New Look and Feel of the Content Lists Page
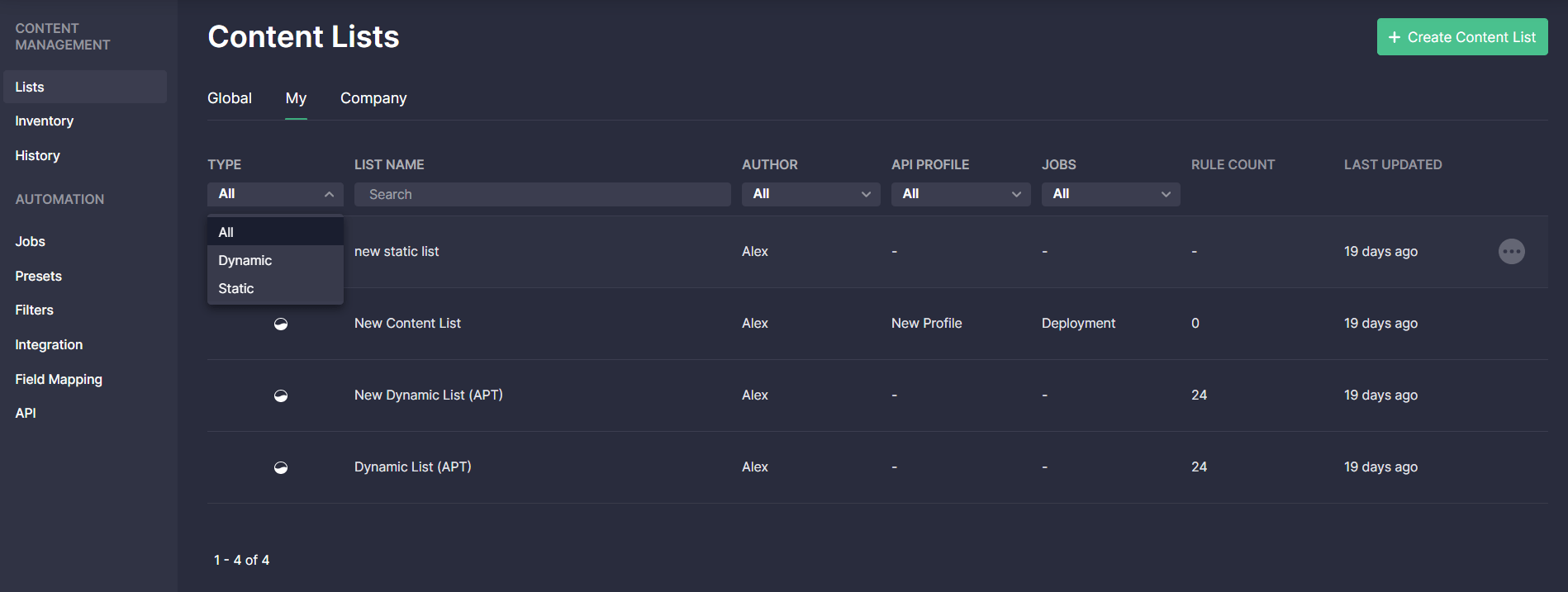
With this latest update, we’ve redesigned the Content Lists page for a more intuitive threat detection experience. Security performers can now see all content lists arranged as a table to keep the page look and feel consistent with other Continuous Content Management (CCM) functionality. The key UX improvements to the Content Lists page are as follows:
- New SVG Icons with three content list types
- Static lists
- Dynamic lists
- Newly added type — Inventory lists
![]()
2. New list details available under the corresponding columns
- Rule Count — number of content items within the list, which is updated on the fly according to the corresponding list changes
- Last Updated — when the list was last updated
3. Streamlined list search via these filters
- Type
- List name
- Author
- API Profile
- Jobs
Content Limits for Dynamic Lists
To prevent platform overload when deploying content via the CCM module, we’ve implemented the content limit related to dynamic lists. Dynamic lists can now contain no more than 200 items of content. The information about the content limit is now available on the Create Content List pop-up when selecting the Dynamic list type.
