To keep your SIEM constantly updated with the cutting-edge compatible SOC content and skyrocket your threat detection speed, the SOC Prime Team is continuously advancing the Continuous Content Management (CCM) module for Threat Detection Marketplace. The latest platform releases (4.11.0 – 4.14.0) introduce a list of major enhancements to the CCM functionality that ensures smooth and streamlined content streaming directly into your security tools in use. Particularly, the updates bring in important content list improvements, expand the list of available rule presets, promote Custom Field Mapping functions, and provide prominent platform experience improvements alongside bug fixes.
Content Lists Improvements
With the latest Threat Detection Marketplace updates, we’ve introduced major enhancements to the content list functionality of the Continuous Content Management (CCM) module.
All List Types
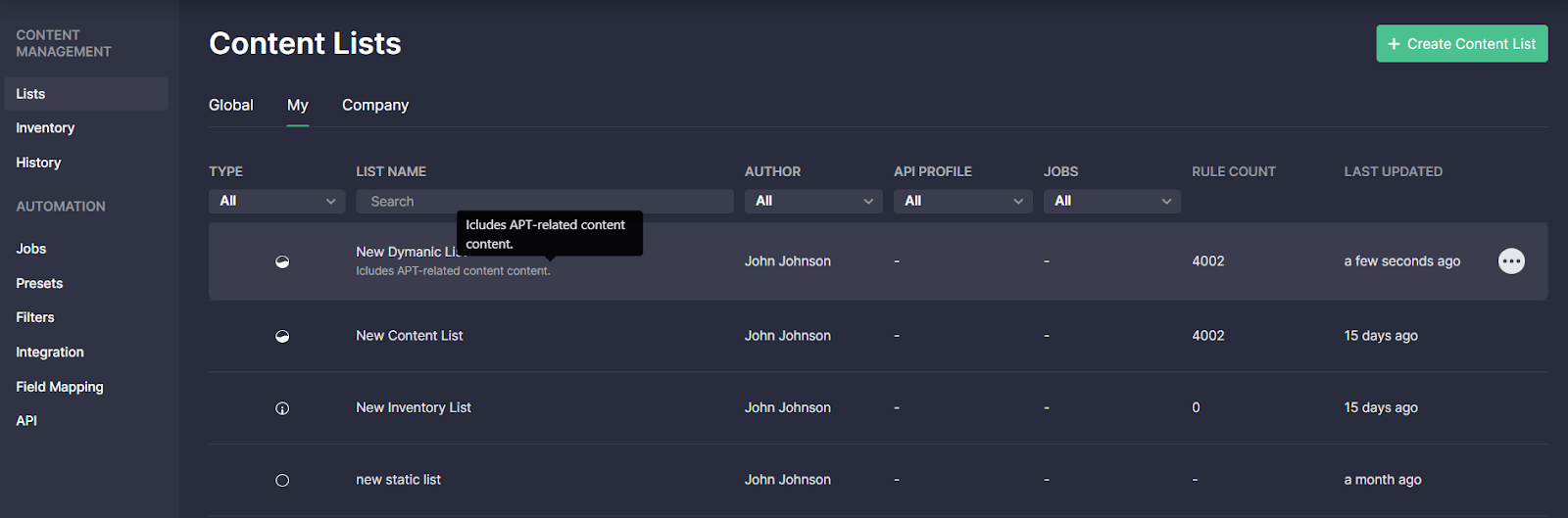
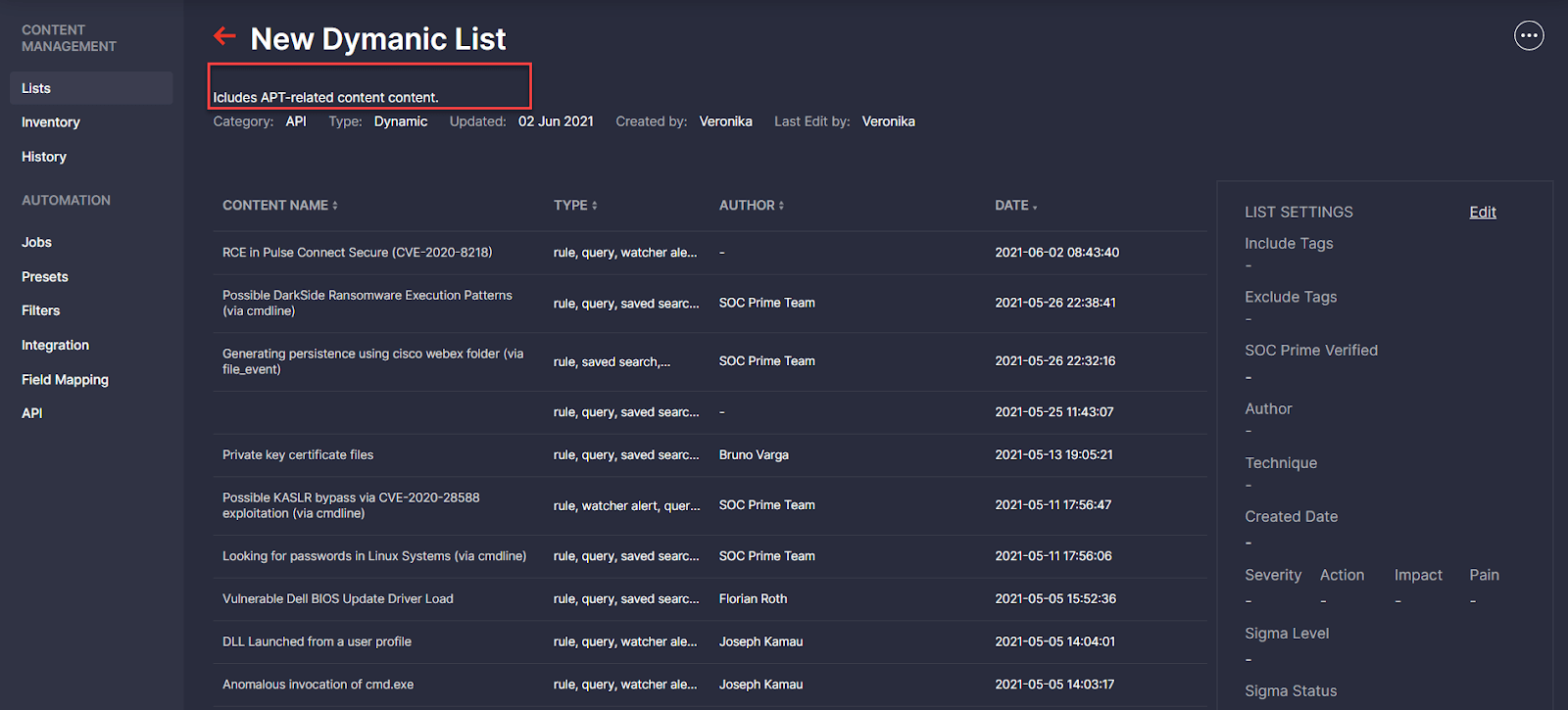
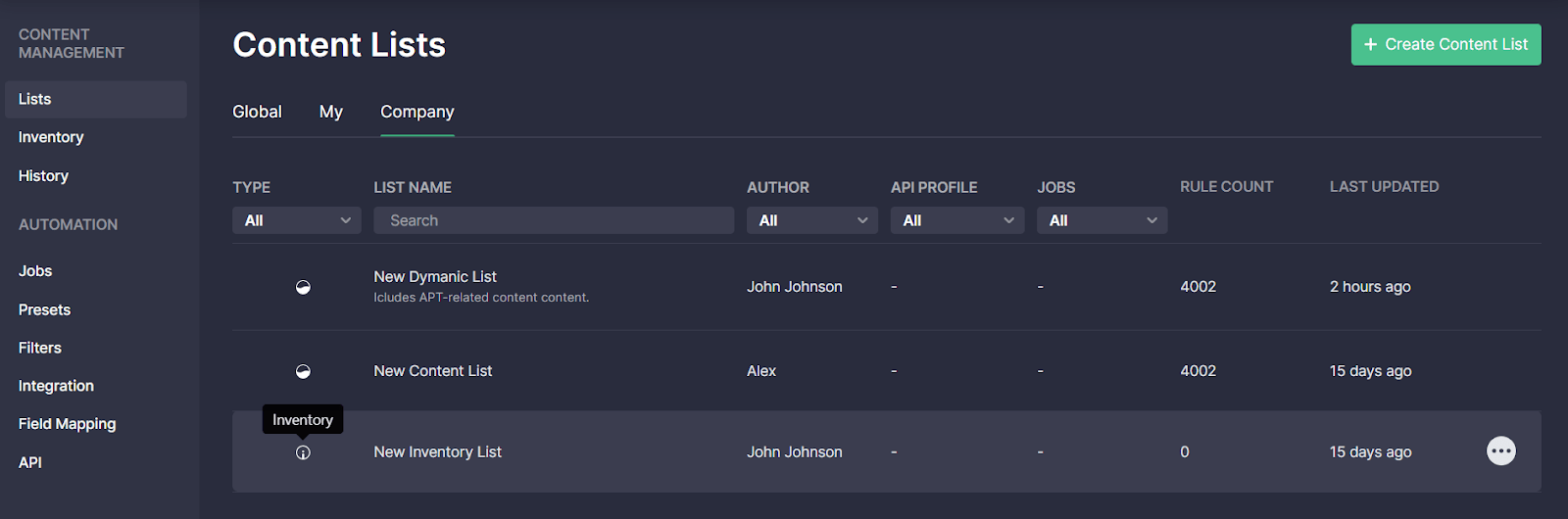
Threat Detection Marketplace version 4.11.0 brought in major enhancements for all content list types. Specifically, we’ve added a description field that can be filled in when creating a new list to highlight the list value and help make it stand out from other items. The created list description will then be visible on the Content Lists page under the corresponding list name. If the description is quite detailed, it will be partly visible under the List Name column to save the page space, and the tooltip will display the full text when hovering over the description.
