Threat Detection Marketplace Now Supports MITRE ATT&CK® Framework v9

Threat Detection Marketplace version 4.10.0 introduces the support for the latest MITRE ATT&CK framework v9 to advance the threat coverage and provide our customers with an even more intuitive experience while searching for the relevant detection content. Particularly, the recent enhancements to our Detection as Code platform allow content mapping according to the ATT&CK v9, with the new sub-techniques and additional tactics added by MITRE in April 2021. Also, we’ve introduced the new ATT&CK page look and feel, so Threat Detection Marketplace users can see all tactics, techniques, and sub-techniques in one place, switch between them, and seamlessly search for the specific content using available sorting options.
The current version of our platform supports 14 Tactics, 185 Techniques, and 367 Sub-techniques updated according to the latest MITRE release.
Navigation
Now it is even easier to get to the MITRE ATT&CK page. The newly added Browse Content By feature introduces the MITRE ATT&CK view option available right from the Content page. Alternatively, Threat Detection Marketplace users who are accustomed to the old interface can get to the MITRE ATT&CK page from the Tools menu.
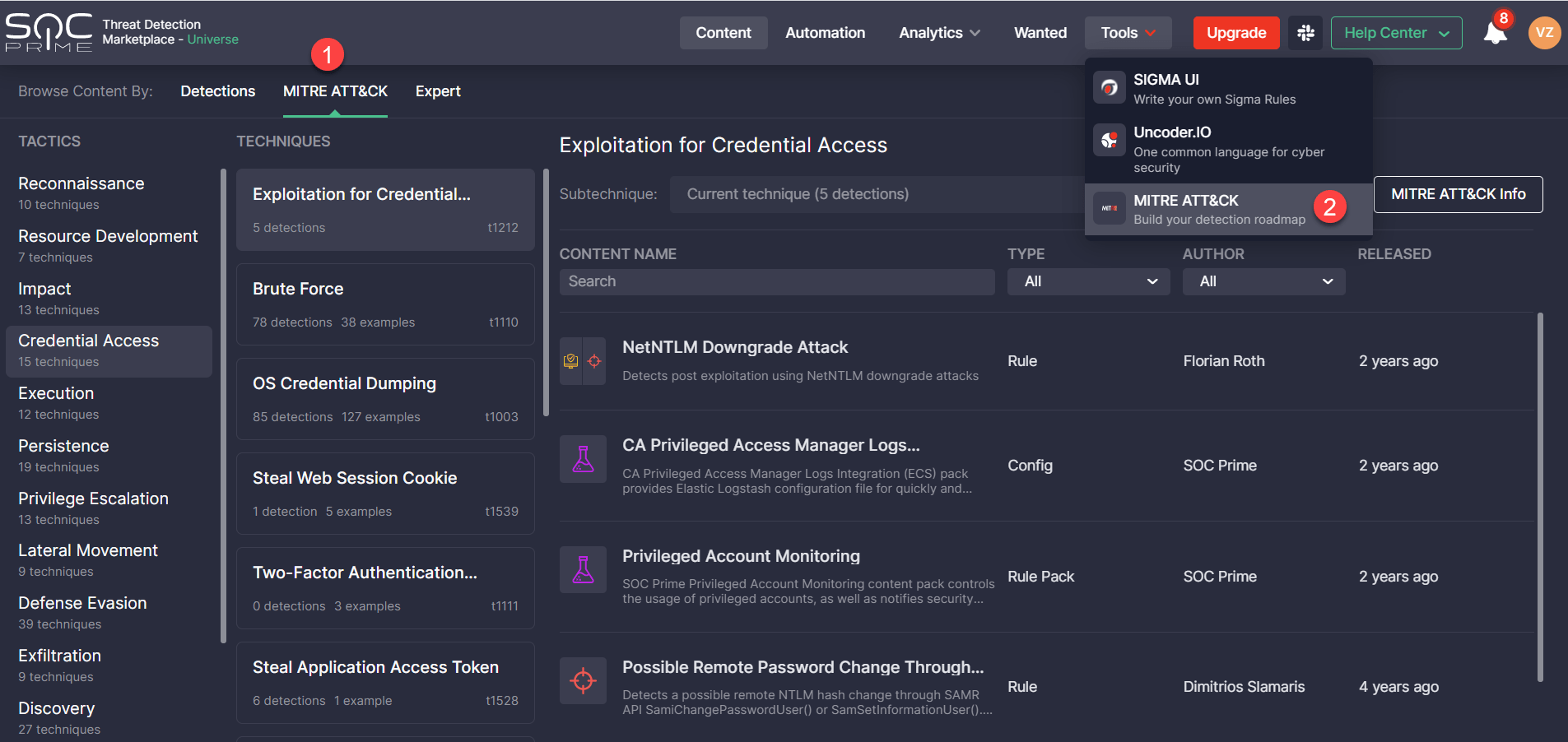
Simplified Look and Feel
