Threat Detection Marketplace 4.11.0 Is Released

On June 2, 2021, we released Threat Detection Marketplace version 4.11.0 to add new hot features and master the existing functionality of our Detection as Code platform. With this latest update, we introduce the support for MITRE ATT&CK® framework v9, initiate a new multi-language ATT&CK project, provide major content quality enhancements, polish the Detection Engineer’s role-based platform experience, and fix a list of minor bugs to resolve issues reported by our customers.
MITRE ATT&CK V9 Support
This Threat Detection Marketplace update introduces the support for the latest MITRE ATT&CK® framework v9. One of the key enhancements is adding the support for ATT&CK Sub-techniques that were not available prior to this platform release. To explore the latest innovation, you can read our dedicated blog article describing all corresponding upgrades.
MITRE ATT&CK® Map: Multi-Language Initiative
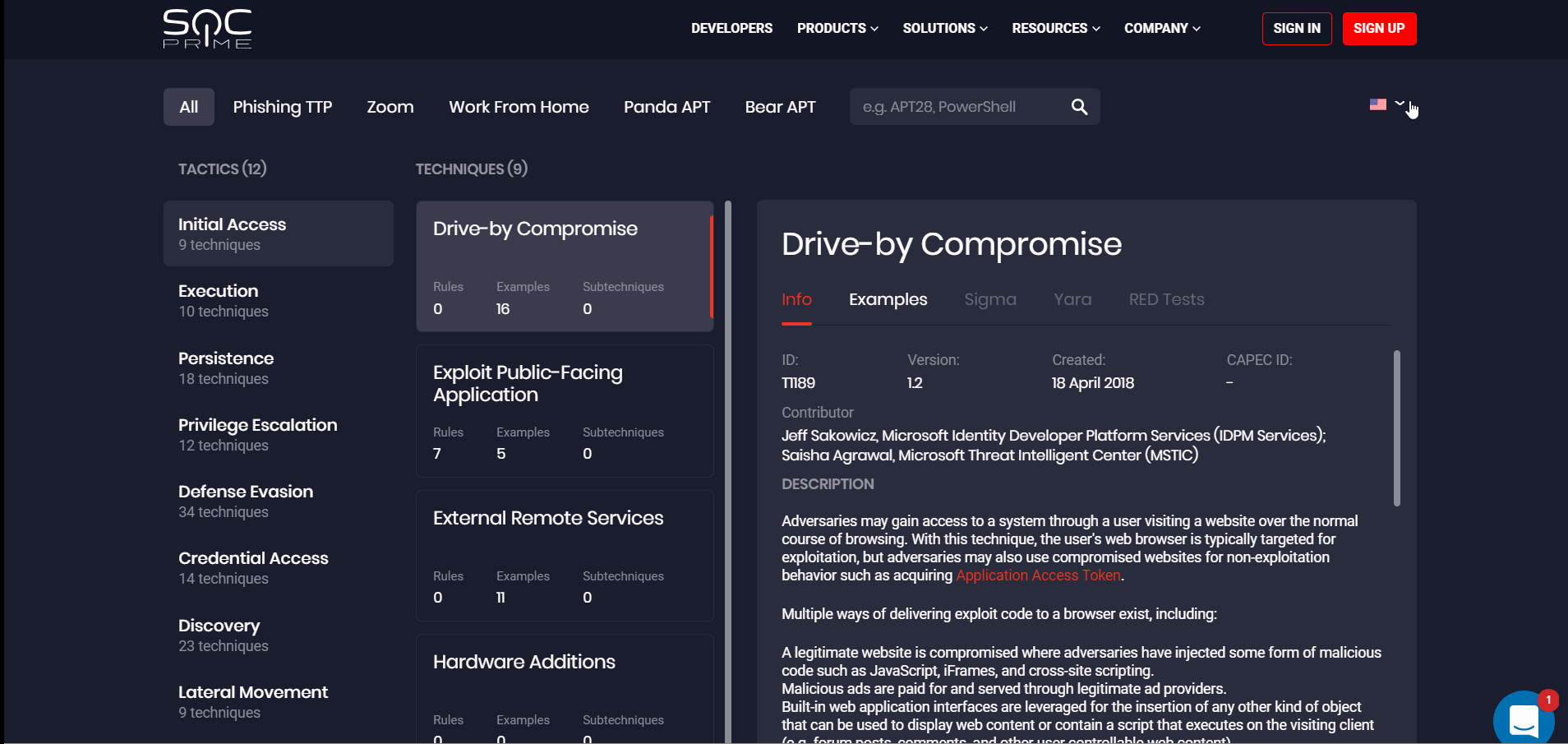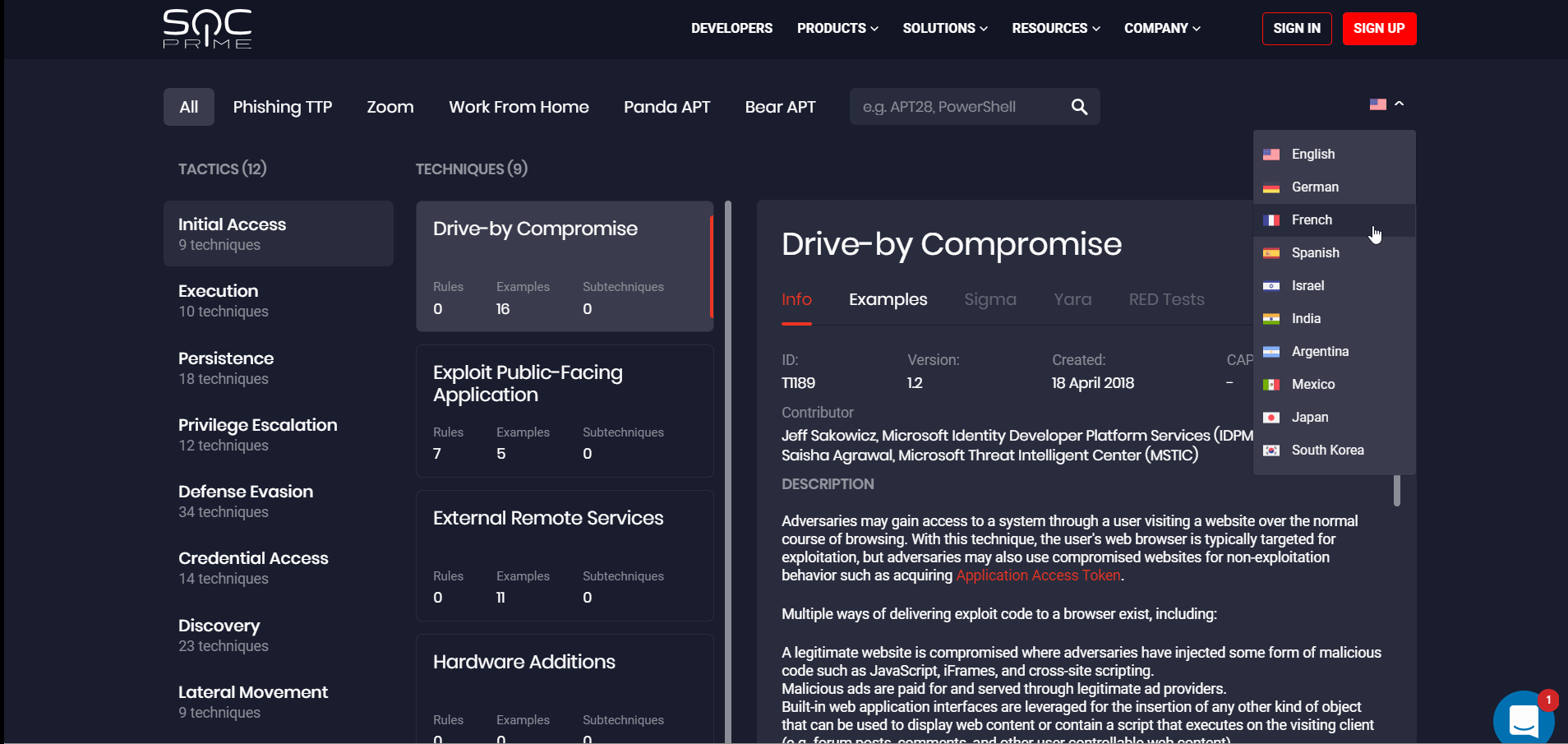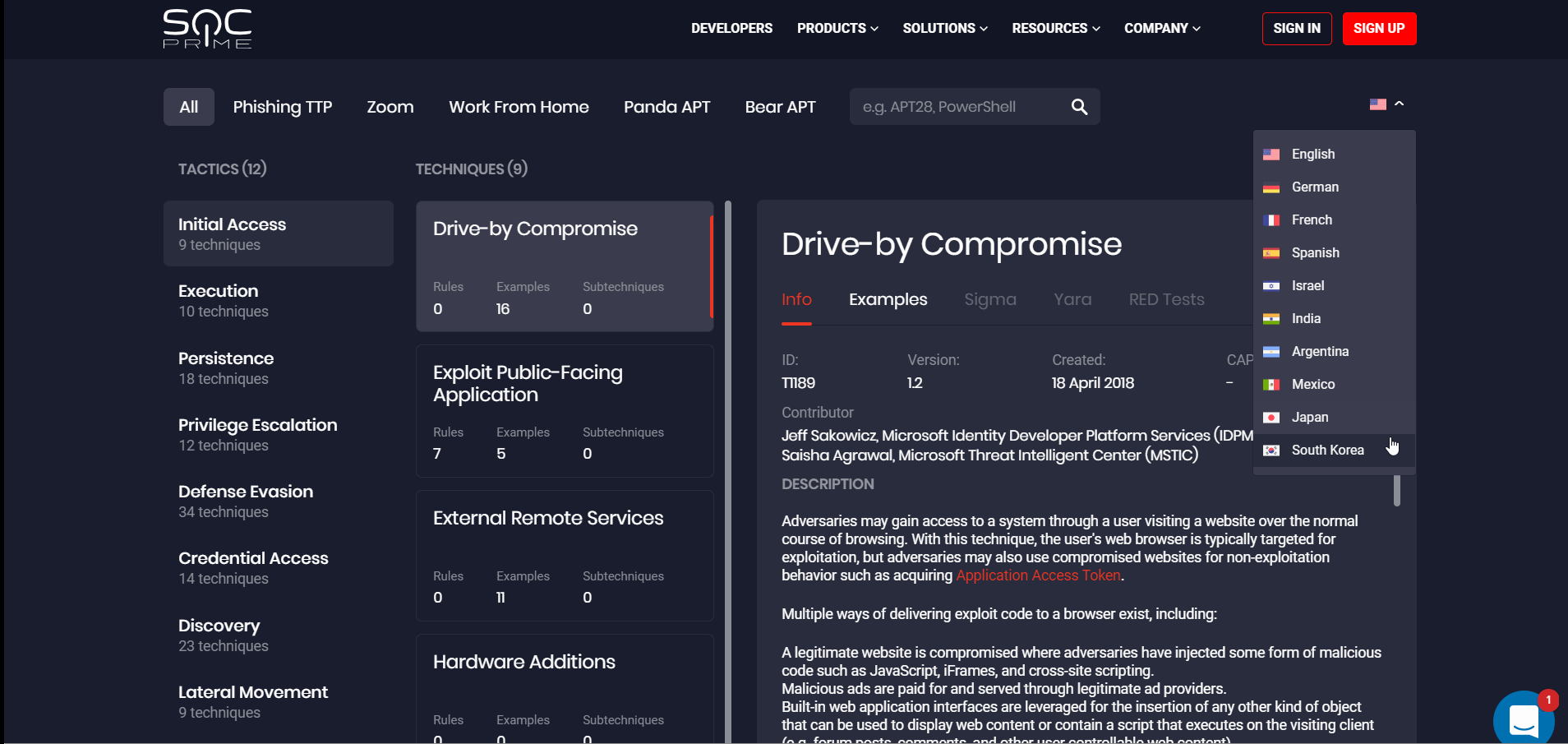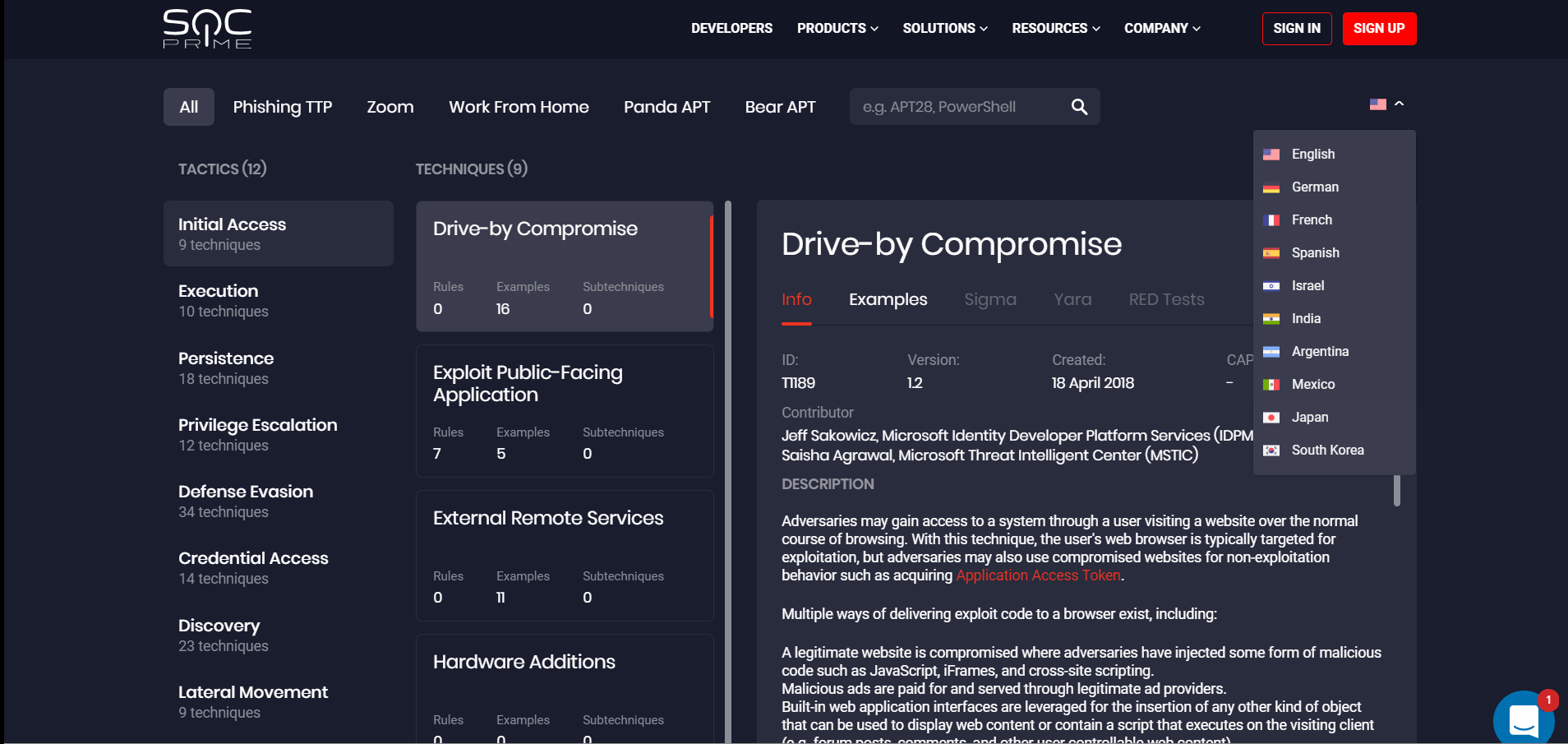
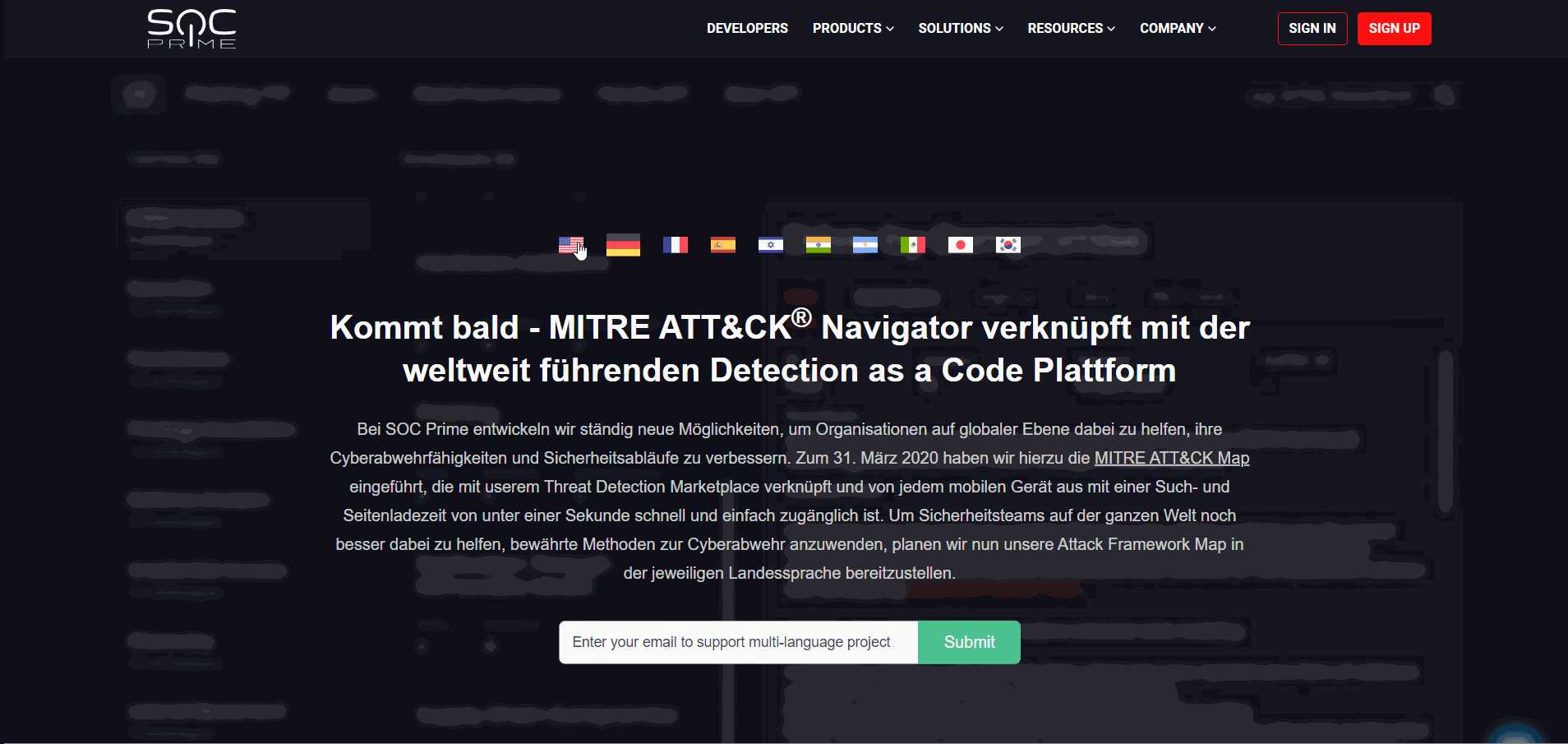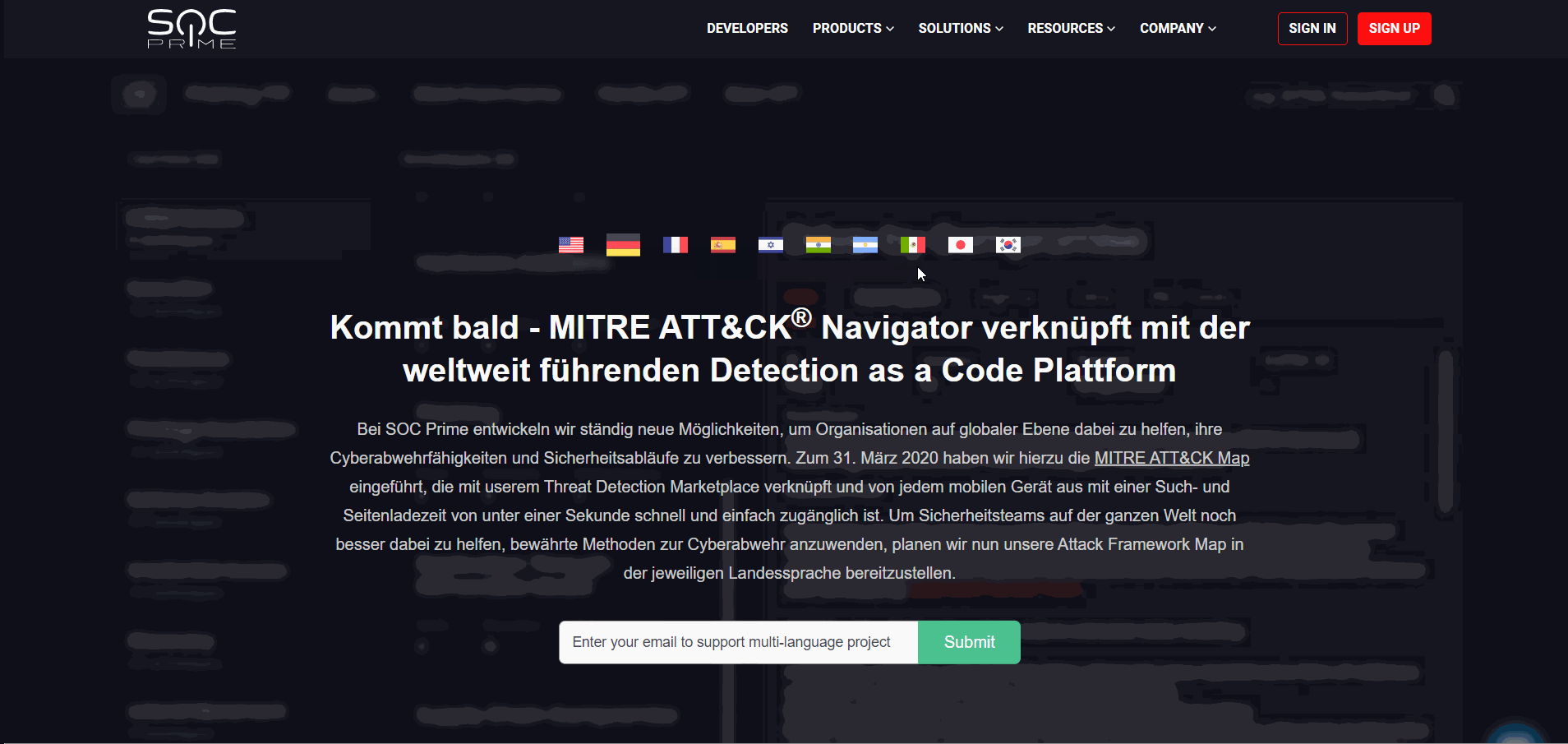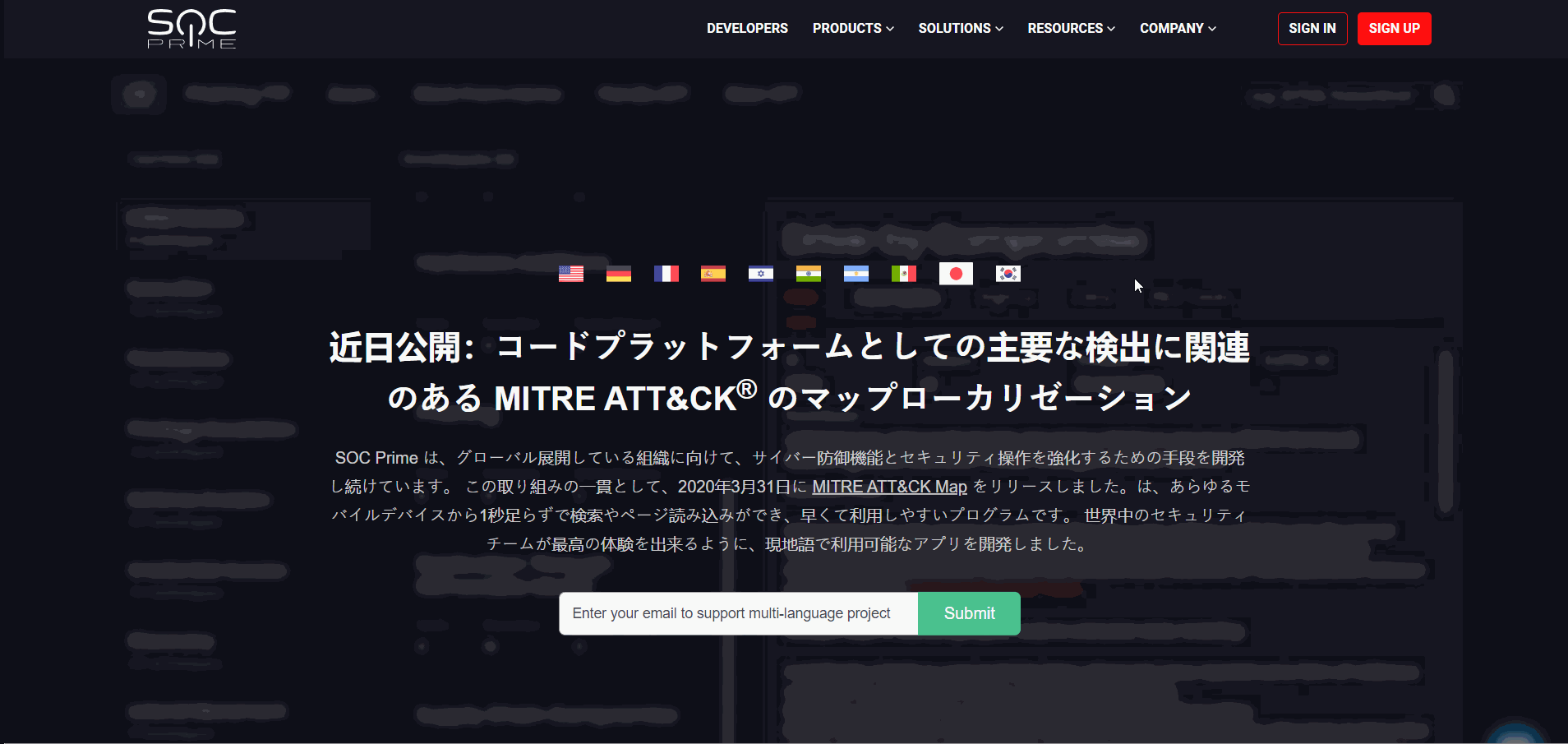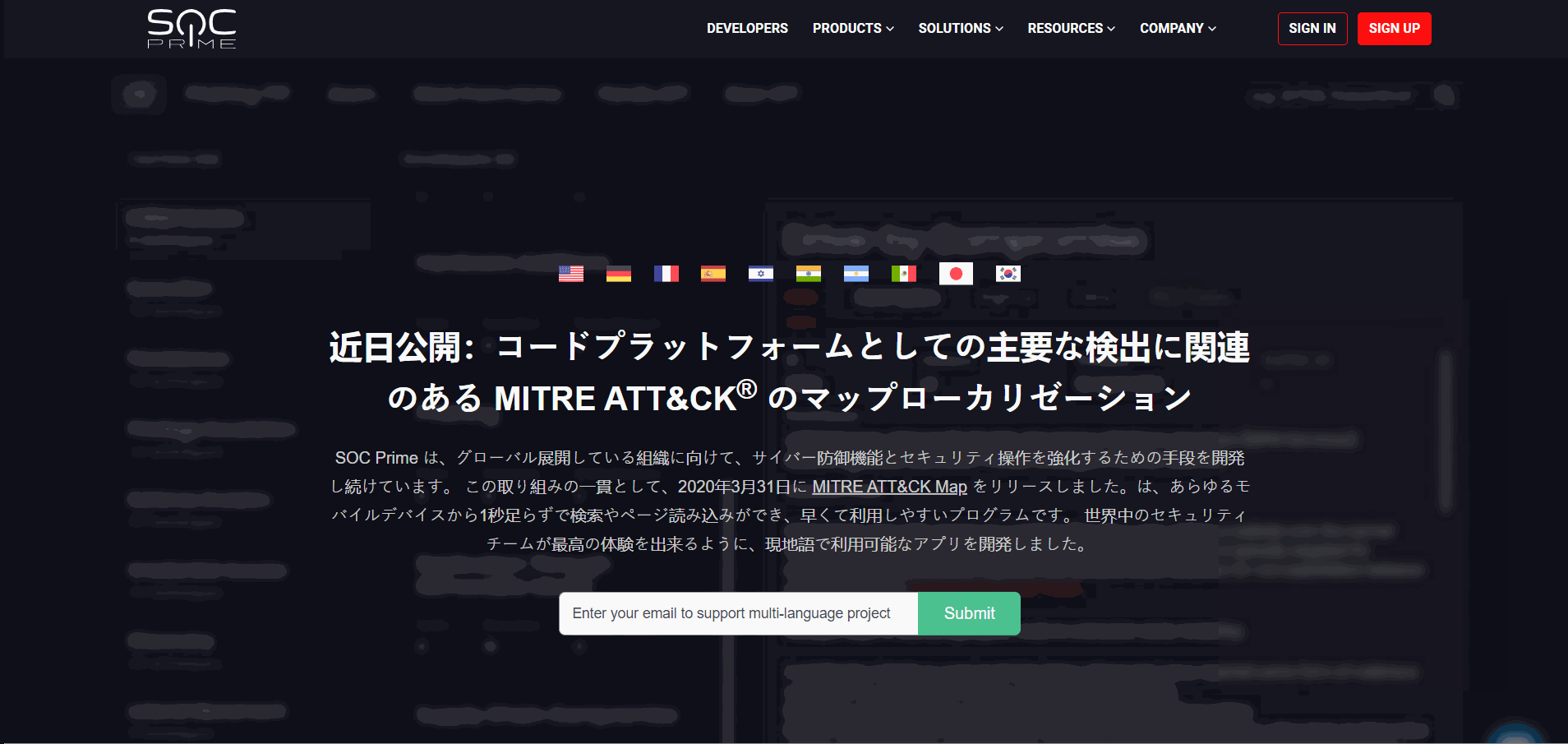