When drilling down to the details of the selected list, its description now appears just below the list name:
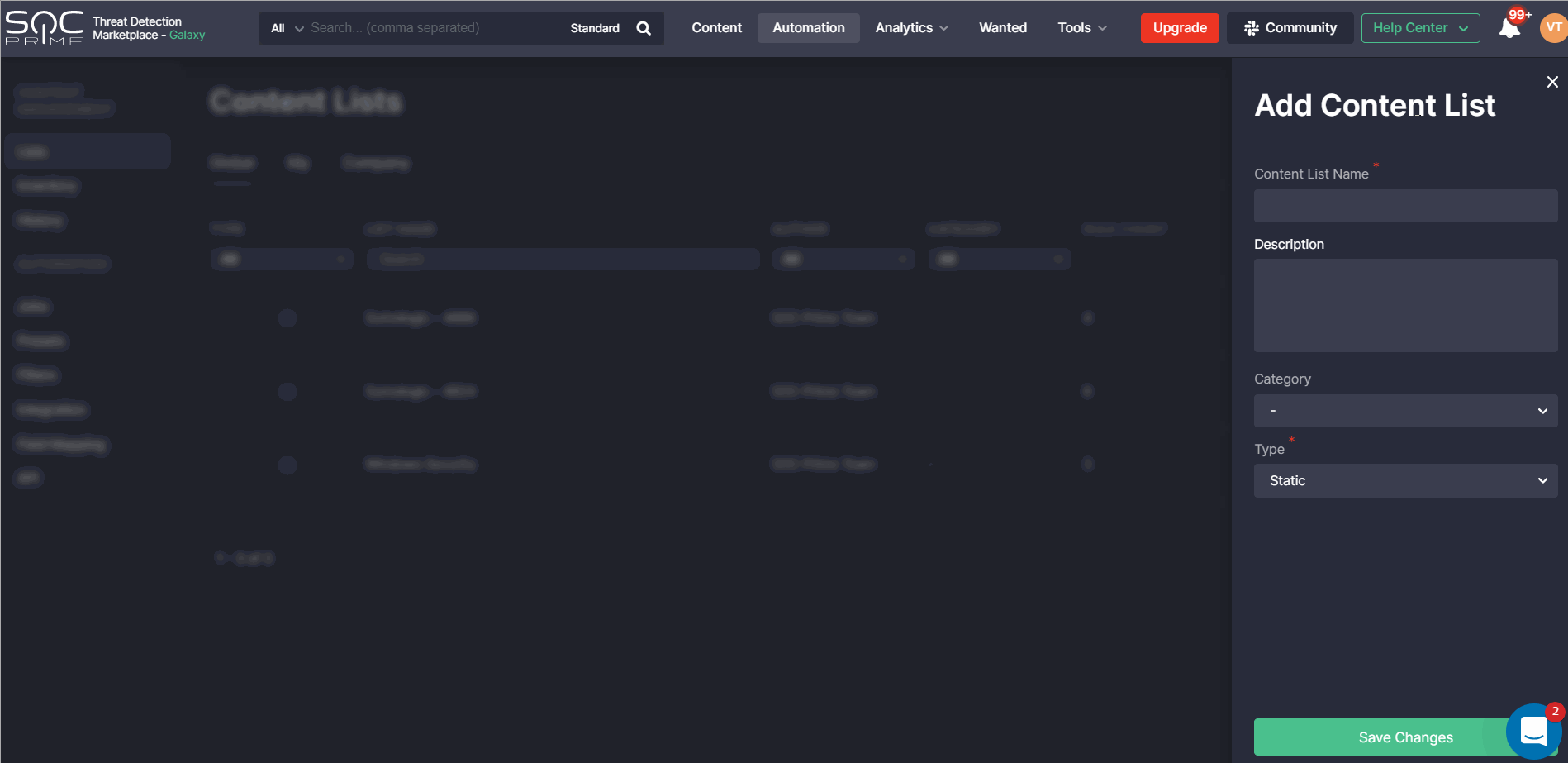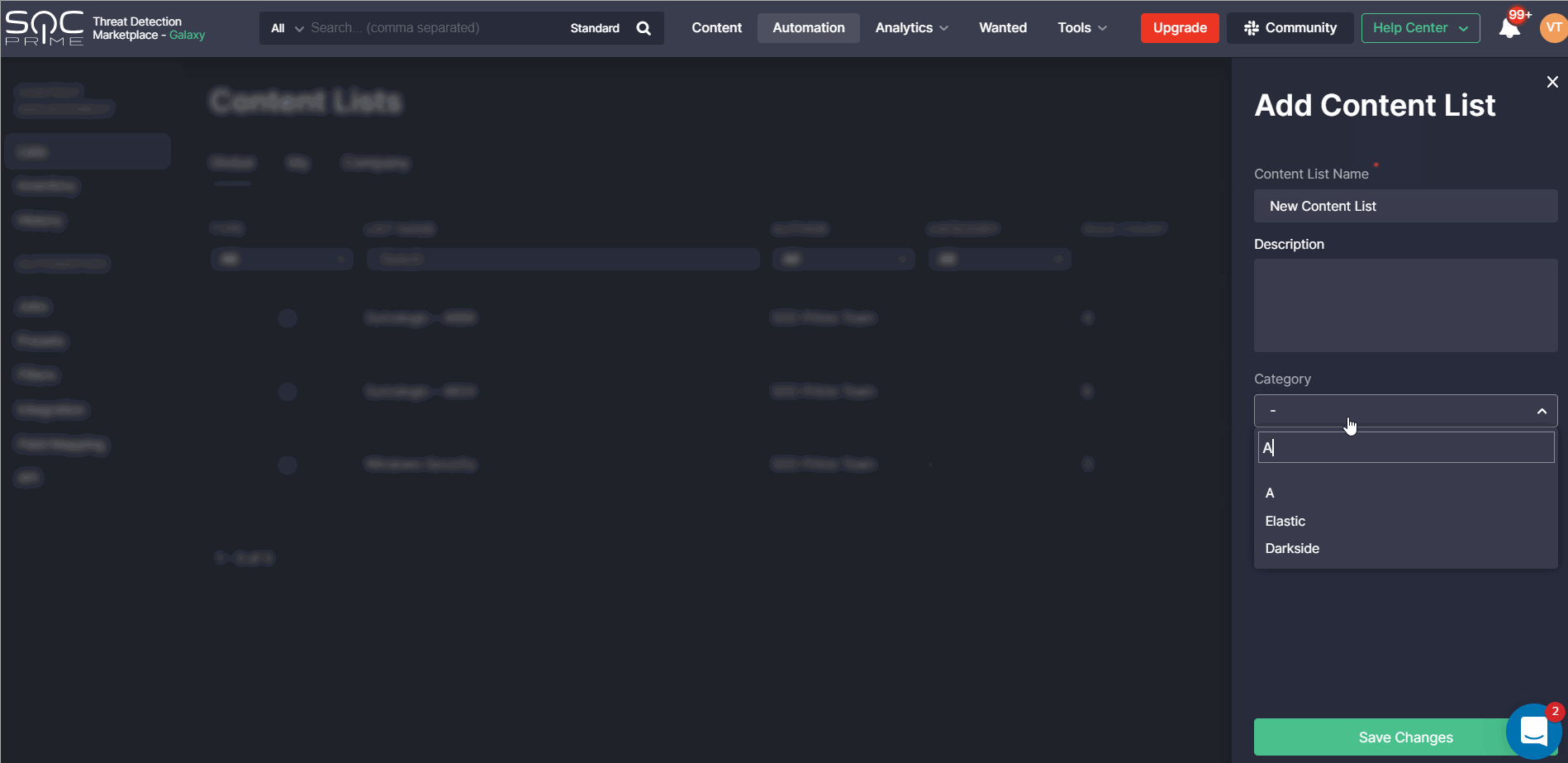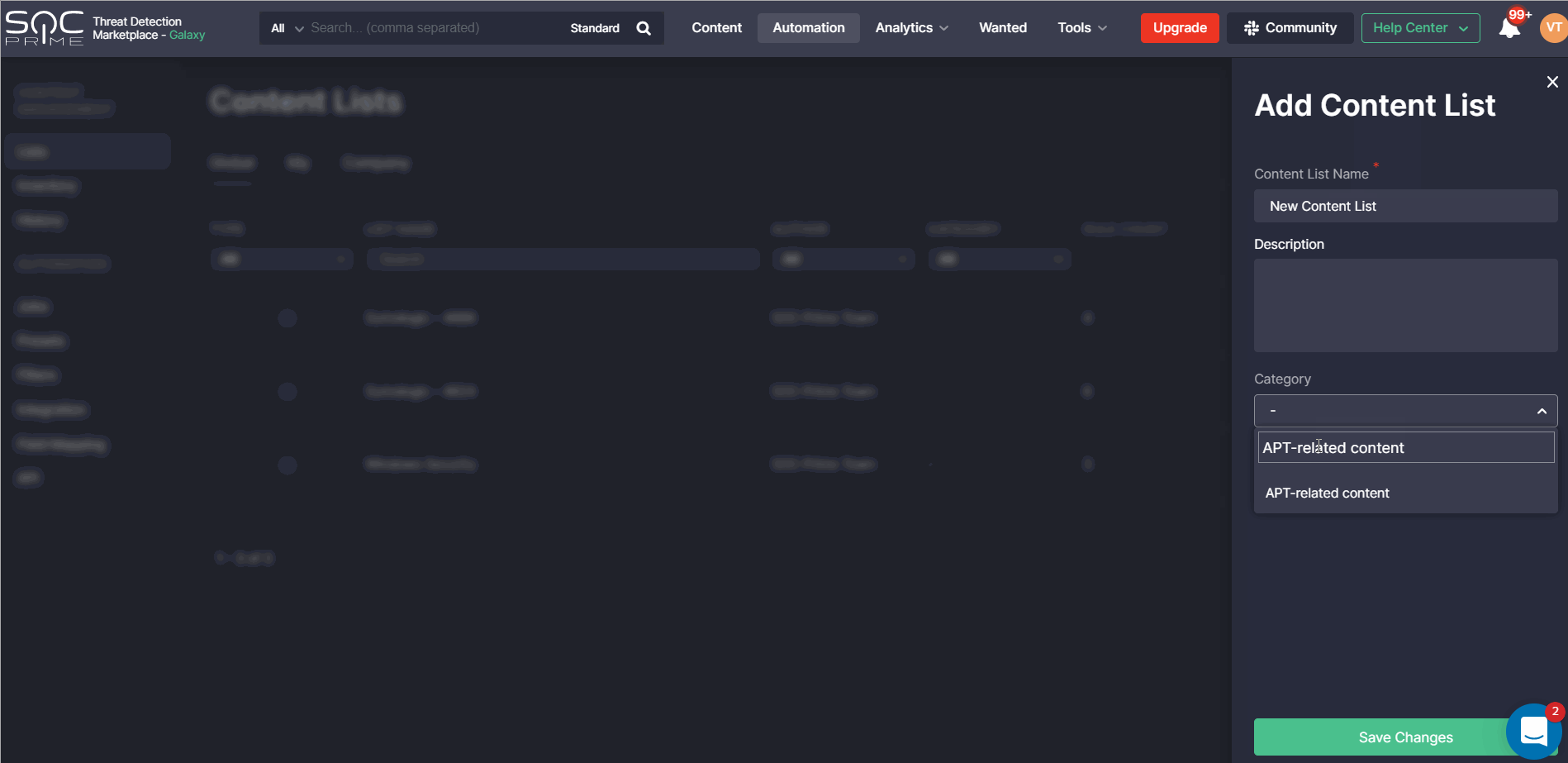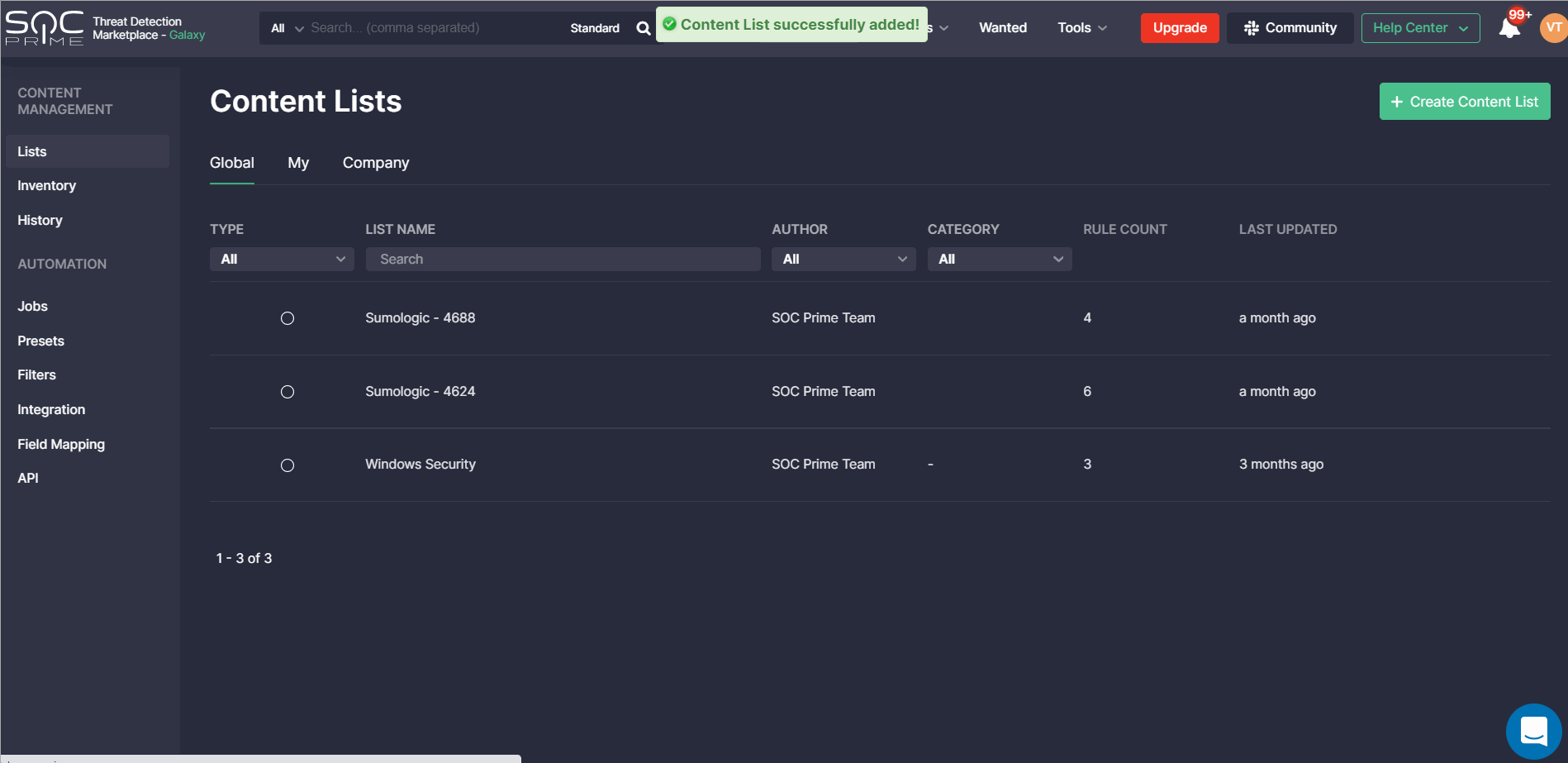
Also, we’ve added the ability to categorize the list by selecting one of the available category options in the corresponding drop-down list or creating a new custom category and applying it on the fly.
