Threat Detection Marketplace 4.12.0 Is Released
On June 16, 2021, we released Threat Detection Marketplace version 4.12.0 to improve the existing functionality of our Detection as Code platform and provide customers with a cutting-edge security intelligence experience. The latest update brings in the support for Securonix SIEM, provides major content quality enhancements, introduces a redesigned version of the Threat Bounty program landing page, advances Rule Master and Warden functionality alongside other platform improvements.
Securonix Support
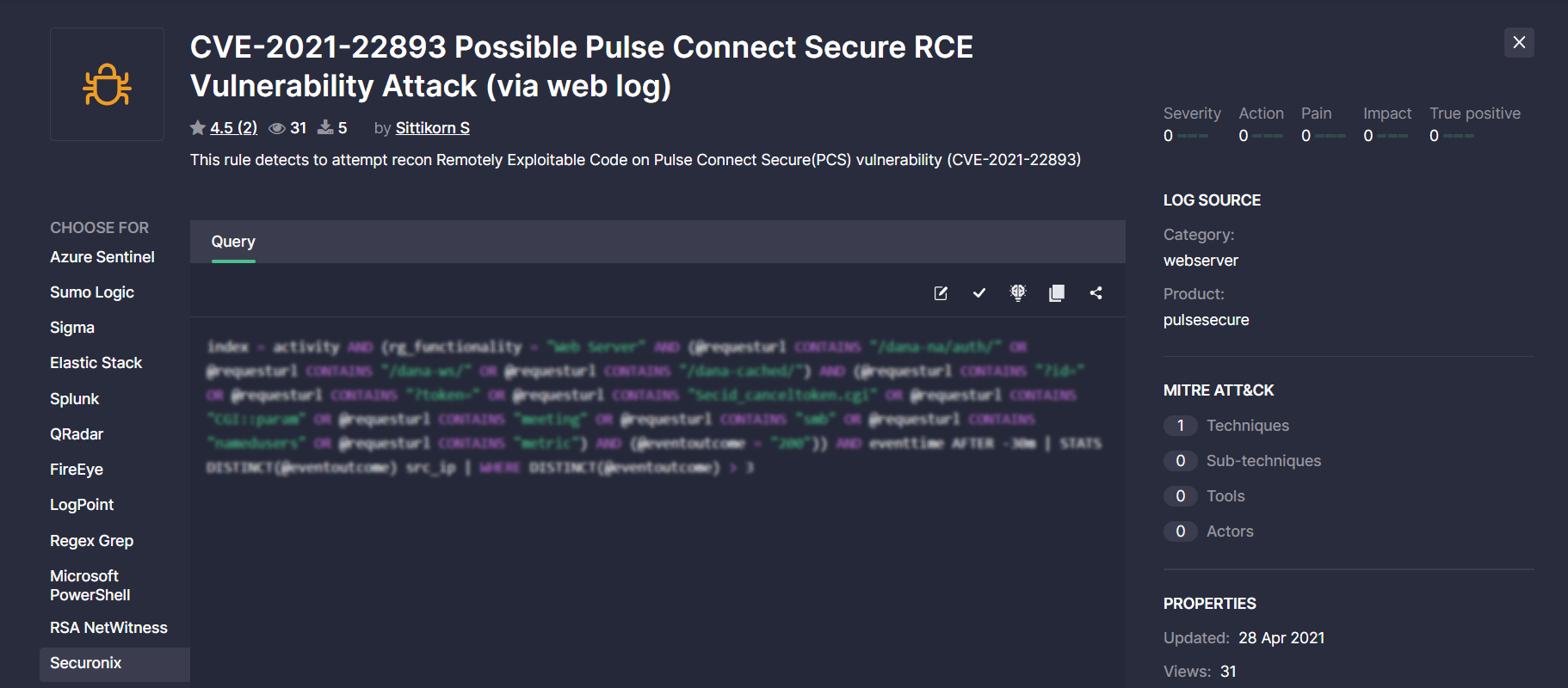
At SOC Prime, we are continuously broadening the support for various SIEM, EDR, and NTDR language formats to make sure our Detection as Code platform delivers cross-tool content tailored to the majority of security solutions. With this latest release, we’ve added the support for the Securonix next-gen SIEM.
Threat Detection Marketplace customers leveraging Securonix can now streamline their search experience by applying this security solution from the Platform filter options.
When drilling down to a certain rule from the filtered list, security performers will see at once the Securonix Query tab selected with the source code converted to this language format.
The statistics on available translations over the selected time period for the Securonix SIEM are also available on the Top Platforms bar chart on the Leaderborads page.
Content Quality Enhancements
At SOC Prime, we’re constantly striving to improve the content quality when translating Sigma behavior-based detections to various SIEM, EDR, and NTDR language formats.
Carbon Black Translation Improvements
With this latest release, we’ve improved content translations to the Carbon Black language format. More specifically, we’ve added the ability to translate Sigma detections with multiple selection values and certain keywords to the Carbon Black language format based on AND / OR operators.
Corelight Translation Improvements
To enable a seamless threat detection experience, we’ve recently improved translations to the Corelight language format. This latest translation enhancement involves replacing the wrongly generated translations that contain the :< and :> symbols with the corresponding < and > symbols omitting a colon (:).
Google Chronicle Translation Improvements
