Threat Detection Marketplace 4.6.0: Major Continuous Content Management Updates
Continuous Content Management Updates
To boost your threat detection and response speed, we are constantly mastering our Continuous Content Management (CCM) module that enables automated SOC content streaming directly into the security solution of your choice. The latest Threat Detection Marketplace version 4.6.0 brings in major innovations to the CCM functionality, including the expanded list of supported security tools, migration to the new architecture, improvements to the overall platform experience, and more.
Support for Sumo Logic
At SOC Prime, we’re continuously broadening the support for various SIEM, EDR, and NTDR solutions in use. With this latest release, we are happy to announce the newly added support for Sumo Logic as part of the CCM module. Security performers leveraging Sumo Logic can now deploy Queries by running the inventory script, make updates to the deployed content, and stream these changes into their SIEM instance on the fly.
Back-End Optimization: New Architecture
Furthermore, we are pleased to inform you that now all platforms supported by CCM — including Microsoft Azure Sentinel, Sumo Logic, Humio, and Elastic Cloud — are implemented on the new back-end architecture. This significantly contributes to the performance optimization and better maintenance of the CCM module.
Content List Enhancements
Also, with this latest release, we’ve introduced multiple platform experience enhancements to provide an even more smooth workflow. For example, we’ve added the ability to view information on the user who created the content list and who was the last to make updates to it. These features have been implemented at a SOC Prime customers’ request. Security performers can now see the following details:
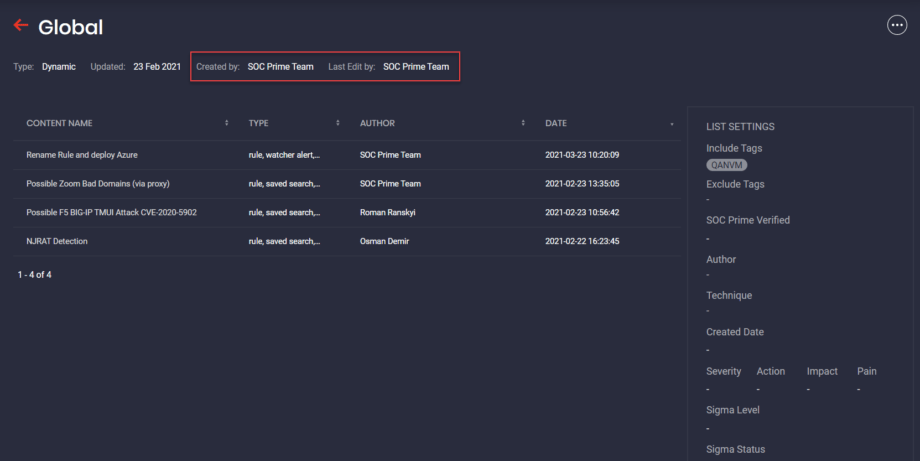
- For All and My lists, next to the Last Edit by label, the username of the person who made the last update:

- For Recommended lists, the “SOC Prime Team” will appear as a single value for Created by and Last Edit by labels:
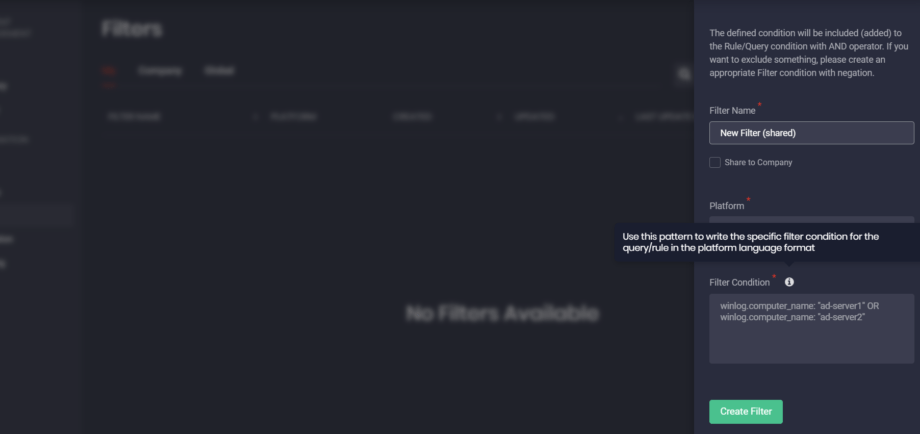
Filter Condition: Tooltips and Placeholders
To help security performers correctly fill in filter conditions for various language formats, we’ve added tooltips to the Filter Condition field on the Create Filter pop-up. In addition, we’ve broadened the list of placeholders with the query example for the Elastic (Watcher Alert) language format.