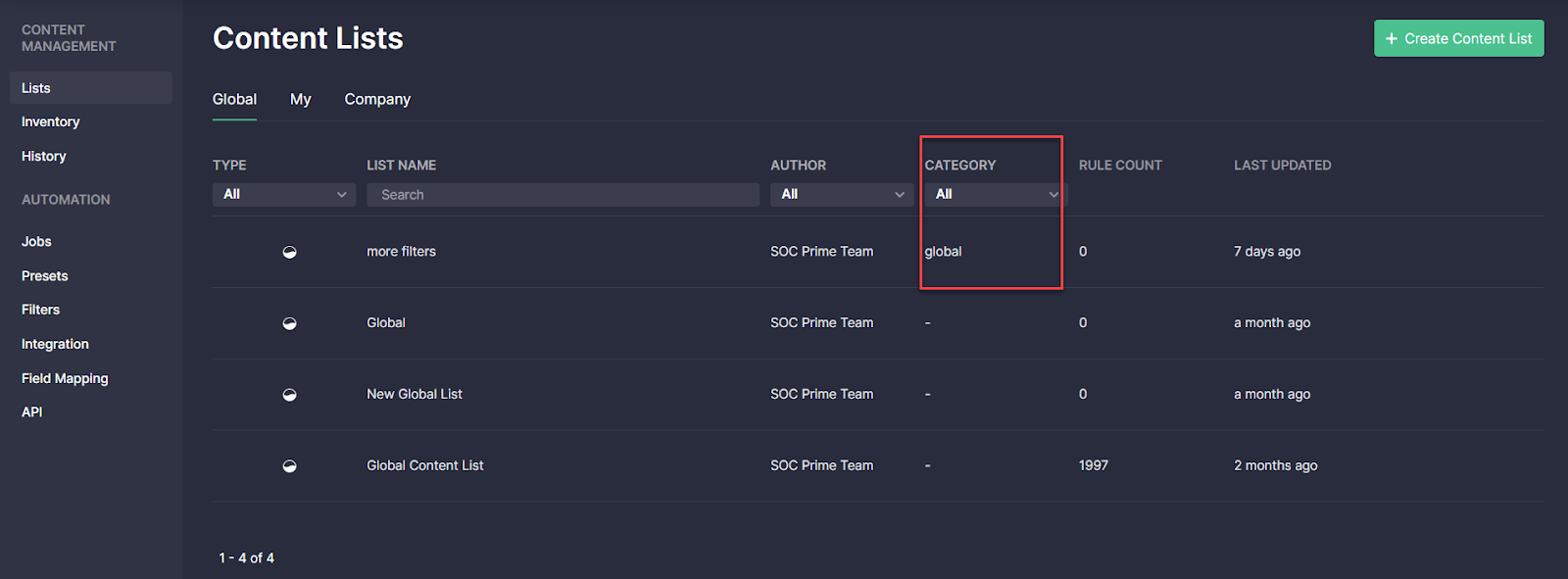
On the Global tab, the applied category now appears under the corresponding Category column.
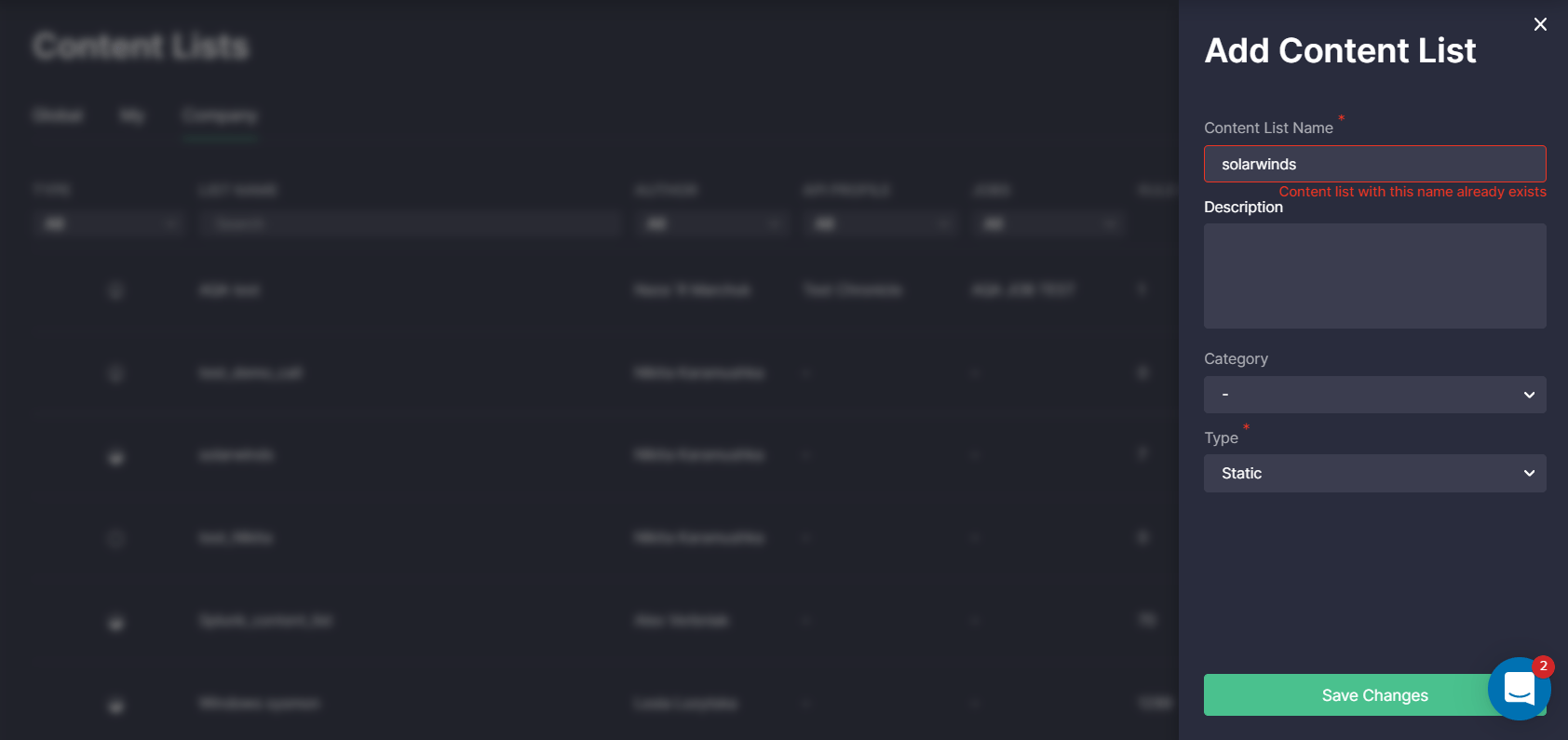
Moreover, we’ve added restrictions to the content list names that must be unique across one and the same company. This update adds to an improved company-wide content management and encourages security performers to provide meaningful and unique names to the content lists that will help identify these lists among the plethora of similar data. From now on, content lists cannot be saved if items with the same name already exist within this organization.
