SOC Prime Now Supports Snowflake, Next-Gen SaaS Data Warehouse Solution
Automatically Pull Queries Tailored to Custom Data Schemas Directly Into Snowflake Environment
At SOC Prime, we are committed to delivering Detection-as-Code operations embracing an innovation-driven approach to cybersecurity. In response to a rising trend across global organizations to transition to the cloud, SOC Prime’s Detection as Code platform continuously broadens the support for next-gen cloud-based solutions. With this latest release, we’ve enriched the technology stack of 25+ SIEM, EDR, and XDRs with the Snowflake integration enabling security practitioners who leverage this solution to extract more value from SOC Prime’s platform.
The integration unlocks new opportunities for Detection-as-Code practices now enhanced with Snowflake’s all-one-one SaaS platform for data warehousing, data lakes, data engineering, data science, and data application development, which marks the next step in the global industry collaboration driven by SOC Prime’s platform.
Currently, SOC Prime’s platform curates over 7,000 Queries ready to deploy to Snowflake cloud-based environment.
Instantly Reach Curated Snowflake Queries
SOC Prime users can gain access to a broad collection of Sigma rules instantly converted to the Snowflake Query language format after signing up or logging into the Detection as Code platform. To reach the detection content, select Discover > Advanced Search, and then apply Snowflake Queries from the Platform filter. Once filtered, security practitioners can drill down to the selected detection, and the platform will automatically display the rule source code in the Snowflake Query format.
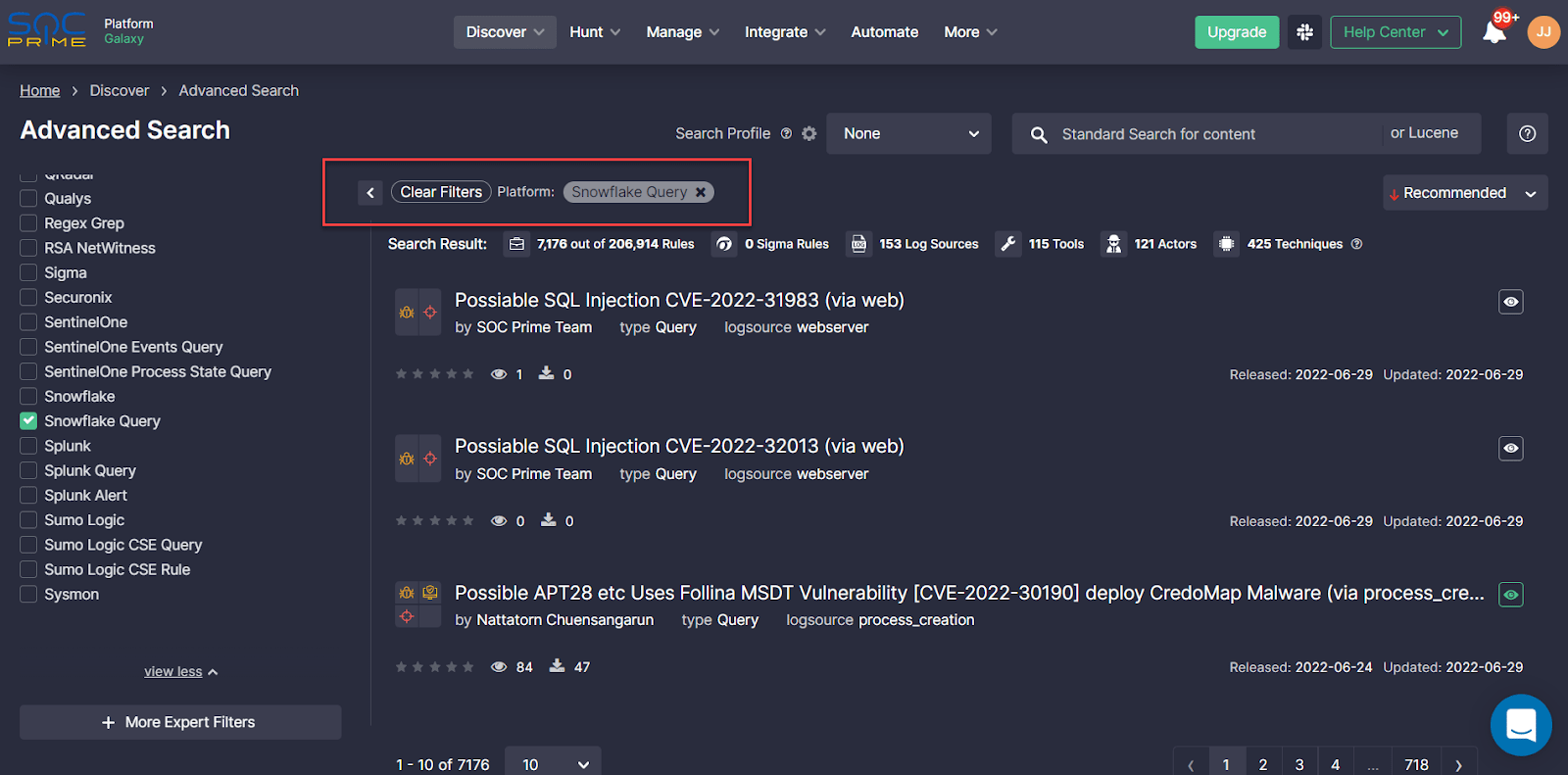
Moreover, for a streamlined threat detection experience, SOC Prime users can pre-configure the Snowflake platform in the onboarding wizard, and the recommendation engine will automatically display all rules in the corresponding language format each time a user logs into the system.
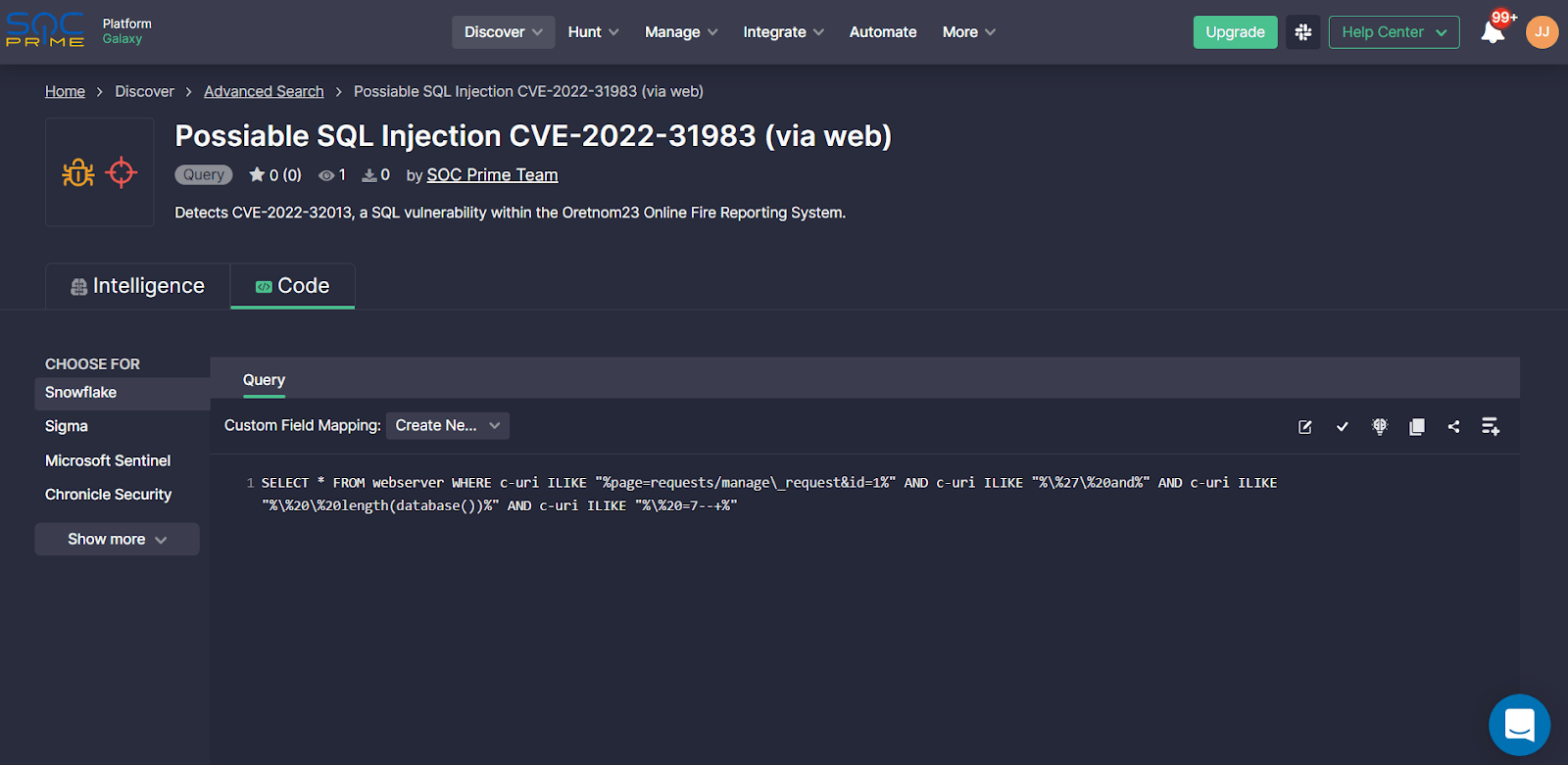
Customize Content Deployments
By default, SOC Prime follows the standard data schema of the target platform following the vendor specifications, which defines a set of fields used for parsing and normalization of data collected from log sources. Still, security professionals frequently have to apply non-standard data schemas or customize the default ones for log collection based on organization-specific needs. To ensure the deployed detection content works properly in the organization’s environment, Snowflake users can take advantage of the Custom Field Mapping capabilities powered by SOC Prime’s platform.