For a seamless threat detection experience of Google Chronicle customers, we’ve improved regular expressions that expect specific values for file paths or executables and numeric values. Additionally, we’ve resolved the issues with quotation marks for specific fields like ports and response codes. As part of the latest Google Chronicle translation improvements, we’ve also made the corresponding enhancements to prevent the file hash issues when converting content items to the YARA-L format. Now, Threat Detection Marketplace users have the ability to convert hash values to lowercase, check the length of the hash value, and based on it determine the hash type.
Sigma Rules with Multiple Log Sources
Sigma behavior-based detections that contain multiple log sources are known to cause issues when translating them into various language formats. With this release, we’ve made improvements when translating such Sigma detections to the Elastic Detection Rule format. Before the update, security performers encountered an issue when trying to download such converted detections as one .ndjson file containing a single array with multiple rules. To enable a seamless detection experience in the customer’s Elastic Stack environment, now each log source within the original Sigma rule can be saved as a separate .ndjson file when converted to the Detection Rule format. This allows downloading the exact number of files that equals the number of log sources the original Sigma rule has. Also, with this release, we’ve improved Sigma rule translations with multiple log sources to the Google Chronicle platform.
Ability to Edit Rule on the Rule Page
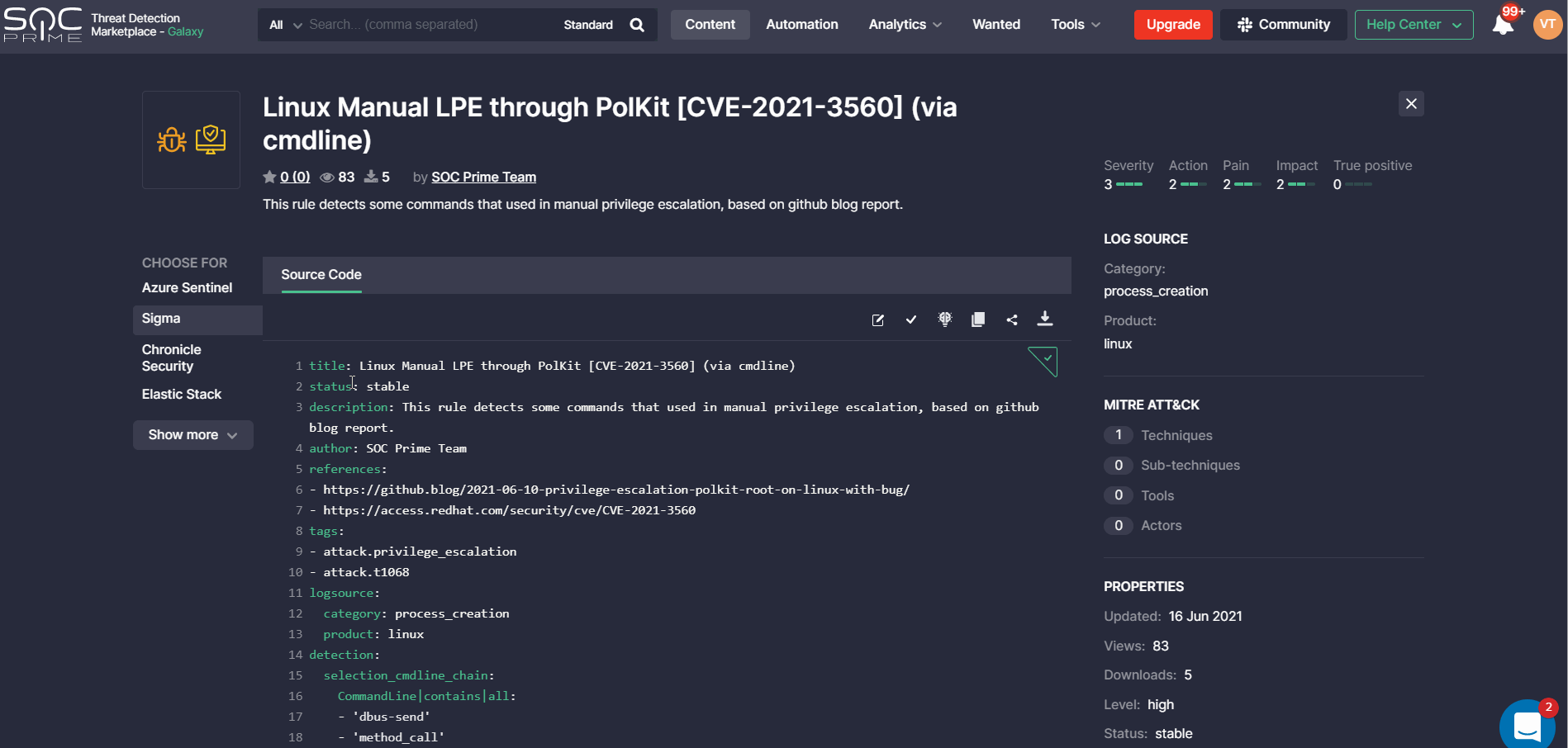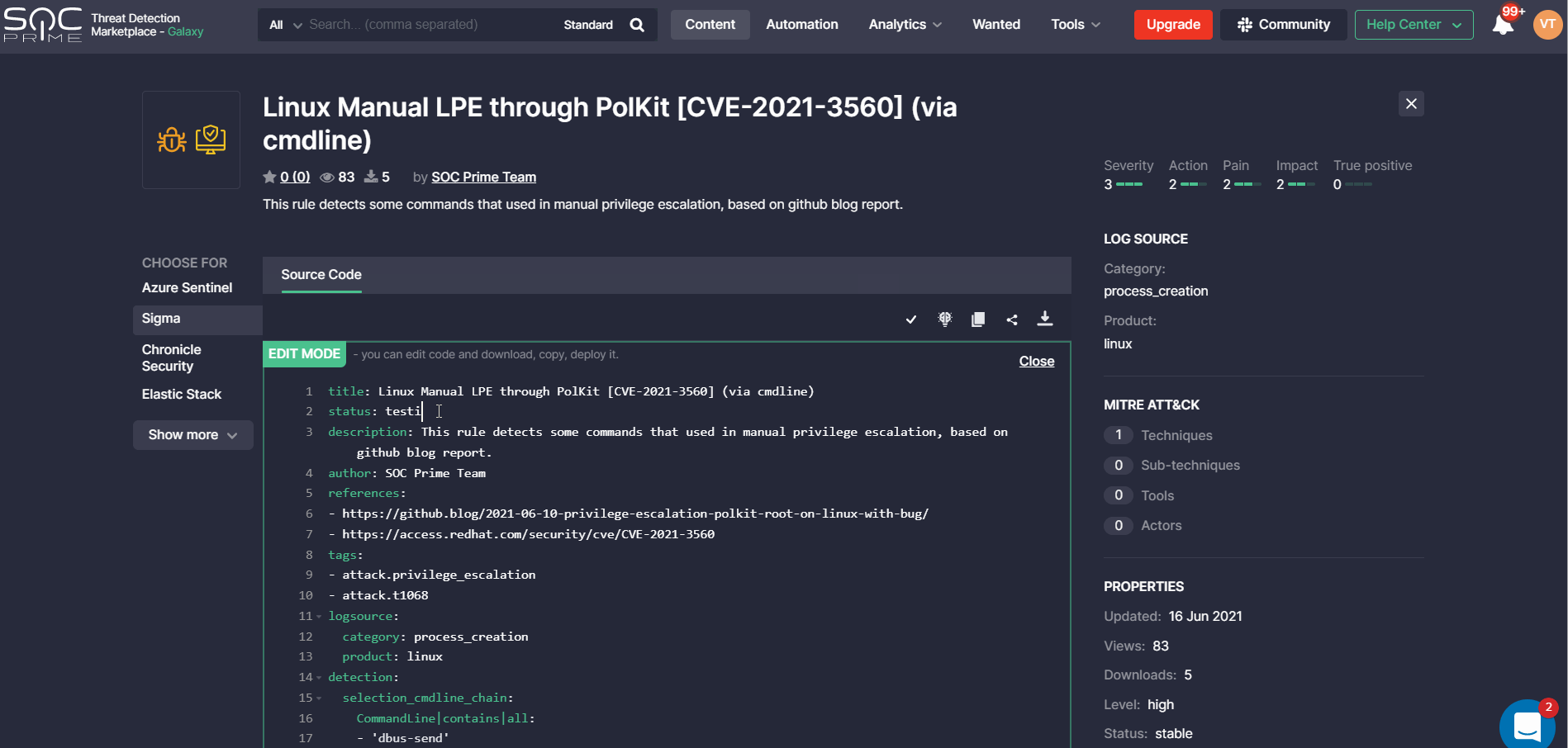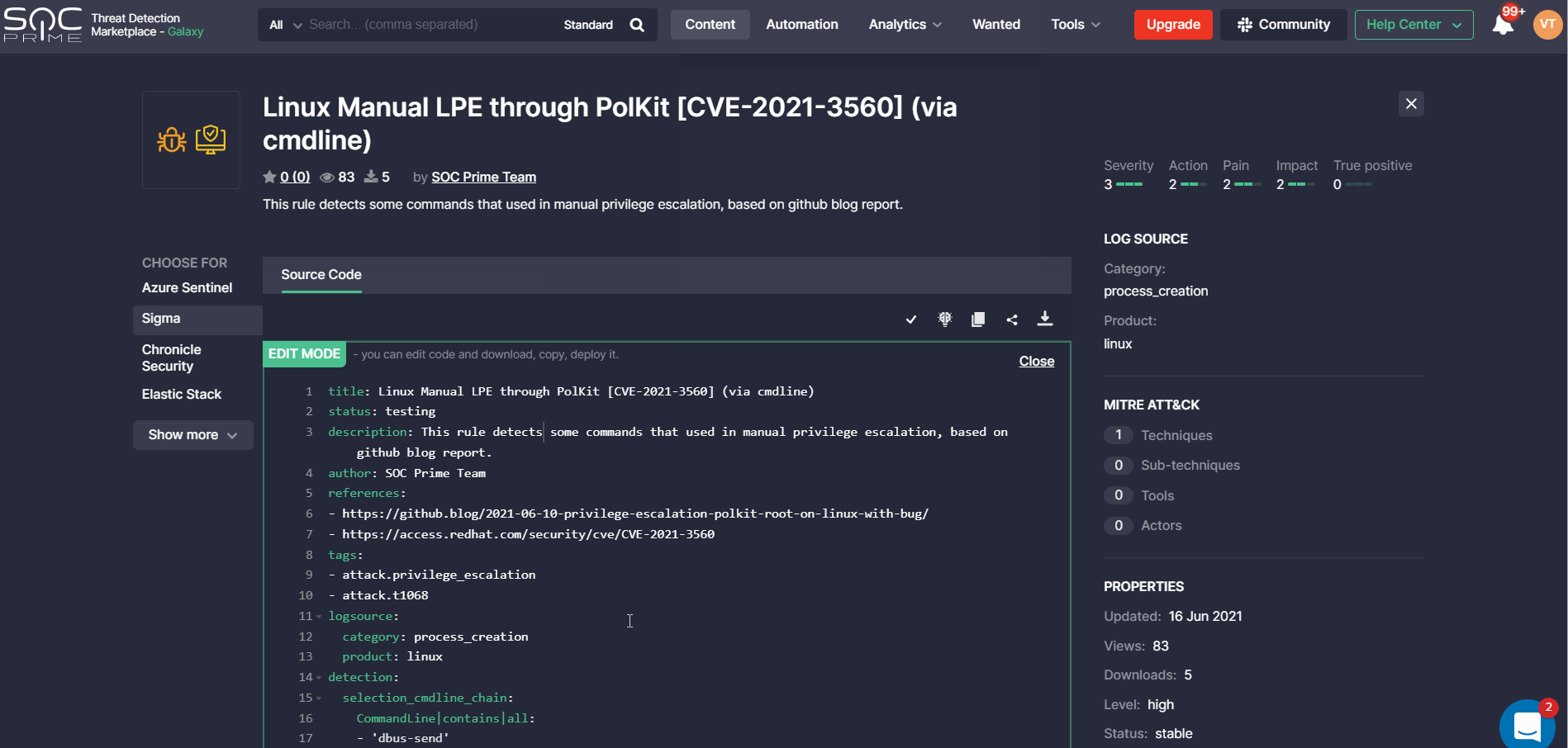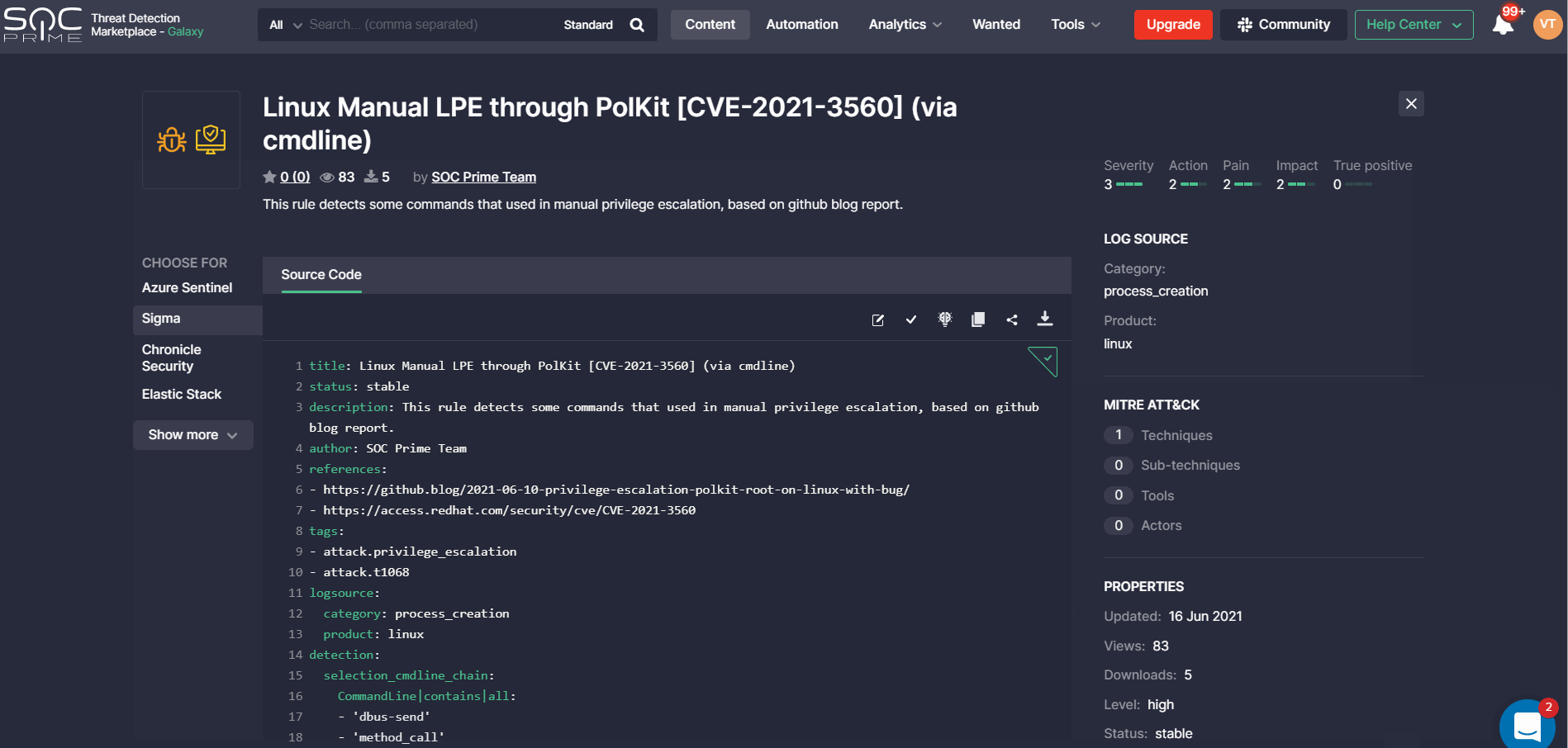
We’re regularly collecting customer feedback based on user experience with Threat Detection Marketplace that allows enhancing the platform functionality and making it more intuitive. With this release, we’ve fulfilled one of the customer feature requests that enables editing rules on the fly right from the content item page. By clicking the newly added Edit button on the action panel, security performers can switch to the rule edit mode and make any changes they want to the content item.