To help Security Teams worldwide adopt the best-proven practices, we have come up with an idea of the MITRE ATT&CK Map available in their local language. To make this initiative real, with this release, we have launched the new multi-language ATT&CK project. SOC Prime’s customers can now click the drop-down list with the list of available languages identified by the flag icon available on the https://attack.socprime.com/#!/ webpage.
By selecting one of the languages, security performers will be redirected to the corresponding webpage version. We are looking forward to receiving support from our cybersecurity community for improving the translation quality. SOC Prime welcomes security enthusiasts across our global community to come up with their translation suggestions by leaving their contact email, so we can get in touch and collaborate on the project’s multi-language support.
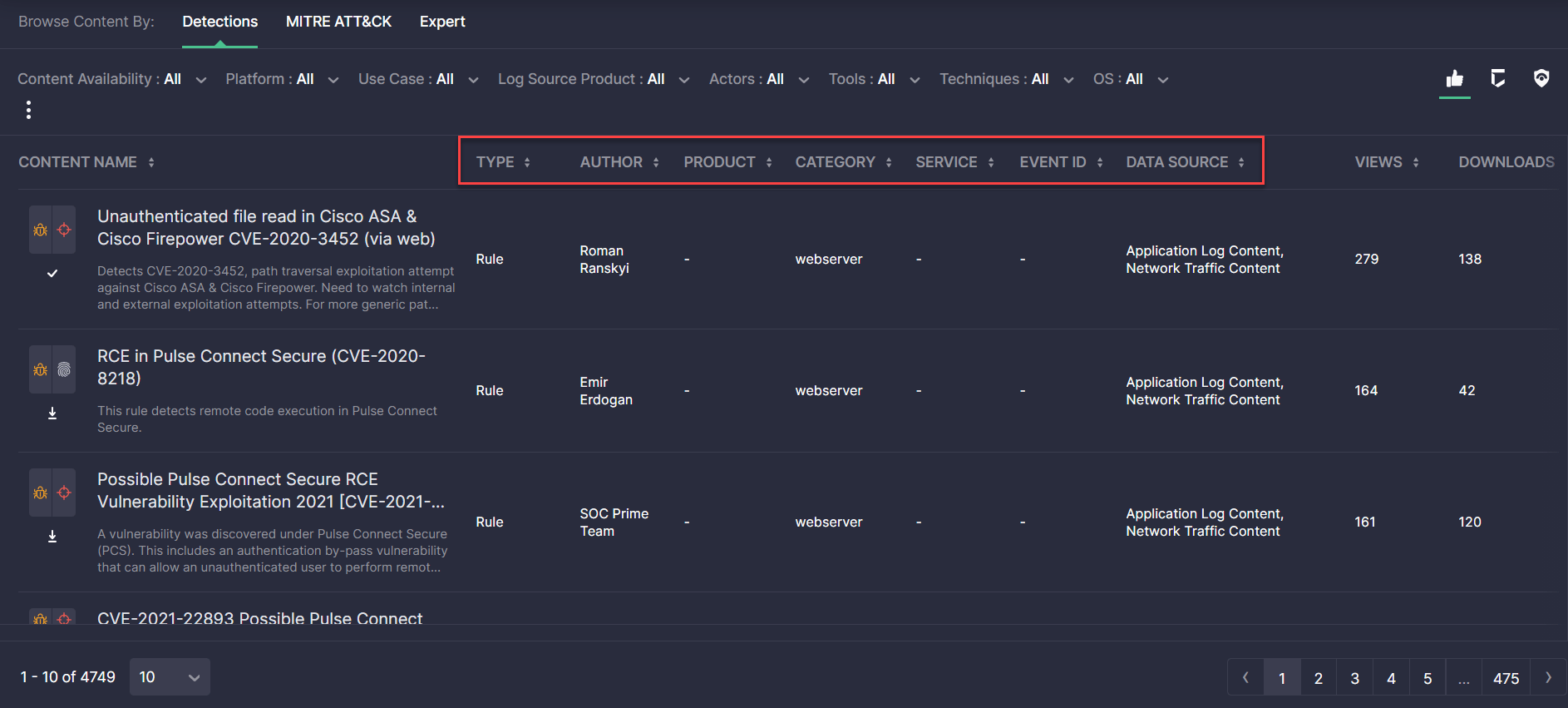
Detections View: Detection Engineer’s Role-Based Experience
SOC Prime is aimed at providing security practitioners with role-based experience using Threat Detection Marketplace addressing the most relevant use cases and procedures their professional role involves. With this release, we’ve implemented the content search functionality tailored to the Detection Engineer’s security needs.
