On April 7, 2021, we released Threat Detection Marketplace version 4.7.0 to reinforce the existing capabilities of our Content-as-a-Service (CaaS) platform and fulfill the requests of our customers. With this latest update, we’ve introduced a new login and signup page, provided Google Chronicle sorting option enhancements, extended the Calendly integration within Threat Detection Marketplace functionality, improved Warded features, and made significant upgrades to boost the overall platform experience.
Threat Detection Marketplace: Improved Login & Signup Page
The latest platform version 4.7.0 introduces an improved look and feel of our login/signup page, so security performers can see at a glance what our Detection as Code platform can offer them and how they can boost the company’s cyber defense potential. The newly redesigned flow introduces the streamlined registration or login experience and gives a quick overview of the platform’s capabilities.
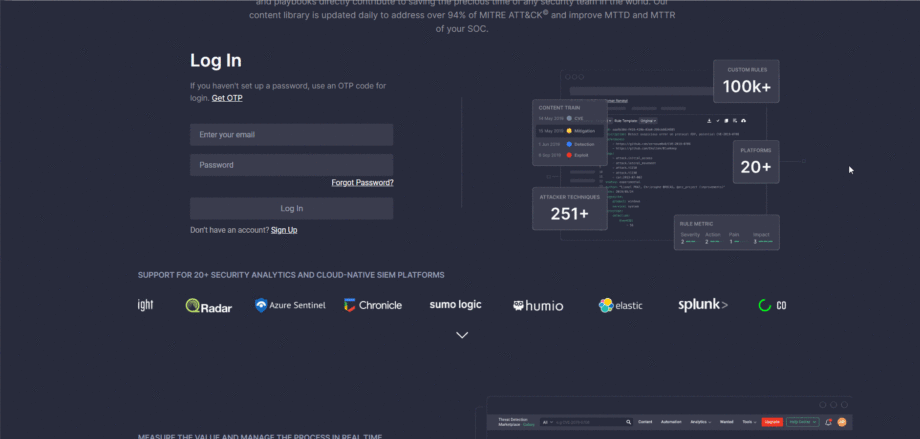
In addition, we’ve made enhancements on the back end for performance optimization and improved the overall page load speed.
Google Chronicle Sorting Option & Content Boosting
For a more streamlined search for detections written in the generic Yara-L format, we’ve added the ability to sort all available SOC content on the fly by selecting the Google Chronicle sorting option on the Content page.
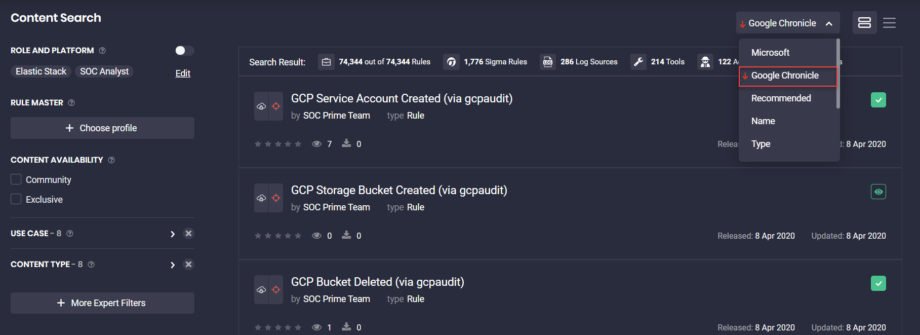
The enhanced boosting functionality is an extra asset for Google Chronicle users who will see the most relevant content items on top of the list.