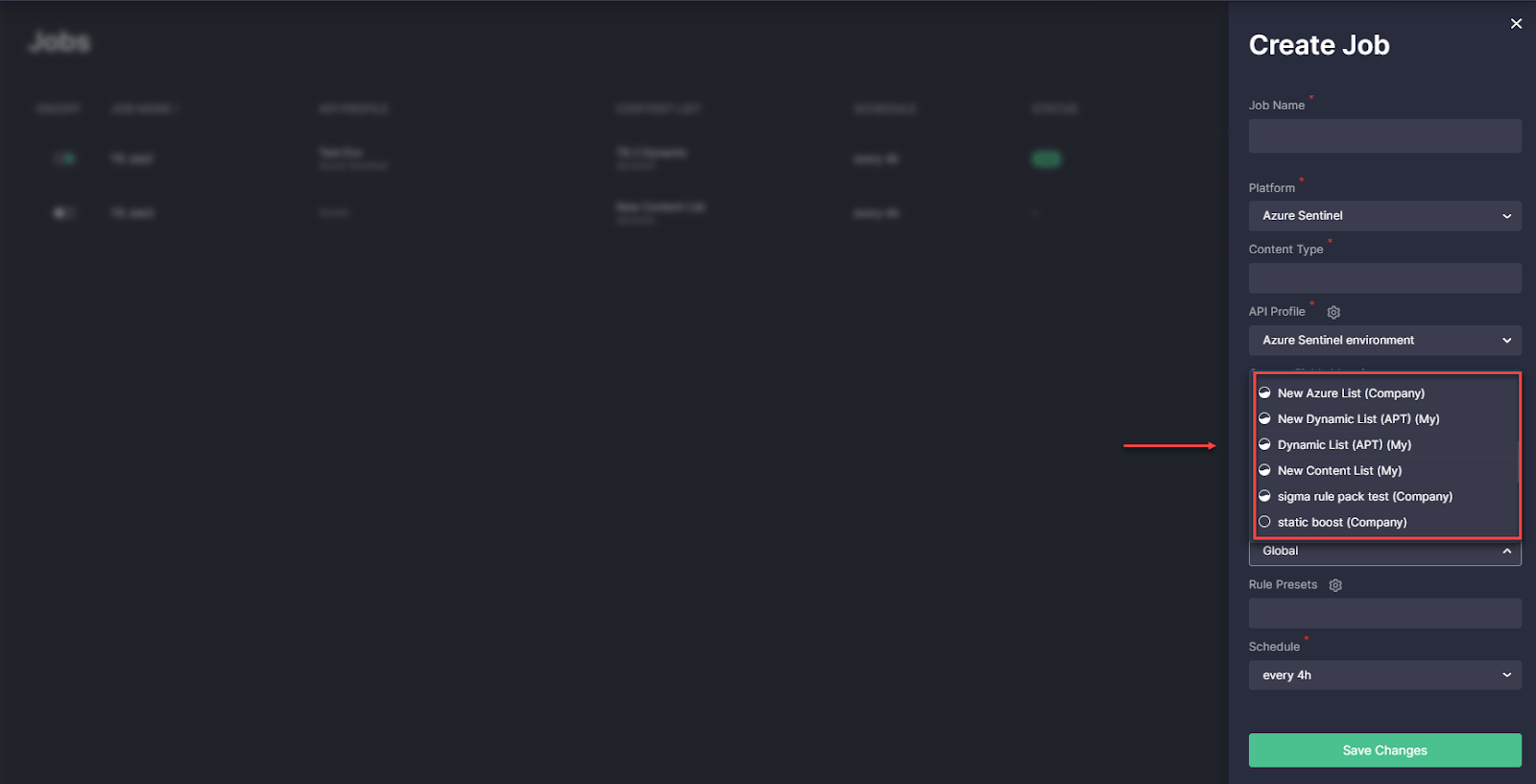
Finally, for a more intuitive user experience, we’ve added tooltips to the content list type icons that identify dynamic, static, and inventory lists.
Dynamic Lists
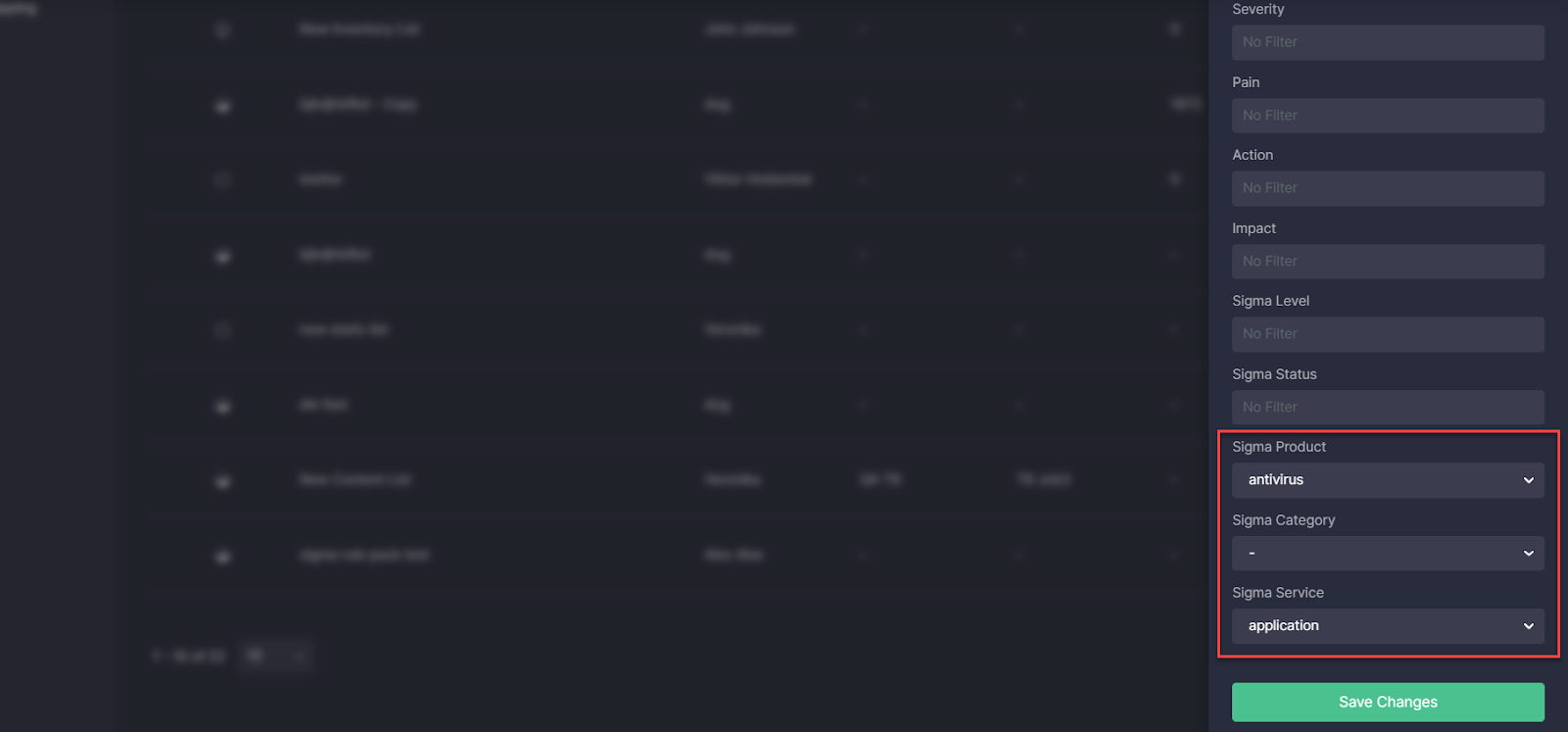
Threat Detection Marketplace 4.11.0 update also introduces important changes to the dynamic lists functionality. With this update, we’ve expanded the list of filters available for dynamic content lists with three new options based on the corresponding fields:
- Sigma Product — tags.product
- Sigma Category — tags.category
- Sigma Service — tags.service
Security performers can now create new dynamic lists based on these filters, as well as run jobs to pull the content filtered accordingly and stream it right into the customers’ environment.
In addition, with Threat Detection Marketplace release 4.14.0, we’ve proceeded with the prominent updates and made the API capabilities processing dynamic content lists consistent with the entire CCM module functionality. Since the dynamic content list cannot contain over 200 detections, the same restrictions have been added to the API functionality. Security performers can now download a maximum of 200 content items from each dynamic list via API. The sorting conditions that select these 200 most relevant content items remain unchanged.
Global Lists
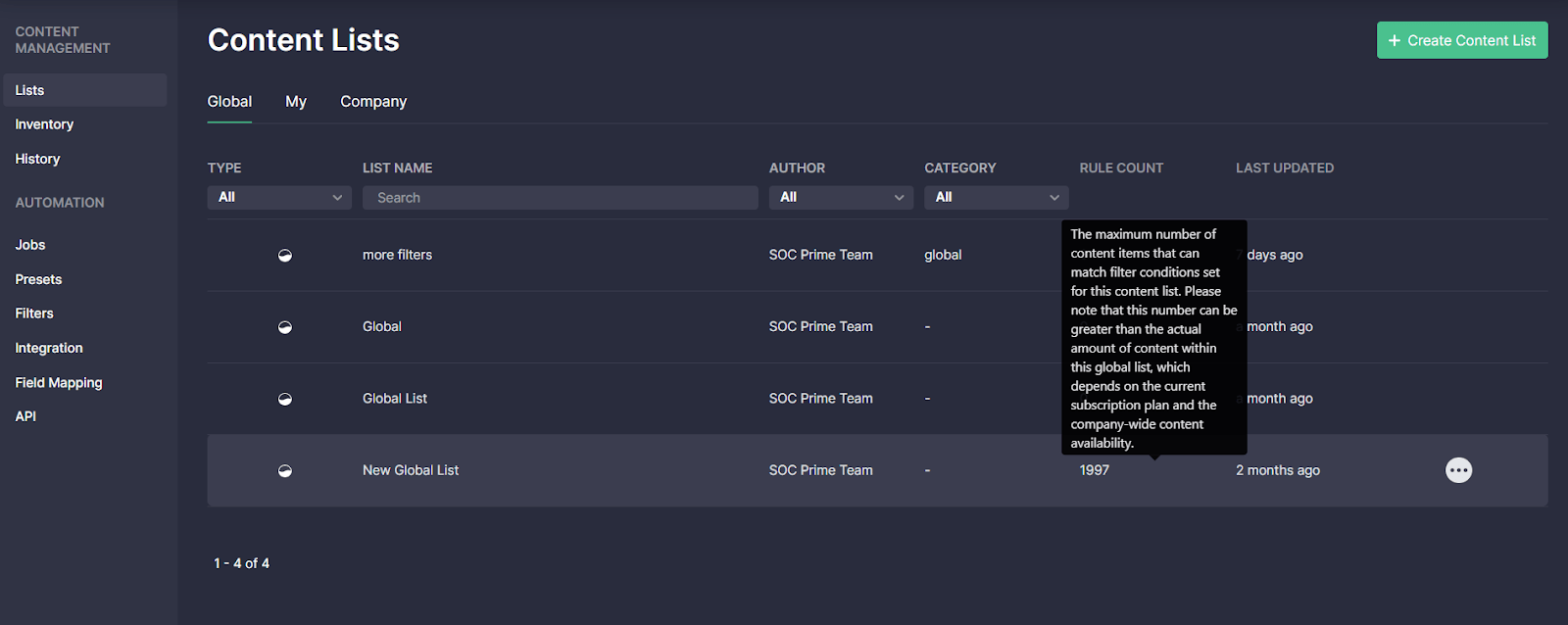
Threat Detection Marketplace release 4.11.0 contributes a lot to the global list features. Particularly, with this release, we’ve added the tooltip on the Global tab explaining the content amount displayed under the Rule Count column. This tooltip appears when hovering over the specific number under the Rule Count column related to the corresponding global list. The added tooltip helps security performers understand the possible difference between the rule count value, which is the maximum number of content items matching filter conditions set for this content list, and the actual amount of content within the corresponding list.