The updated rule can then be copied to the clipboard or deployed to the customer instance. By refreshing the page, the rule will return to the state it had before manually adding the changes.
First-Ever Bounty Program for Cyber Defenders: New Look and Feel
SOC Prime eagerly promotes collaborative cyber defense powered by its crowd-sourced Threat Bounty initiative that connects over 300+ SOC content developers and researchers worldwide. With this release, we are proud to share a newly redesigned version of the Threat Bounty program landing page that highlights in a few scrolls all the benefits and values the world’s first Bounty program for cybersecurity defenders can bring to the participants and active content contributors and how to become part of the project. The landing page is available at https://my.socprime.com/tdm-developers.
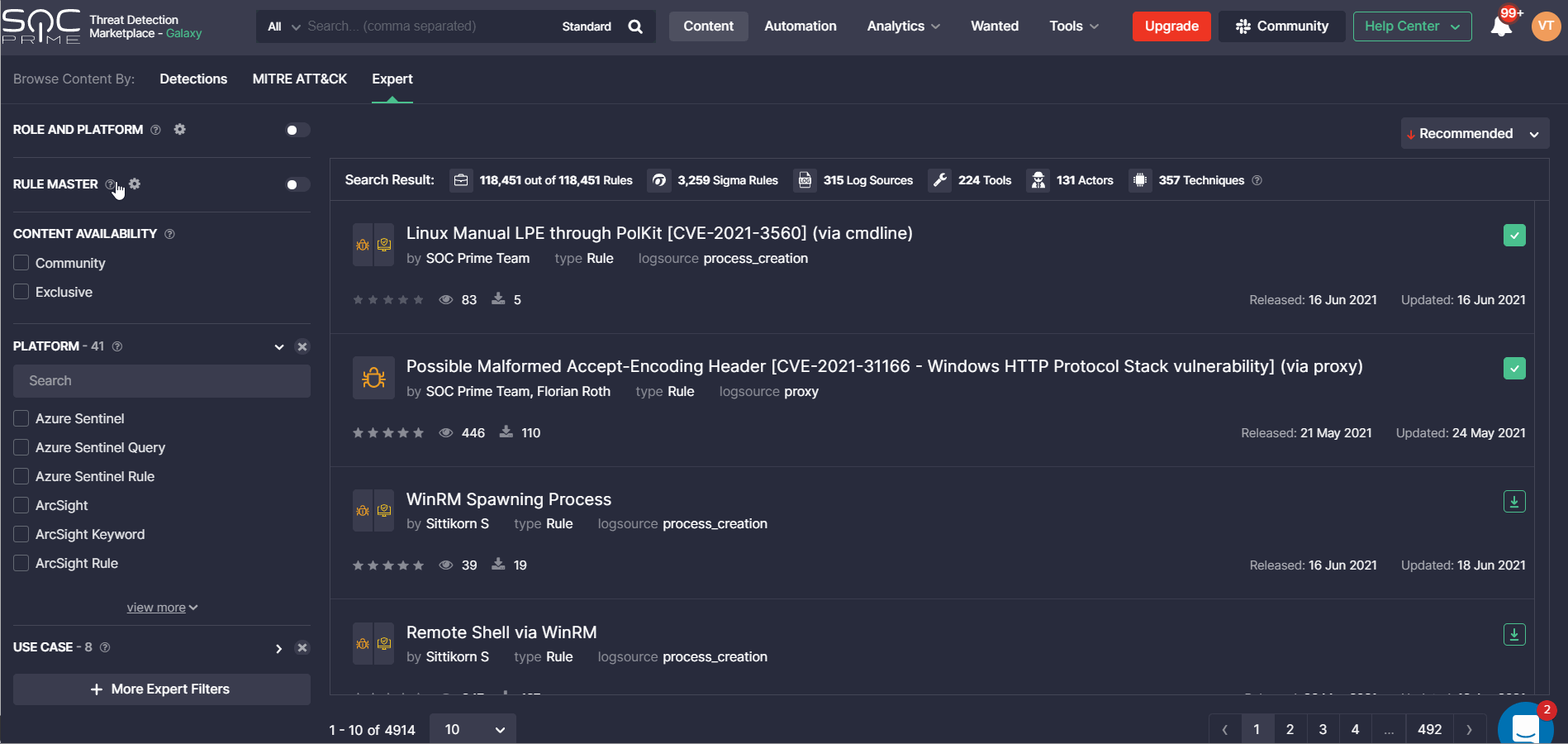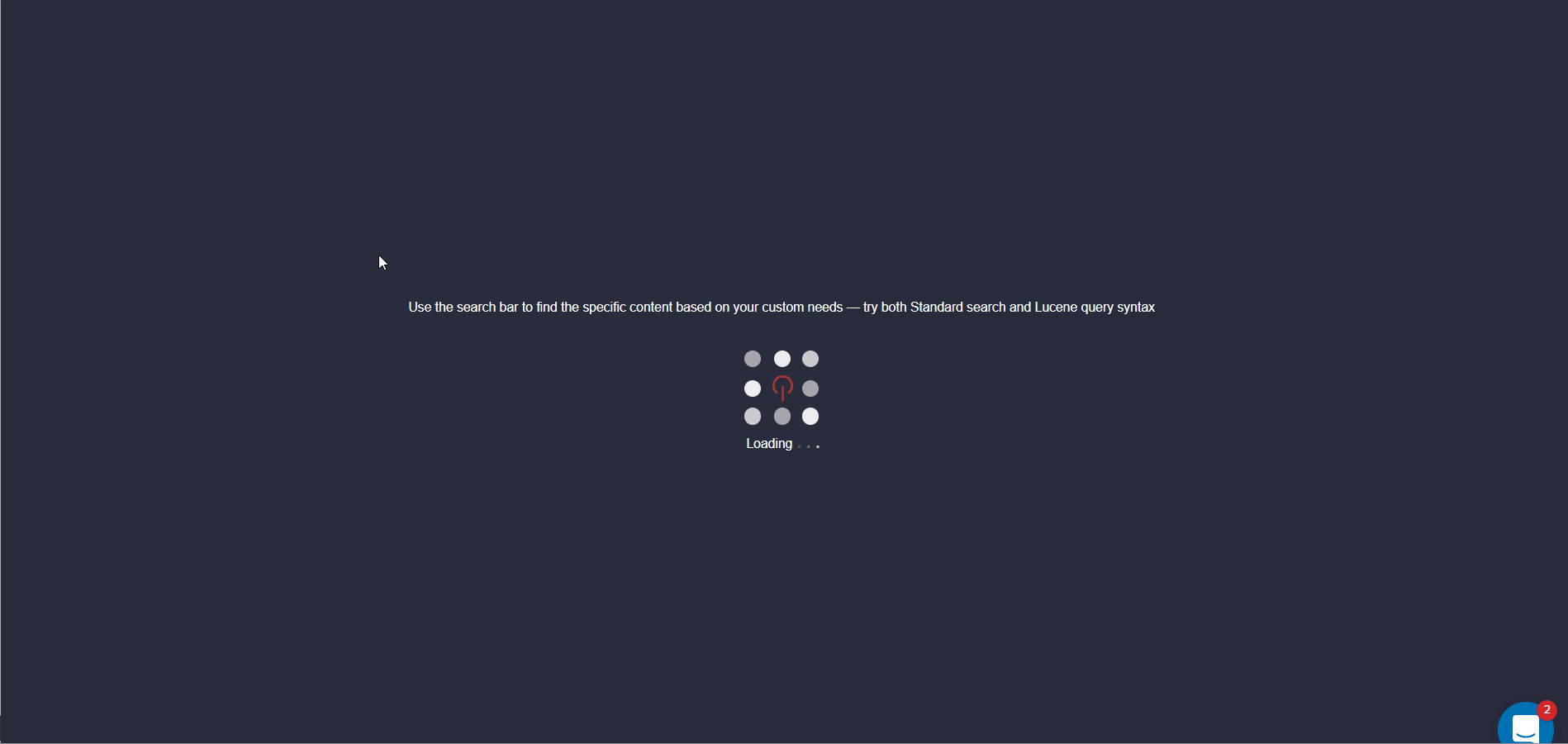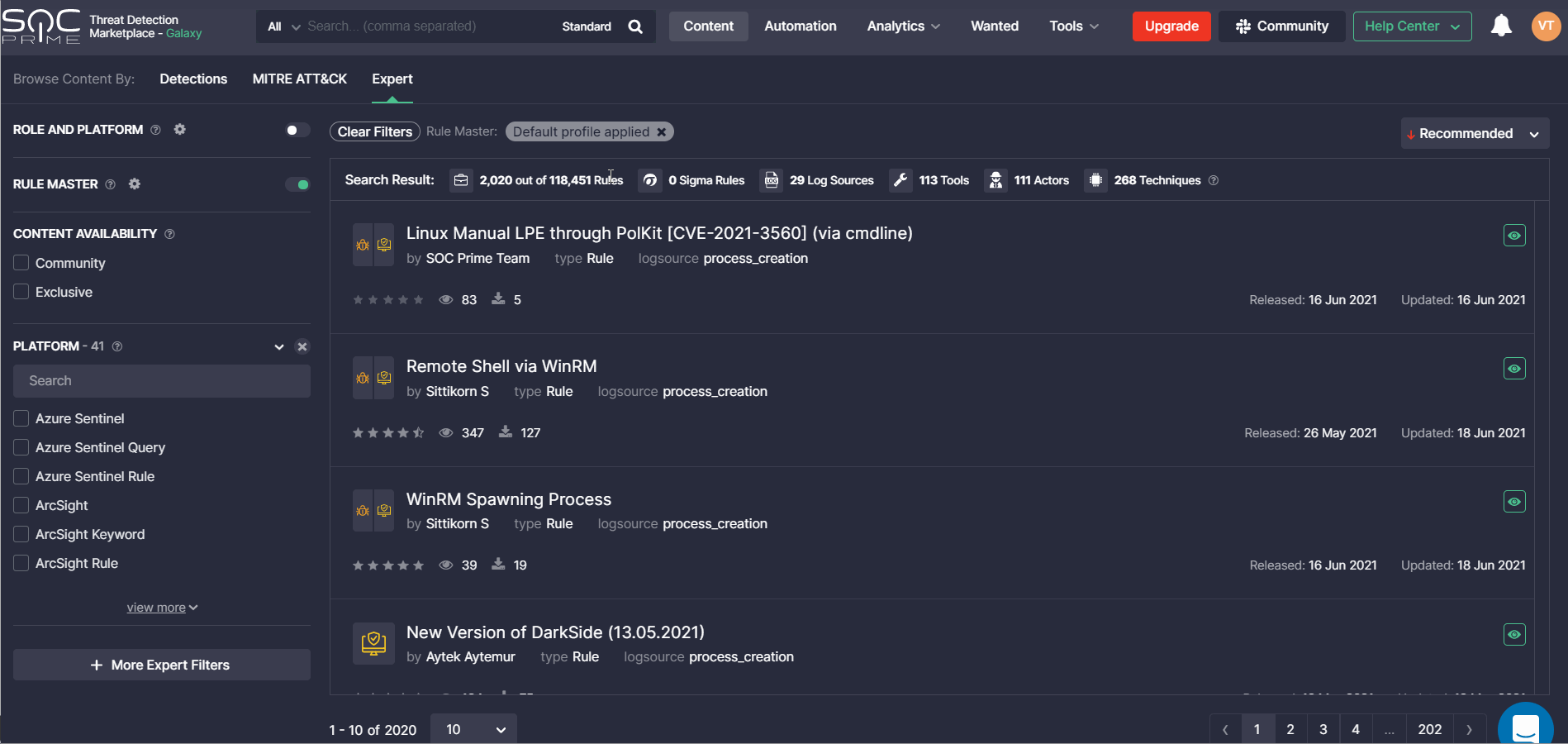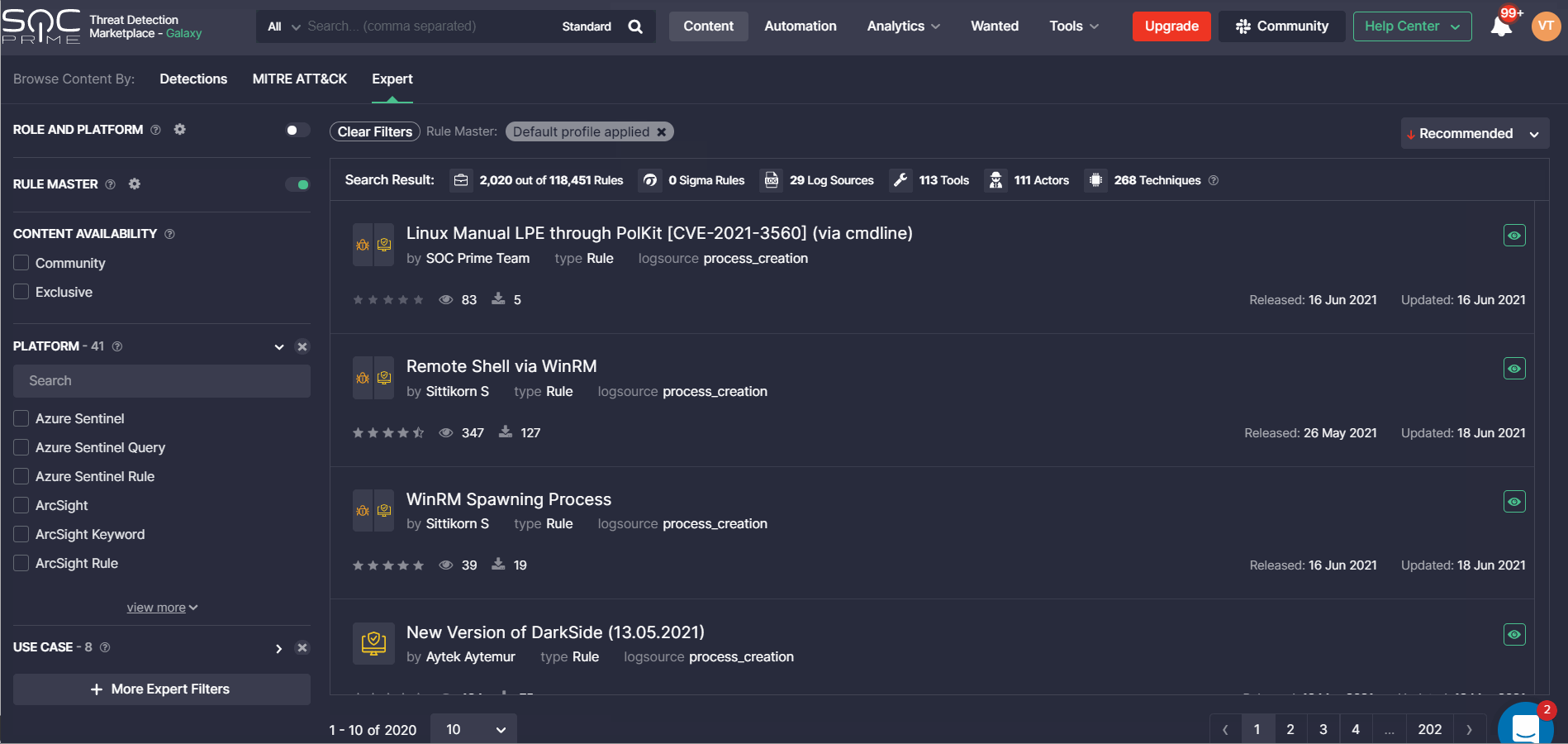
Rule Master Updates
With this release, we’ve made improvements to the Rule Master functionality for a more intuitive user experience on the Content page. To enable Threat Detection Marketplace users to configure all content profiles in one place, we’ve removed the Rule Master settings to the corresponding section in the user profile. The Content page can now neatly display only the ability to switch the Rule Master filtering ON or OFF, which determines whether the previously configured content profile will affect the search results. Once enabled, the corresponding notification will appear on the filter result panel displaying the name of the active Rule Master profile that influences how the content is filtered.