Extended Calendly Integration
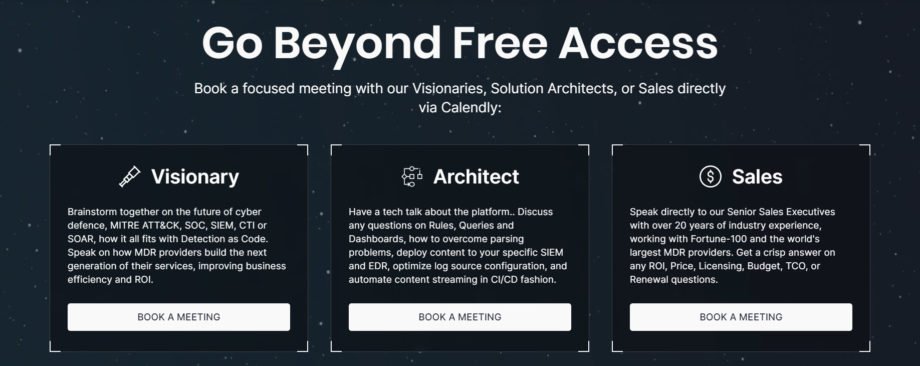
With this latest release, we’ve extended the Calendly integration for other Threat Detection Marketplace functionality to make on-the-fly communication with our SOC Prime experts real. Our Premium customers can now book a focused meeting with the representative of one of the three expert groups depending on their business or tech concerns:
- Visionaries to have a business talk and brainstorm ideas on the future of cyber defense and how to improve business efficiency and ROI
- Architects to have a deep dive expert talk on the content deployment, log source configuration, and other tech issues
- Senior Sales Executives to get a crisp answer on any ROI, Price, Licensing, Budget, TCO, or Renewal questions
All this is possible by clicking the corresponding button on top of the Upgrade page and scheduling a meeting on the fly via the Calendly add-on.
Additionally, to make the platform experience more streamlined and provide a quick solution for the emerging issues, we’ve introduced the following pop-ups automatically offering an ability to book a focused expert meeting:
- When a user has no more keys to unlock the specific content items or due to their subscription limitations related to the Premium content access
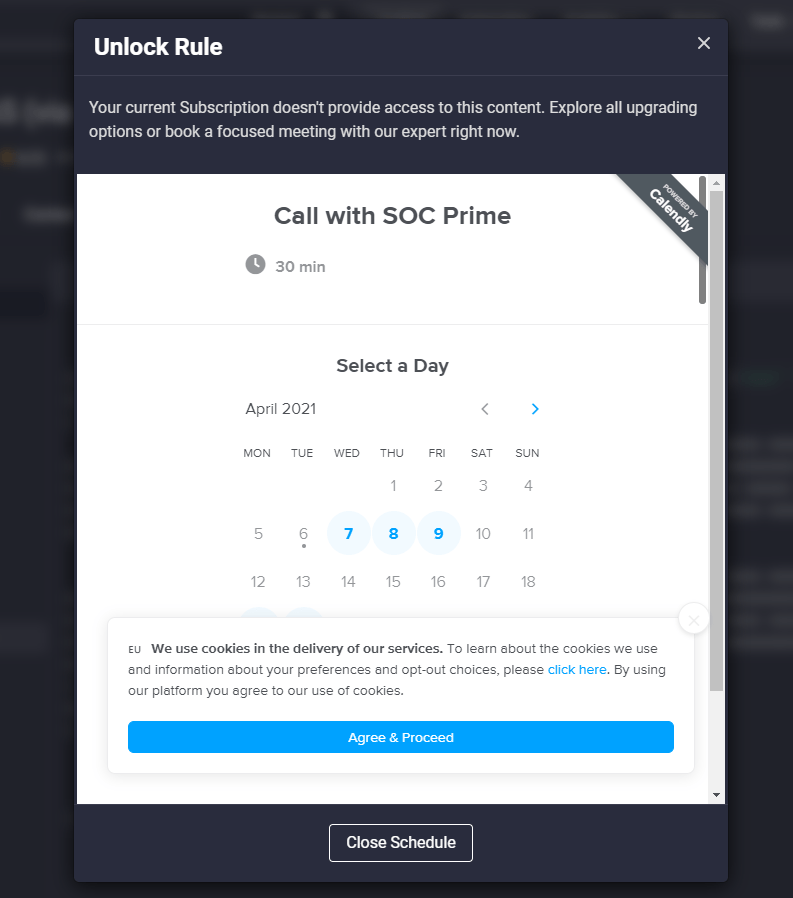
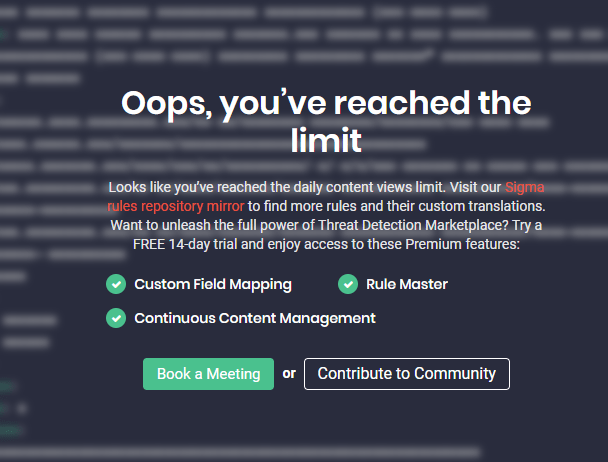
- When a user has reached the daily content viewing limit
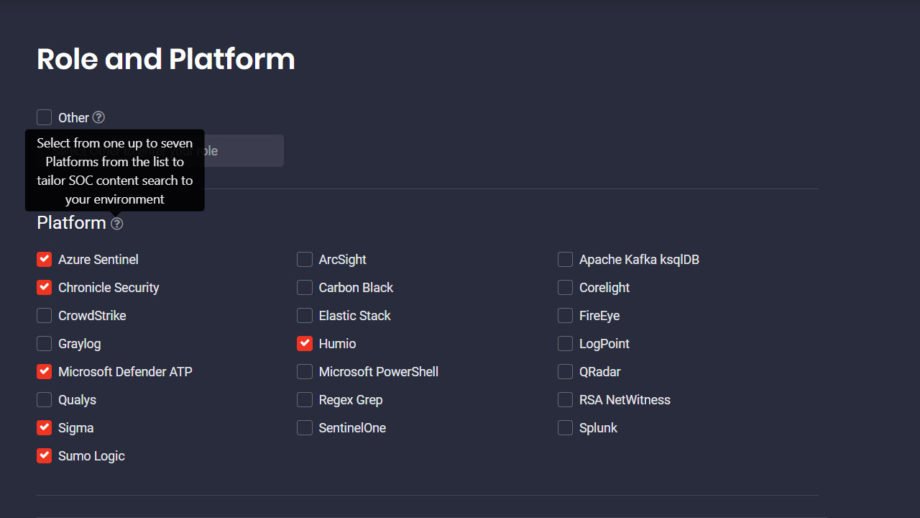
Role and Platform Selection Updates
At SOC Prime, we aim to deliver the most personalized platform experience for security professionals considering their cybersecurity role, as well as SIEM and XDR stack in use. To help security performers obtain the most relevant content tailored to their organization’s environment, we’ve limited the platform selection to maximum of seven options from 23+ SIEM, EDR, and NTDR technologies. Threat Detection Marketplace users can now see the corresponding tooltip upon registration or in the Role and Platform section of the user profile.
If the user tries to move ahead without selecting any platform or exceeding the platform limit, the corresponding error message will appear prompting them to select from one up to seven platforms from the list.
