On March 24, 2021, we released version 4.6.0 of Threat Detection Marketplace to enhance the existing capabilities of our Detection as Code platform. With this latest upgrade, we’ve launched the Calendly integration to provide on-the-fly communication with the Customer Success Team and added the ability for our customers to invite their colleagues and peers to explore the platform. Also, this release introduces content type and language format localization improvements, enhances the Uncoder.IO functionality, boosts role-based platform experience, and advances the logic for displaying use case icons.
Upgrade Page: Calendly Integration
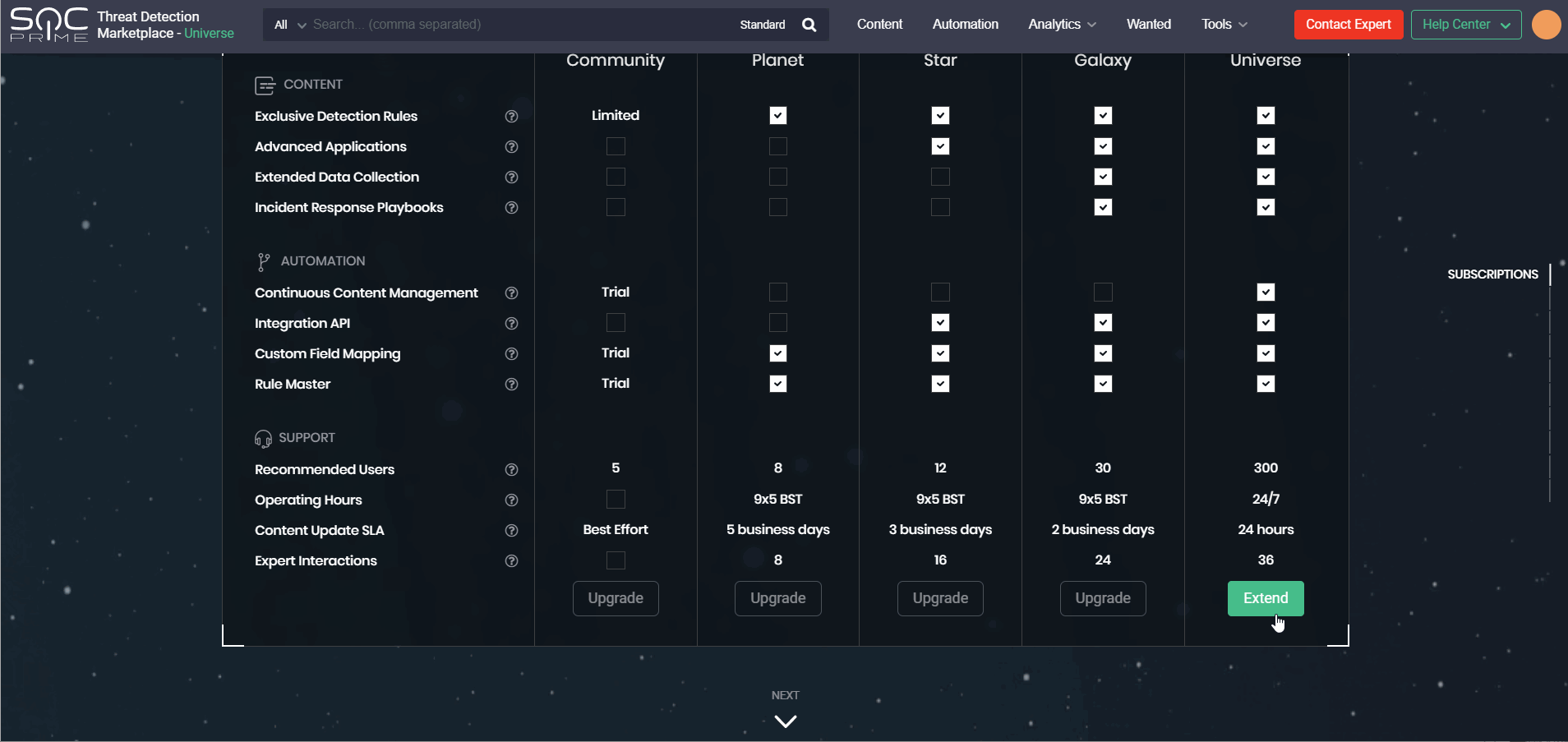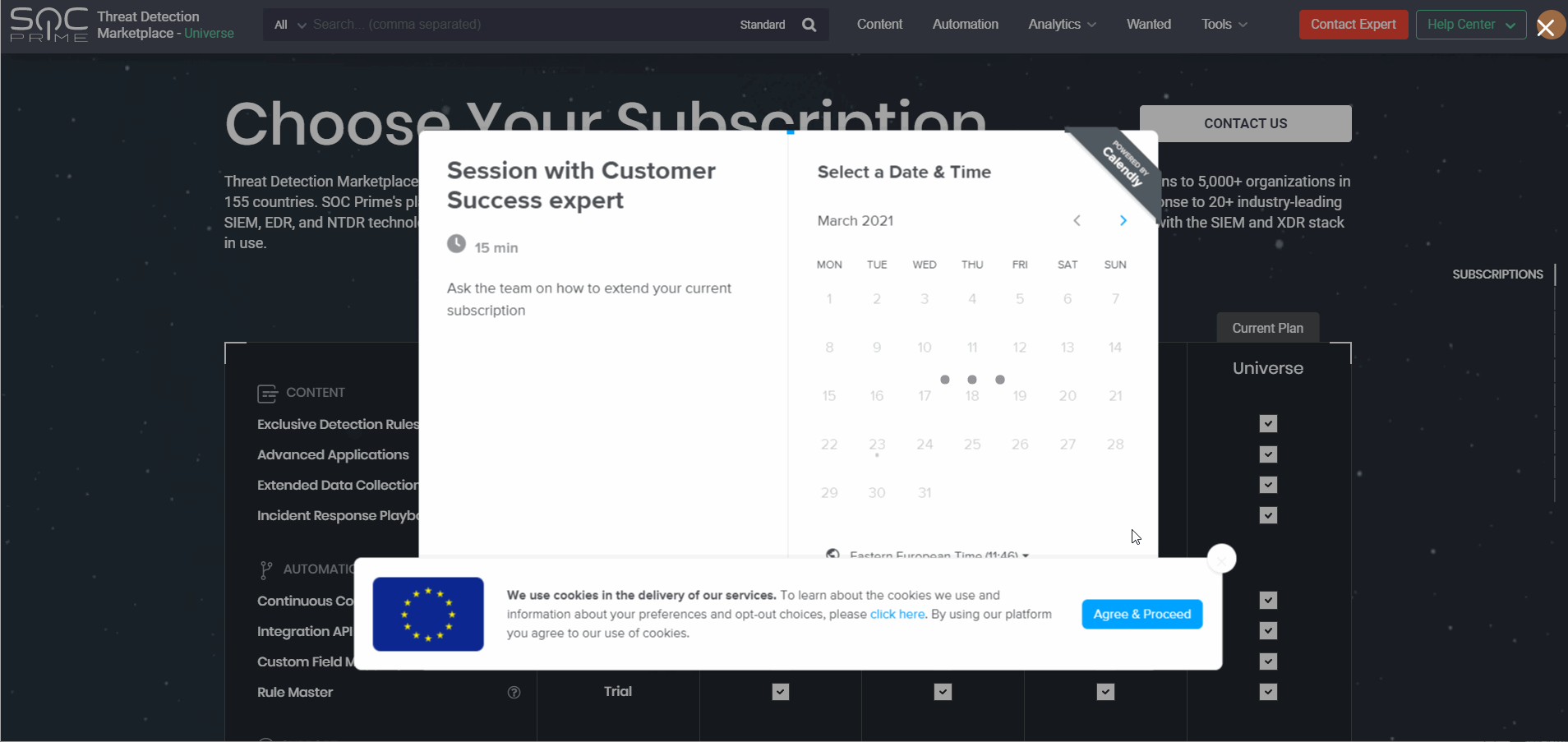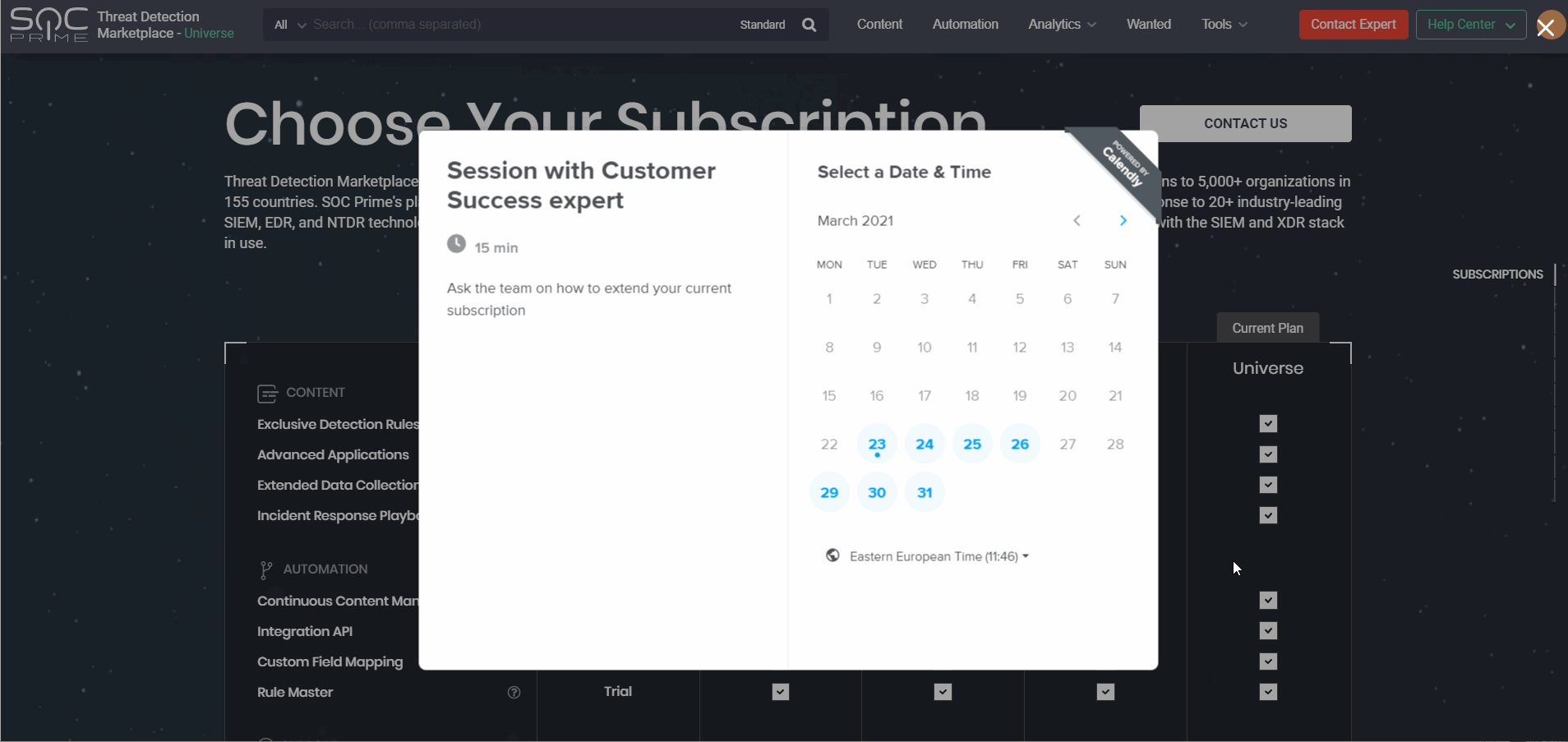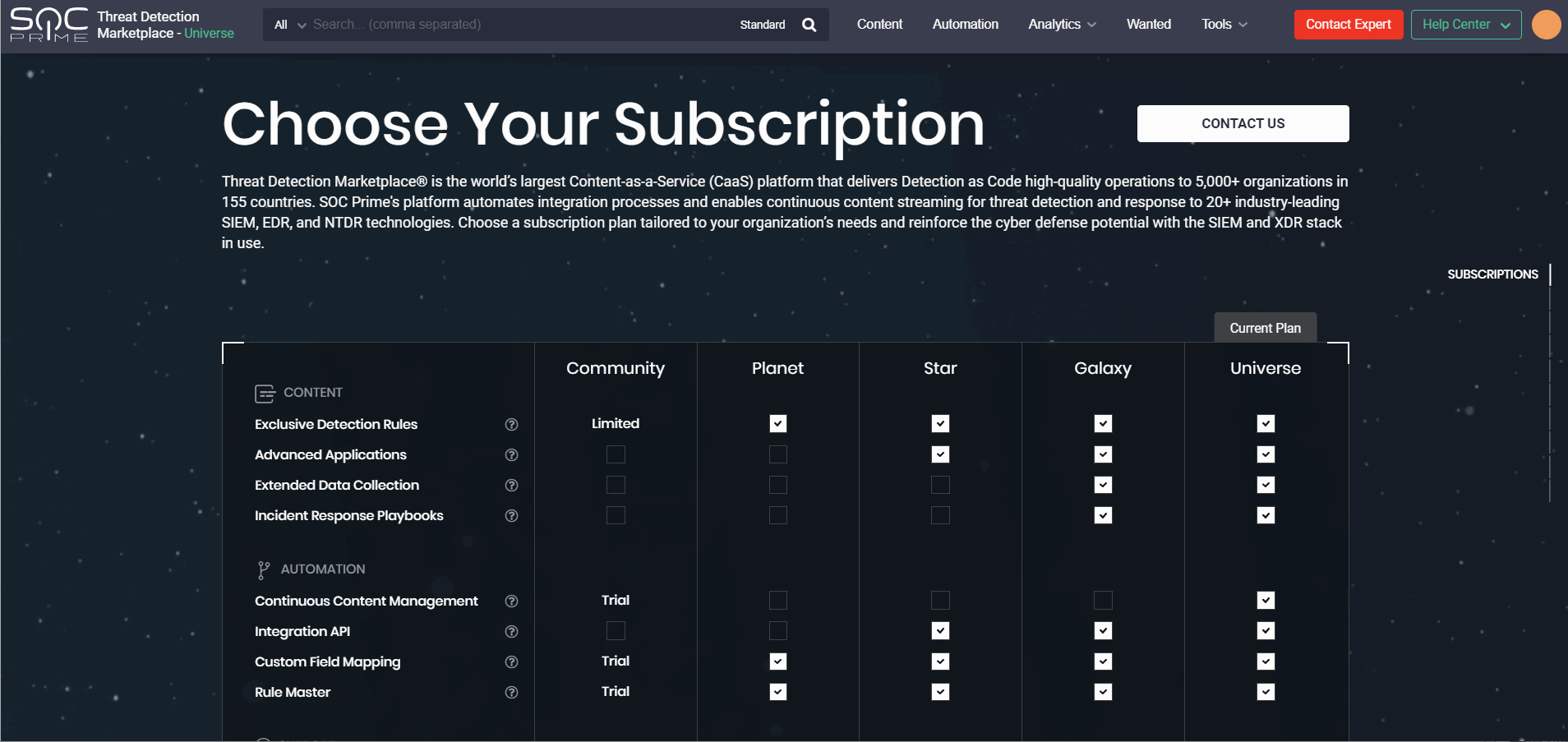
Getting in touch with our team and resolving the subscription issues has become even smoother and faster. In version 4.6.0, we’ve added the Calendly