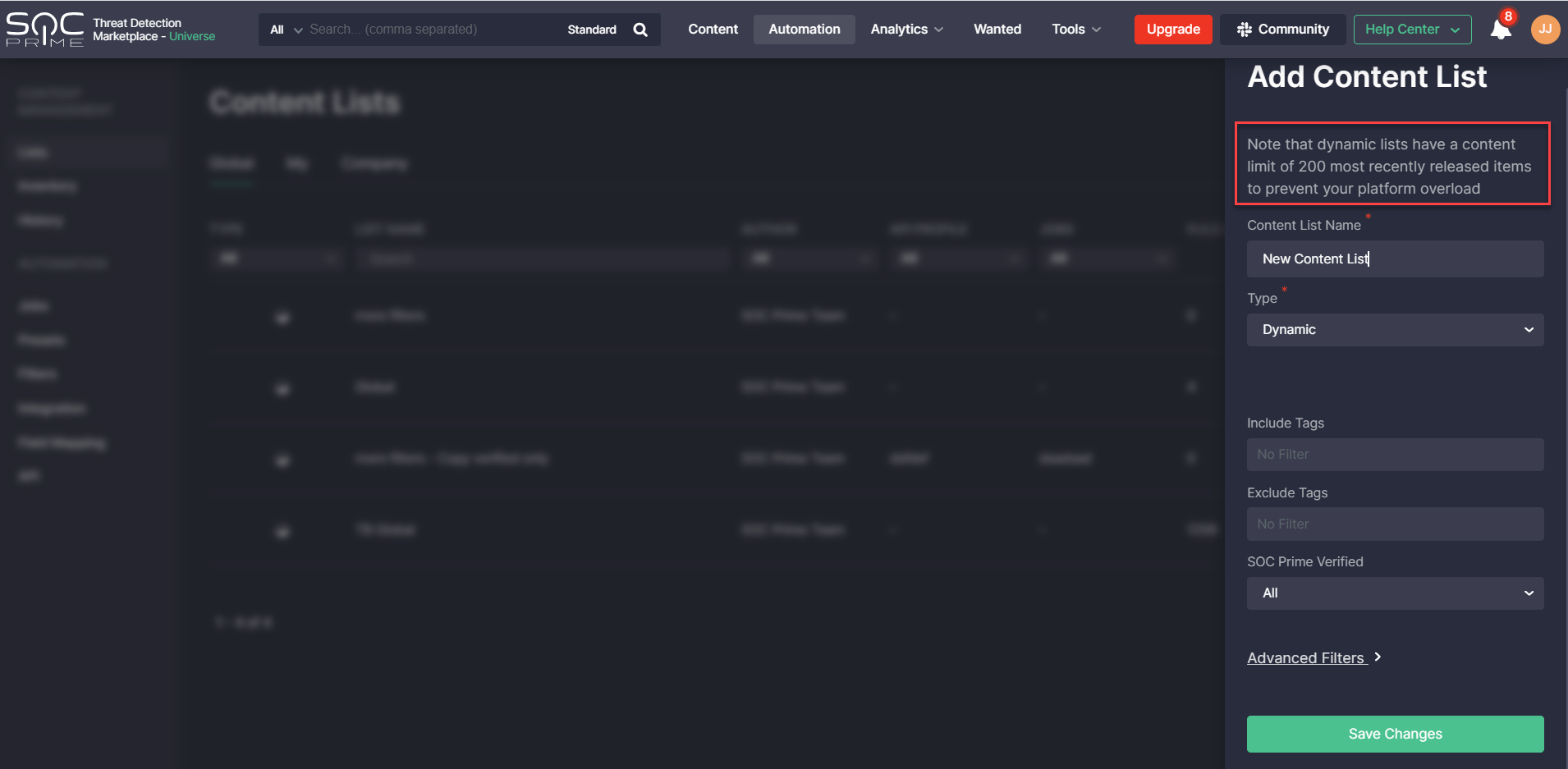
Note: When creating a new dynamic content list, it will display a maximum of 200 items of the most recently released content.
When saving a new list that has more than 200 content matches due to a lack of specific filter conditions, security performers will see the corresponding notification.
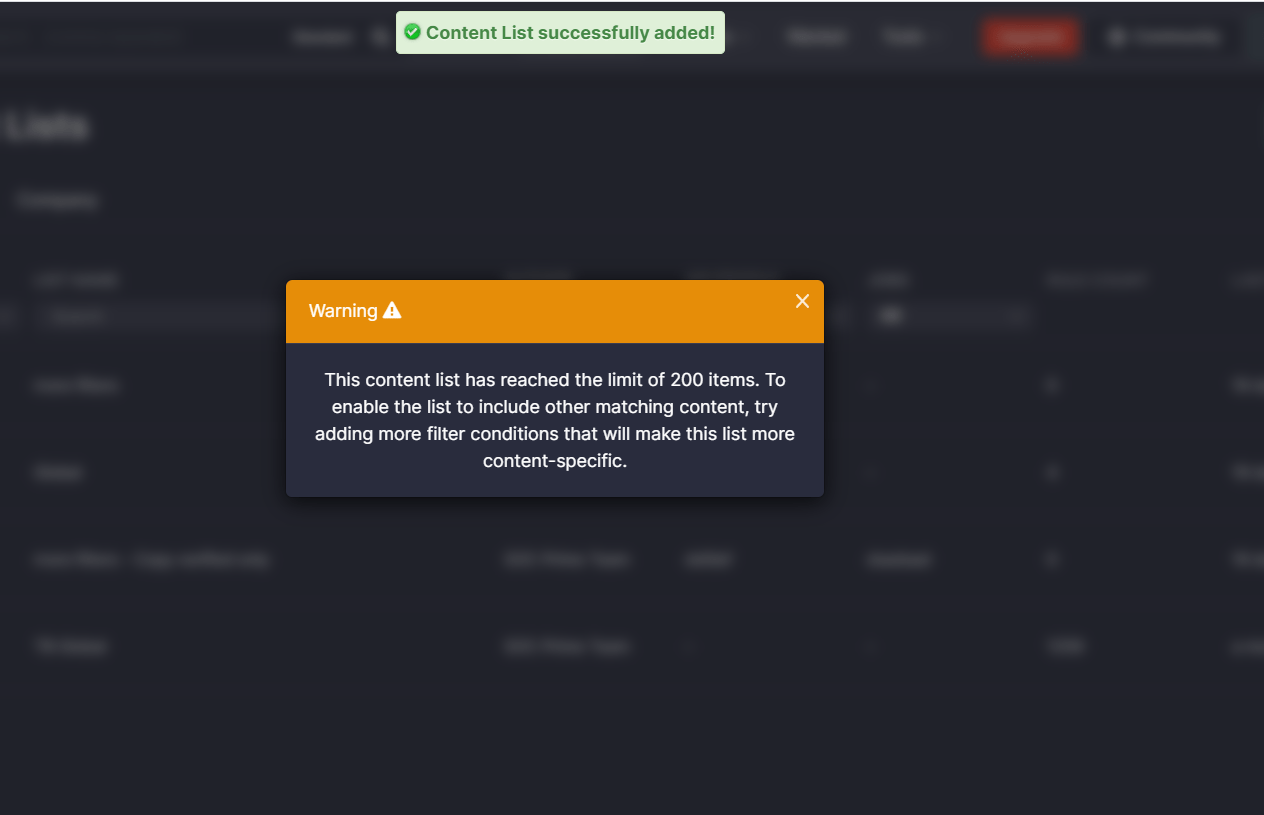
To enable the list to include other matching content, more filter conditions can be specified that will make this list more content-specific.
Content List Streaming via Threat Detection Marketplace API
With this latest release, we’ve added the ability to stream modified content from the CCM lists for various platforms via the Threat Detection Marketplace API using a newly added /content-list endpoint. The following parameters can be passed in the headers of API requests:
- client_secret_id — API key (Required)
- content_list_name — content list name (Required)
- siem_type — platform name
- preset_name — preset name, including filters
- alt_translate_config — configuration name of the alternative translation
Inventory Lists: New Content List Type
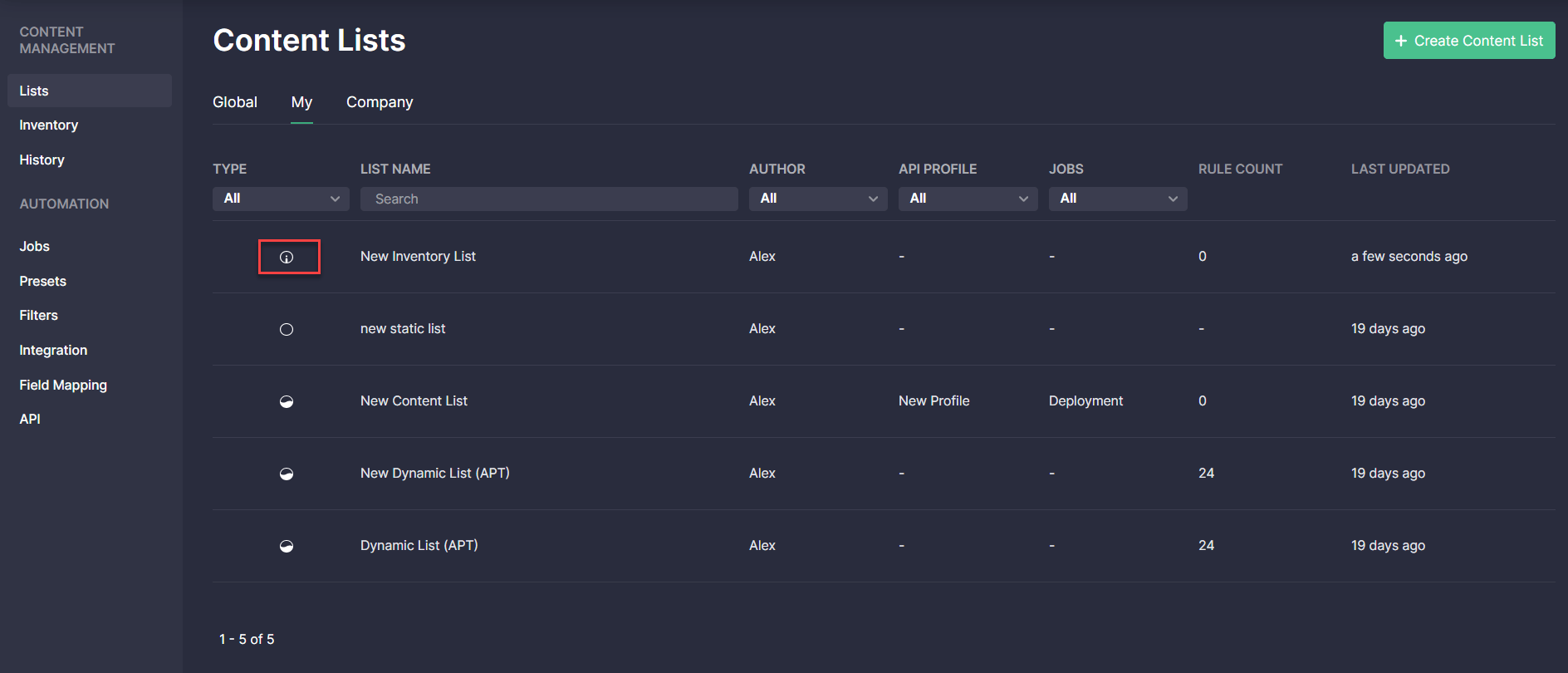
This latest CCM update introduces a new content list type that has its separate index. Inventory content lists can be separately deployed via jobs to another customer’s SIEM instance. In addition, security performers can edit content within inventory lists and save these local changes keeping original content items on the Inventory page completely intact. Content items updated within the inventory lists can then be separately deployed to a different SIEM instance.