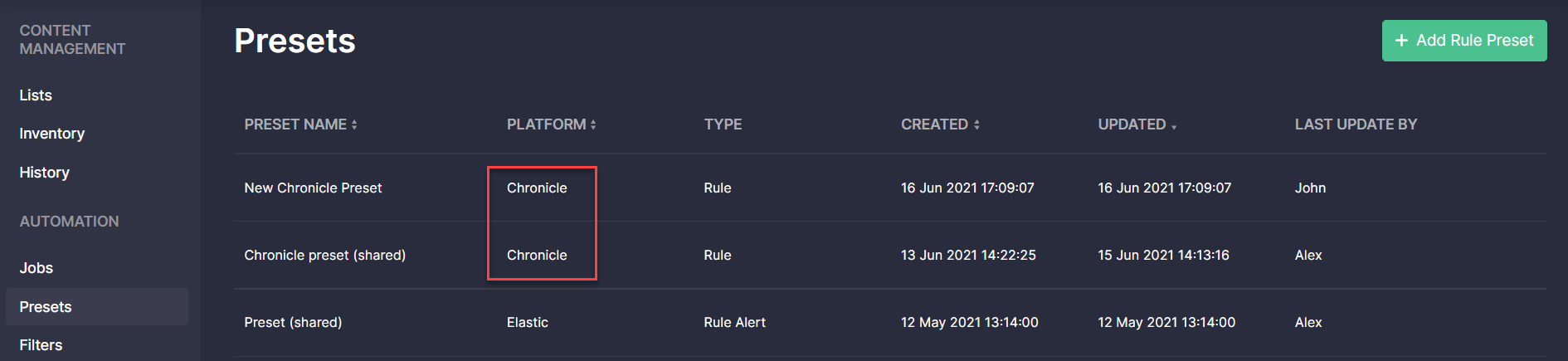
New Presets for Google Chronicle & Splunk Alerts
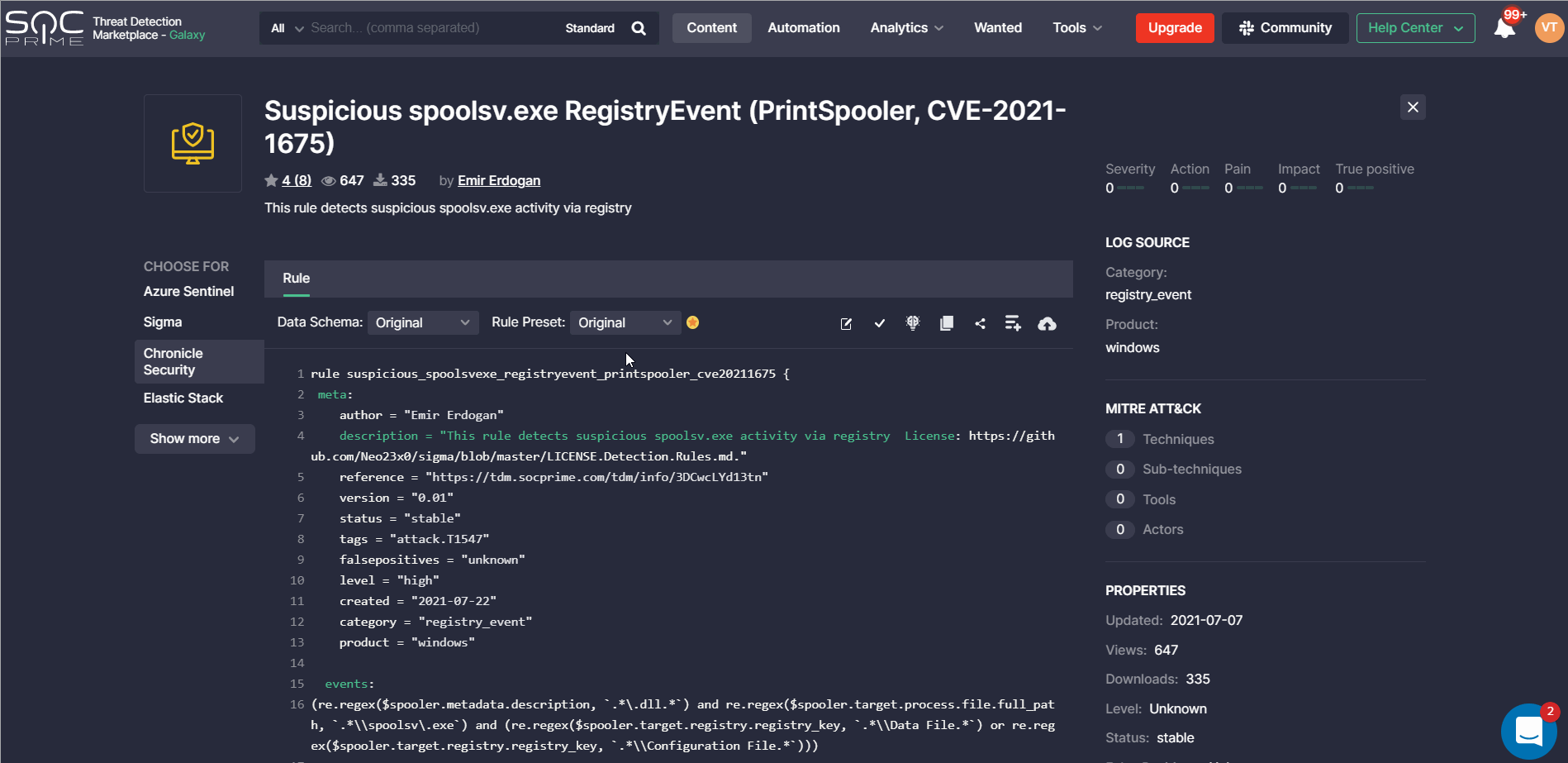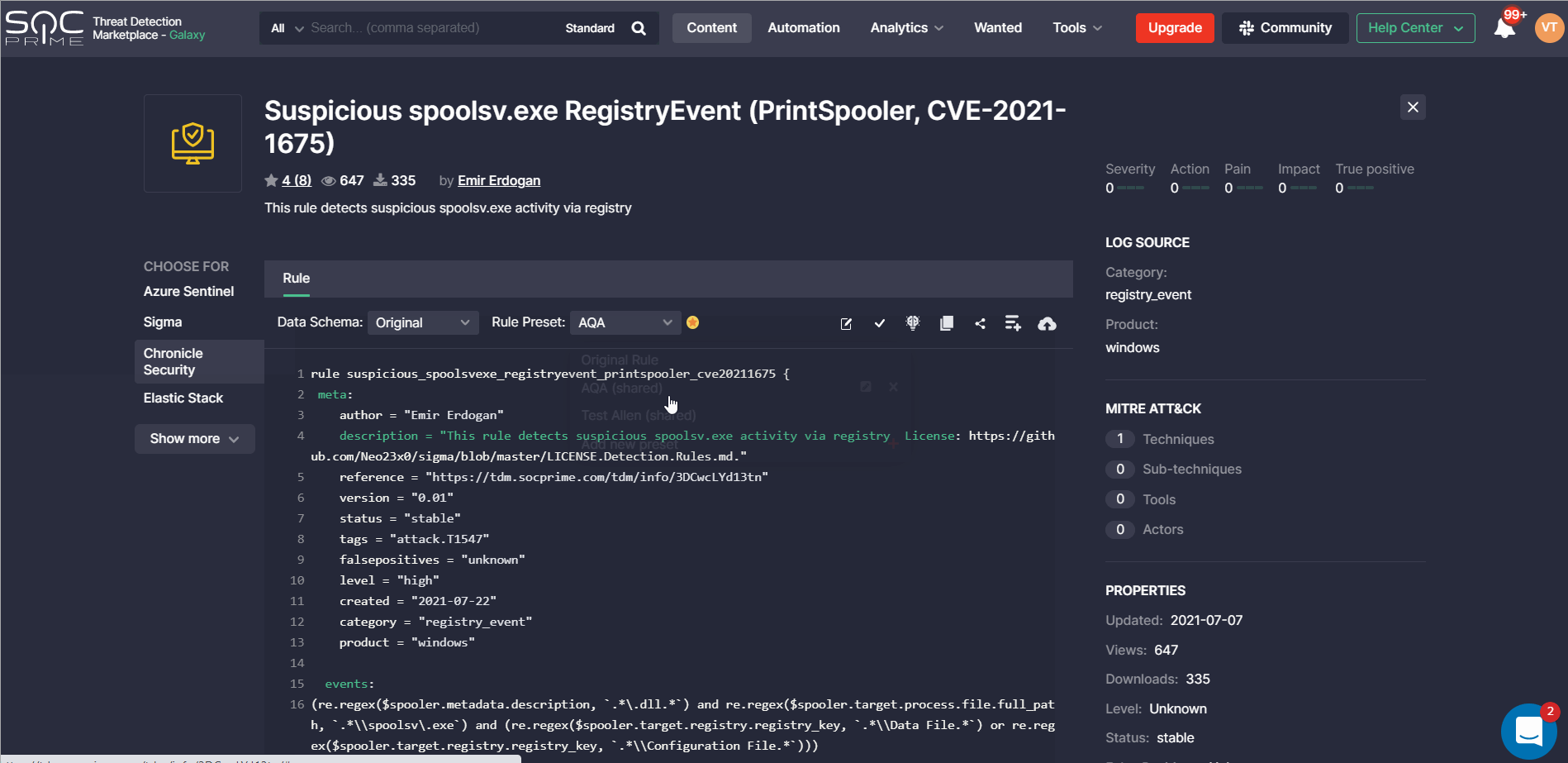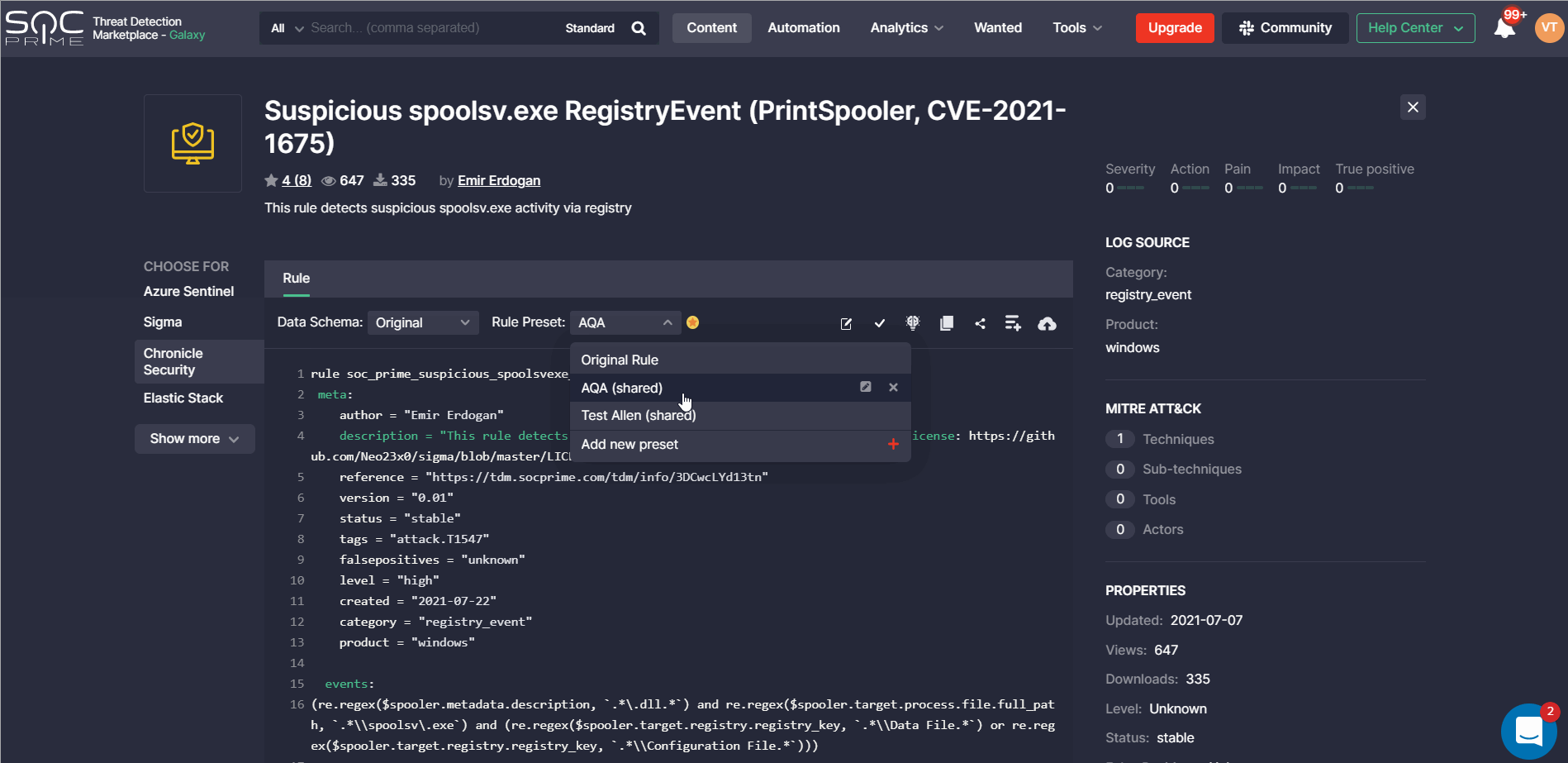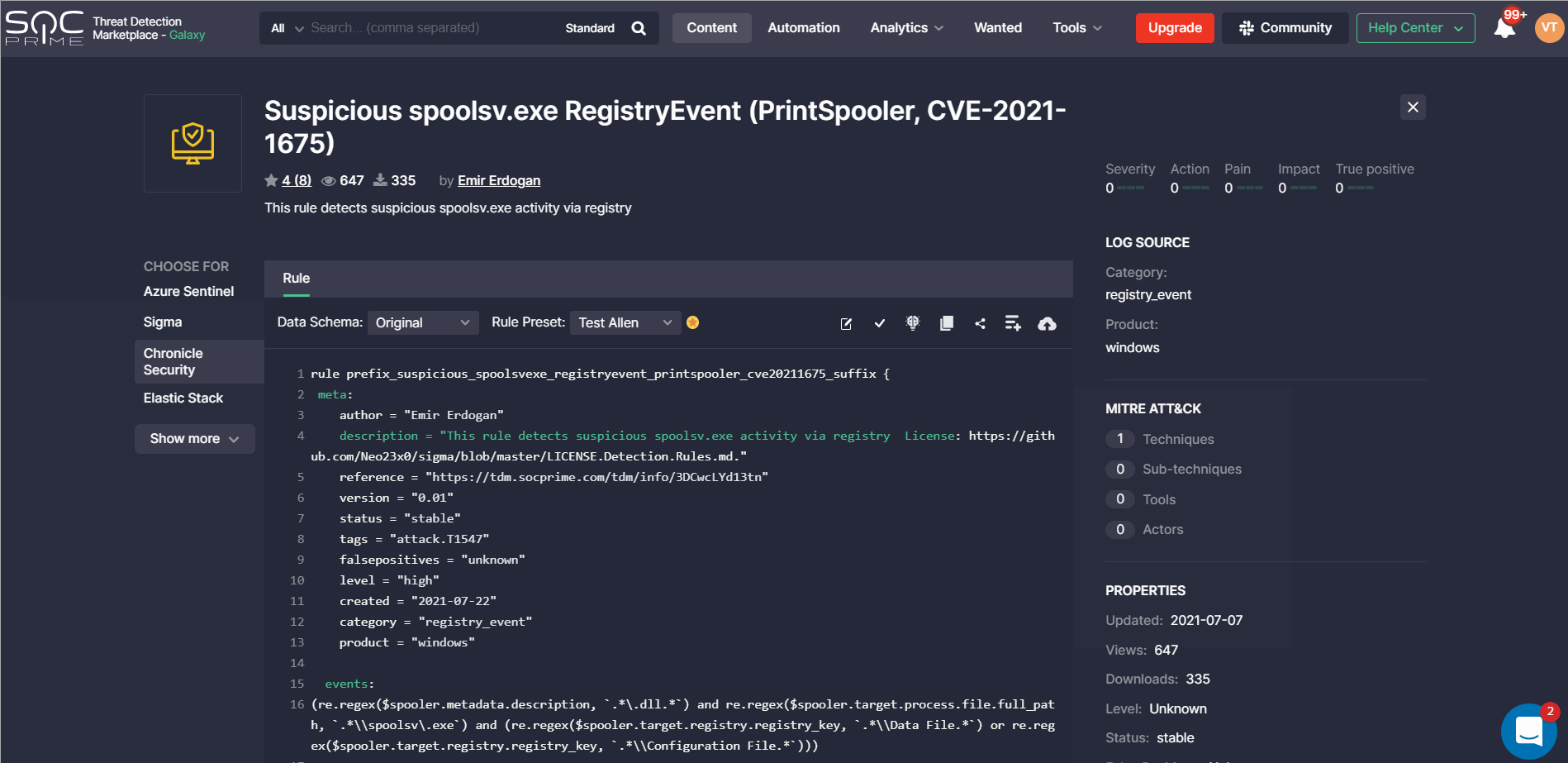
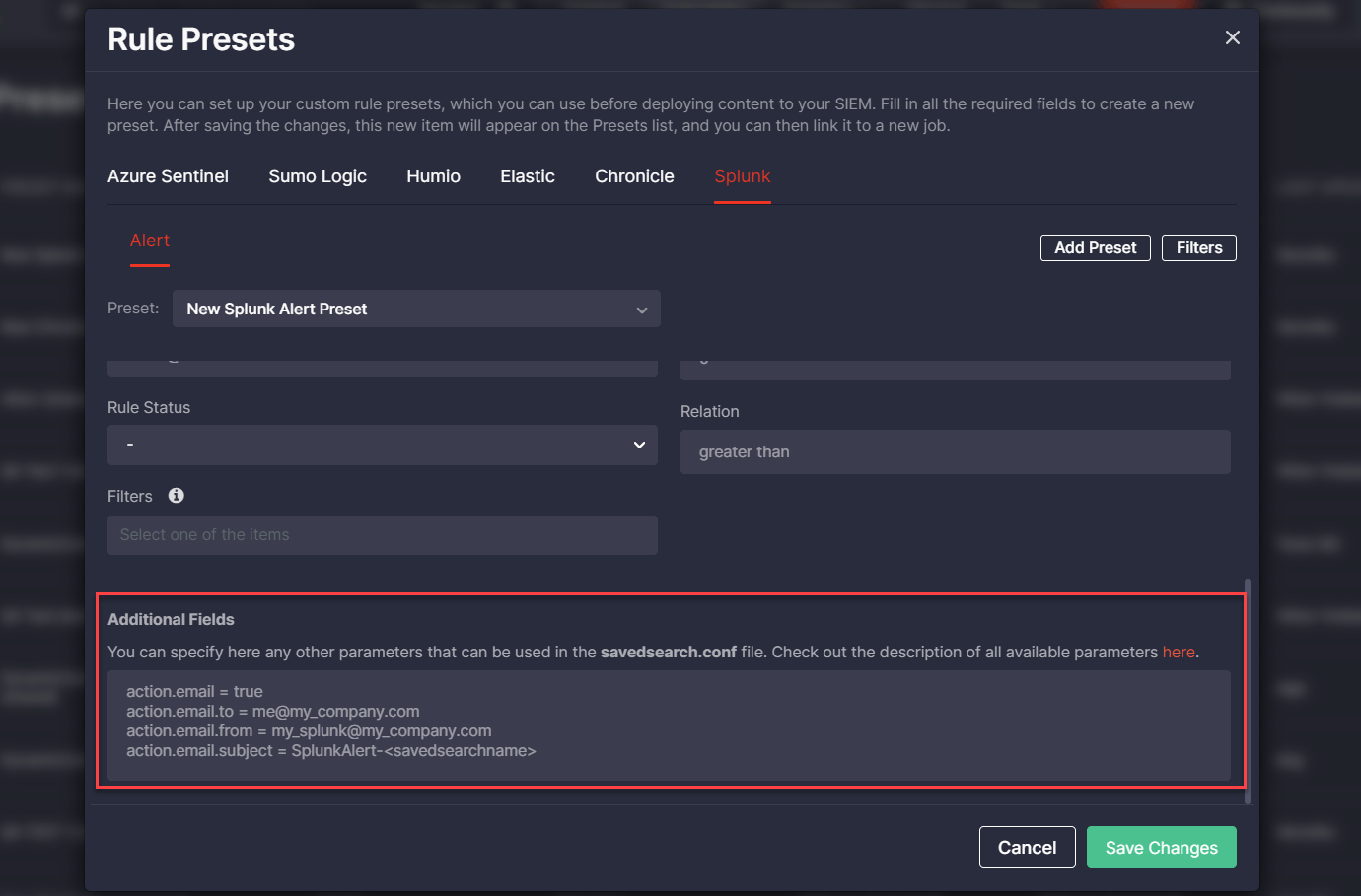
With Threat Detection Marketplace releases 4.12.0-4.13.0, we’ve introduced the ability to create and apply rule presets for the Google Chronicle language format and the Splunk Alert content type. The list of created options is available on the Presets page and now it is also enriched with the Chronicle and Splunk Alert possibilities. CCM users can edit or delete the existing presets, or create a new one by clicking the Add Rule Preset button.
Similarly to other platforms, the newly created preset needs filling in certain fields determined by the platform configuration and can also include filters to make the content search more specific.