integration to the Upgrade page that allows scheduling on the fly a deep dive session with the Customer Success Team to discuss the possibilities of extending the current subscription. This functionality is available for the following paid subscriptions:
- Planet
- Star
- Galaxy
- Universe
The Calendly pop-up appears by clicking either of the following:
- Extend from the Choose Your Subscription section
- Extend Current Plan from the specific paid subscription section
Also, with this release, we’ve added the ability to automatically notify users of their subscription change to Community as soon as their Premium subscription expires. Now security performers will receive a system notification to their email address informing them of the automatic subscription change. Threat Detection Marketplace users whose Premium subscription has expired can always upgrade from Community to one of the paid plans matching their business needs and tailored to the company’s budget.
Invite Your Team
To support community initiatives and promote cybersecurity networking, we’ve expanded the abilities of our customers to invite their colleagues to Threat Detection Marketplace. Previously, users could invite their team members to join the platform only if they had the Company Manager user role. This functionality is available in the Team Members section of the user profile and visible only for Company Managers.
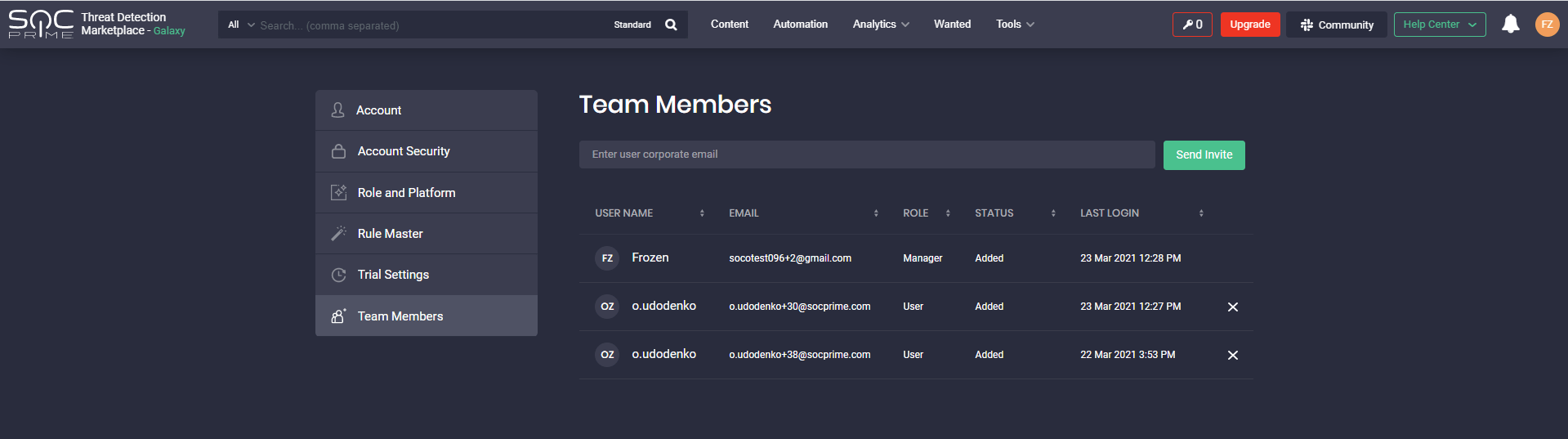
With this latest update, security performers whose Threat Detection Marketplace account is linked to the corporate email address can now invite up to 10 teammates to the platform. To invite a colleague, users need to enter their email address and click the Send Invite button. Once sent, the emails of team members who have been invited will have the Pending status. As soon as these users sign up for the platform, the status changes to Invited.