Content lists of the recently added type called Inventory can be created by selecting the corresponding type from the Type drop-down list on the Add Content List pop-up.
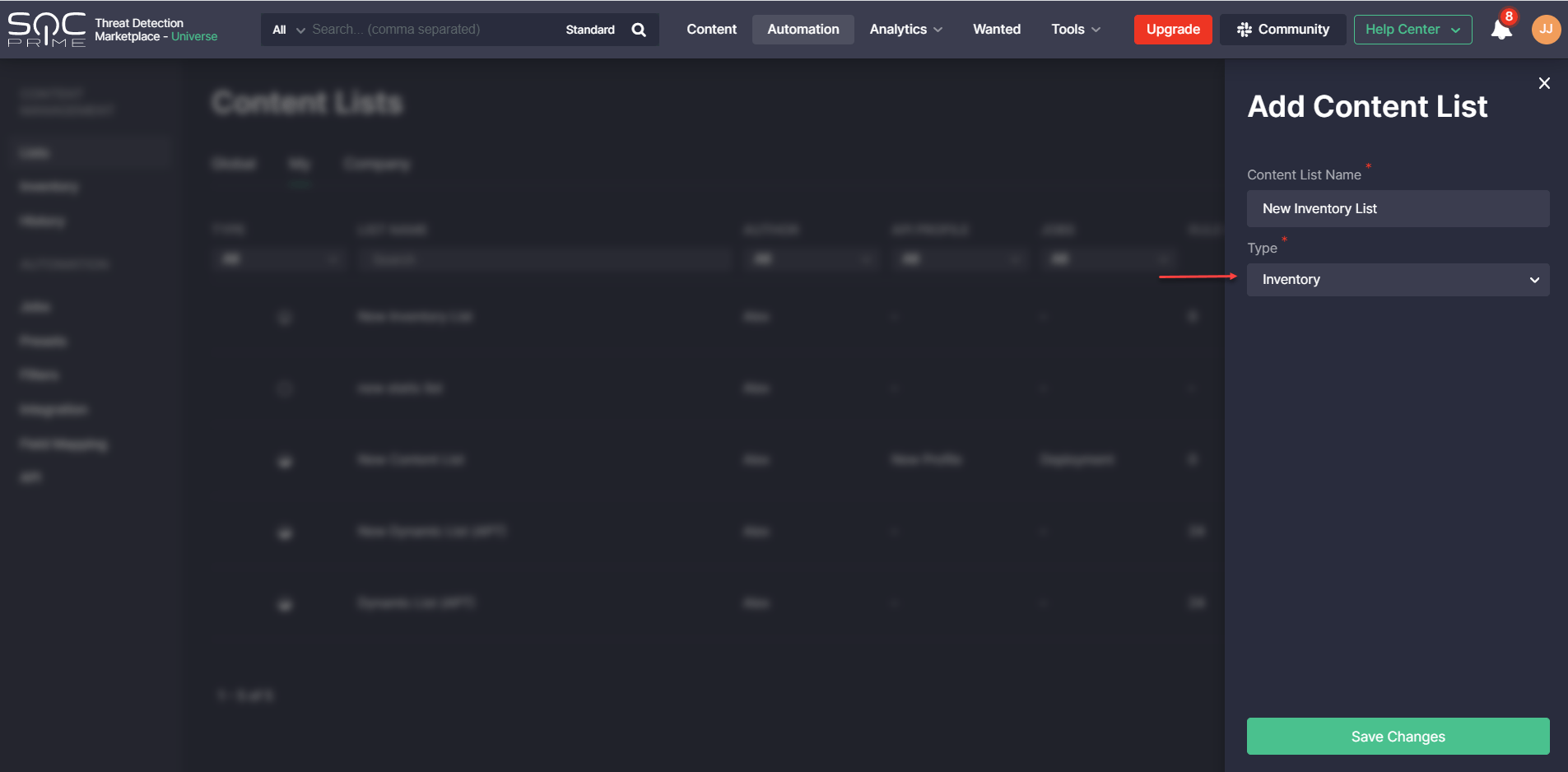
On the Inventory page, security performers can select the specific platform and content items and link them on the fly to the existing inventory list on the Add to Inventory List pop-up.