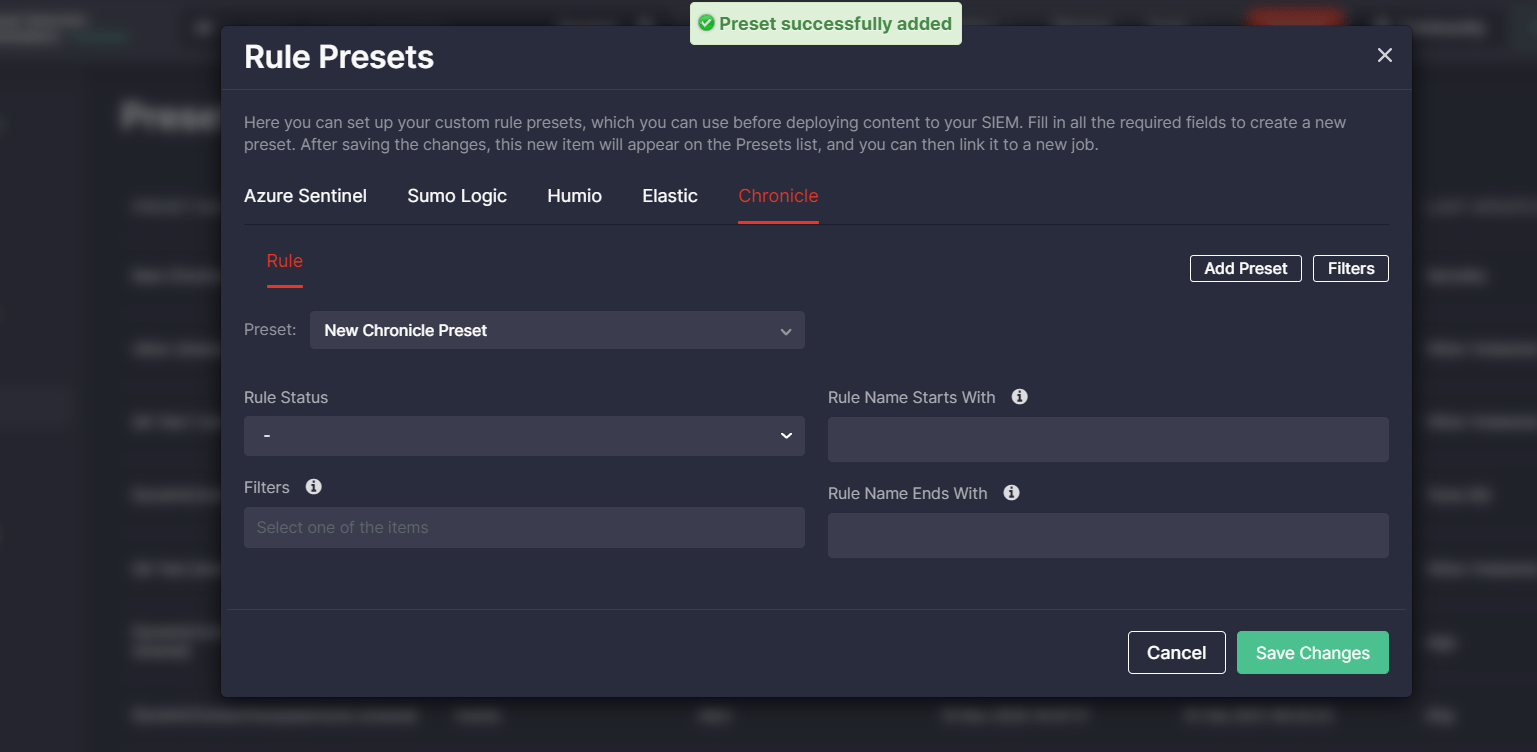
Security performers can also indicate the specific parameters other than the standard fields used for the Splunk Alert configuration in the Additional Fields block using the syntax template.
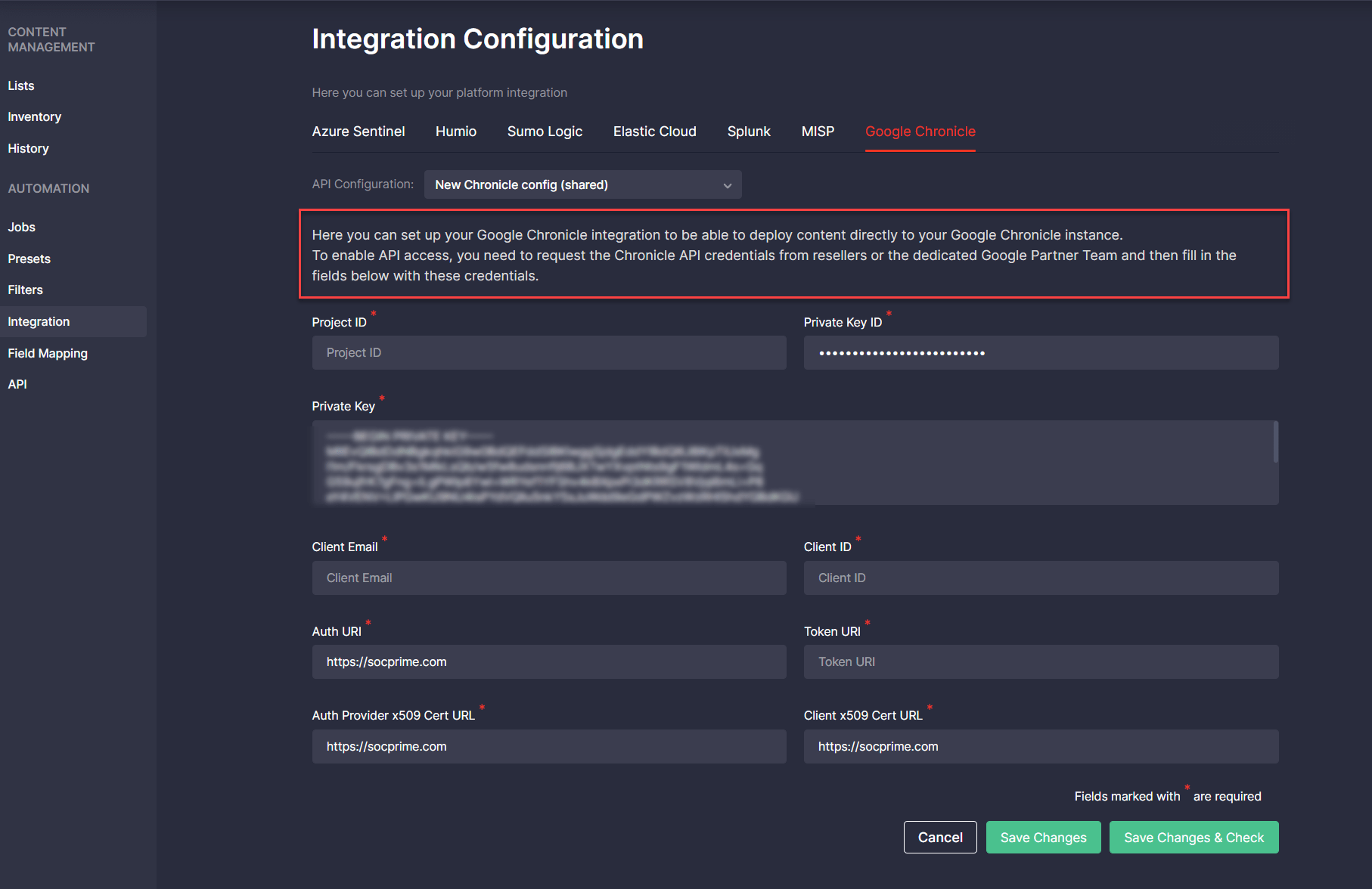
Google Chronicle Integration Updates
To ensure the most intuitive experience for Google Chronicle customers, with Threat Detection Marketplace release 4.13.0, we’ve updated localizations on the Integration Configuration page for this security solution. To stream Google Chronicle content right into the customer’s environment, security performers now will need to request the Chronicle API credentials from resellers or the dedicated Google Partner Team and then fill in the fields on the Integration Configuration page with the acquired credentials.
Custom Field Mapping Updates
With the latest platform updates, we’ve broadened the support for more Elastic Stack content types available for the Custom Field Mapping configuration and added the support for Securonix next-gen SIEM.
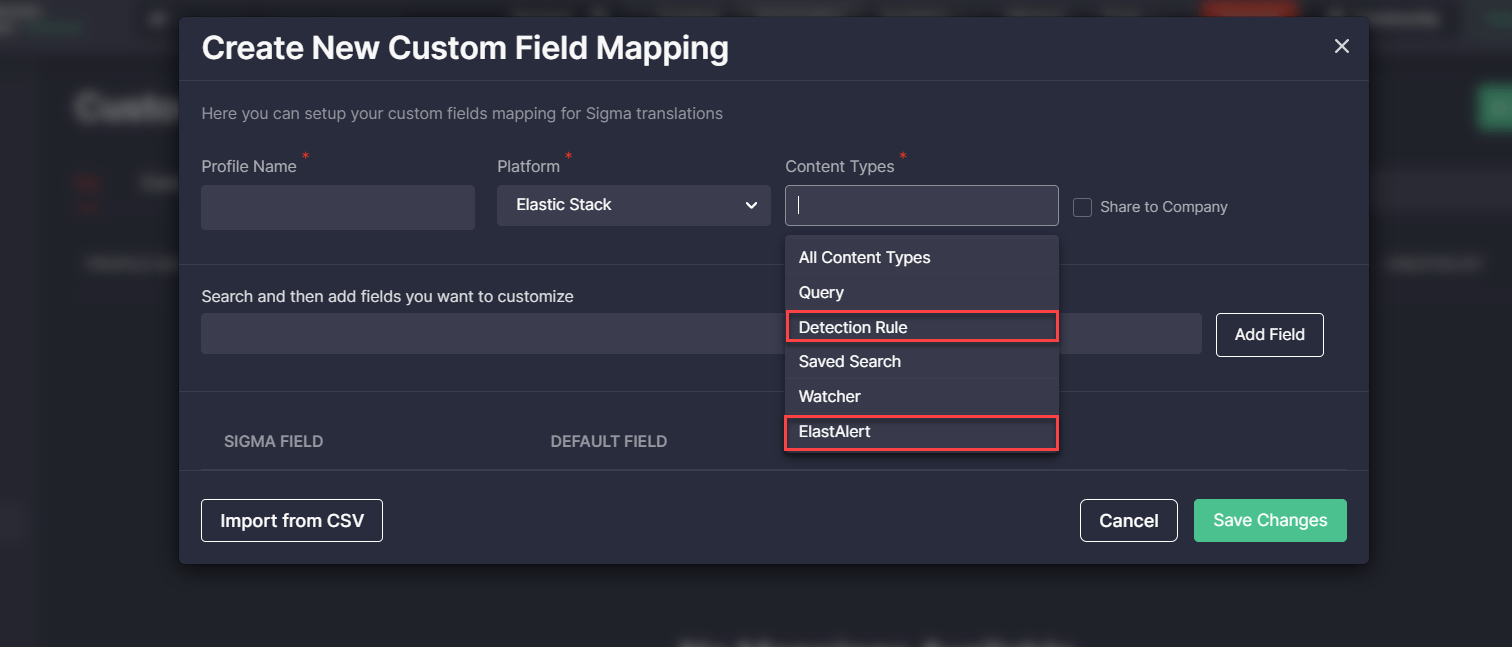
Elastic Detection Rules and ElastAlert Support
With Threat Detection Marketplace release 4.13.0, Custom Field Mapping profiles can now be configured for the following Elastic content types:
- Detection Rule
- ElastAlert
Security performers can now build field mapping profiles for these language formats using the Custom Field Mapping tool from the Automation page or the user settings menu.
Alternatively, the data schema profile for Detection Rules and the ElastAlert content can be configured right from the rule page. To deliver a consistent user experience, we have also updated localizations for the Data Schema drop-down list by introducing the updated “Add New Field Mapping” option as part of these improvements.