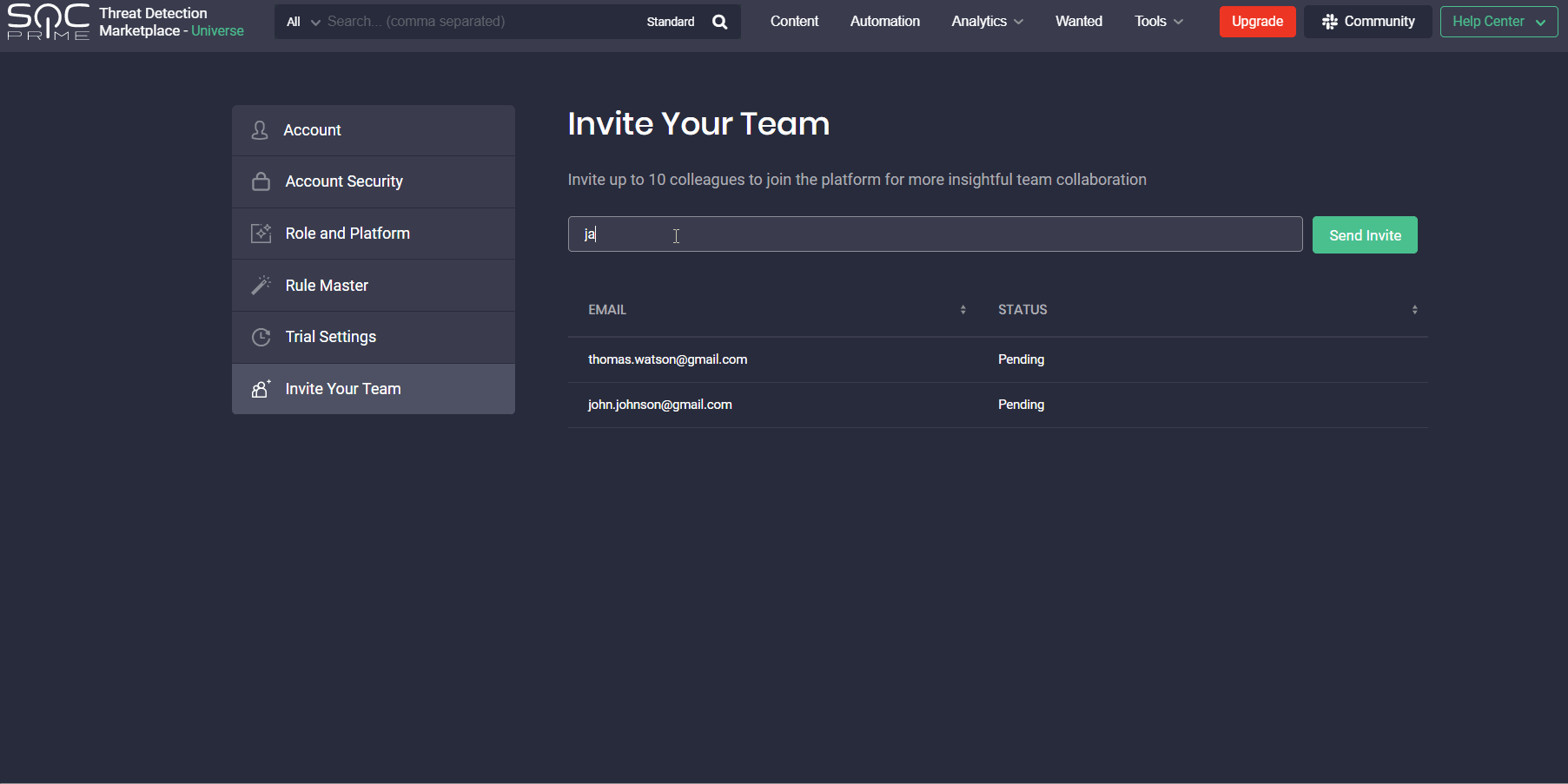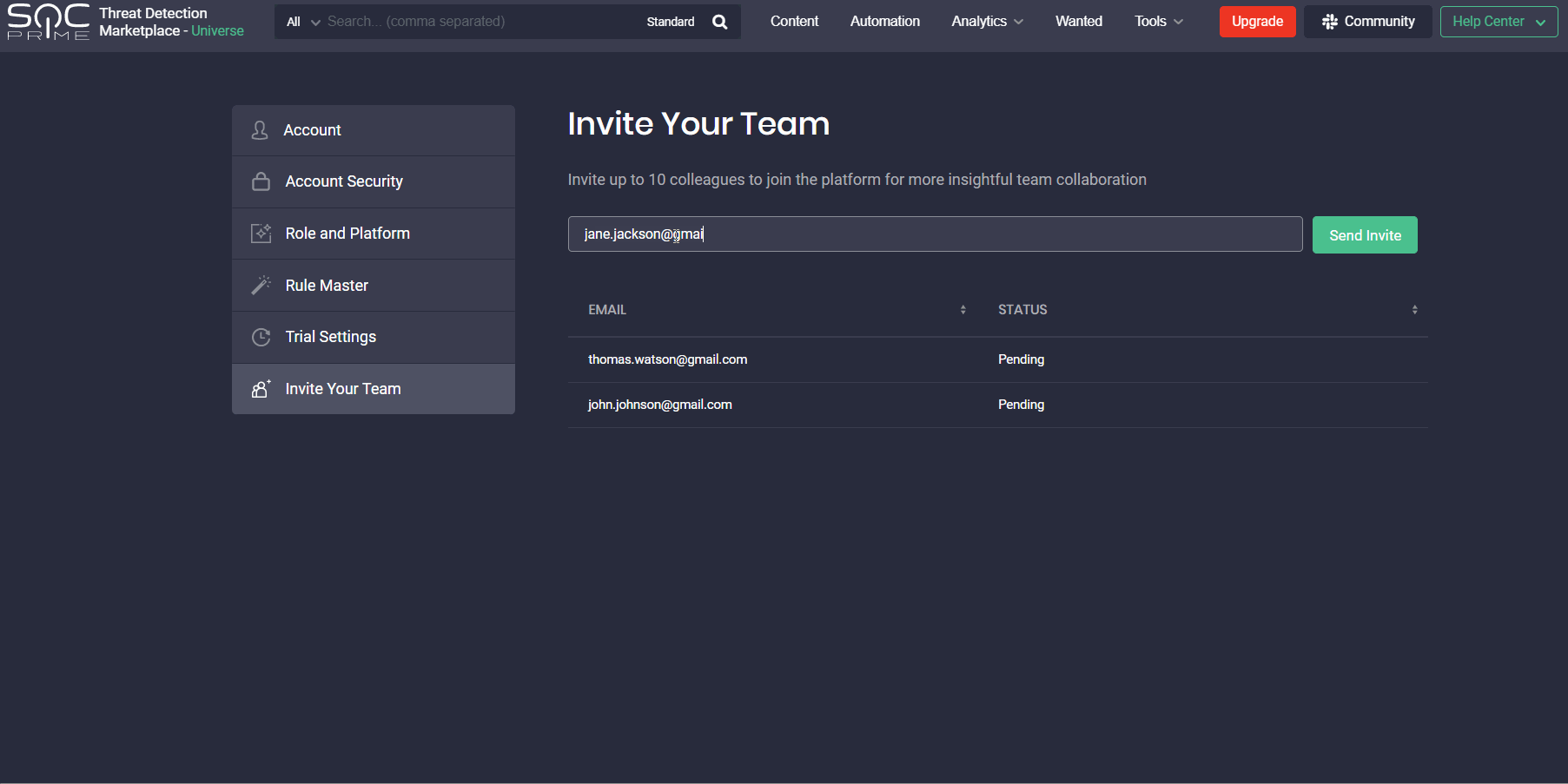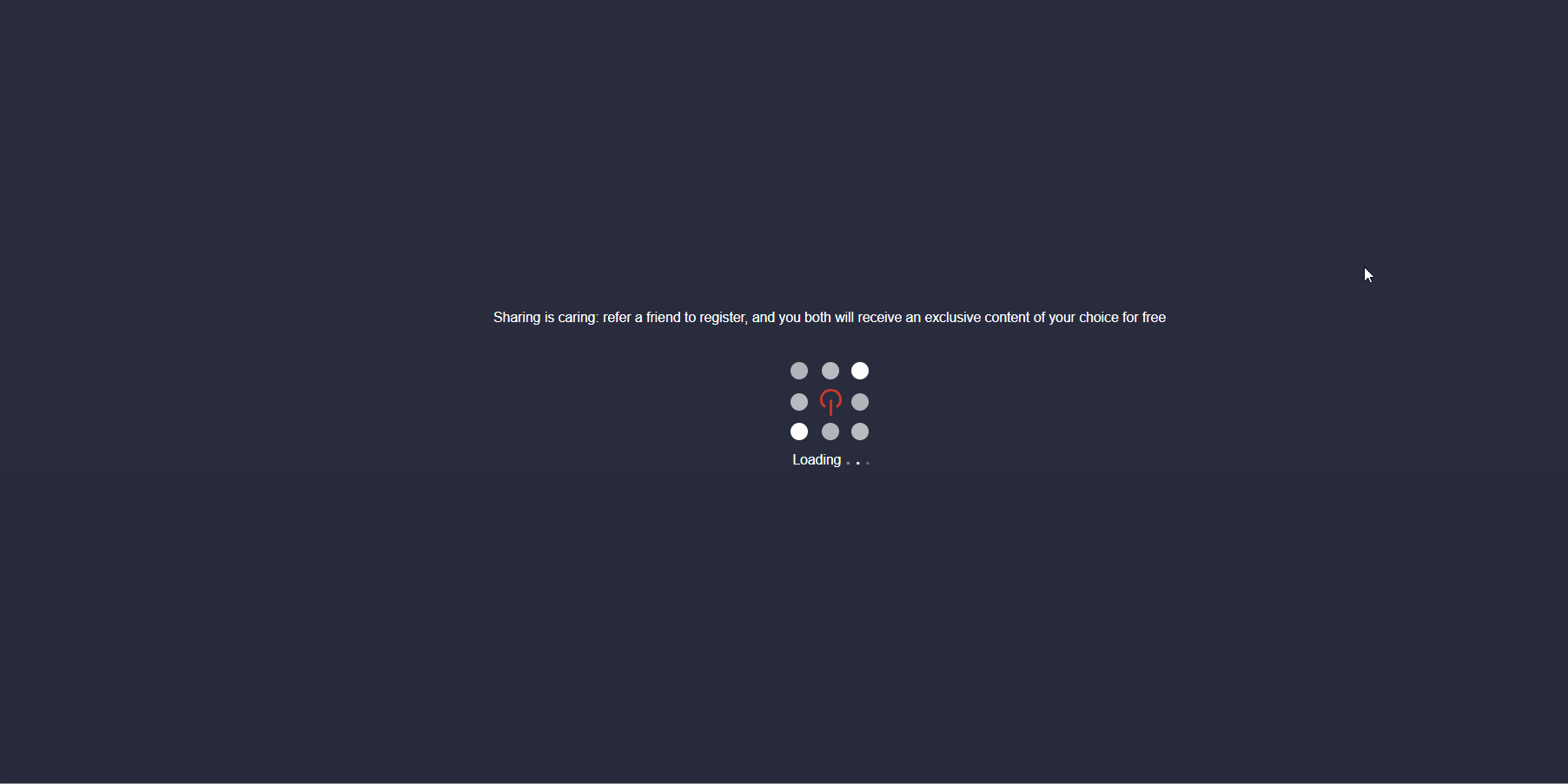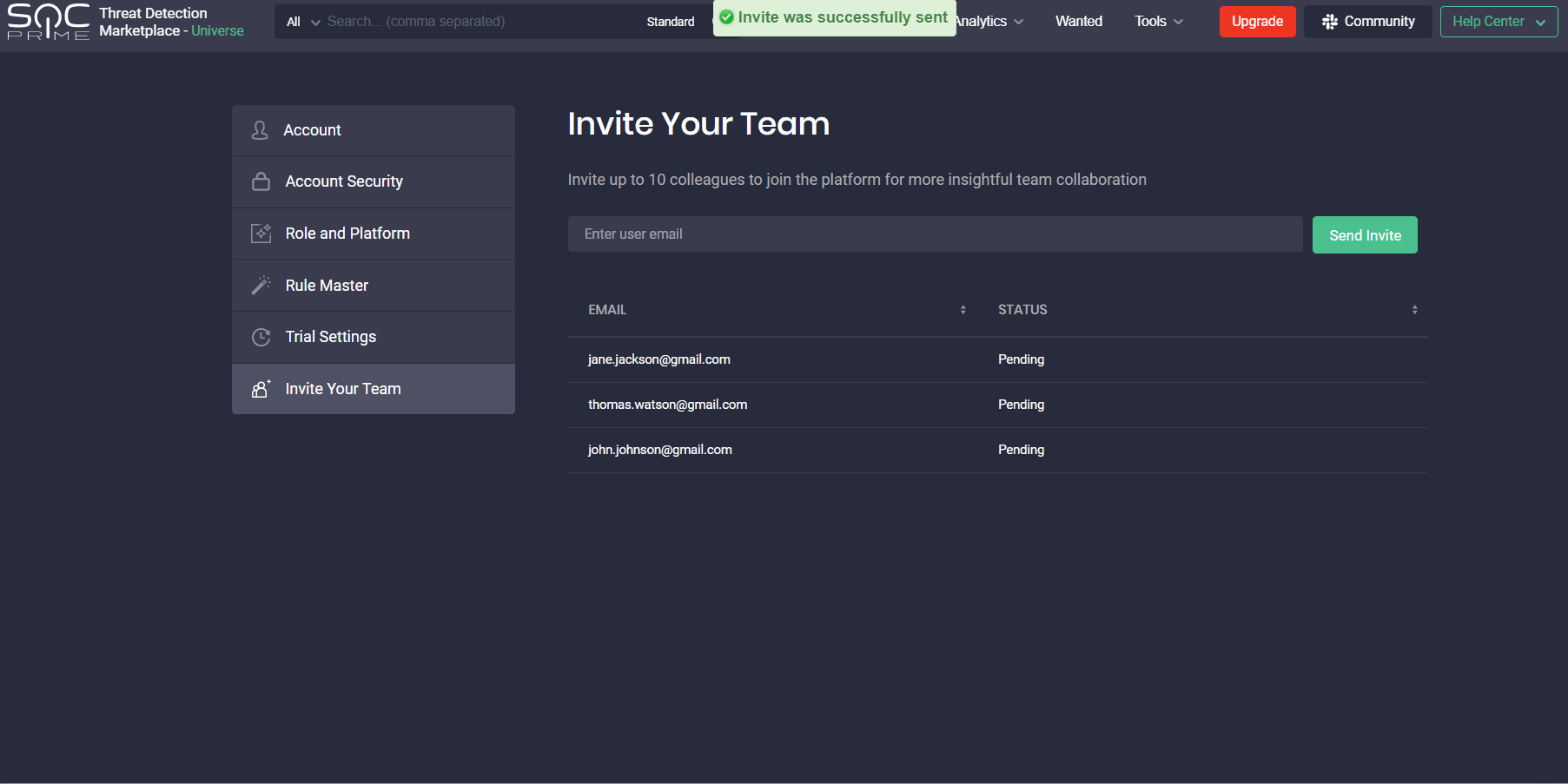
Note: The Invite Your Team section is NOT available in the user profile for users:
- With the Limited Access subscription
- With the Company Manager user role who will see the Team Members section with the similar functionality instead
Elastic Stack: Localization Improvements
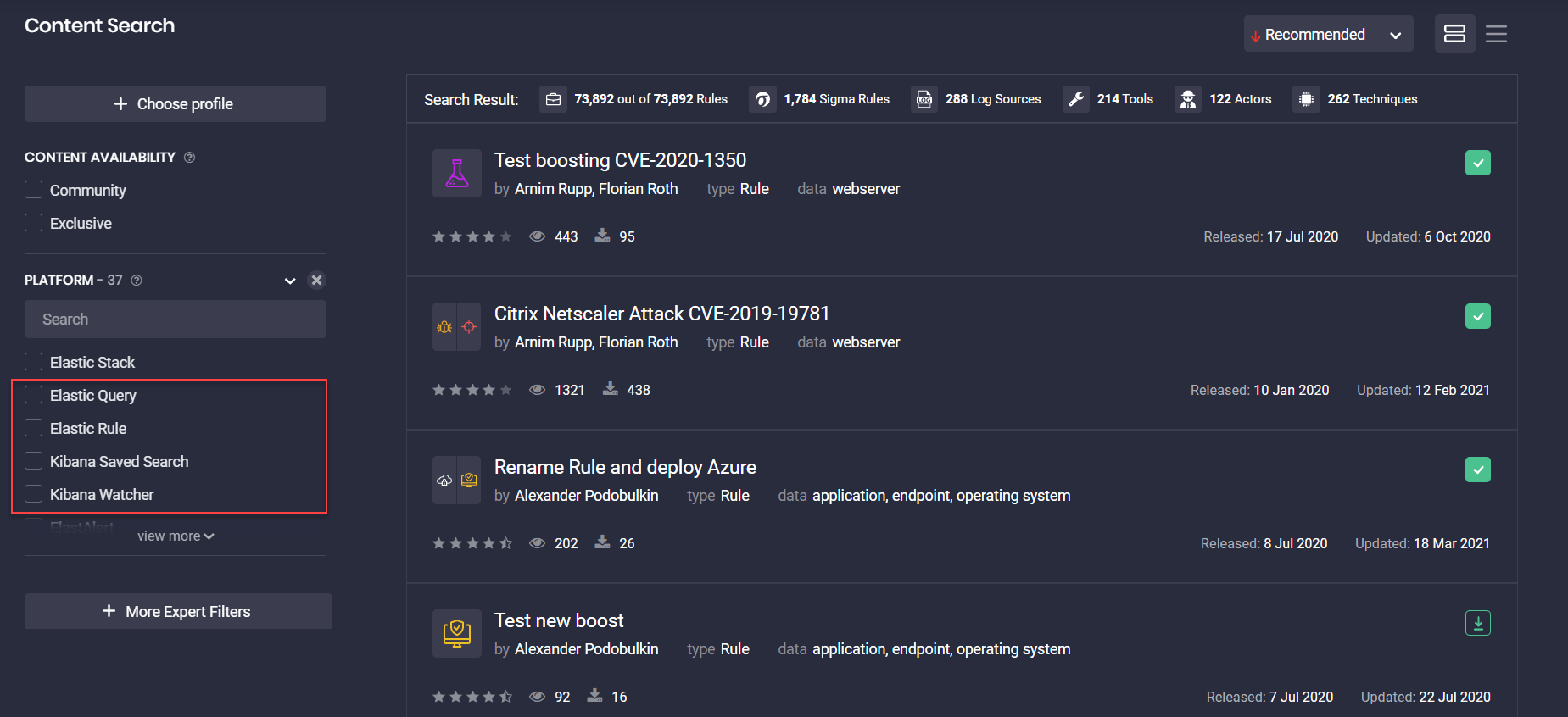
To provide a more native platform experience, Threat Detection Marketplace version 4.6.0 implements a number of Elastic Stack content type & localization improvements that ensure consistency with Elastic product naming. The localization improvements to the Elastic Stack content types are as follows:
- Rule Alerts → Detection Rules
- Watcher Alert → Watcher
In addition, we’ve updated localizations for the following Elastic SIEM-native language formats in Filters > Platforms:
- Elasticsearch → Elastic Query
- X-Pack Watcher → Kibana Watcher
- Kibana → Kibana Saved Search
Uncoder.IO: Adding Sigma Body and Platform to URL
The latest Threat Detection Marketplace update also brings notable enhancements to our Uncoder.IO service. To make your experience with Uncoder.IO even more streamlined, we’ve added the ability to include the Sigma body and the platform to which the rule is going to be translated right into the URL address. The URL now includes the following parameters:
- to – indicates the platform to which this Sigma rule is going to be converted;
- to_mapping – displays the corresponding mapping for Corelight/Zeek, Sumo Logic, Humio, and SentinelOne;
- sigma – Sigma in the YAML format.