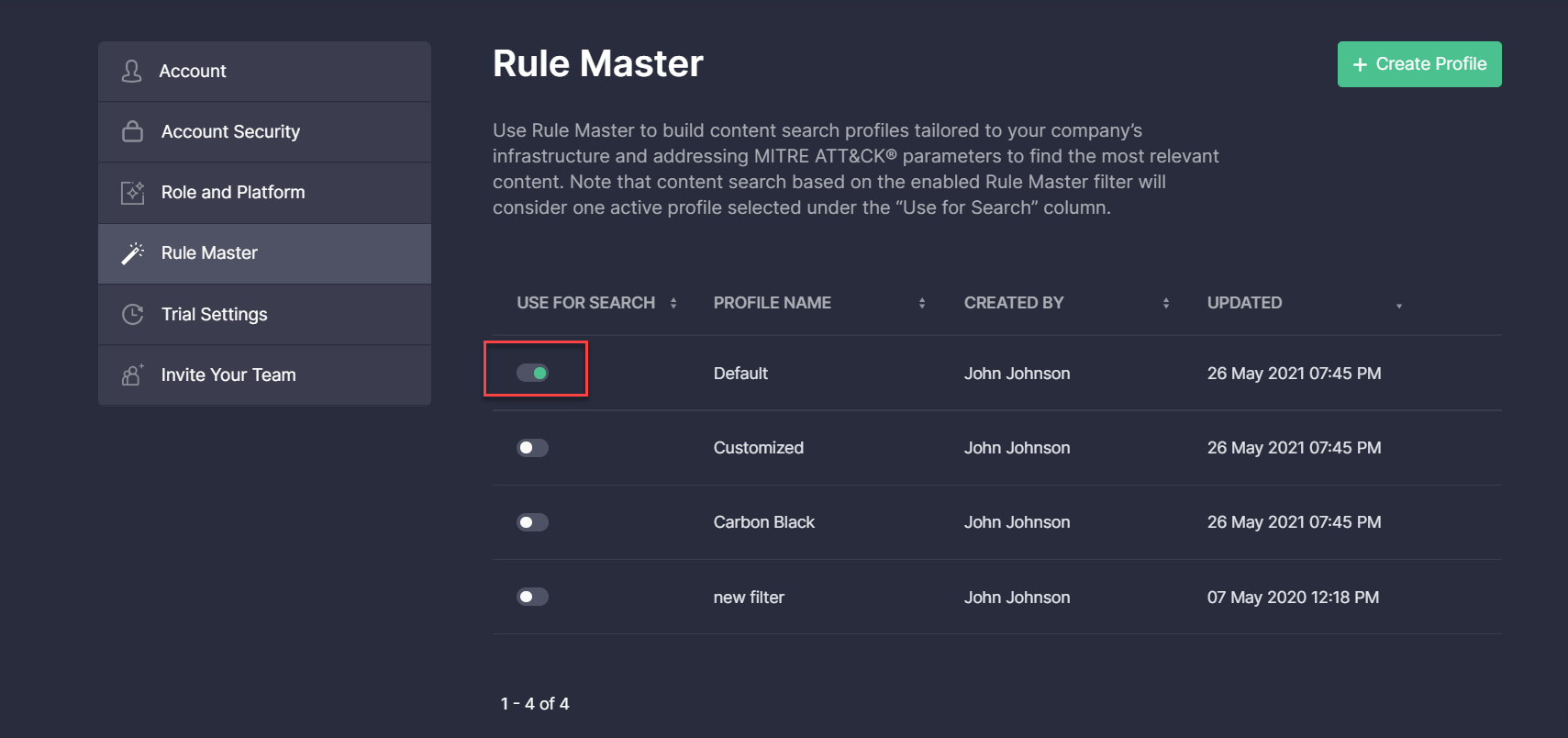
In the user profile, we’ve added the ability to consider only a single profile that will be used for filtering on the Content page once the Rule Master filtering is enabled. To activate one of the available Rule Master profiles, security performers need to switch it ON below the Use for Search column. Other profiles will be automatically disabled.
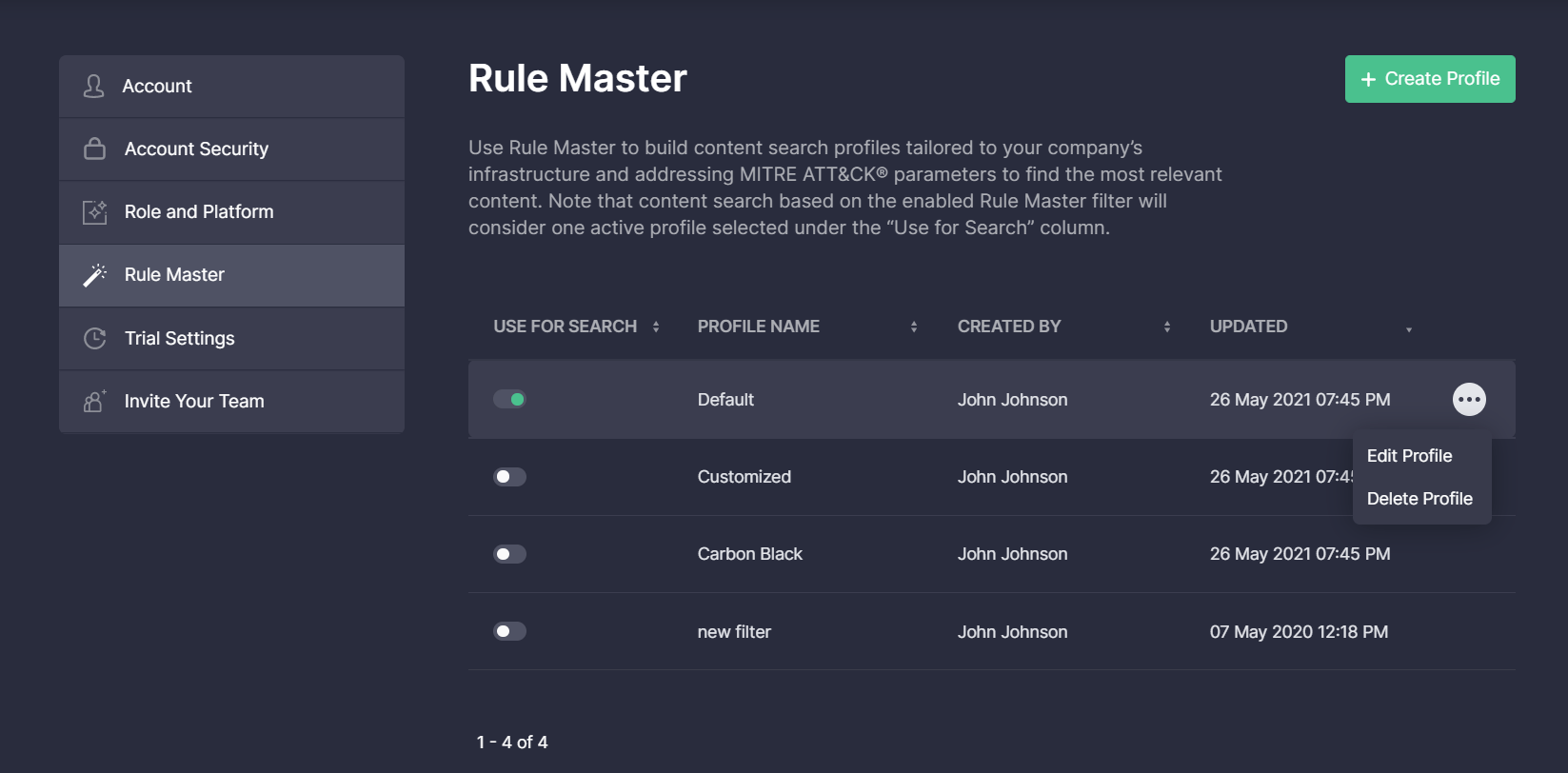
Security performers can also add a new profile by clicking the Create Profile button in the top right corner and then enable it to control the search, edit the existing profiles on the fly, or delete any items they no longer need by choosing the corresponding action from the menu.
Warden Improvements
At SOC Prime, we’re striving to constantly enhance the Warden functionality to make sure all detections written by our content contributors are unique and there are no rule duplicates.
With this latest release, we’ve updated the list of validation cases that trigger Sigma spell checker and plagiarism issues, more specifically:
- Removed checks for the availability of Sigma rule fields that are not considered required, including action, license, date, modified, and fields
- Removed deprecated validation for special symbols in the description field
- Resolved the issue with the startswith and endswith modifiers
As part of these improvements, we’ve updated localizations for error messages that are visible to the end users when a certain plagiarism issue occurs, including errors, warnings, and duplicates. Now, these error messages sound more intuitive and describe the issue in more detail.
Key Bug Fixes & Improvements
With this release, we’ve made the following key bug fixes and improvements to Threat Detection Marketplace:
- Fixed the table header for the Detections view mode so it is always on the top of the scrolled page. This allows security performers to have at hand the content name, type, author, and other content details when scrolling through the filtered list of detections.
