June ‘22 Updates
This June we introduced several significant updates related to SOC Prime’s Threat Bounty Program to acknowledge the contribution of the Program members and smooth their experience with Sigma rules creation. Now, all SOC Prime users can access detailed information about Threat Bounty authors’ achievements on a dedicated page. Also, the beta version of Sigma Rules Slack Bot is out, allowing to submit Sigma rules directly via Slack.
Sigma Rules Author Page
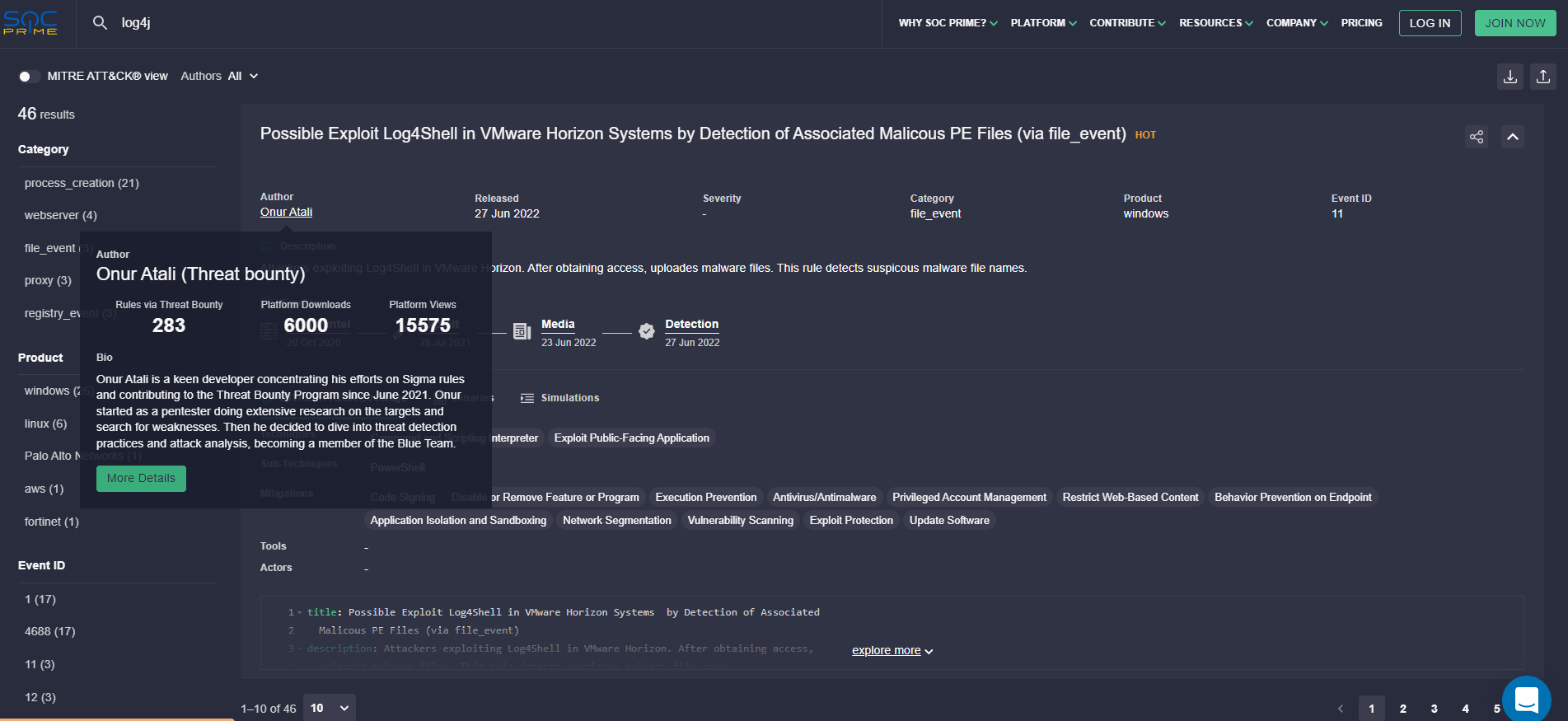
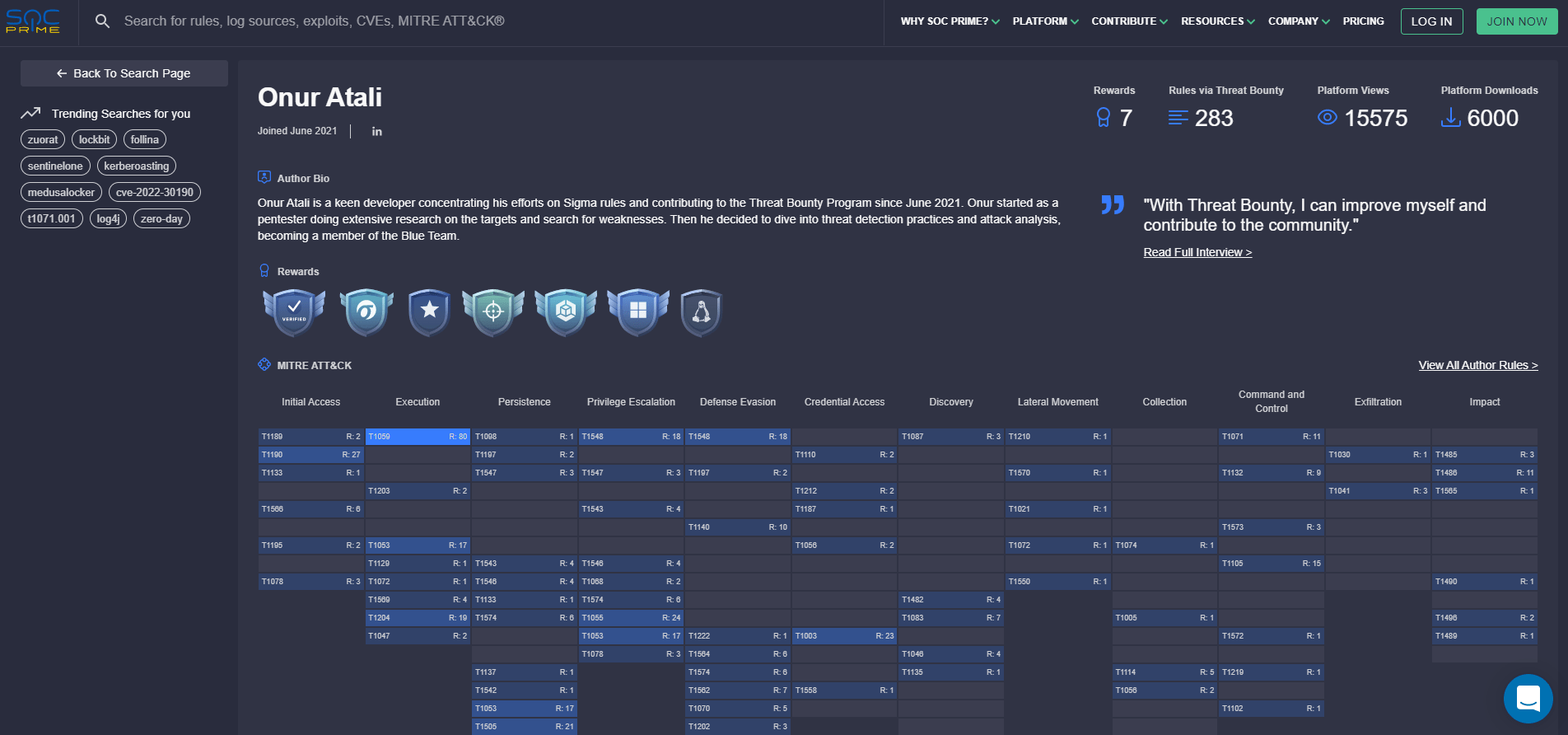
Starting from June 2022, all Threat Bounty Sigma rules authors can see the information about their achievements on SOC Prime’s Search Page. To open the page with your personal Threat Bounty achievements, open More details for Sigma Author available within the rule metadata.
On the Author Page, the Threat Bounty Sigma authors can see their achievements and the badges assigned to them for their Threat Bounty contributions to SOC Prime’s Detection as Code Platform:
Sigma Rules Bot for Threat Bounty
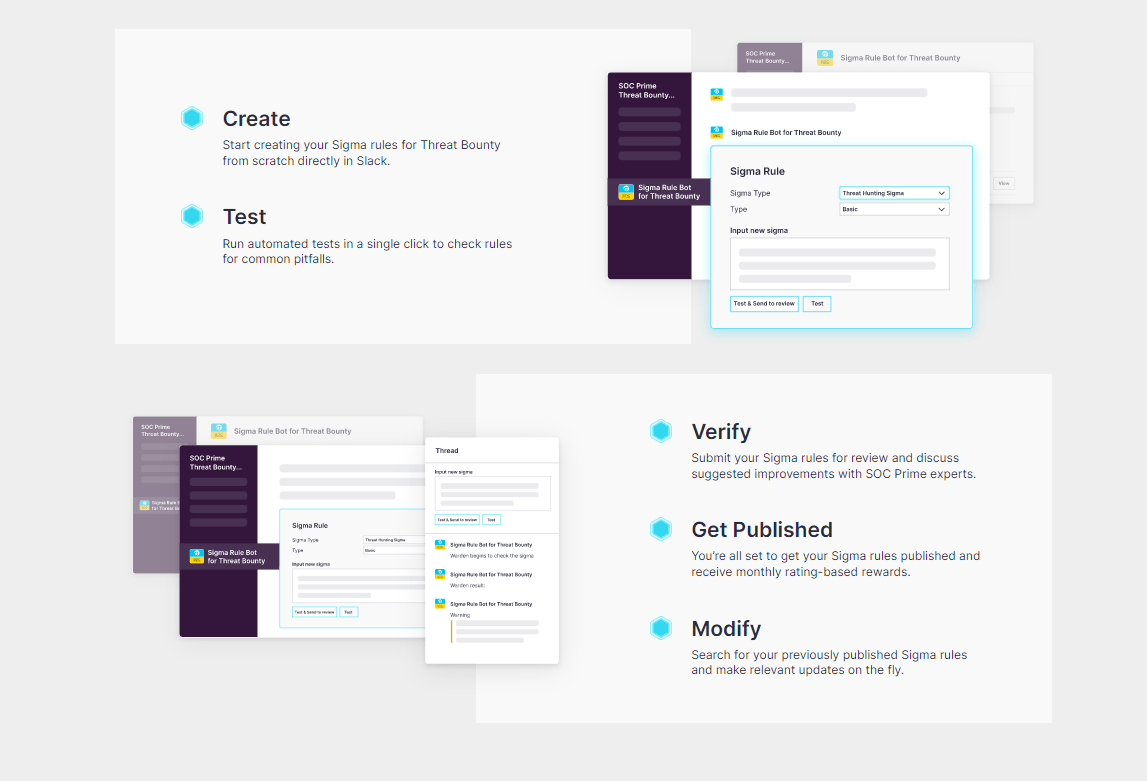
SOC Prime has released a beta version of the Sigma Rules Slack bot. With it, Threat Bounty members can contribute Sigma rules directly via Slack which enables real-time cooperation and enhances the collaborative cyber defense. Using the Sigma Rules Slack bot, the community Sigma authors can:
- Create Sigma rules directly in Slack.
- Get the rule checked with the automagic Warden checkup which instantly prompts the author about the common known issues and possible improvements to polish the rule before submitting it to review by SOC Prime experts.