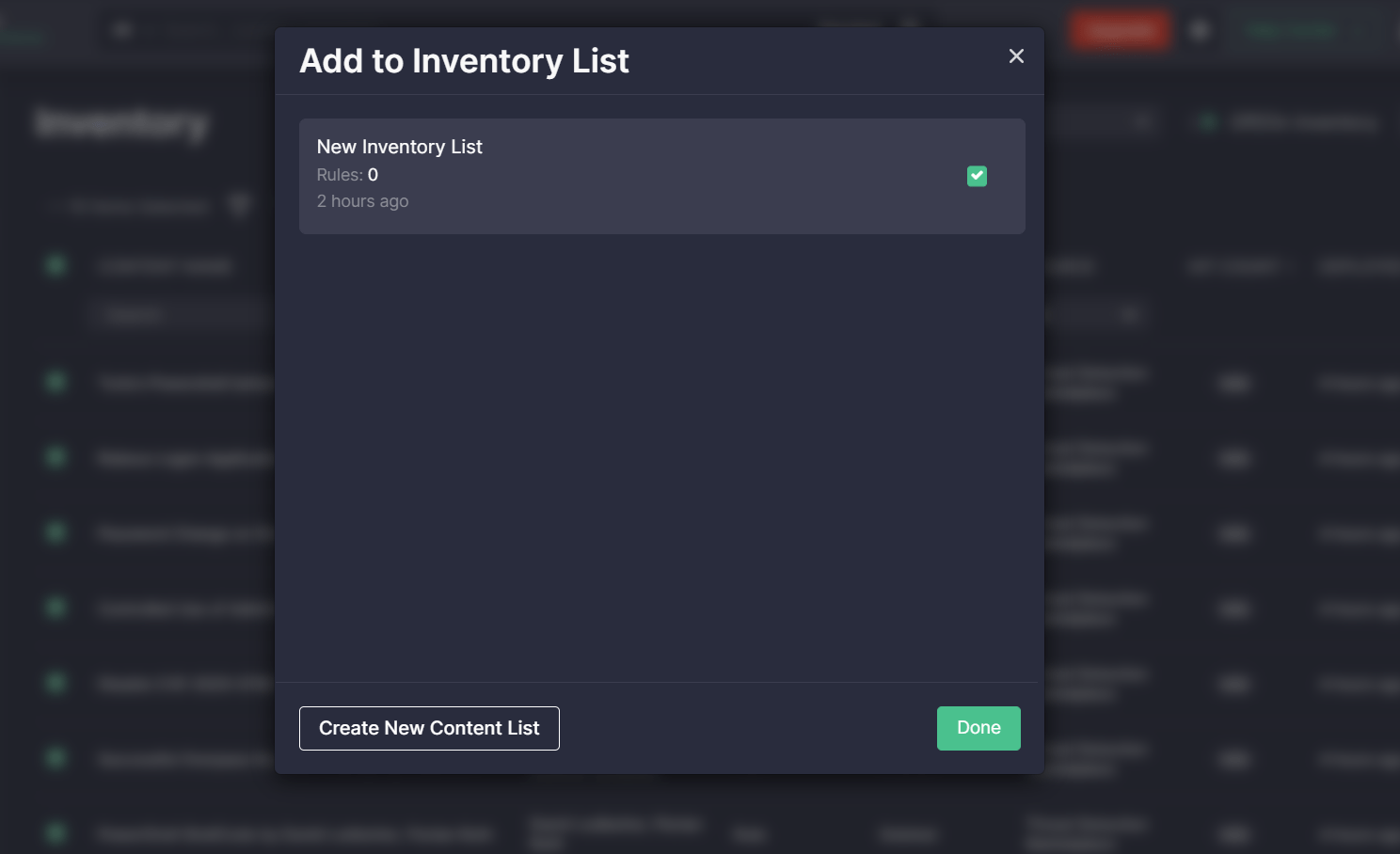
Once created, a new inventory list will be automatically added to the list collection under the My tab and will be indicated with the specific icon aimed to make such lists stand out from other list types.