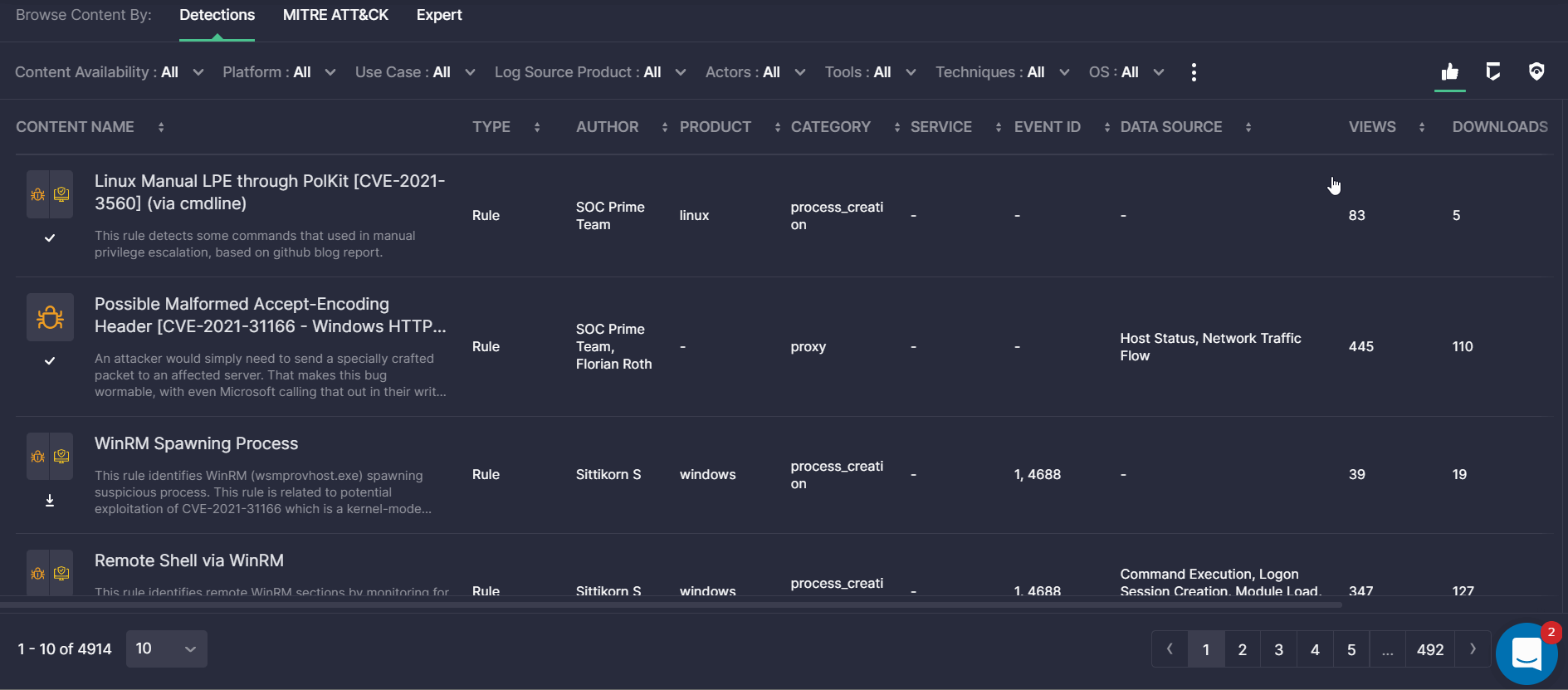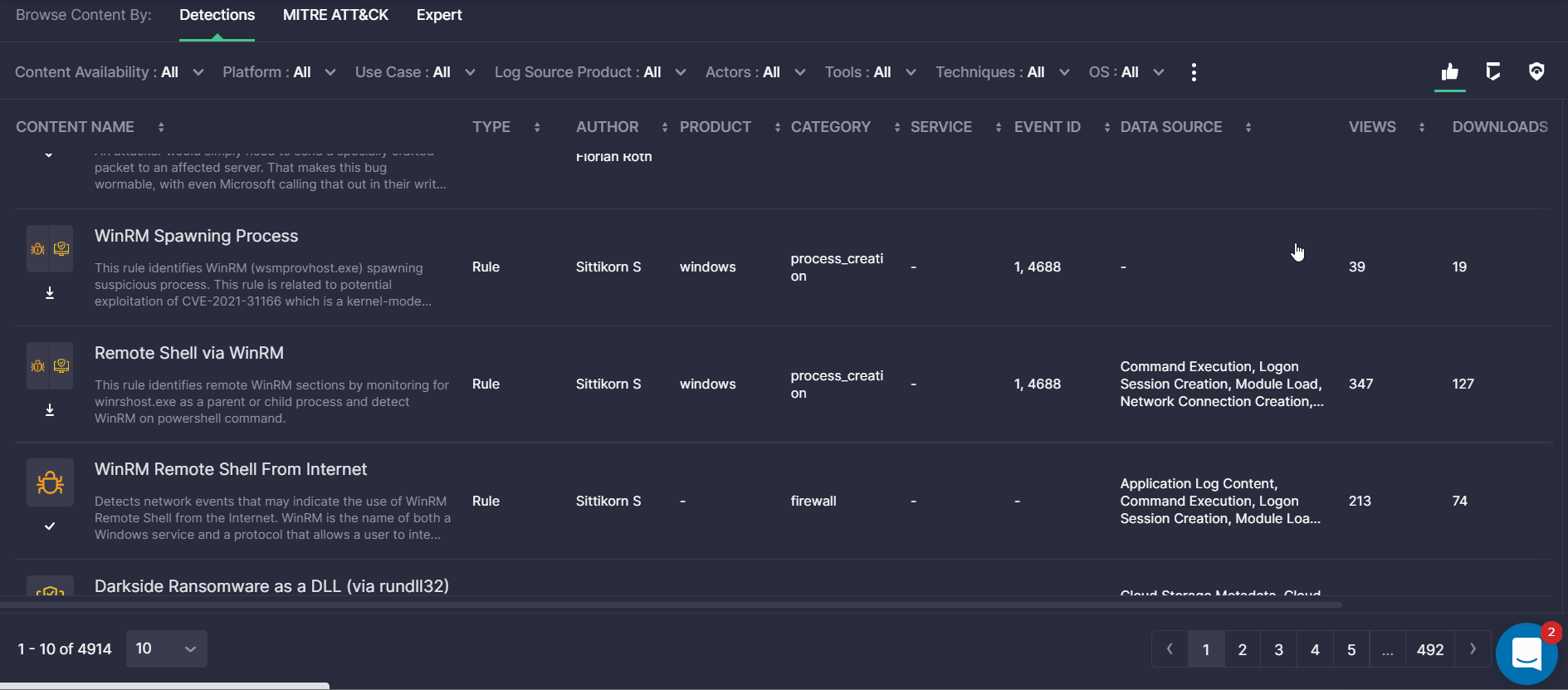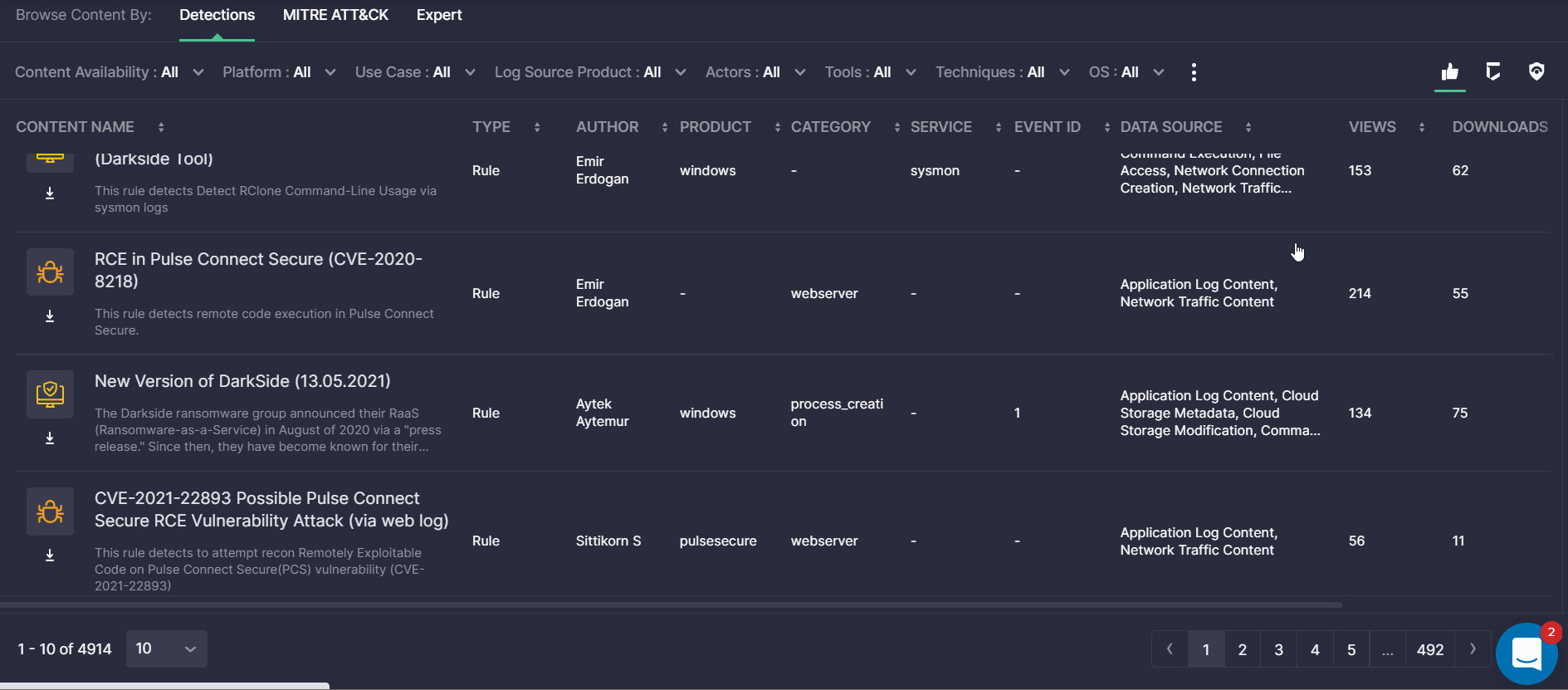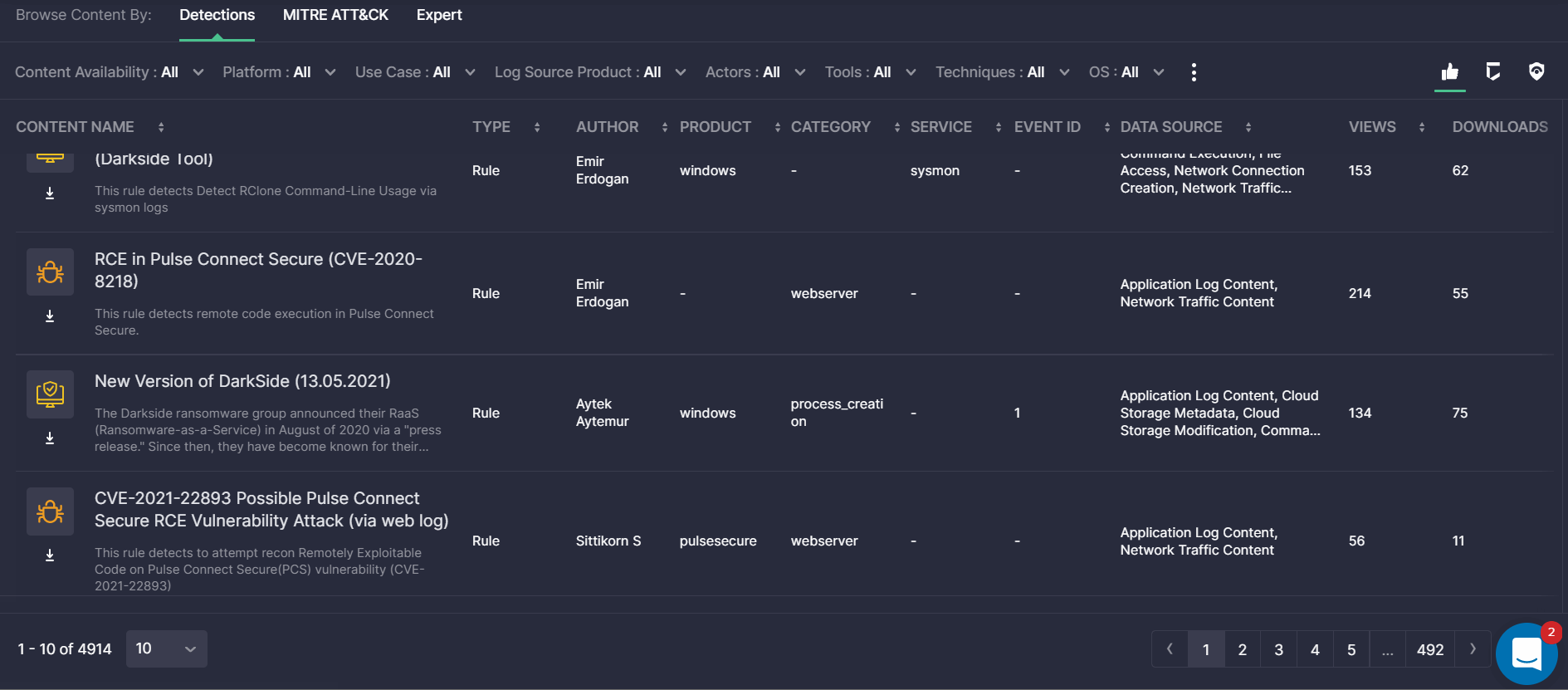
- Improved the styles of numbers displayed on the Top Authors bar chart of the Leaderboards page for a consistent platform experience.