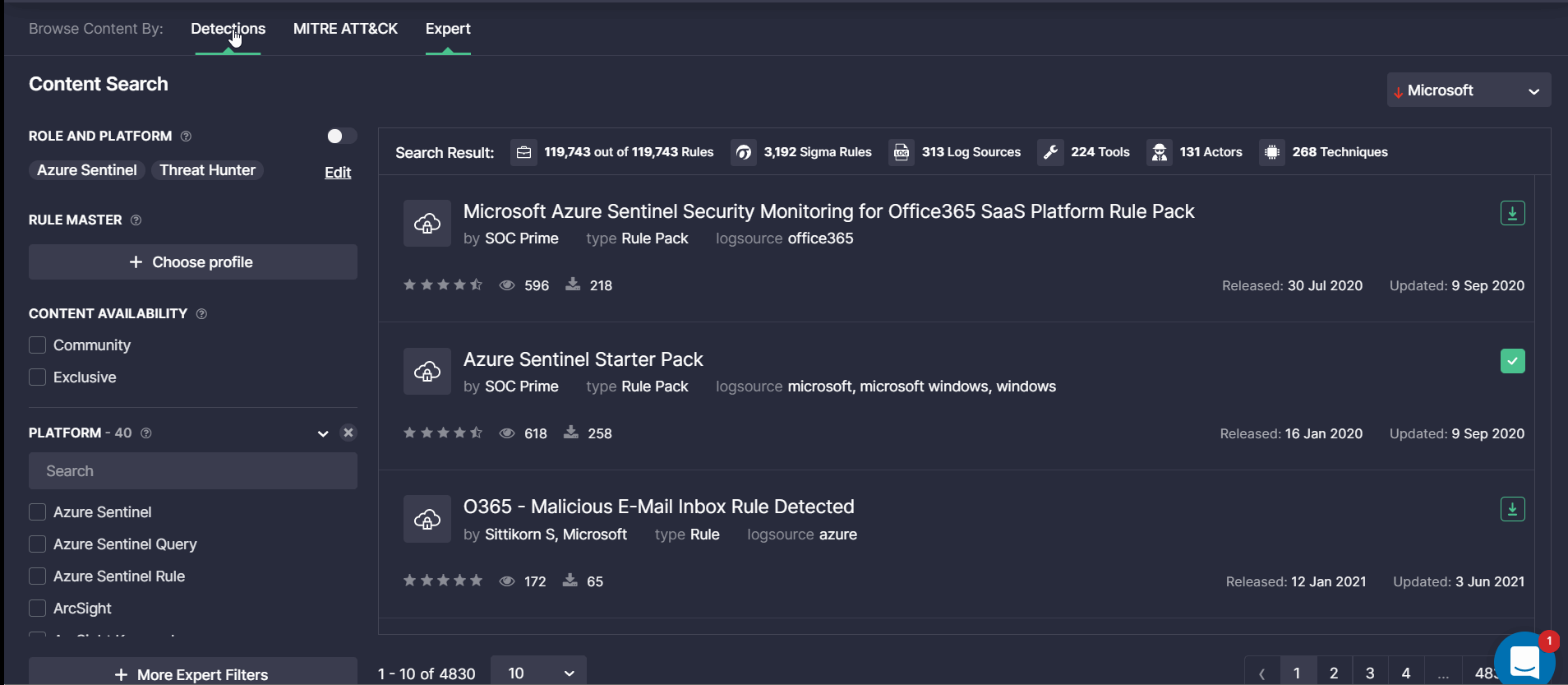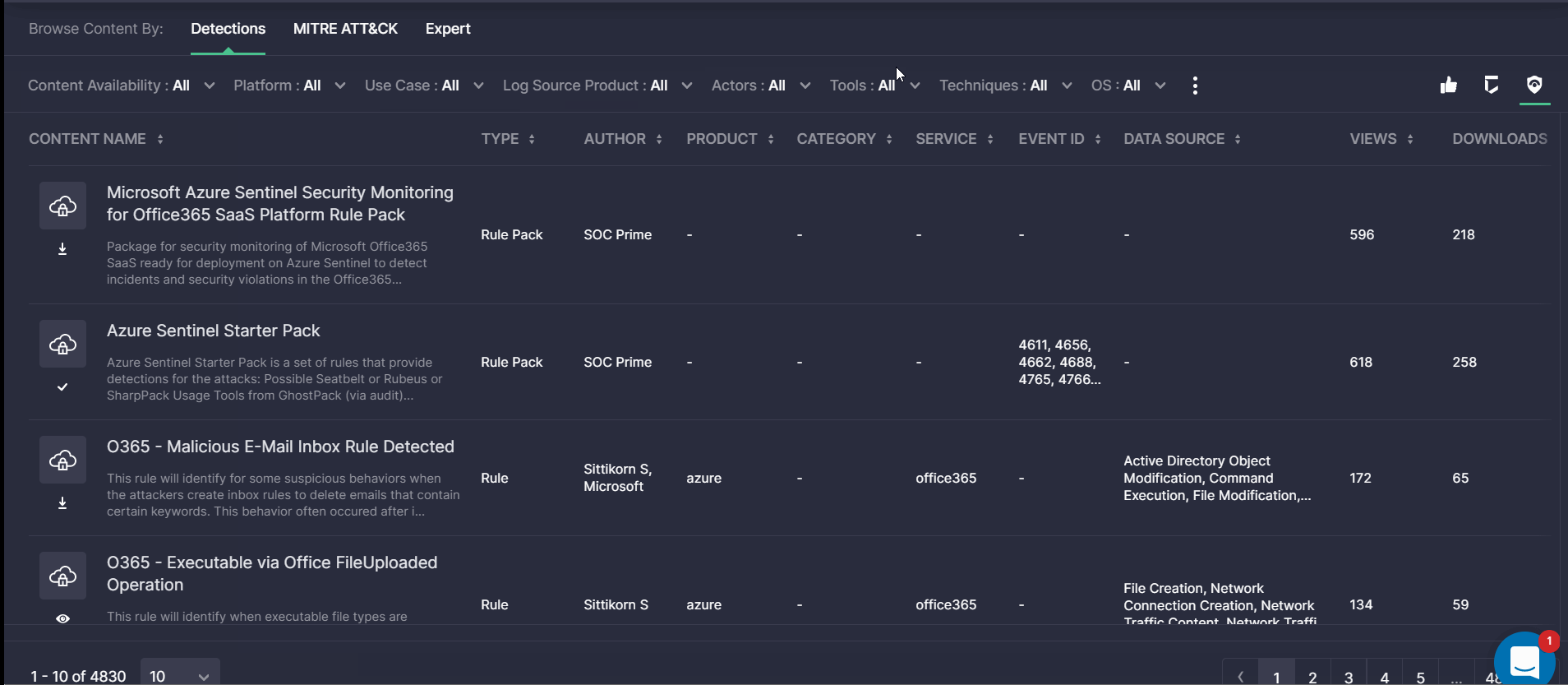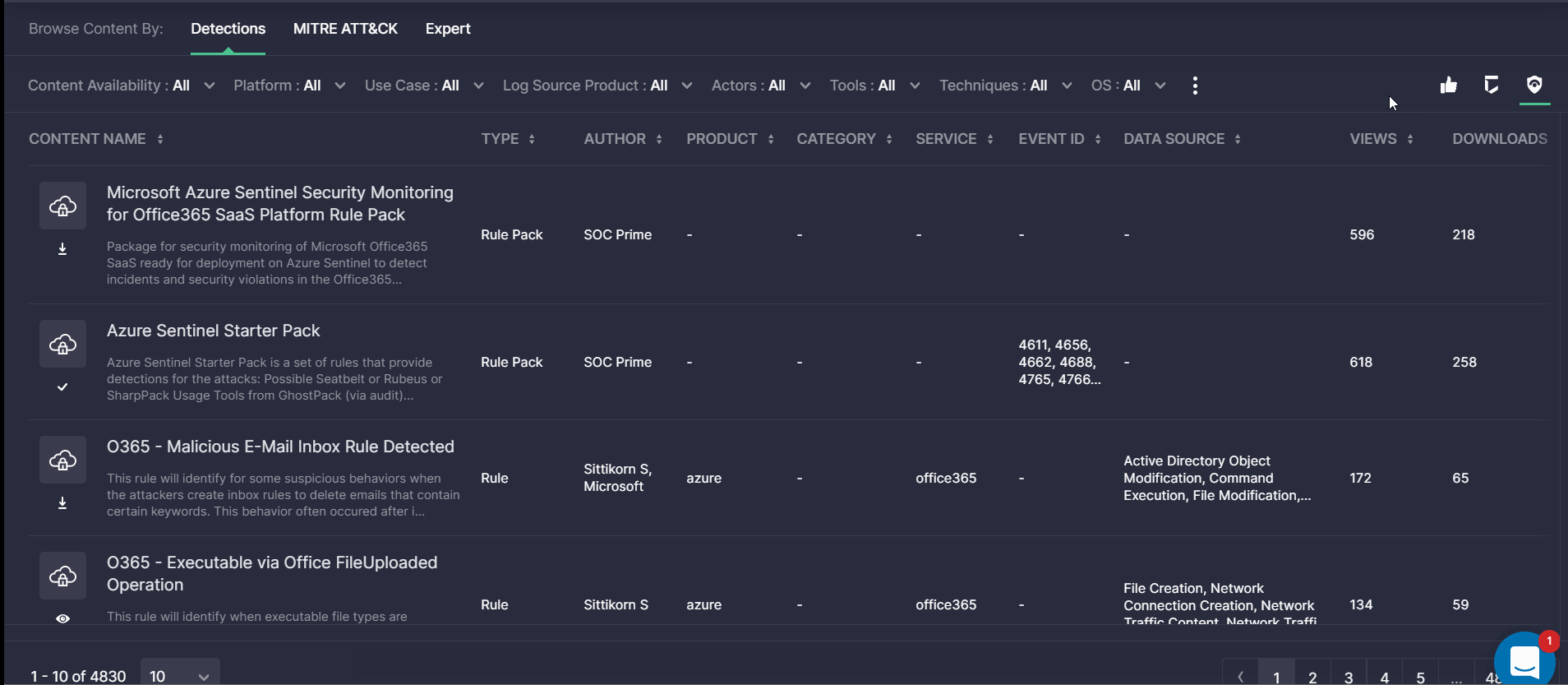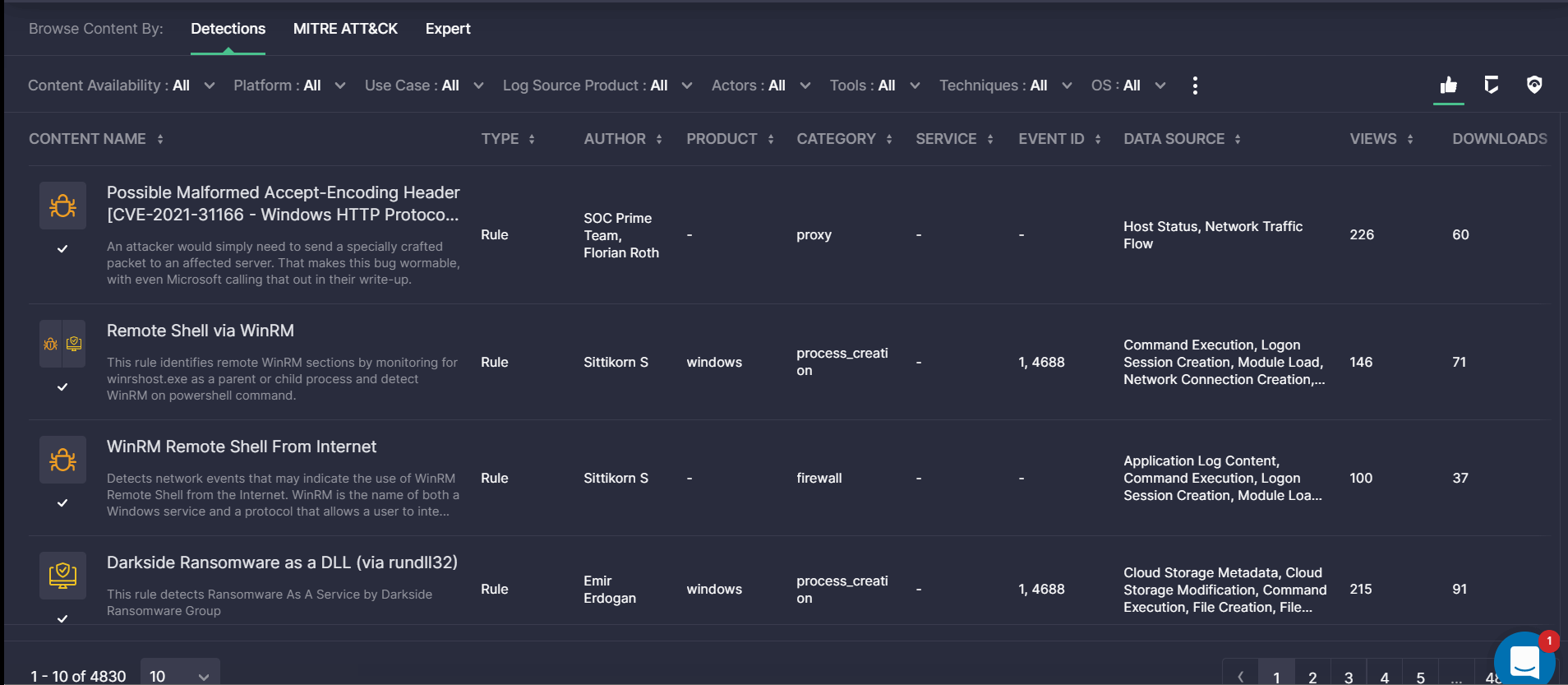
Detection Engineers can switch to their tailor-made view mode by selecting the Detections tab from the Browse Content By functionality on the Content page. For the most personalized role-based experience, the Detections view mode displays all highly relevant filters at once, which can help Detection Engineers analyze the latest threats and adversaries at a glance, as well as streamline the continuous log management delivery as part of their daily procedures.
The content list is arranged accordingly to simplify the process of defining attack priorities and enabling continuous event collection by displaying the following details under the corresponding columns:
- Type
- Author
- Log Source Product
- Log Source Category
- Log Source Service
- Event ID
- Data Source
The Detections view mode also adds to a more streamlined and intuitive content sorting using the corresponding icons:
- Recommended (default option)
- Google Chronicle
- Microsoft
Log Source Product Filter Improvements
To streamline the content search and personalize the platform experience for our customers, we’ve introduced improvements to the Log Source Product filter logic for the Expert and Detections view models. Particularly, new three fields have been added to the Lucene query dictionary to enable content filtering by the log source product:
- tags.category
- tags.product
- Tags.service
To keep Threat Detection Marketplace users informed on the latest platform changes, we’ve updated the Lucene Search section in our dedicated Help Center guide. Now the platform guide displays three new fields based on the newly added log source categories that can be used in the search queries when switching to the Lucene syntax.
Moreover, to maintain consistency with the Log Source Product filter enhancements across the entire platform functionality, we’ve reduced several fields previously available in Rule Master. Now security performers will see a single Log Source Product option instead of a set of deprecated filters, such as Application, Firewall, Network Equipment, Operating System, Proxy, etc. Removing these filters makes the profile customization flow faster and more intuitive.