Role Selection During Registration and in User Profile
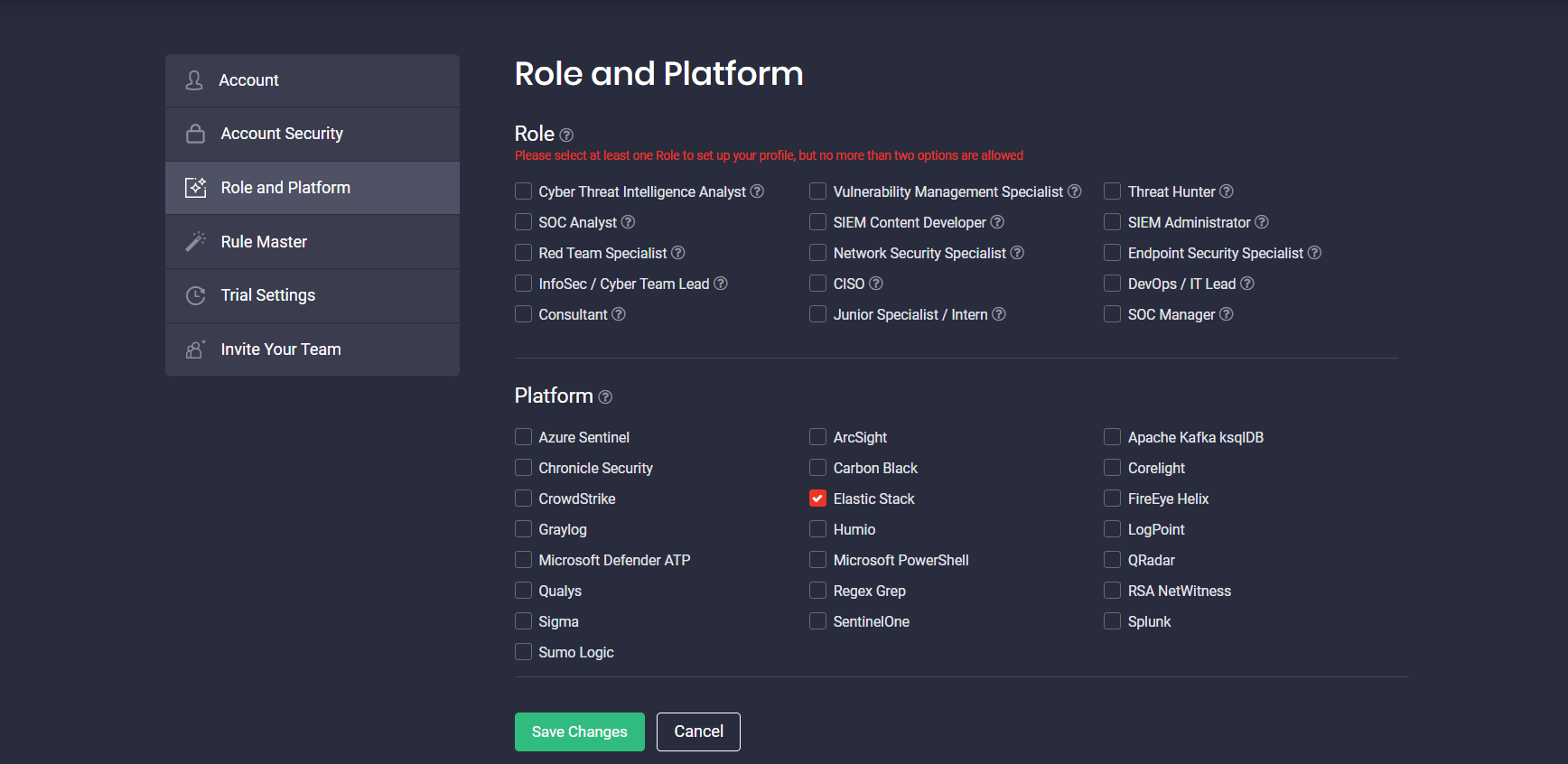
SOC Prime Threat Detection Marketplace is aimed at delivering the most personalized platform experience for security professionals considering their cybersecurity role, as well as SIEM and XDR stack in use. This release has added improvements to the role-based platform functionality by limiting the role selection to a maximum of two options. This helps getting the most relevant content tailored to the specified cybersecurity position. Security practitioners can now see the corresponding tooltip upon registration or in the Role and Platform section of the user profile.
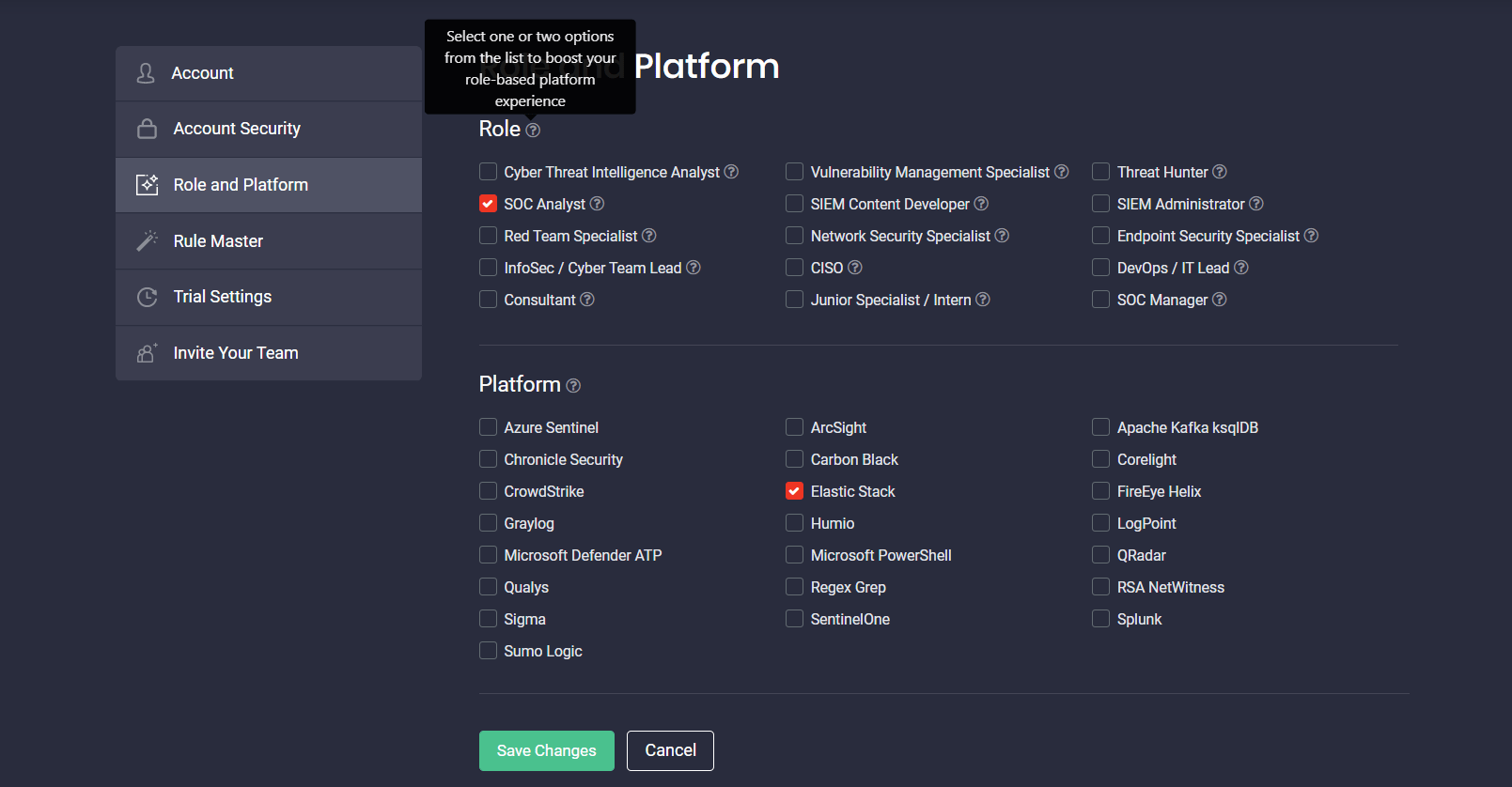
If the user tries to move ahead without selecting any role, the corresponding error message will appear prompting them to select one or two roles from the list.