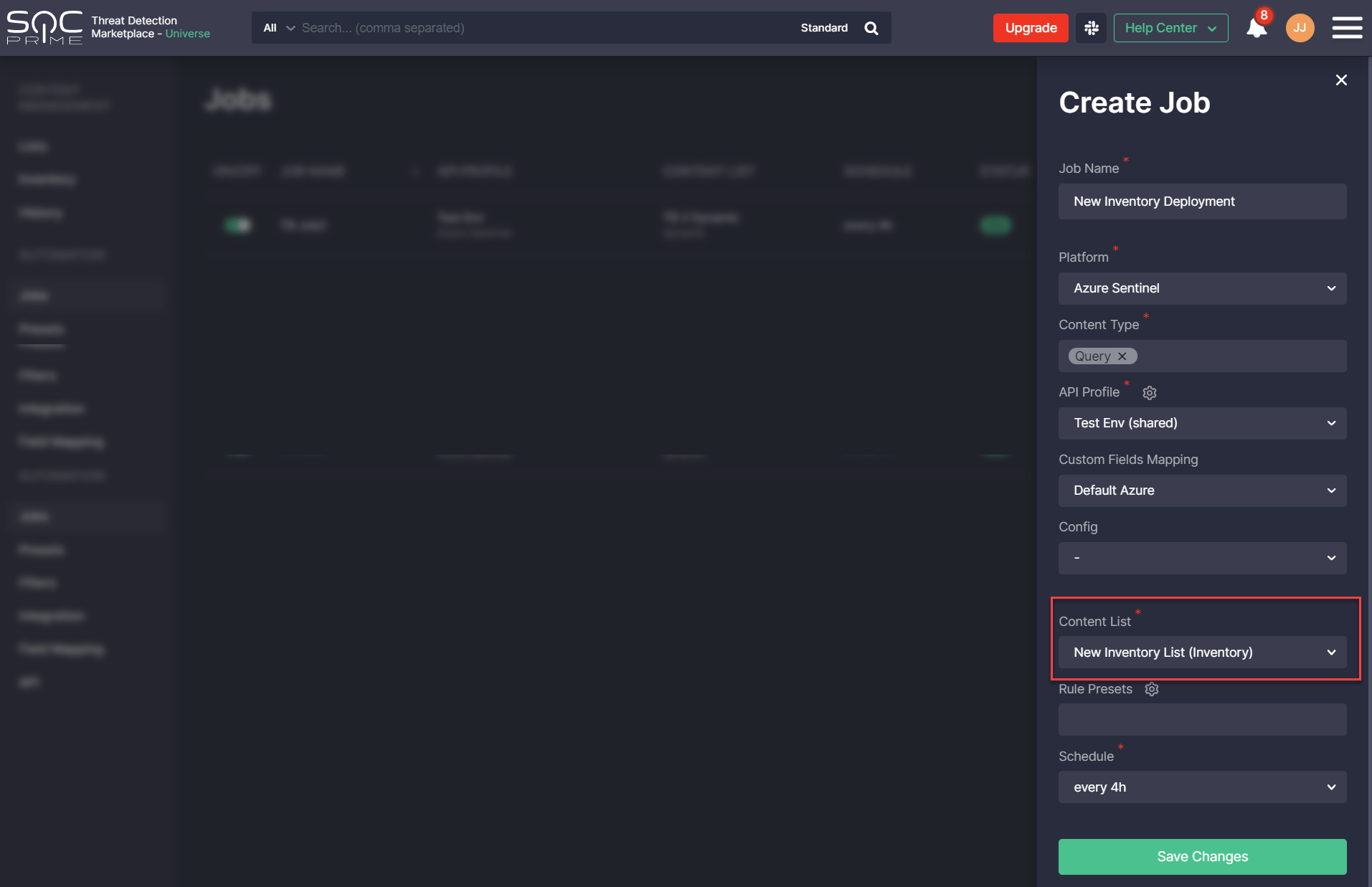
Created inventory lists can then be linked to jobs for various platforms and API profiles. When selecting the specific content list of such type, it will be automatically indicated as Inventory in parentheses after the list name.
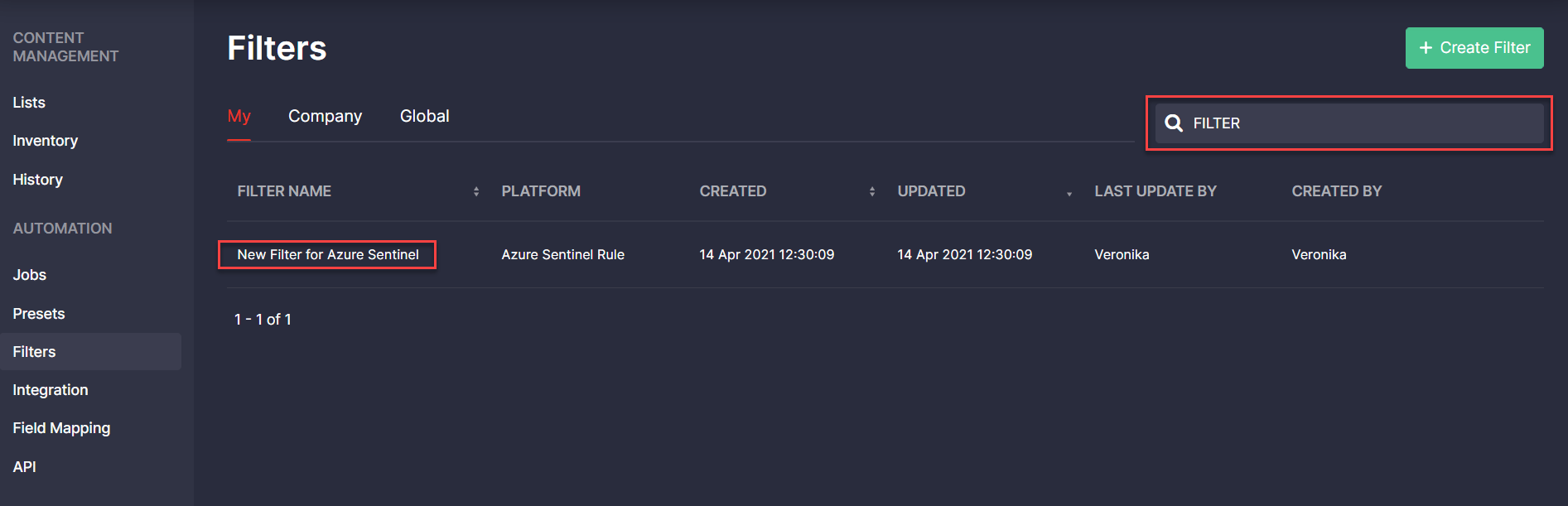
Search Enhancements
With this latest Continuous Content Management (CCM) release, we’ve added the support for uppercase search across all items on the Filters page. Now security performers can apply both uppercase and lowercase to their search queries and then see the list of all matching filters.