Content Quality Enhancements
At SOC Prime, we’re constantly striving to improve the content quality when translating Sigma behavior-based detections to various SIEM, EDR, and NTDR language formats.
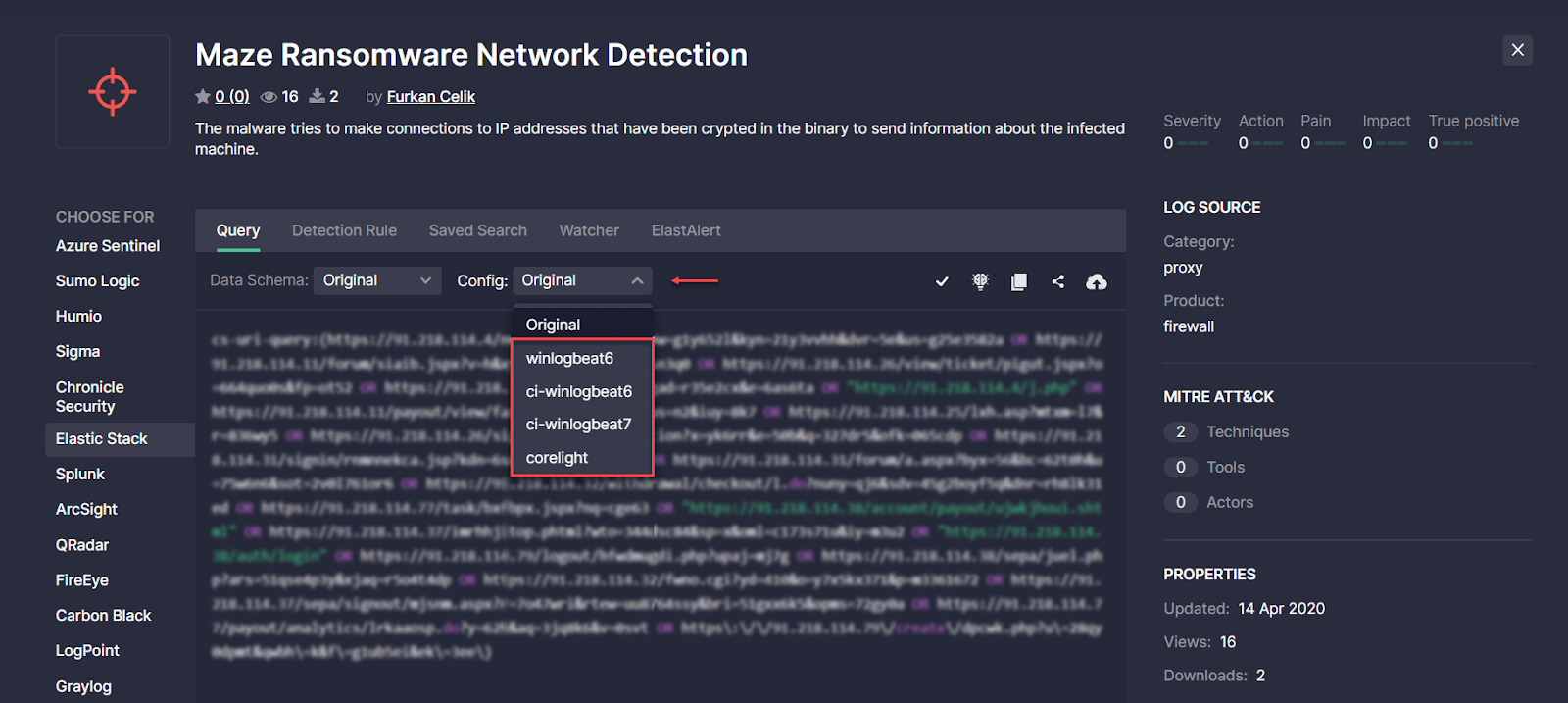
Elastic Stack Translation Improvements
The latest Threat Detection Marketplace version 4.11.0 provides improvements to Elastic Stack language format. For an even more intuitive threat detection experience, we’ve updated all options with alternative translations in the Config drop-down list to make them consistent across all content types available for the Elastic Stack platform. Elastic customers can now see the same options in the Config drop-down list no matter what content type has been chosen — Query, Detection Rule, Saved Search, Watcher, or ElastAlert:
- winlogbeat6
- ci-winlogbeat6
- ci-winlogbeat7
- corelight
Metadata for Chronicle Translations
For an improved threat detection experience of Google Chronicle customers, we’ve recently added the ability to include more detailed metadata when translating Sigma rules to the YARA-L language format. The newly added meta parameter can now contain the following additional information when converted from the Sigma language:
- Reference to the source links, including the Threat Detection Marketplace reference
- Rule status
- Custom tags from Threat Detection Marketplace, including “Community” or “Exclusive”
- False positives
- Level
Sigma Rules with Multiple Log Sources
Sigma behavior-based detections that contain multiple log sources are known to cause issues when translating them into various language formats. We’ve hit a snag when such Sigma rules were wrongly translated with a single log source instead of multiple ones. With this release, we’ve improved a number of translation issues related to such types of Sigma rules, including those for Azure Sentinel, Google Chronicle, and the Elastic Stack. As a result, Sigma detections with multiple log sources are properly translated to other language formats.