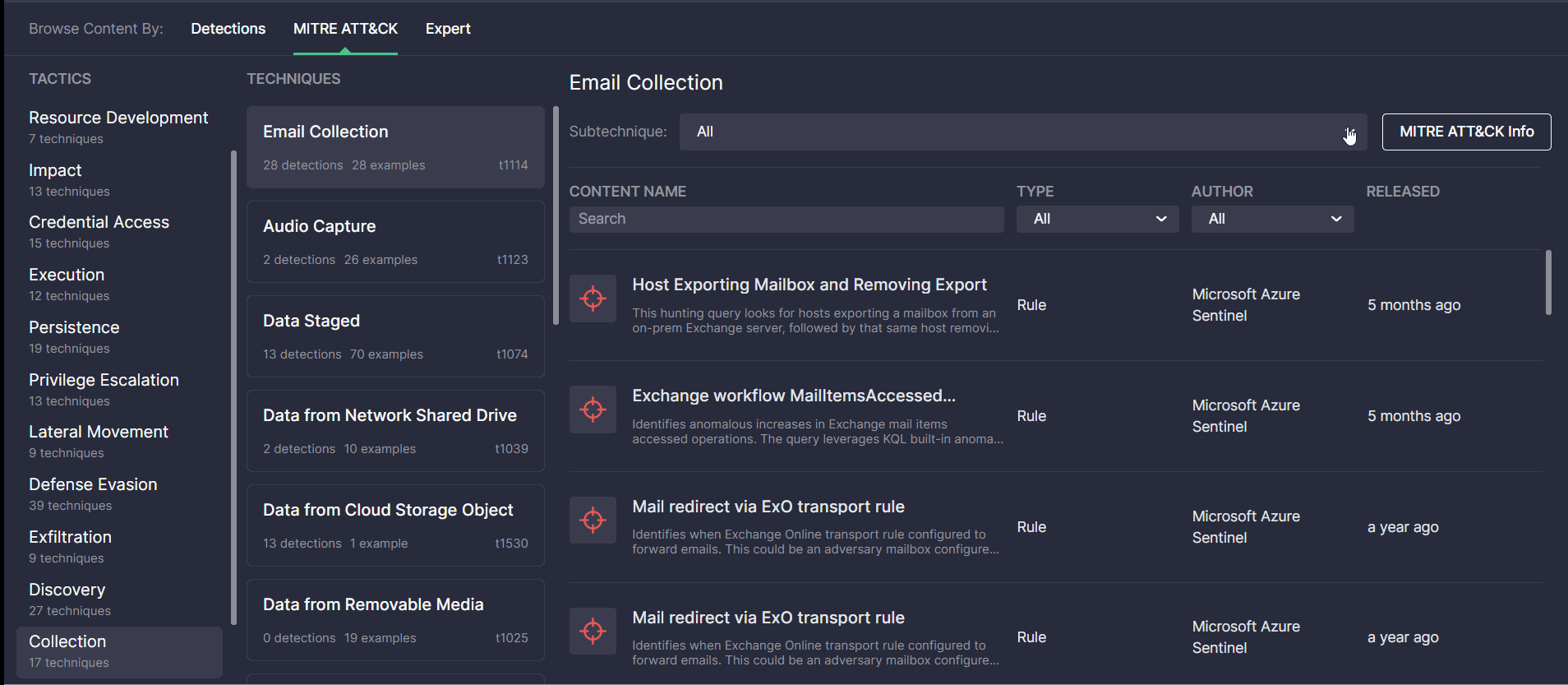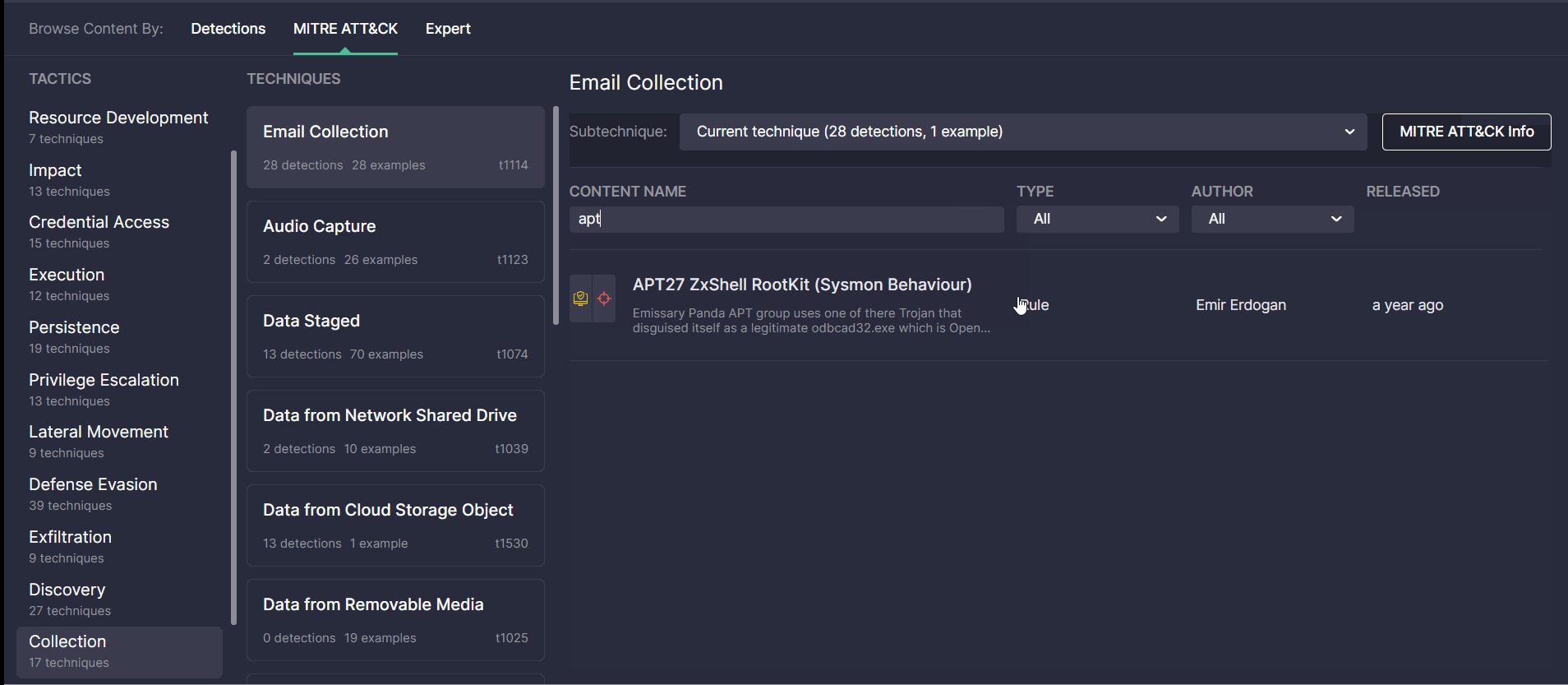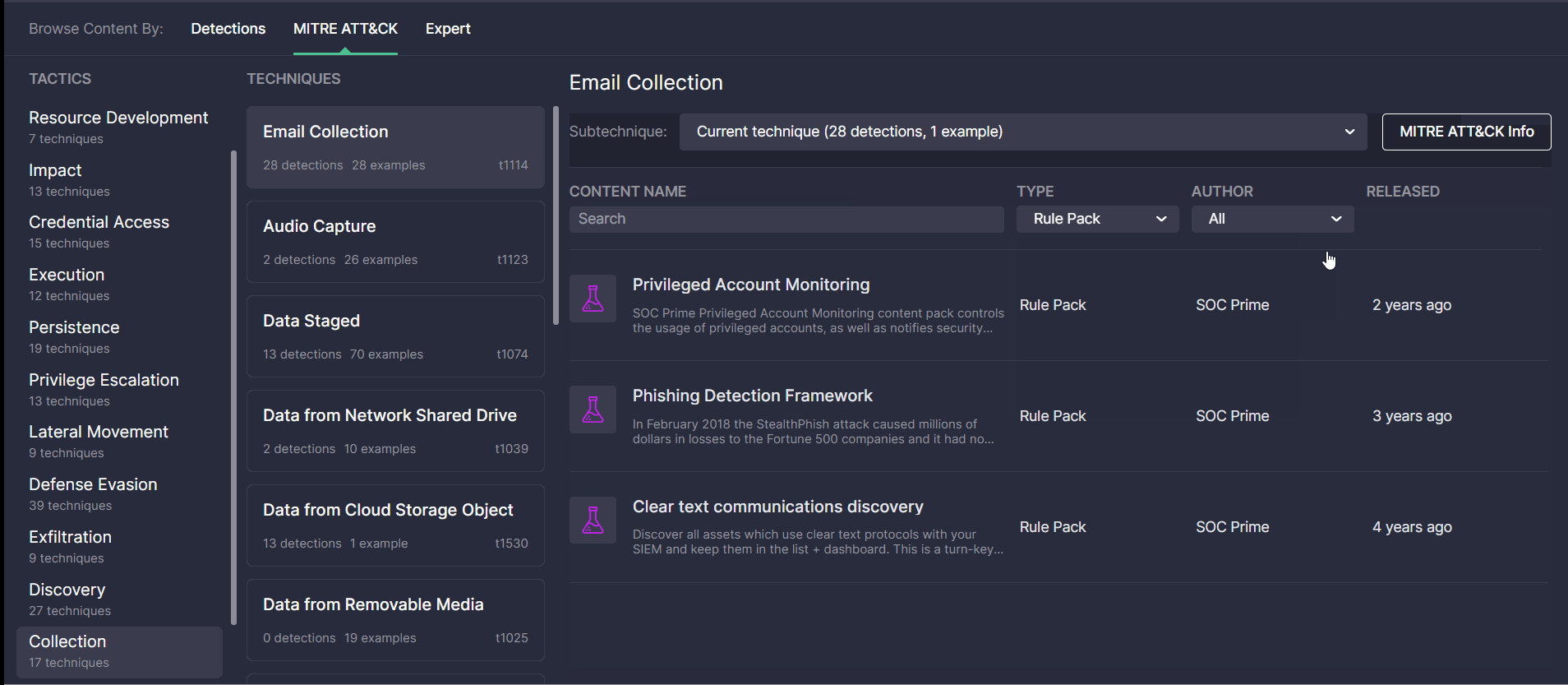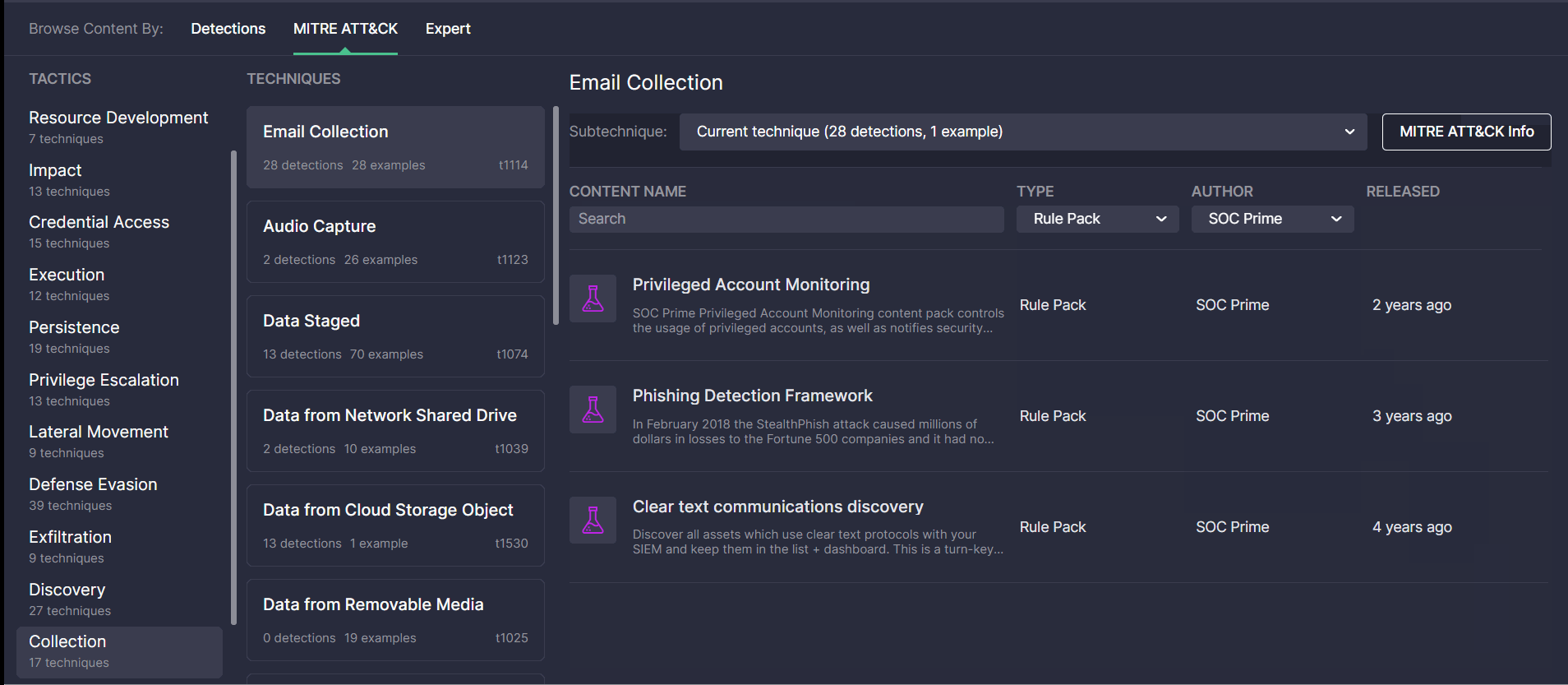
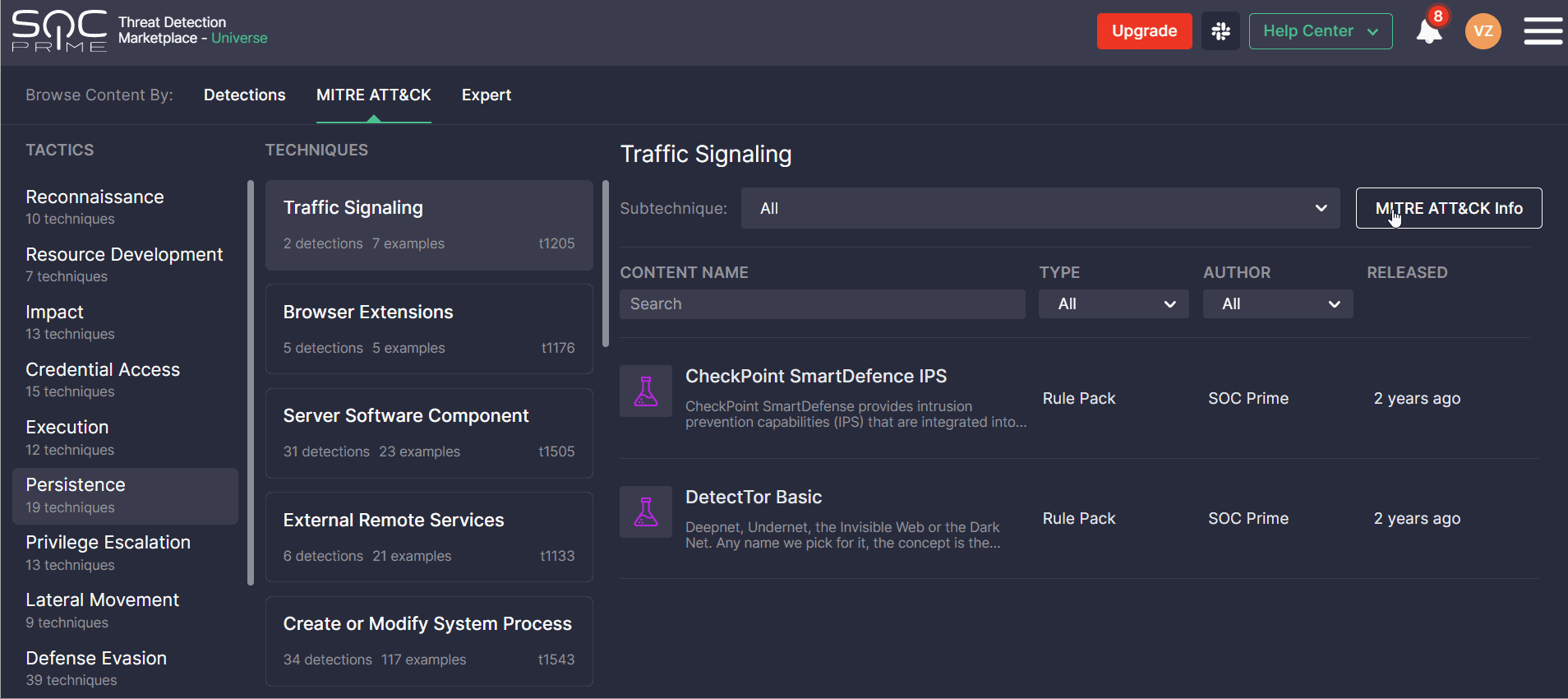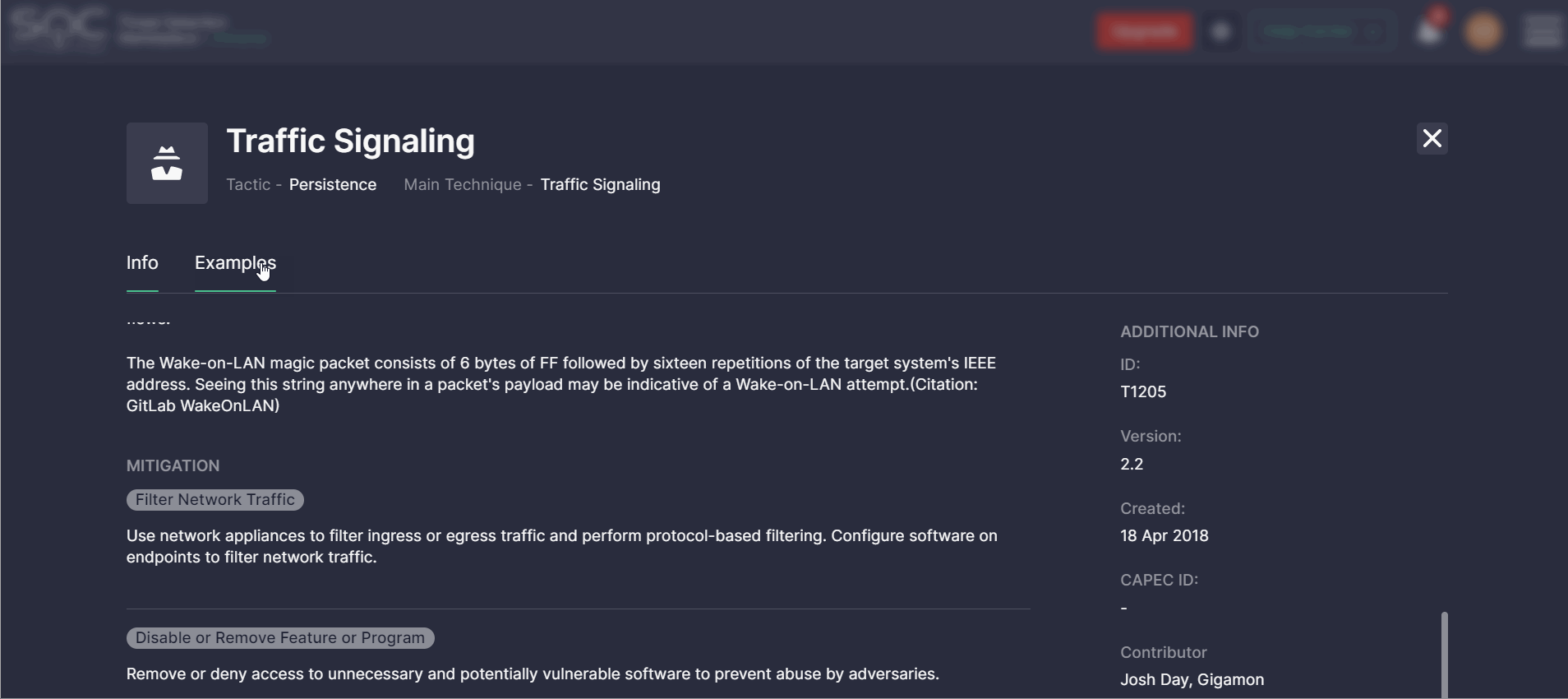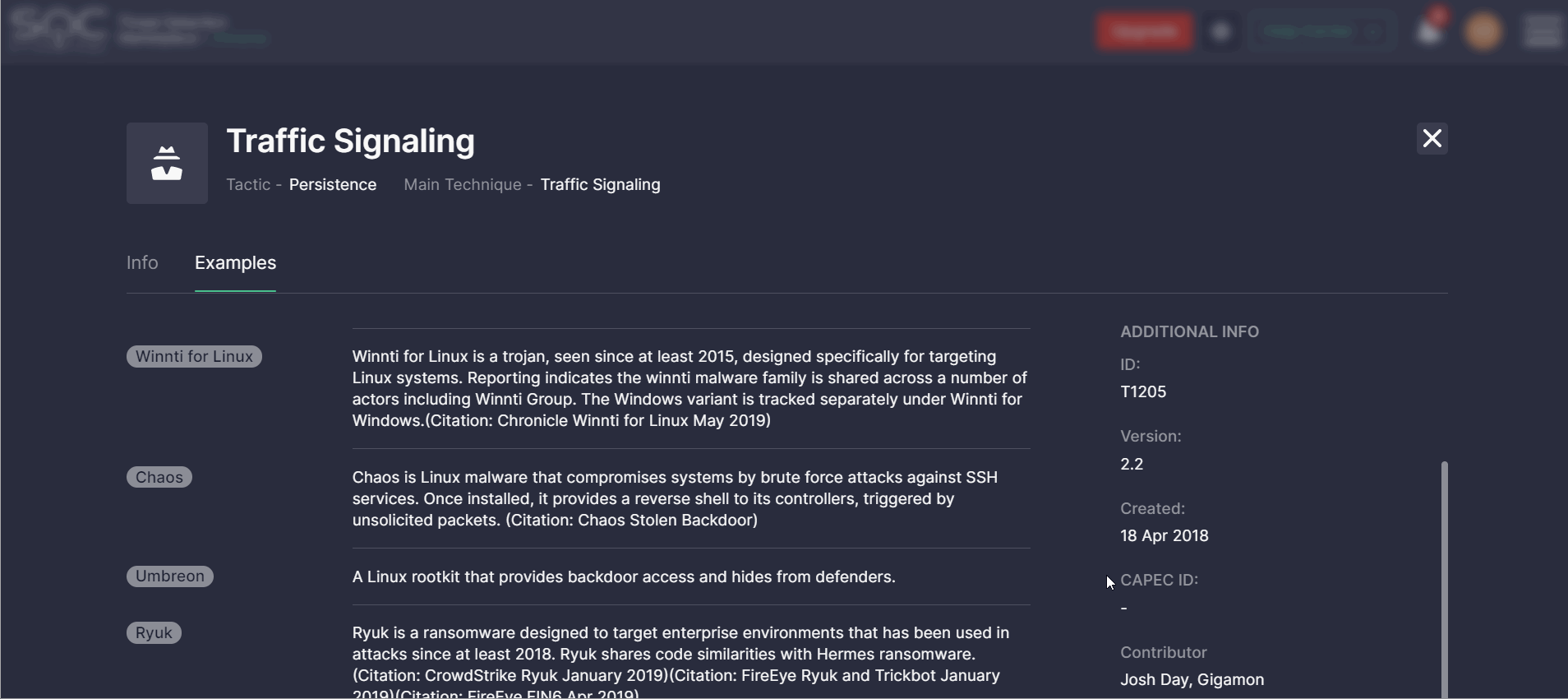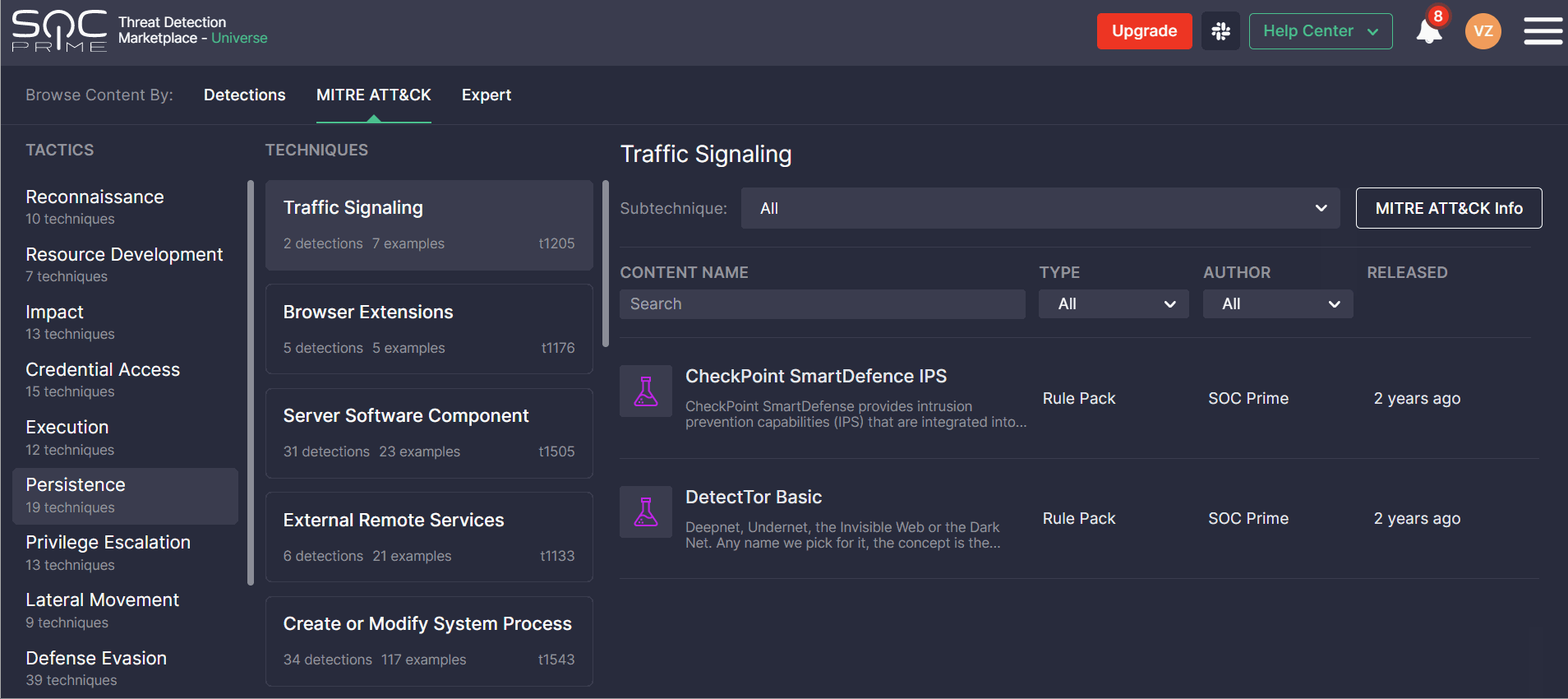
The newly redesigned MITRE ATT&CK page consists of three main sections:
- Tactics — displays the list of all available ATT&CK tactics and the number of techniques each of them is linked to.
- Techniques — all available ATT&CK techniques related to the selected tactic, including the technique ID, as well as the number and examples of content items addressing this technique.