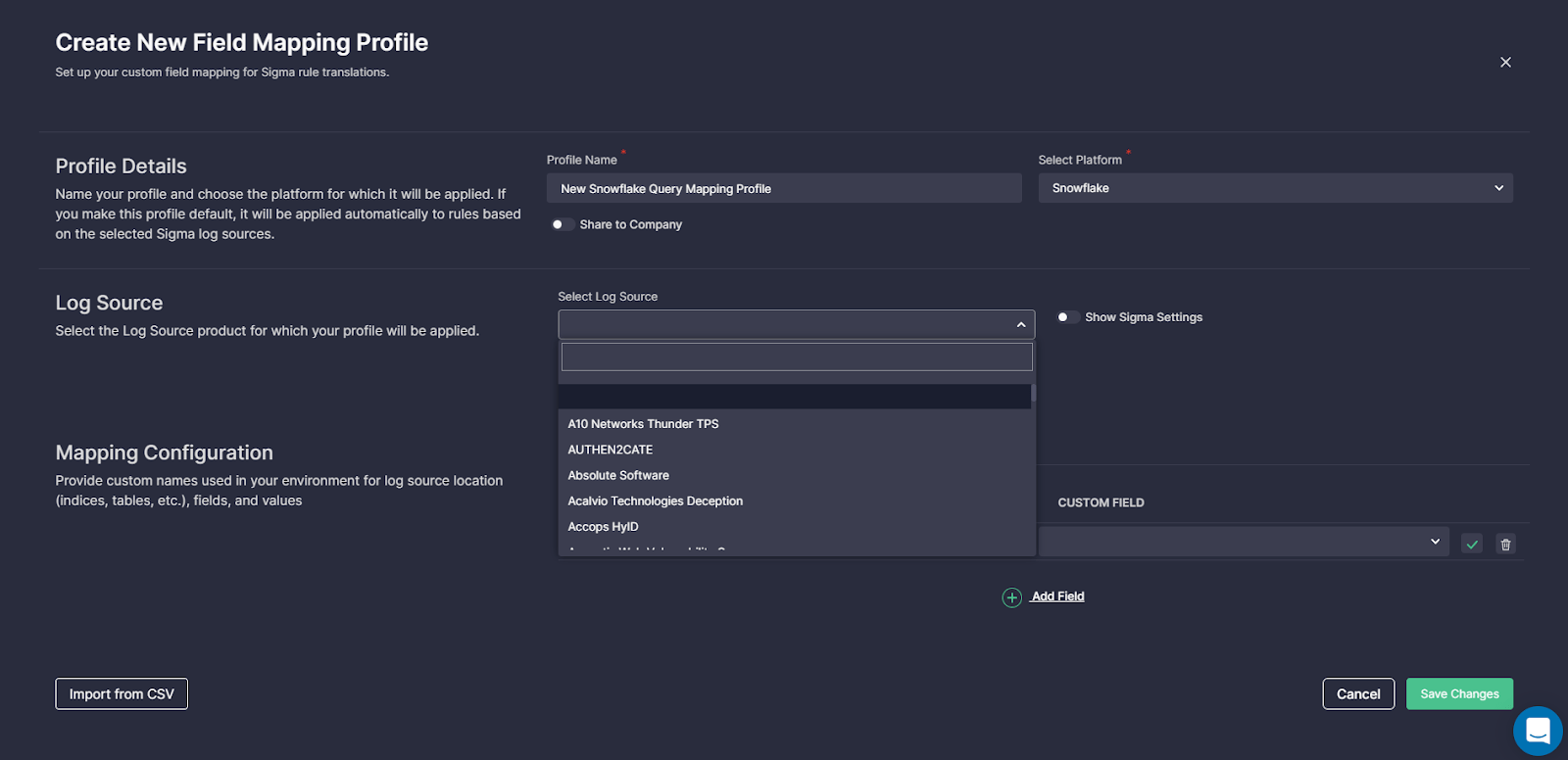
To create a new Custom Field Mapping profile, select Integrate > Custom Field Mapping, and then click the Create button. Alternatively, security professionals can create a new profile right from the rule page.
- In the Profile details, choose a name for a new Custom Field Mapping configuration.
- In the Log Source section, select the log source product from the list of options.
- Finally, provide the details of the log source location used in your environment, like tables and indices, as well as customize field names and their values to map them to the default ones.
To shave seconds off content deployments, SOC Prime’s platform allows pre-configuring the Custom Field Mapping settings in advance using the Log Source section of the onboarding wizard. Please refer to this blog article to learn how to seamlessly go through a one-time configuration and set up the platform to your unique security needs. Once configured, the log source location details you’ve provided will be automatically applied for subsequent content deployments. What’s more, you will have a unique Custom Field Mapping profile generated for each provided log source product, which ensures a fully customizable experience.