Cyber Library Updates: New Content Guide for Creating Rules in the Google Chronicle Instance
At SOC Prime, we’re constantly looking for ways to share cybersecurity knowledge across our global community. With this in mind, we have created the Cyber Library that provides free access to content guides for the majority of SIEM, EDR, and NTDR solutions powered by Threat Detection Marketplace. This latest update introduces a deep dive content guide for creating YARA-L rules from scratch right in the customers’ Google Chronicle instance with detailed guidelines and examples. 
Key Bug Fixes & Improvements
With this release, we’ve made the following bug fixes and improvements to Threat Detection Marketplace:
1) Platform experience improvements:
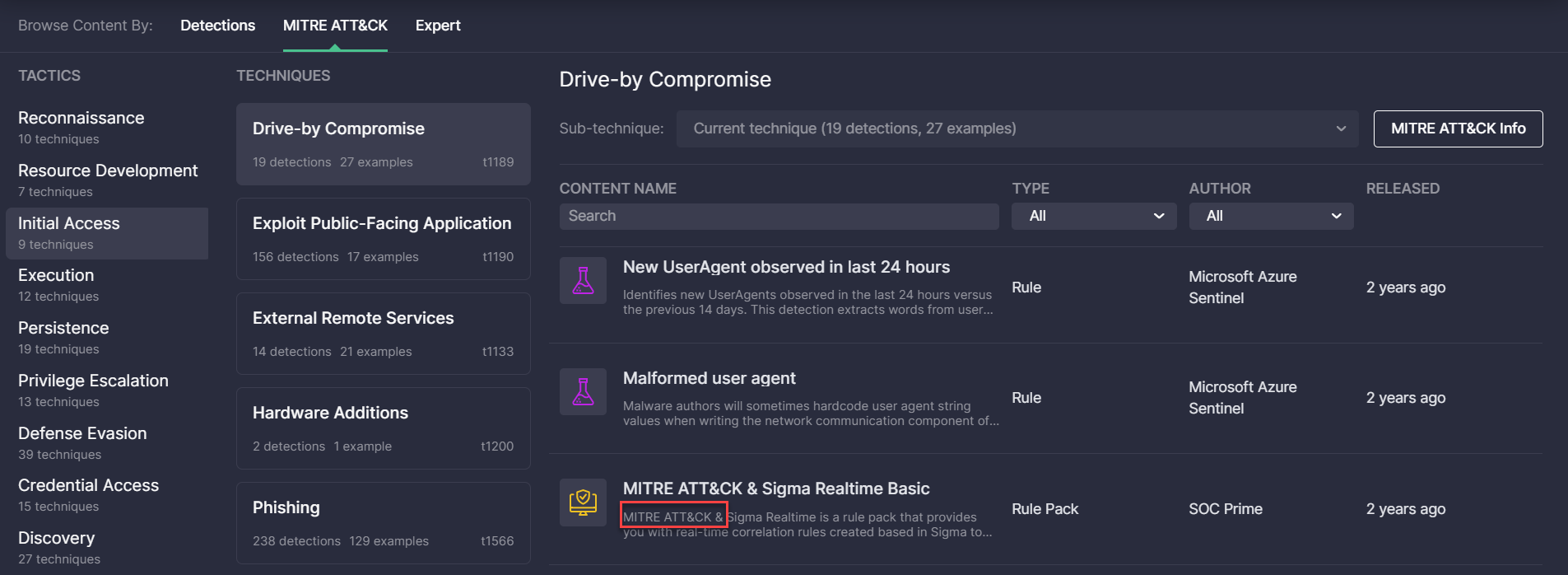
- Fixed the issue with the HTML entity (&) display in the rule descriptions on the Content page when the MITRE ATT&CK view mode is selected. After the update, the ampersand is properly displayed in rule descriptions as in “ATT&CK” instead of the HTML entity:
- Updated the number of rules displayed for users with the Limited Access subscription that appears as a message prompting them to switch to a corporate email address for a more insightful platform experience.
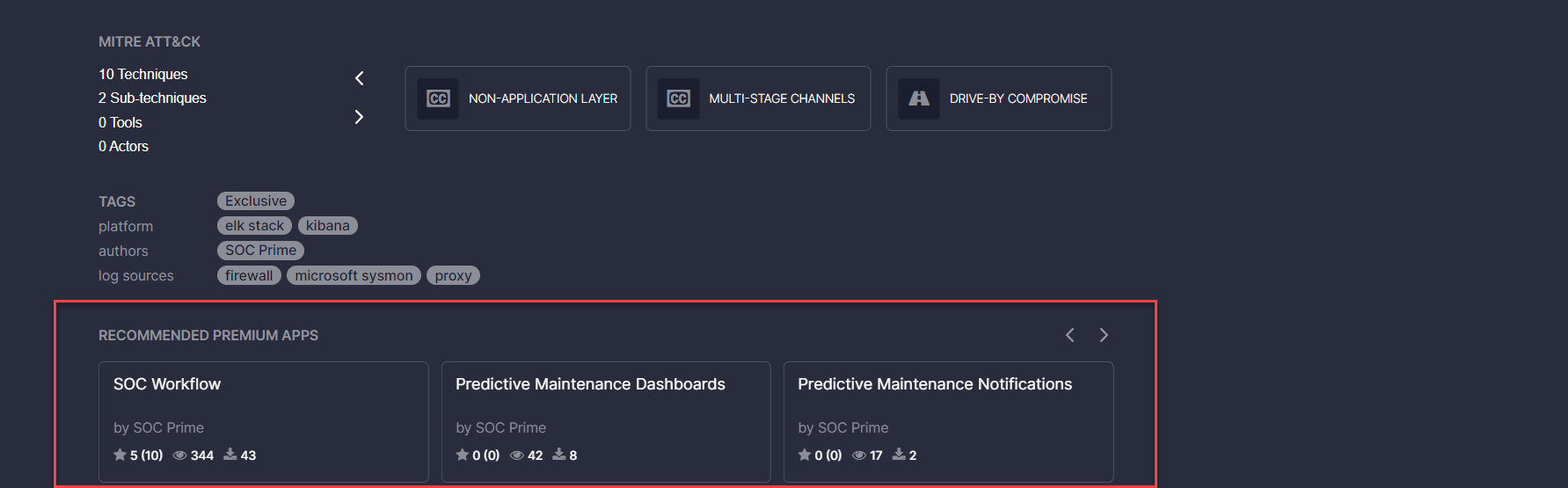
- Fixed the issue with the Unlock icon display in the Recommended Premium Apps section when opening Exclusive content. After resolving this issue, Threat Detection Marketplace users will no longer see this icon for content items available for access.
- Fixed the data display on the Detection Quality Increase pop-up when drilling down to the content details from the Dashboard page. Before this release, the Detection Quality Increase pop-up failed to display all the columns properly.