- Sub-techniques — the list of ATT&CK sub-techniques related to the selected technique along with information on content items, their authors, release date, and use cases.
Streamlined Search for Mapped Content
The updated look and feel of the MITRE ATT&CK page enable security performers to search for content items covered by certain ATT&CK tactics, techniques, or sub-techniques much easier and faster. For more convenience, security performers can sort the list of all detections addressing the corresponding ATT&CK sub-technique by Type (like Rule, Rule Pack, Config, and more content types) or the Author of content. The icons with content categories allow capturing at a glance what use cases are more typical of the certain ATT&CK parameters. All content types matching the selected technique and sub-technique are clickable and enable security performers to drill down to the content page on the fly.
ATT&CK Details
By clicking the MITRE ATT&CK Info button in the top-right corner, Threat Detection Marketplace users can drill down to the ATT&CK details and see all the ins and outs of the selected tactic and its main technique. Two tabs are available with the following ATT&CK details:
- Info — provides the description of the selected tactic, available data sources, platforms that can be applied by adversaries, and mitigation procedures aimed to help withstand the adversary activities.
- Examples — displays the list of malicious software, tools, or adversaries associated with the specific tactic and its techniques, such as malware and APT groups. These examples include links to the MITRE ATT&CK methodology page to get a full picture of the tools used for malicious purposes or related adversaries.
The Additional Info on the right-hand side shows the main technique ID, its version, date of creation, and contributors.
Also, to keep consistency across all Threat Detection Marketplace capabilities, we’ve made updates to the Detections and Expert view modes on the Content page, including the filtering functionality. Now all three view modes available on the Content page consistently reflect the latest changes to the MITRE ATT&CK matrix, including the updated stats on tools, actors, and techniques, as well as expert filters expanded by sub-techniques. Similarly, the Dashboards and Leaderboards page can now visualize updated ATT&CK information as per the framework v.9.
To share our experience and contribute to the MITRE ATT&CK best practices, SOC Prime is participating in the seventh EU ATT&CK Community Workshop which takes place online on June 1-2, 2021. Our CEO, Andrii Bezverkhyi, will speak about Sigma customization and provide insights into SOC Prime’s Threat Bounty Program. Check out the agenda to learn more: https://www.attack-community.org/event/
Get a free subscription to Threat Detection Marketplace, an industry-leading Content-as-a-Service (CaaS) platform that powers complete CI/CD workflow for threat detection by providing qualified, cross-vendor, and cross-tool SOC content. SOC Prime’s library aggregates over 100K queries, parsers, SOC-ready dashboards, YARA and Snort rules, Machine Learning models, and Incident Response Playbooks tailored to 23 market-leading SIEM, EDR, and NTDR technologies and mapped directly to CVE and MITRE ATT&CK® frameworks. Eager to craft your own detection rules? Join our Threat Bounty Program and get rewarded for your input!