Snowflake users can tailor the Query format to a non-standard data schema right from the content item page by choosing the corresponding Custom Field Mapping profile.
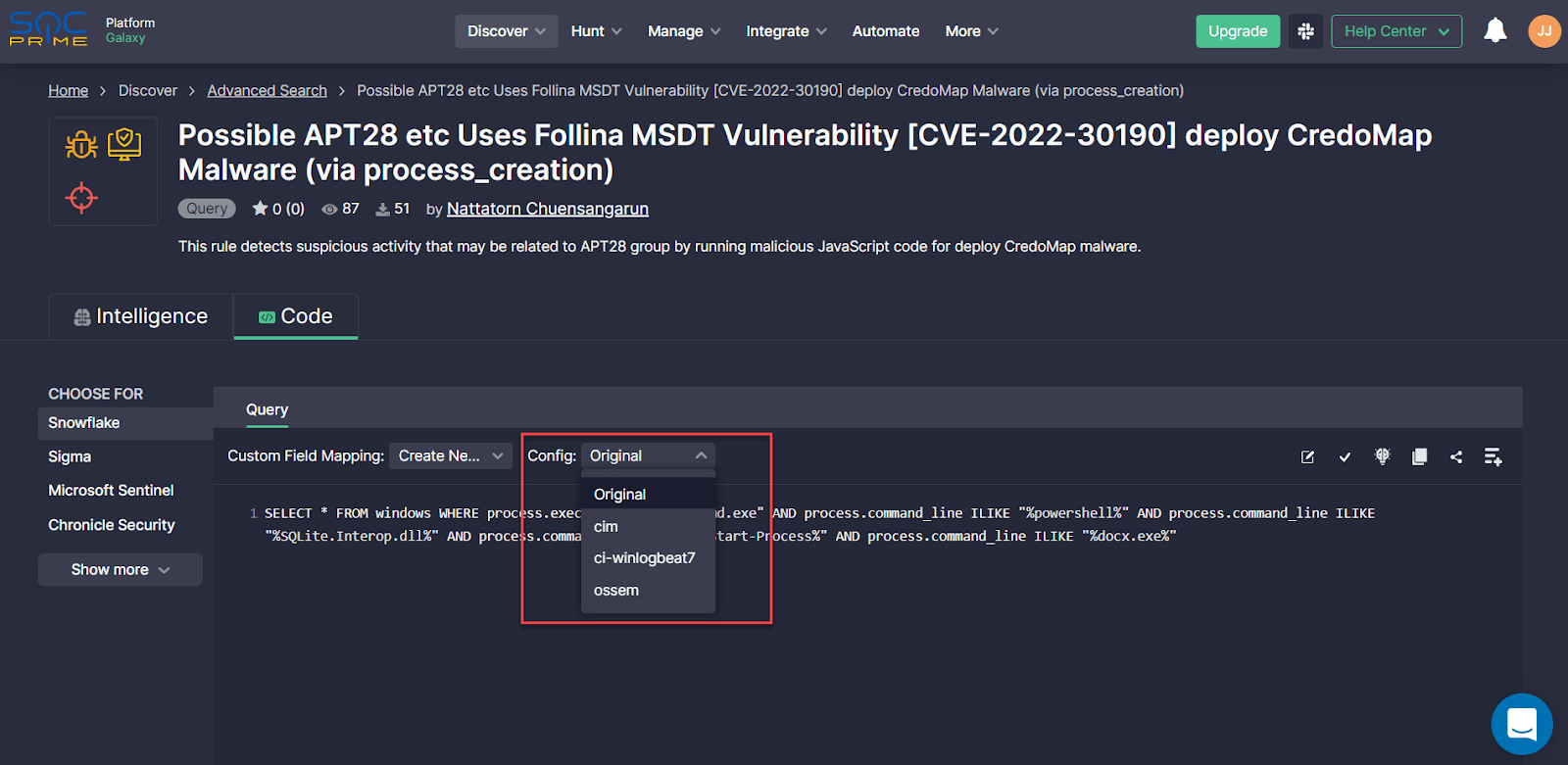
In addition to non-standard mapping configurations, security practitioners can also adjust Snowflake Queries to alternative data schemas. To tailor content deployments to an alternative data schema, click the Config drop-down list and select the schema type of your choice, like Open Source Security Events Metadata (OSSEM), Common Information Model (CIM), or ci-winlogbeat7. Once selected, this detection will be adjusted to the alternative format and deployed accordingly directly into the Snowflake environment. By default, the Original option is pre-selected meaning the content deployment will apply a standard data schema.
Accelerate Query Deployment Using API
Apart from manual content deployments, SOC Prime users can automatically pull Snowflake Queries directly into their cloud-native instance leveraging the SOC Prime Continuous Content Management (CCM) API. SOC Prime’s platform enables running your own scripting based on specific API queries and endpoints to generate unique Content Lists matching the organization’s security needs and then automatically pull relevant Snowflake Queries from these lists. The CCM API capabilities allow teams to adjust the detection logic to non-standard data schemas for automated and customized deployments.
Download the dedicated guide for the latest version of the CCM API Integration Tool to be all set for leveraging the automated content deployment capabilities.
Crowdsourced detection content fuels multiple SIEM, EDR, and XDR solutions with more opportunities to keep updated on emerging cyber threats, taking global industry collaboration to the next level. Subscribe to SOC Prime’s platform to adopt your security strategy to the collaborative cyber defense approach and future-proof detection and hunting capabilities. By joining the ranks of SOC Prime’s crowdsourced initiative, the Threat Bounty Program, individual cybersecurity researchers and SOC content authors can submit their own high-quality detection algorithms and make a notable contribution to the collective pool of knowledge connecting over 23,000+ industry experts worldwide.