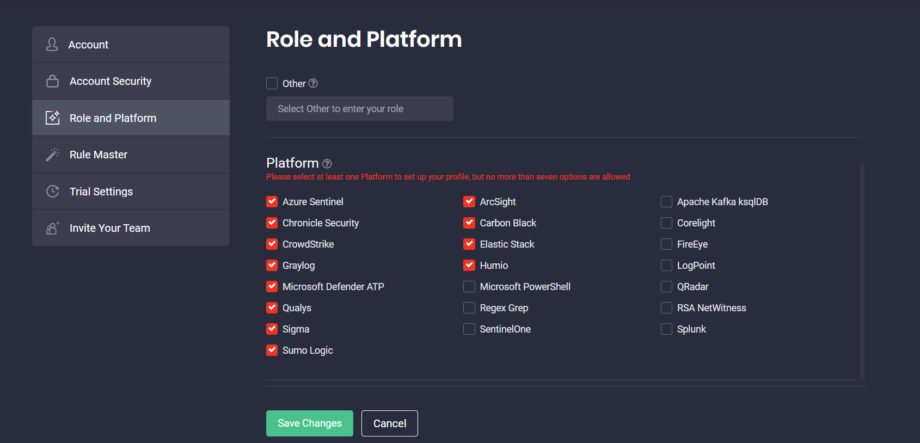
Apart from changes to the platform selection, we’ve also introduced enhancements to the Next button functionality upon registration. Now Threat Detection Marketplace users can see that the button is active once they have entered a name and choos at least one professional role. Also, we’ve added a more user-friendly and informative error message that appears when a security performer has selected the Other checkbox and then clicked Save Changes without specifying their role in the corresponding field.
Warden: Plagiarism Checker Improvements
With each new Threat Detection Marketplace release, we’re striving to add even more enhancements to the Warden functionality to make sure all detections written by our content contributors are unique and there are no rule duplicates. This latest update has brought in a major improvement to the plagiarism checker that scans content for required attributes to the specific fields in the Sigma source code. If such fields are empty, content authors can now see the corresponding Warden issues displayed on the Scan Result pop-up under the Error or Warning sections.
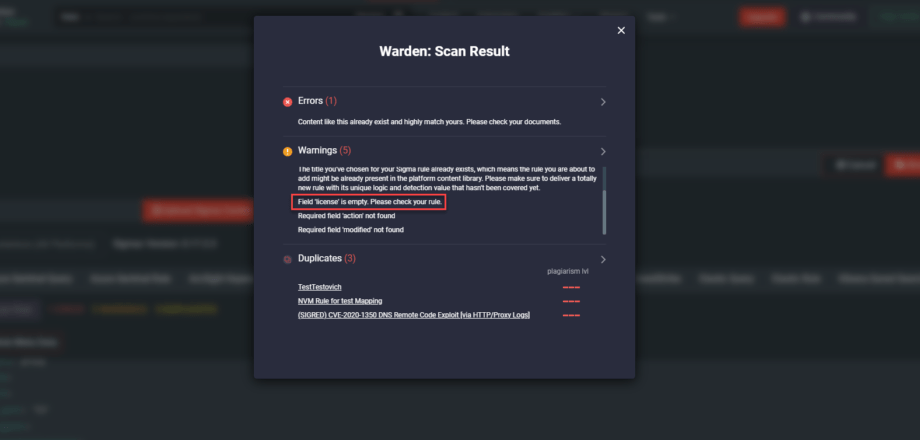
Additionally, with this Warden release, we’ve added a bunch of enhancements to properly check the specific rule fields:
- Created a new repository that now includes all configurations related to the logsource, detection, and tags fields.
- Added new functions for checking the logsource field. If the log source doesn’t match any of the set configurations, Warden displays an error message that the log source value doesn’t match the provided log source type.
- Similarly, created new functions to check the detection fields and tags whether they match the configurations. If these newly added functions don’t find any matches with the existing fields in configurations, the system displays an error message about the unknown fields.
Help Center Updates
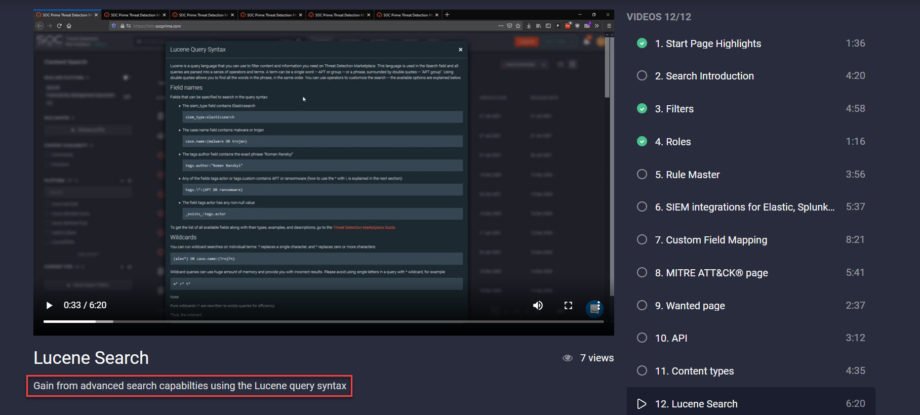
With this latest platform release, we’ve added an updated walk-through video to the Help Center > Videos section highlighting the Lucene search capabilities. To scan at a glance what this video covers, we’ve also added a brief video description.