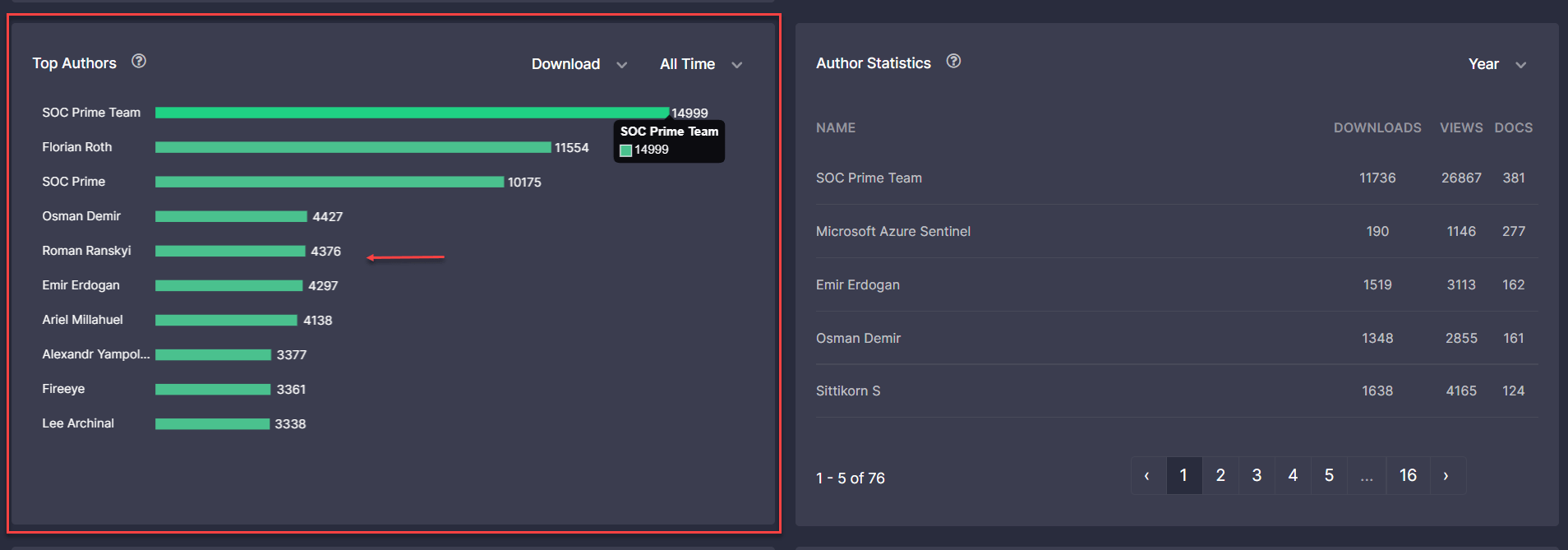
- Improved performance on the rule page by fixing the page load issue in the case of an excessive number of mapped MITRE ATT&CK Techniques and Sub-techniques.
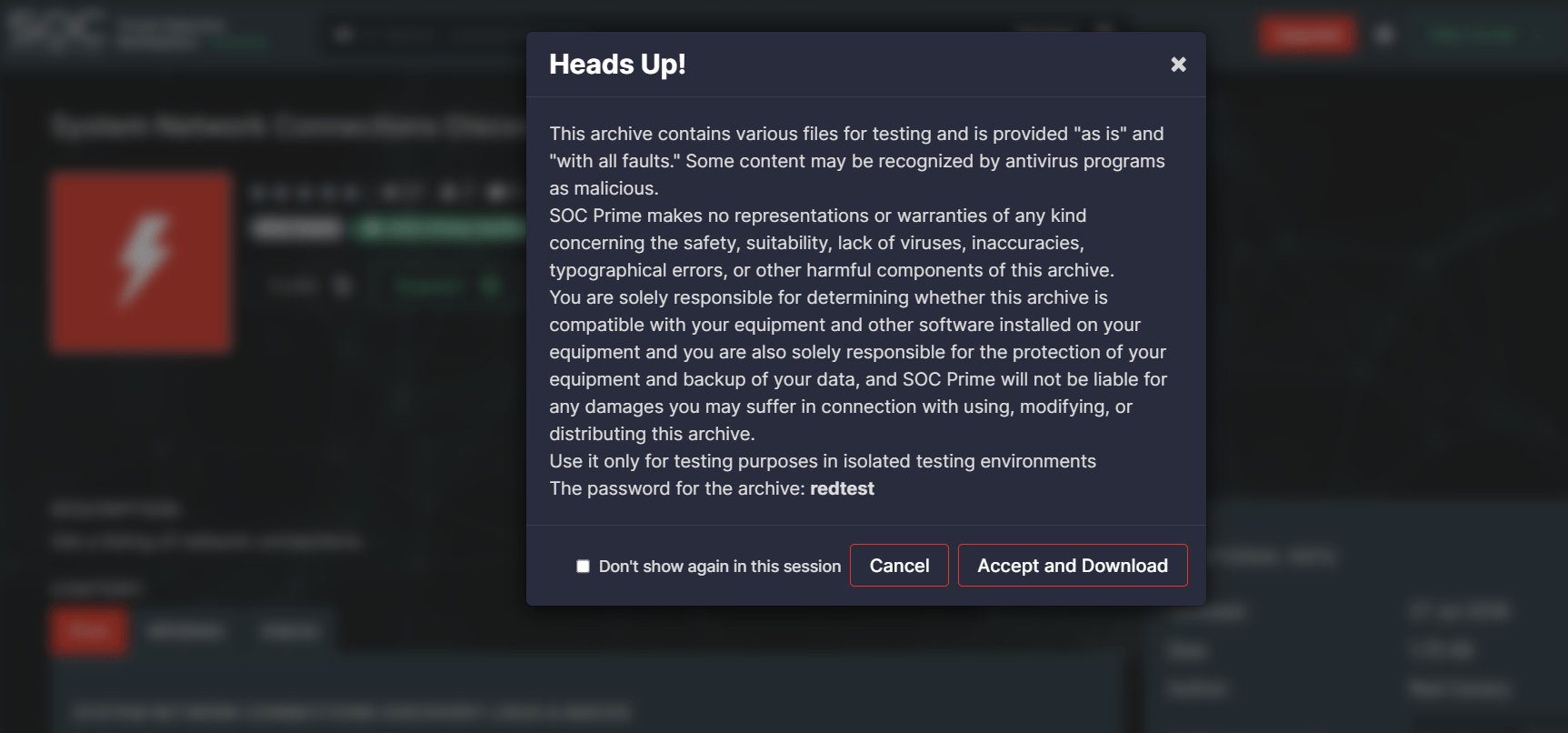
- Improved the pop-up layout with buttons when trying to download any Red Test content.