Use Case Icons
With this Threat Detection Marketplace version 4.6.0, we’ve updated the logic for displaying use case icons that identify the category of content items. Now, content can be identified by multiple use case icons if several categories apply to the specific item. Use case icons appear in the order of priority listed in Filters > Use Cases:
- Proactive Exploit Detection
- Active Directory Security
- Cloud Security
- Endpoint Detection Enhancement
- Threat Hunting
- Compliance
- IOC Sigma
- Mixed / Other
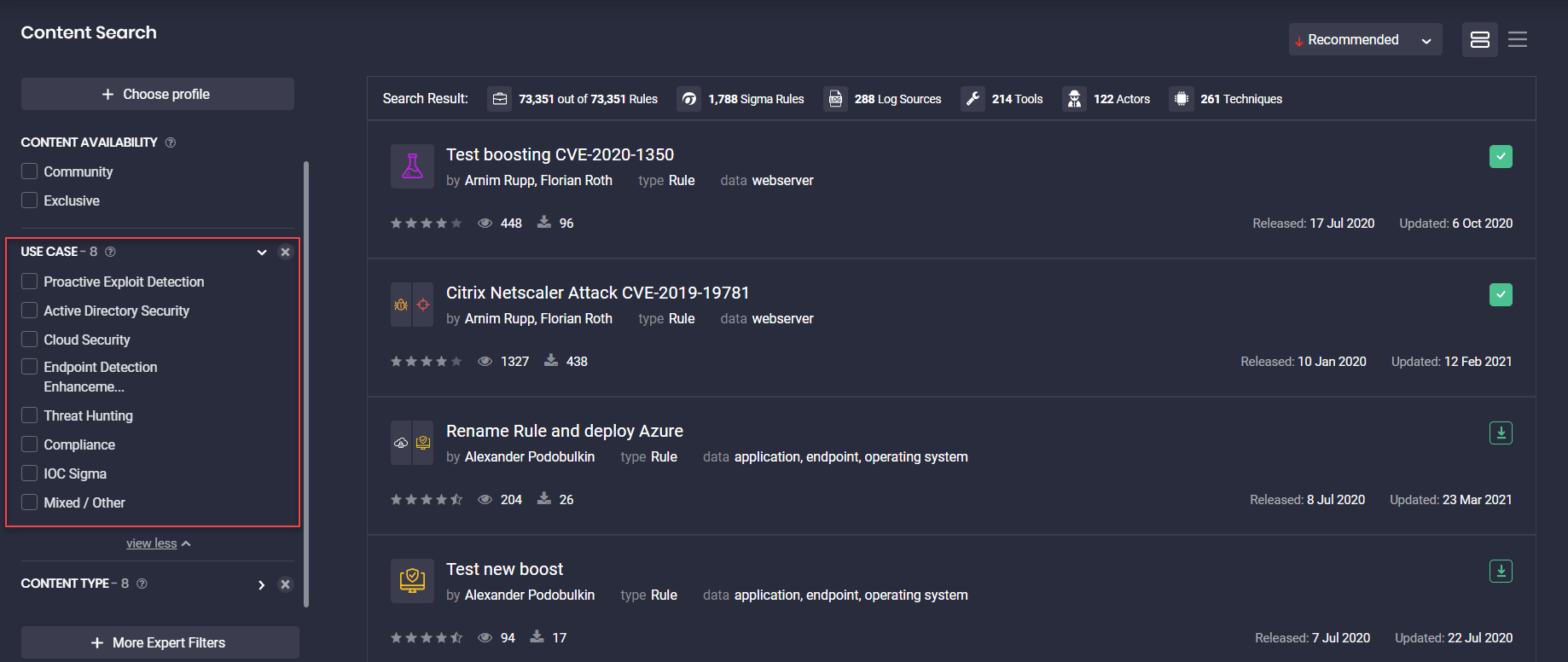
The maximum number of icons that can identify the content item use case is four.
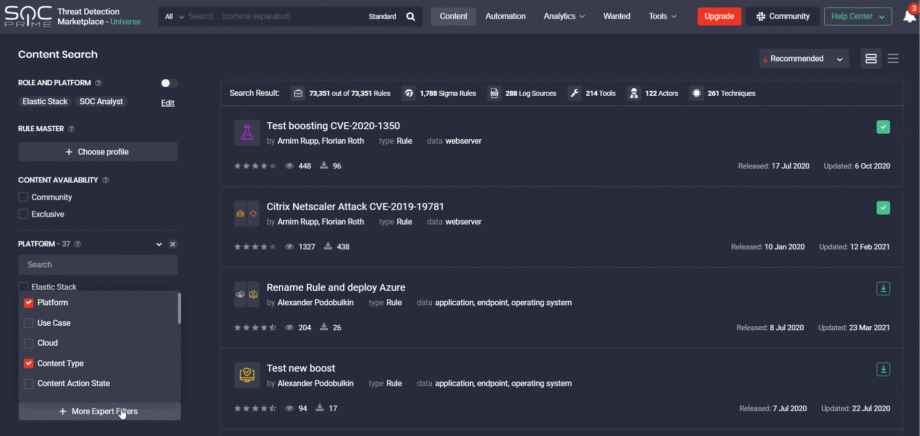
Content items that belong to the Mixed / Other category cannot match any other use cases and are identified by a single icon on the list.
Key Bug Fixes & Improvements
Finally, to master the existing functionality of Threat Detection Marketplace, version 4.6.0 fixes a set of bugs to make your platform experience the most comfortable. With the latest upgrade, we’ve enhanced the following:
1. Made user experience improvements to the two-factor authentication functionality. More specifically, fixed the following issues:
-
- With barcode scanning for iOS
- With clicking the Copy button to save recovery codes for Safari
2. Fixed the issue with deploying rules to the Elastic Stack instance. The issue was fixed by deleting all line breaks (“\n”) before saving the rule to the *.ndjson format:
3. Fixed the issue with Sigma rules containing multiple log sources that failed to display all the necessary details in the metadata field during the second and next translations.
4. As part of user experience improvements, fixed the issue with displaying the Continuous Content Management Free Trial option in the Dashboards > Feature Checklist section for smaller screens:
5. Fixed the issue with displaying a GIF image when clicking More Expert Filters on the Content page for users with the Limited Access subscription:
6. Fixed the scrolling issue on the pop-up for updating content on the fly right from the Inventory page:
Subscribe to Threat Detection Marketplace, an industry-first content-as-a-service (CaaS) platform that aggregates 100K+ detection algorithms and threat hunting queries for 23+ market-leading SIEM, EDR, and NTDR tools. Over 300 contributors enrich our global SOC content library each day to enable continuous detection of the most alarming cyber threats at the earliest stages of the attack lifecycle. Enthusiastic about creating your own detection content and contributing to global threat hunting initiatives? Join our Threat Bounty Program and get rewarded for your input!