Content Improvements for Better Look and Feel
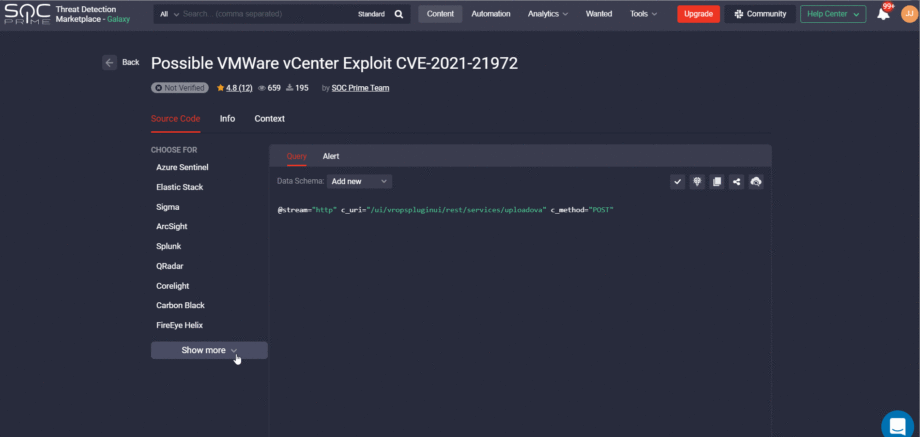
To deliver the most intuitive user experience for security performers leveraging our Detection as Code platform, we’ve recently added a couple of enhancements to the Rules and Rule Packs content types. From now on, the Copy URL to Clipboard link to the action panel of the above-mentioned content items is available in Threat Detection Marketplace. This functionality allows copying the content URL on the fly and then pasting it to the clipboard with just a single click. Security performers will see a success notification once the link is copied.
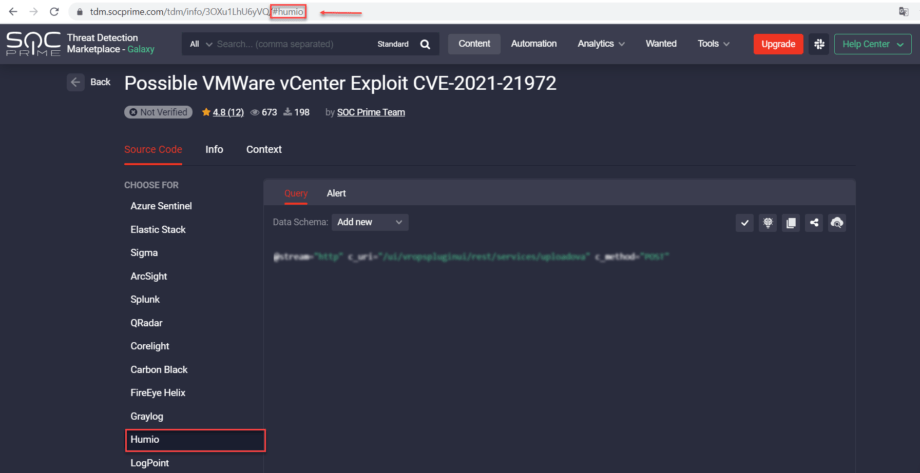
Also, for a better threat detection experience, security practitioners can now see the selected platform tab for the specific Rule or Rule Pack content types right in the URL address. We’ve added the # followed by the name of this platform as a query parameter directly to the content URL address instead of the platform ID, which adds to a more intuitive user experience.