Additionally, in Threat Detection Marketplace version 4.9.0, we’ve enhanced the search functionality on the Custom Field Mapping page by adding the ability to search for mapping profiles using uppercase. Now the system accepts both uppercase and lowercase queries and delivers matching search results.
Custom Field Mapping: CSV File Import
Also, with this release, we’ve continued to master the Custom Field Mapping functionality for a more streamlined platform experience. Security performers can now import the mapping file in the CSV format with the preconfigured fields for all available platforms, which saves the need to fill in these custom fields manually on the Custom Field Mapping pop-up. To use the uploaded data, click the Import from CSV button on the profile creation pop-up, and then add a CSV file from the local disk or drop it to upload.
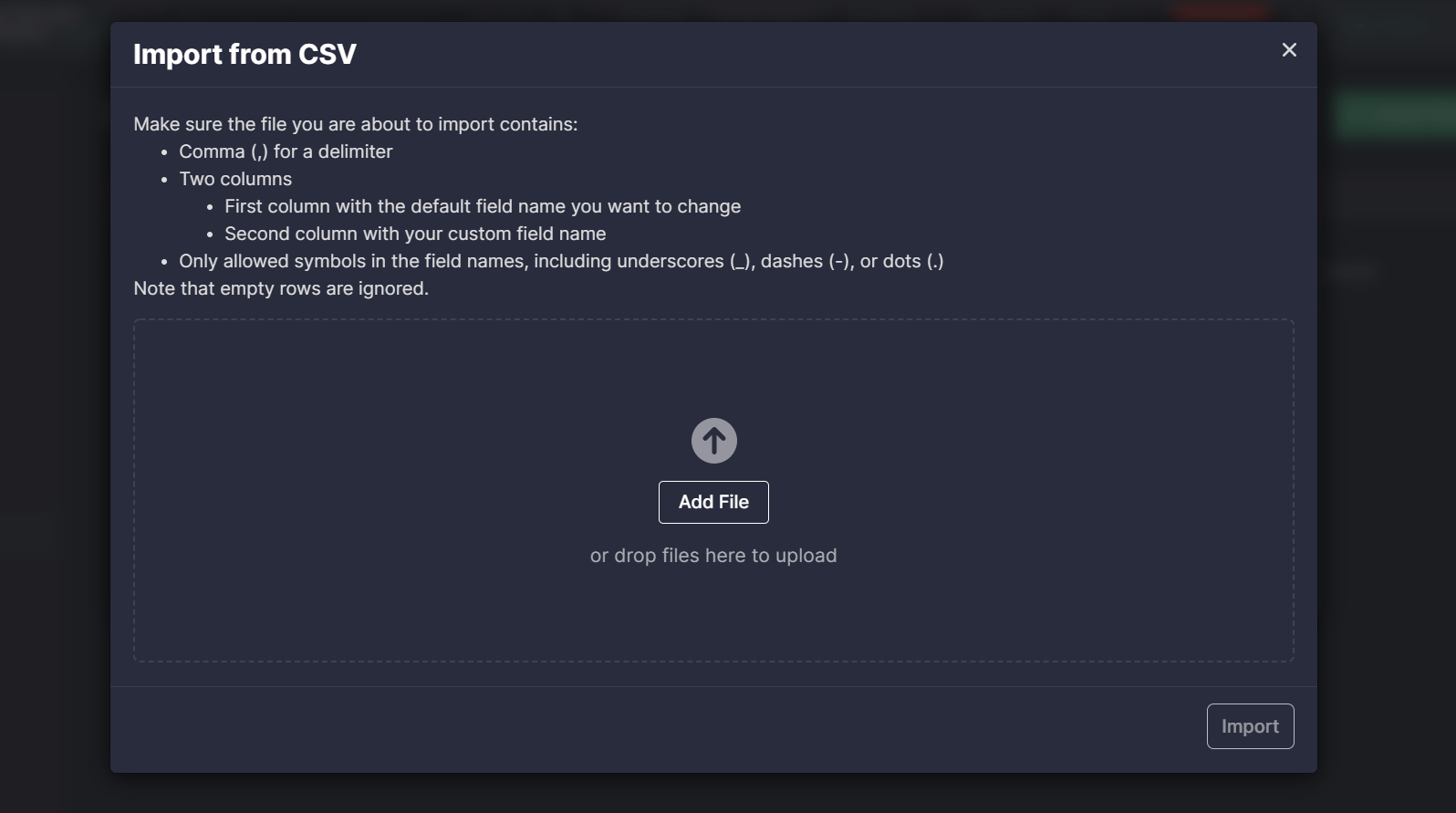
Note: The CSV file must be in a valid format and meet all the set requirements. If something is wrong or some required details are missing, an error will appear, and the file data won’t be uploaded.