2) Fixed the position of the tooltip icon next to the Vulnerability Management Specialist role in the Role and Platform section of the user profile: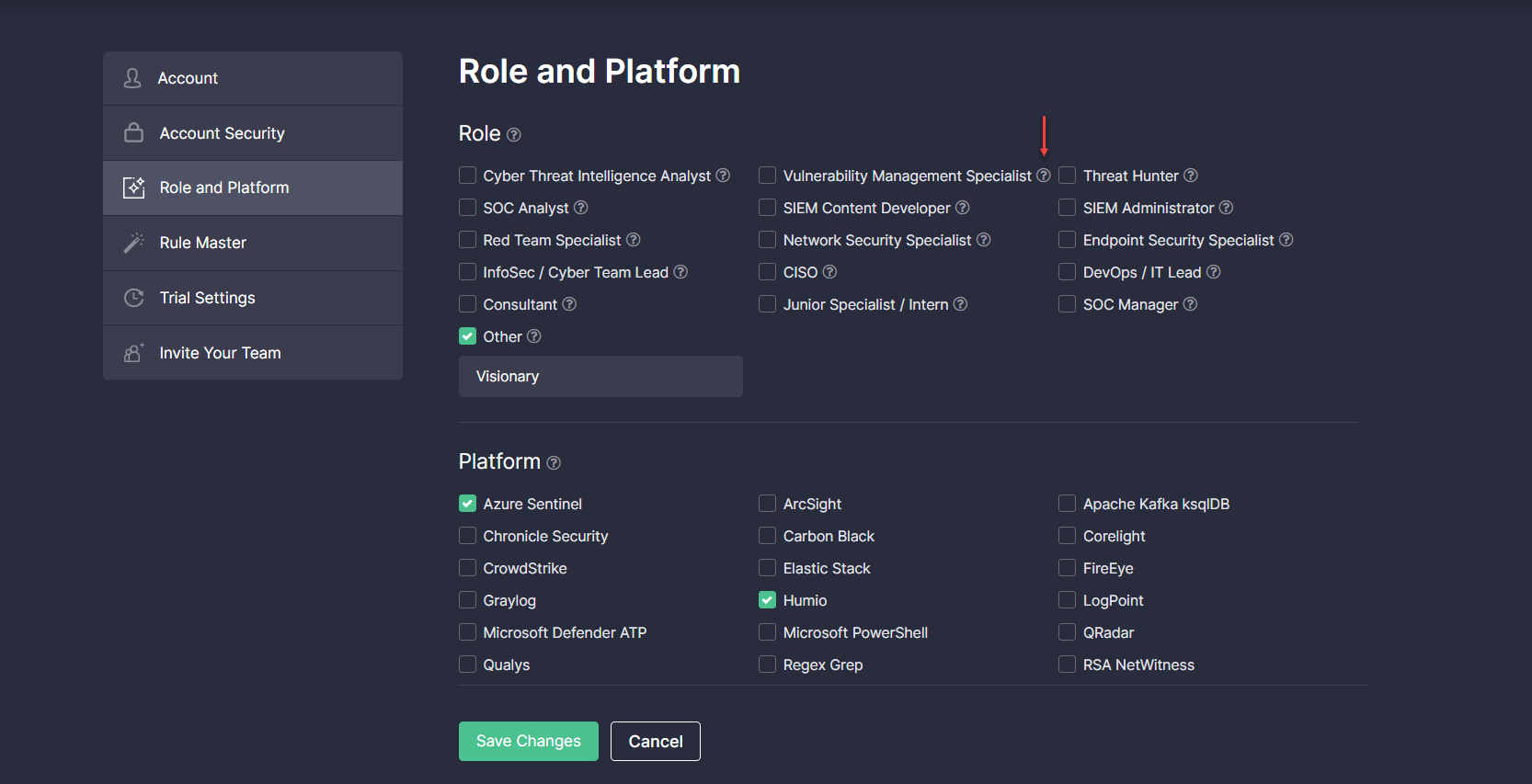
3) In the Cyber Library:
- Fixed the scroll bar position for webinar registration pop-ups in the Cyber Library to ensure a more consistent user experience across the entire platform.
- Fixed the issue with the webinar video display in the fullscreen mode for Safari browsers.
4) Fixed the issue with downloading Rule Packs for users with the Community subscription who have reached the content download limit for their subscription plan. From now on, users will be redirected to the Upgrade page and promoted to upgrade their subscription to increase their content availability options. 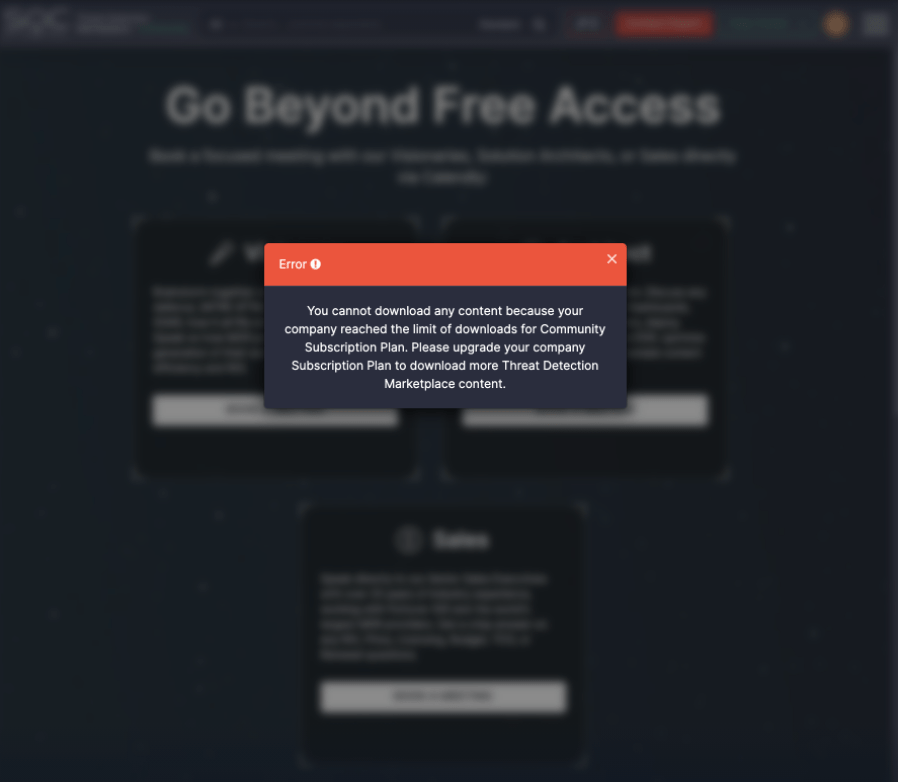
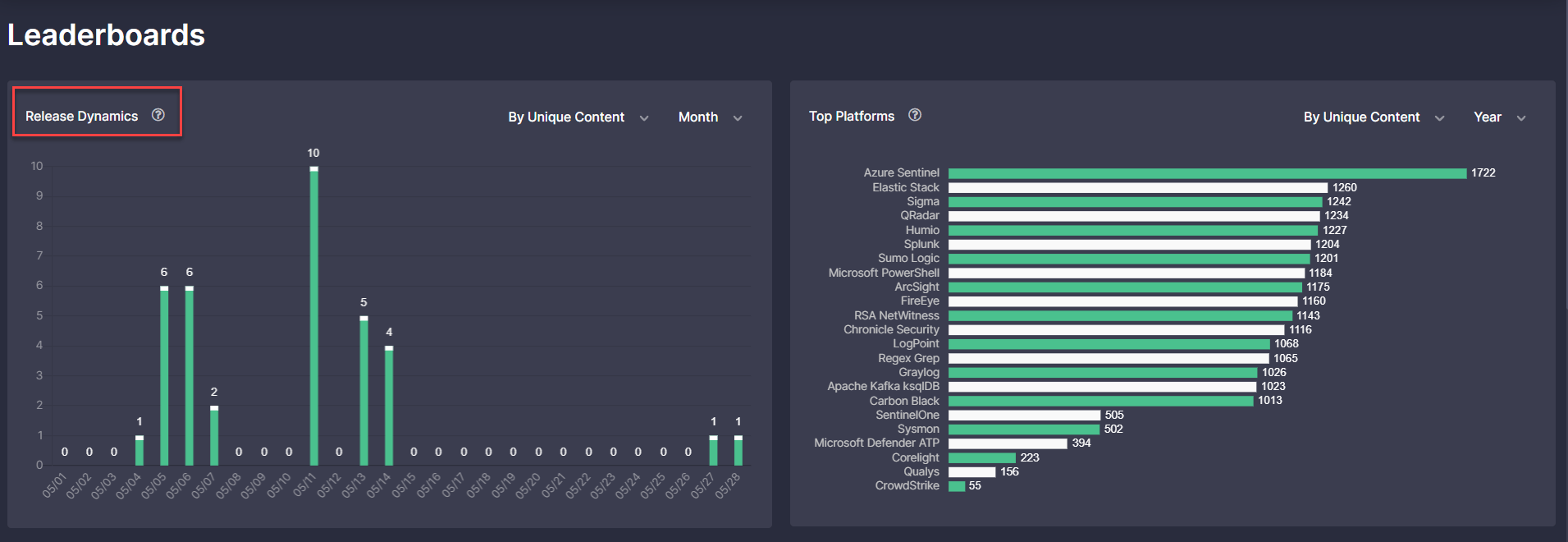
5) On the Leaderboards page:
- Improved the logic for the consistent display of the content amount on the Leaderboards > Release Dynamics chart and on the Content page based on the same filters. The issue occurred when comparing this amount on the Release Dynamics chart and then drilling down to the Content page filtered by the corresponding Lucene query.
- Fixed the issue with the data display on the All Content Linked With MITRE ATT&CK chart when switching between various time ranges:
Get a free subscription to Threat Detection Marketplace, an industry-leading Content-as-a-Service (CaaS) platform that powers complete CI/CD workflow for threat detection by providing qualified, cross-vendor, and cross-tool SOC content. Our library aggregates 100K+ SIEM and EDR algorithms tailored to the company’s environment and threat profile. The detections are continuously enriched with additional threat context, verified, checked for impact, false positives, and other operational considerations through a series of quality assurance audits. Eager to participate in threat hunting activities and craft your own detection content? Join our Threat Bounty Program!