- Get the rule reviewed by content experts of the SOC Prime Team who provide their feedback directly via Slack.
- Modify Sigma rules which were earlier created via the Slack bot or published to the SOC Prime Platform.
Currently, the Sigma Rules Bot is used by a limited number of experienced Threat Bounty members who are very excited about the improved experience of publishing their verified Sigma rules to the SOC Prime Platform.
June ‘22 Publications
In June, 110 rules from Threat Bounty members successfully passed the verification and validation by SOC Prime and were released to the SOC Prime Platform. However, 333 rules suggested by the community members were declined for the reasons of content quality and content duplication.
The detections submitted by Threat Bounty authors are available to users of the SOC Prime platform based on their current Subscription Plan. Additionally, the detections submitted by Threat Bounty members are included in our news and blog articles providing the security experts with additional information about the latest threats.
TOP Authors and Rewards Information
The average payout to active content contributors in June was $1,538. The following Threat Bounty content authors gained the highest rating based on the usage of their published content by unique SOC Prime clients:
We suggest the Threat Bounty authors follow the wanted_list recommendations in the community Slack channel which is available for the approved Threat Bounty members who have activated accounts in the Developer Portal.
Top Rated Content
Suspicious Threat Actor Execution by Detection of Associated Commands Related to COVID-19 [Targeting Indonesia] (via cmdline) threat hunting Sigma rule by Osman Demir detects suspicious covid19-related command line activity.
Possible Backstab Tool EDR Defense Evasion by Detection of Associated Commands (via cmdline) exclusive Sigma rule by Sittikorn detects Backstab tool that will use a local administrator account to kill antimalware protected processes by leveraging sysinternals’ Process Explorer (ProcExp) driver, which is signed by Microsoft.
Suspicious PureCrypter Loader Persistence by Adding of Run Key to Registry (via registry_event) Sigma rule by Osman Demir helps to detect possible malicious activity when PureCrypter Loader adds entries to the registry run key to ensure persistence. Read more about the related malicious activity in our blog.
Possible Threat Actor Activity by PowerShell Connecting to Dropbox (via network_connection) threat hunting Sigma detection rule by Onur Atali detects the accessing suspicious dropbox domain address via powershell.
Possible Execution by AppInstaller Process Outbound Connection (via network_connection) threat hunting Sigma rule by Onur Atali detects suspicious outbound network connection attempts by the AppInstaller process.
These rules and all the content published via the Threat Bounty program were validated by the dedicated team of SOC Prime experts. The Sigma rules are applicable for various SIEM, EDR, and XDR solutions supported by the SOC Prime Platform, and are aligned with the latest version of the MITRE ATT&CK® framework.