- Fixed the text overflow issue with the Rule Preset and Data Schema drop-down list options on the rule page.

- Fixed the position of the sorting arrow icons on the Techniques, Tools, and Actors pop-ups when drilling down to the content details from the Dashboard page. Now, these icons are properly located next to the column names for a more intuitive user experience.
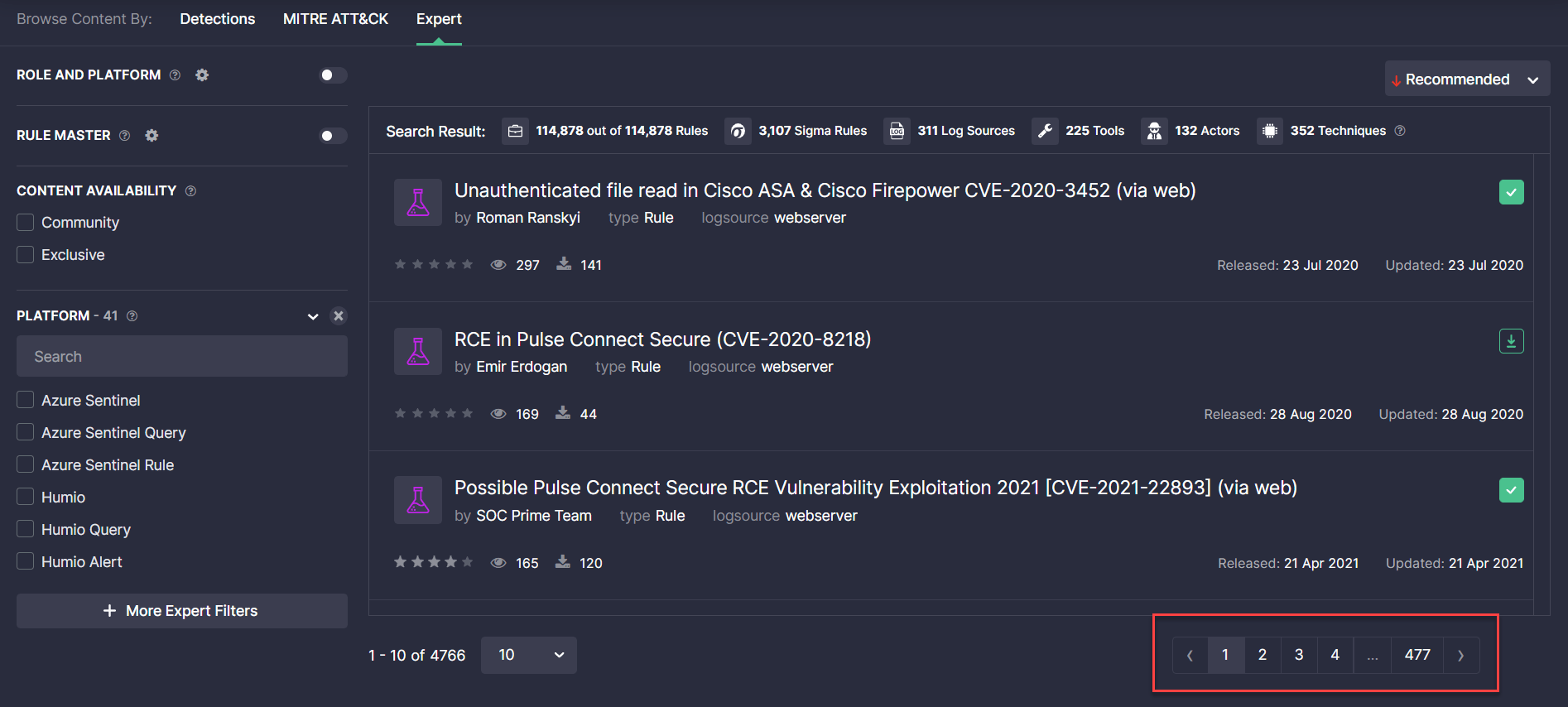
- Fixed the pagination issue on the Content page when buttons were unclickable and prevented seamless navigation.
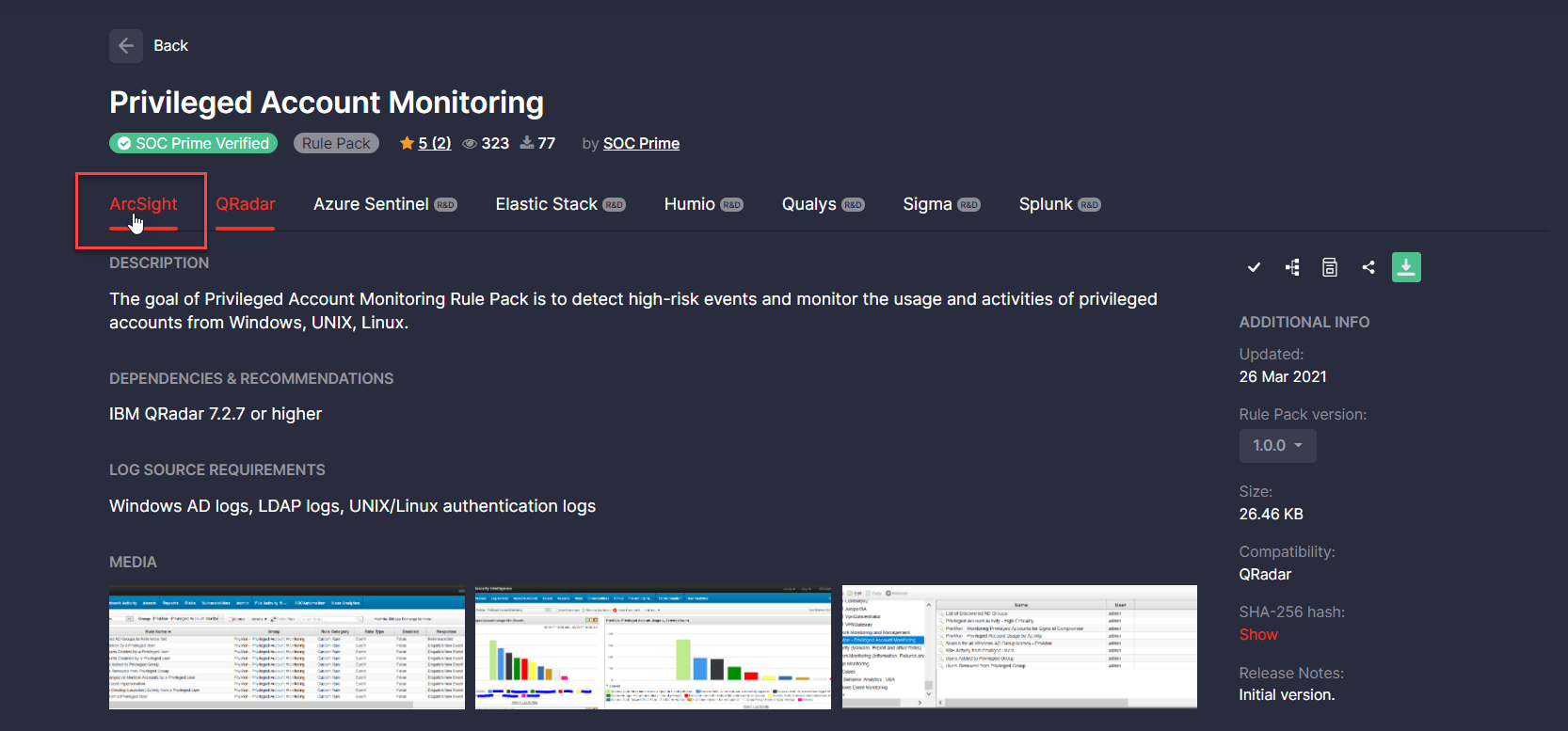
- Fixed the Rule Pack issue when hovering over the menu with a list of available platforms. Before this update, the entire list of platforms was selected instead of a single tab displayed on hover.
- Fixed the issue that prevented users from deploying free content items, including Rules, Rule Packs, Configs, and Playbooks available for the Community subscription. Before the update, Community customers couldn’t see the button for content deployment when drilling down to the content item page.
Get a free subscription to Threat Detection Marketplace, an industry-leading Detection as Code platform that provides detection, enrichment, integration, and automation algorithms to support security performers while translating big data, logs, and cloud telemetry into cybersecurity signals. Our SOC content library contains over 100K detection and response rules, parsers, search queries, and other relevant SOC content so you can withstand the growing number of cyber-attacks. Want to craft your own detection content? Join our Threat Bounty Program and get rewarded for your input!