Key Bug Fixes & Improvements
To master the existing functionality of Threat Detection Marketplace and make your platform experience smother, version 4.7.0 fixes a set of bugs. With the latest upgrade, we’ve enhanced the following:
- Fixed the issue on the Leaderboards page > Release Dynamics chart when filtering by All Content. Now filtering by All Content also includes unique content results:
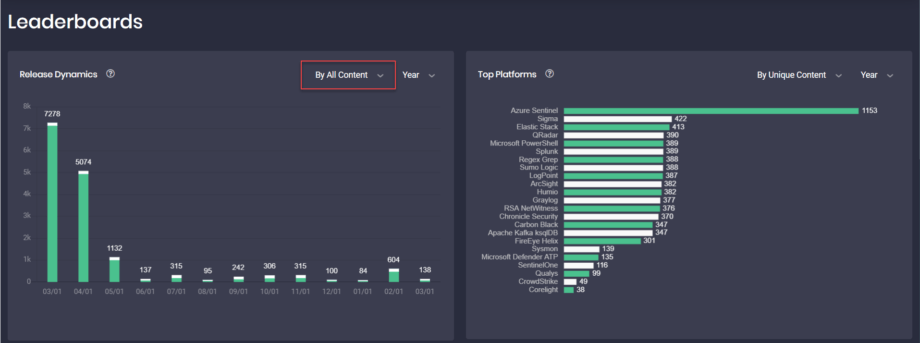
- Fixed the issue with the inconsistent number of search results displayed on the Content page after filtering. Before the update, the number of content items next to Search Results and the content amount displayed next to the pagination view options at the bottom was different
- Fixed the issue with displaying a GIF image when clicking Rule Master for users with the Limited Access subscription
- Made enhancements to the Dashboard page when drilling down to the pop-ups with stats details
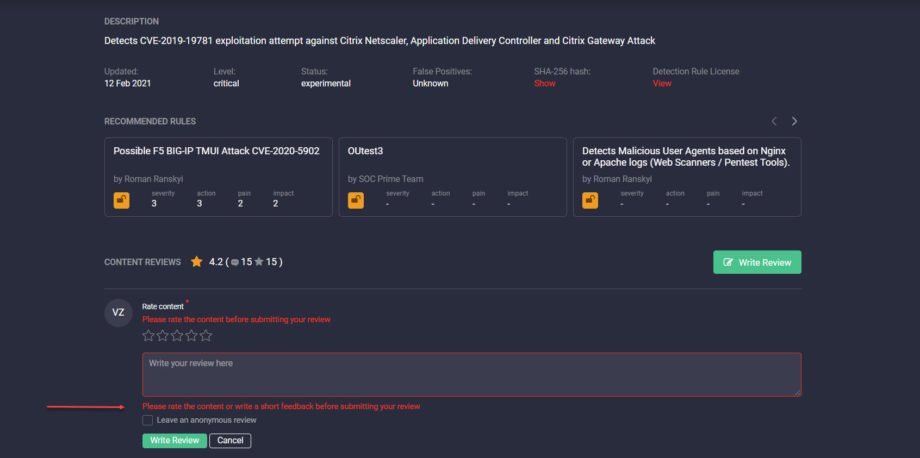
- Fixed the error message alignment to the left in the Content Reviews block for Firefox to achieve consistency across all browsers