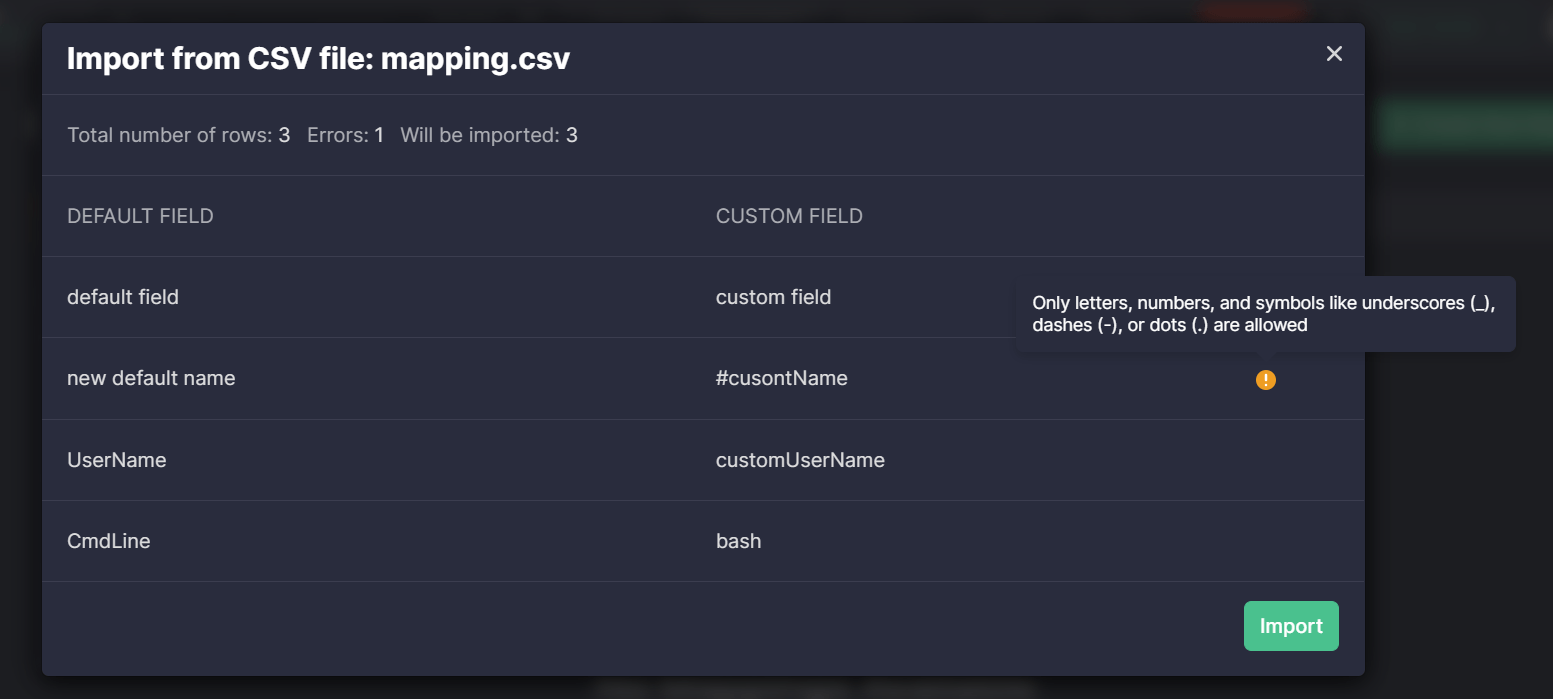
The following requirements need to be considered to make sure the CSV file is appropriate:
- It must use a comma (,) for a delimiter
- It must contain two columns
- The first column with the default field name that will be changed
- The second column with the custom field name
In addition, the imported CSV file must contain only allowed symbols in the field names, including underscores (_), dashes (-), or dots (.).
Threat Detection Marketplace users with Admin privileges can import CSV files that fit into the Global mapping category.
Searching for the best SOC content compatible with your SIEM, EDR, and NTDR solutions in use? Get a subscription to our Threat Detection Marketplace and obtain 100K+ detection and response rules easily convertible to various language formats. The content base enriches every day thanks to the joint efforts of our international community of 300+ security performers. Enjoy coding and eager to contribute to the industry-first SOC content library? Join our Threat Bounty Program!