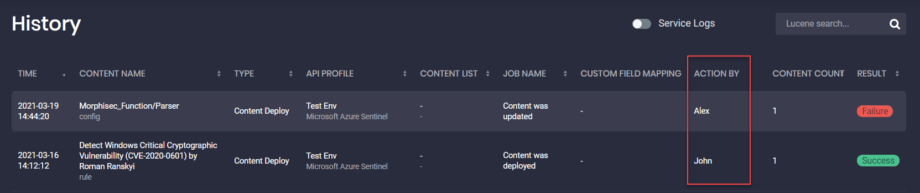
History: Action By Details
For a more streamlined experience with the CCM module, we’ve added the Action By column to the History page, so security practitioners can keep track of all user action logs within the company. The Action By column displays the username of the person who has performed a certain action on the History page.
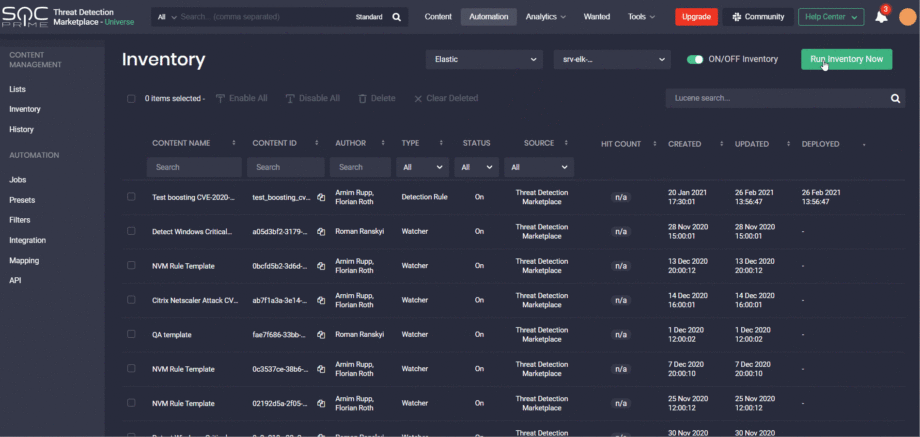
Inventory Manual Launch for All Platforms
Finally, the latest Threat Detection Marketplace update brings notable improvements to the Inventory. Security performers can now manually run their content inventory script for enabled API profiles for all cloud-native SIEMs that the CCM module currently supports, including Azure Sentinel, Sumo Logic, Humio, and Elastic Cloud.
To manually run the script, click the Run Inventory Script button in the upper right-hand corner of the Inventory page. The button is active once the Inventory toggle switch next to the selected API profile for a certain SIEM is ON.
Note: The Run Inventory Script button is active and can be clicked if at least 10 minutes have passed since the last inventory script launch to prevent this script and SIEM data from overload. Otherwise, the button won’t be active.
After clicking the Run Inventory Script button, you can see the following details:
- The name of the related API Profile to be launched
- The date and time of the last script launch
To complete the manual inventory script launch, click the Confirm button.
Searching for the best SOC content compatible with your SIEM, EDR, and NTDR solutions in use? Get a subscription to our Threat Detection Marketplace and obtain 100K+ detection and response rules easily convertible to various language formats. The content base enriches every day thanks to the joint efforts of our international community of 300+ security performers. Enjoy coding and eager to contribute to the industry-first SOC content library? Join our Threat Bounty Program!