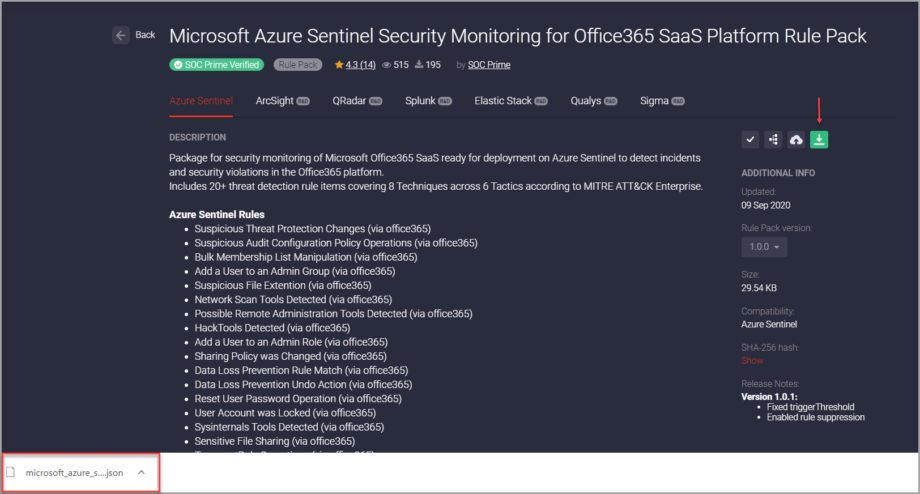
- Fixed the issue with downloading the Rule Pack content for Azure Sentinel when clicking the Download button. Before this release, the content was displayed in the JSON format in the separate browser window rather than being downloaded to the local user’s disc
- Fixed the issue for the Threat Detection Marketplace API with downloading rules for the Elastic Stack and deploying them to Kibana by changing the .txt file extension to the *.ndjson format and removing all line breaks (“\n”)
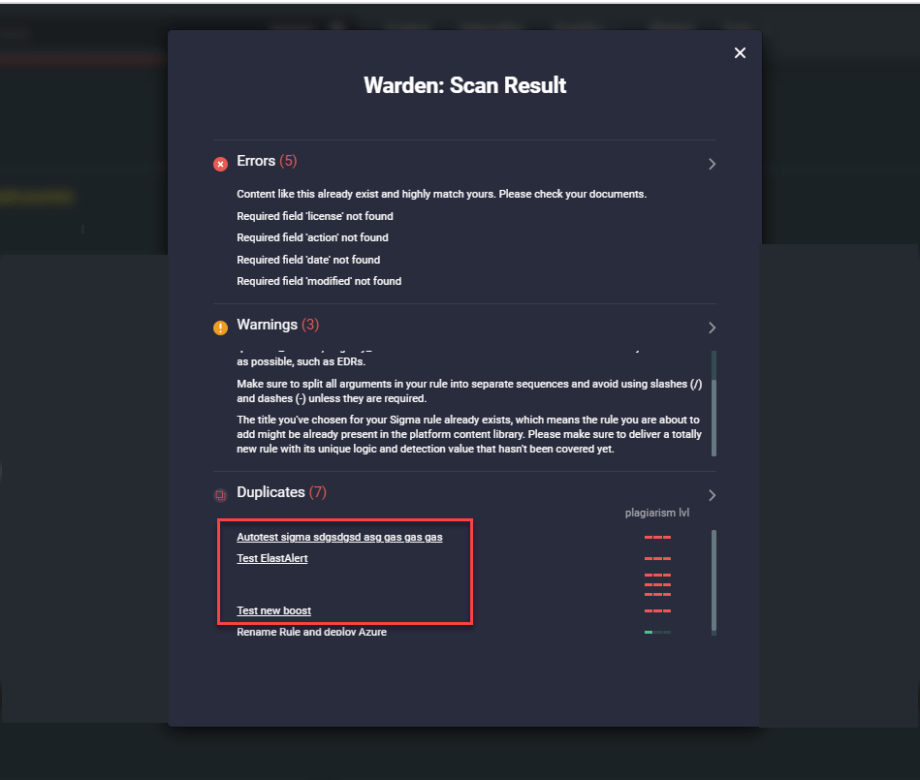
- Fixed the Warden issue on the back end that prevented displaying the Sigma rule names and links to them on the Scan Result pop-up under the Duplicates section
Subscribe to Threat Detection Marketplace, the world-leading Detection as Code platform for SOC content that provides access and support to 100,000+ detection and response algorithms for 23+ market-leading SIEM, EDR, and NTDR technologies. Want to craft your own detections and share them with the global community of cyber defenders? Join our Threat Bounty Program!