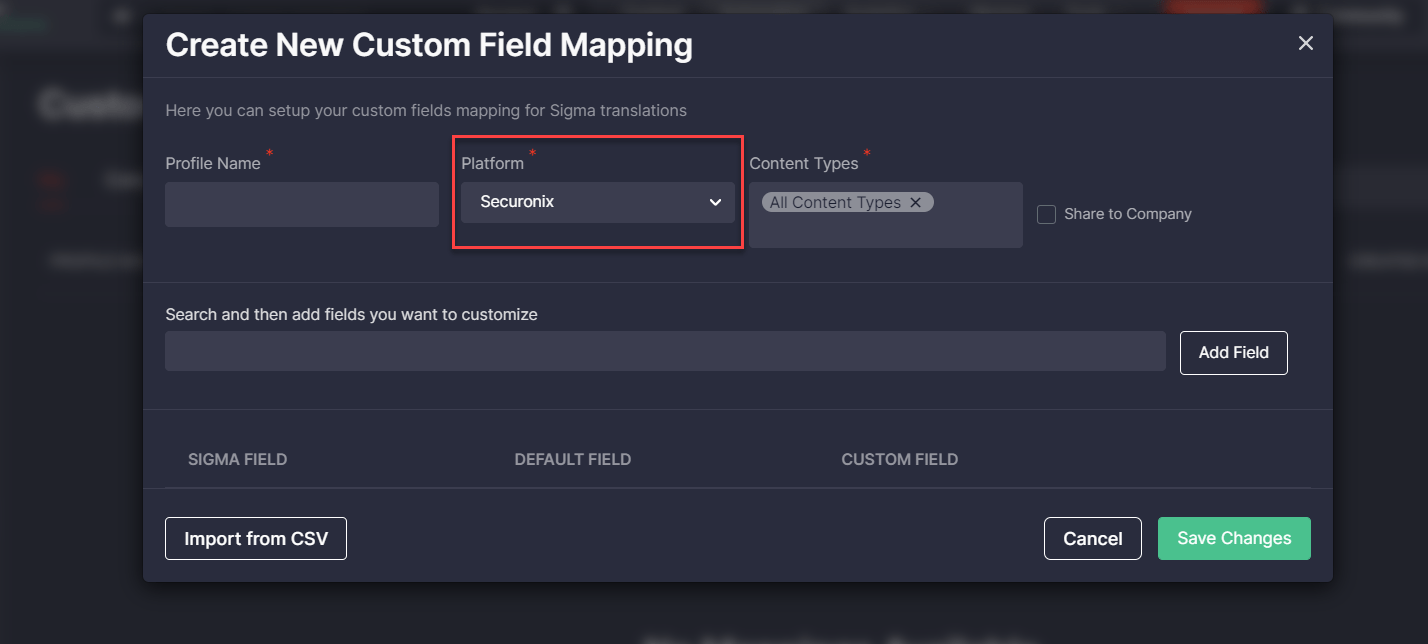
Custom Field Mapping Support for Securonix
To ensure the most streamlined threat detection experience for our customers leveraging the Securonix next-gen SIEM, with the release of Threat Detection Marketplace version 4.14.0, we’ve also added the Custom Field Mapping support for this security solution. Security performers can now change the default field names to the custom ones they prefer and enable on-the-fly conversions to the Securonix format without any parsing problems.
Key User Experience Improvements & Bug Fixes
With the latest releases, we’ve introduced the corresponding updates to the CCM module for a better user experience:
On the Create Job pop-up:
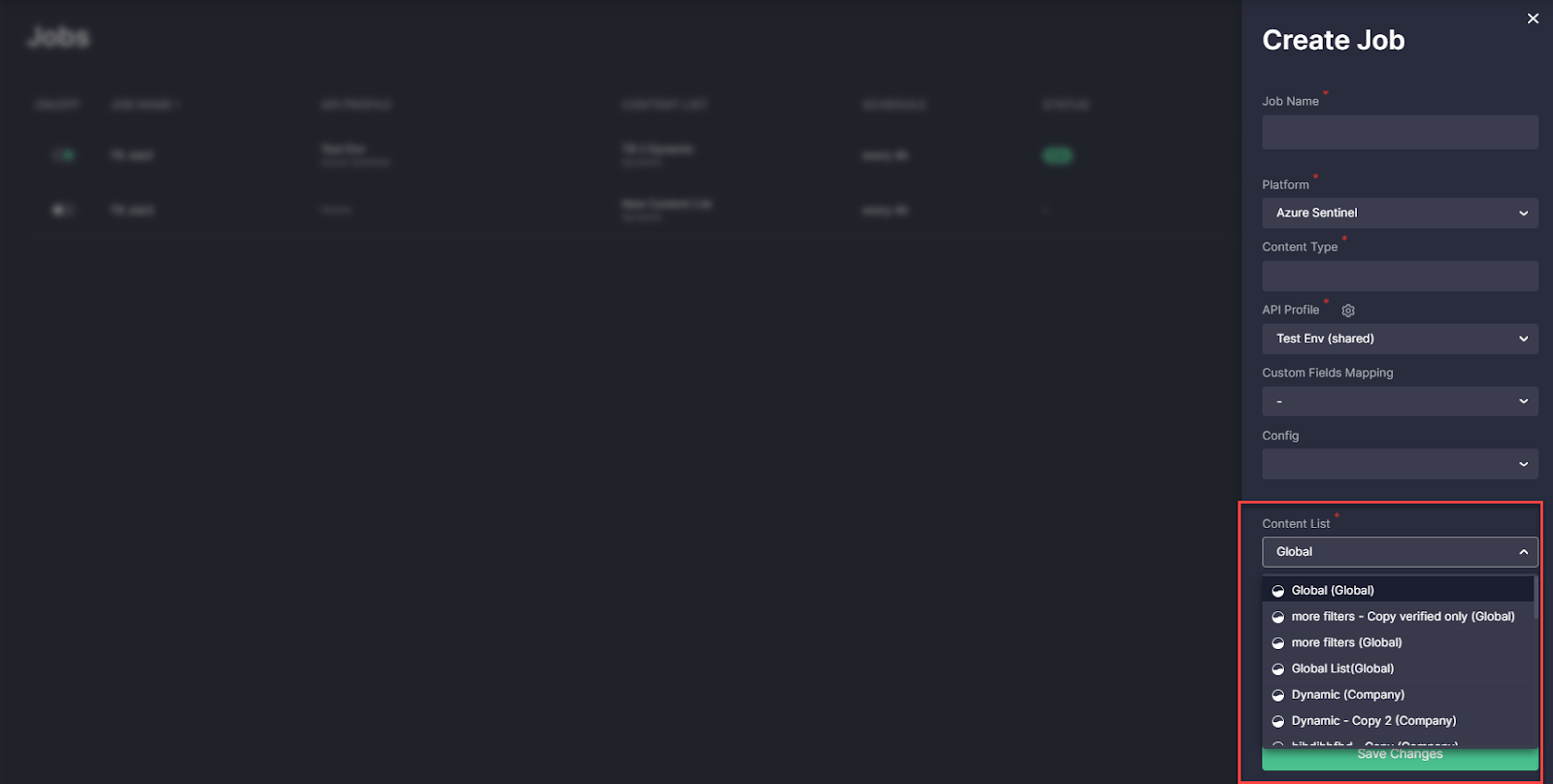
- Added icons to the Content List drop-down list that help identify the list type. For an even more intuitive user experience, security performers can now see whether the list is private, shared among the company, or a global one.
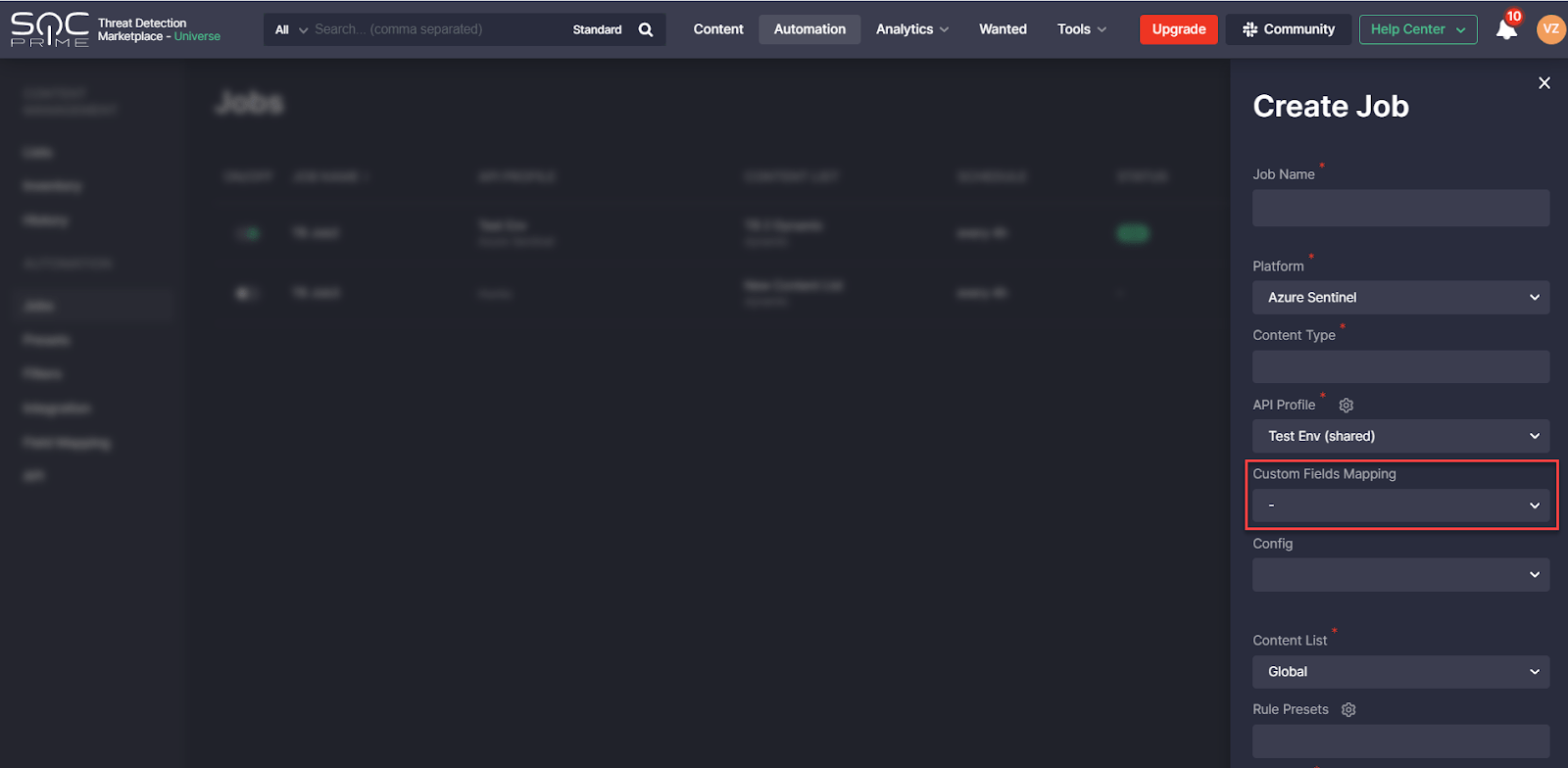
- Enabled creating jobs without selecting any Custom Field Mapping profile. Before this release, jobs couldn’t deploy content without the Custom Field Mapping profile, and the default profile was applied automatically if the CCM users hadn’t selected anything specific.
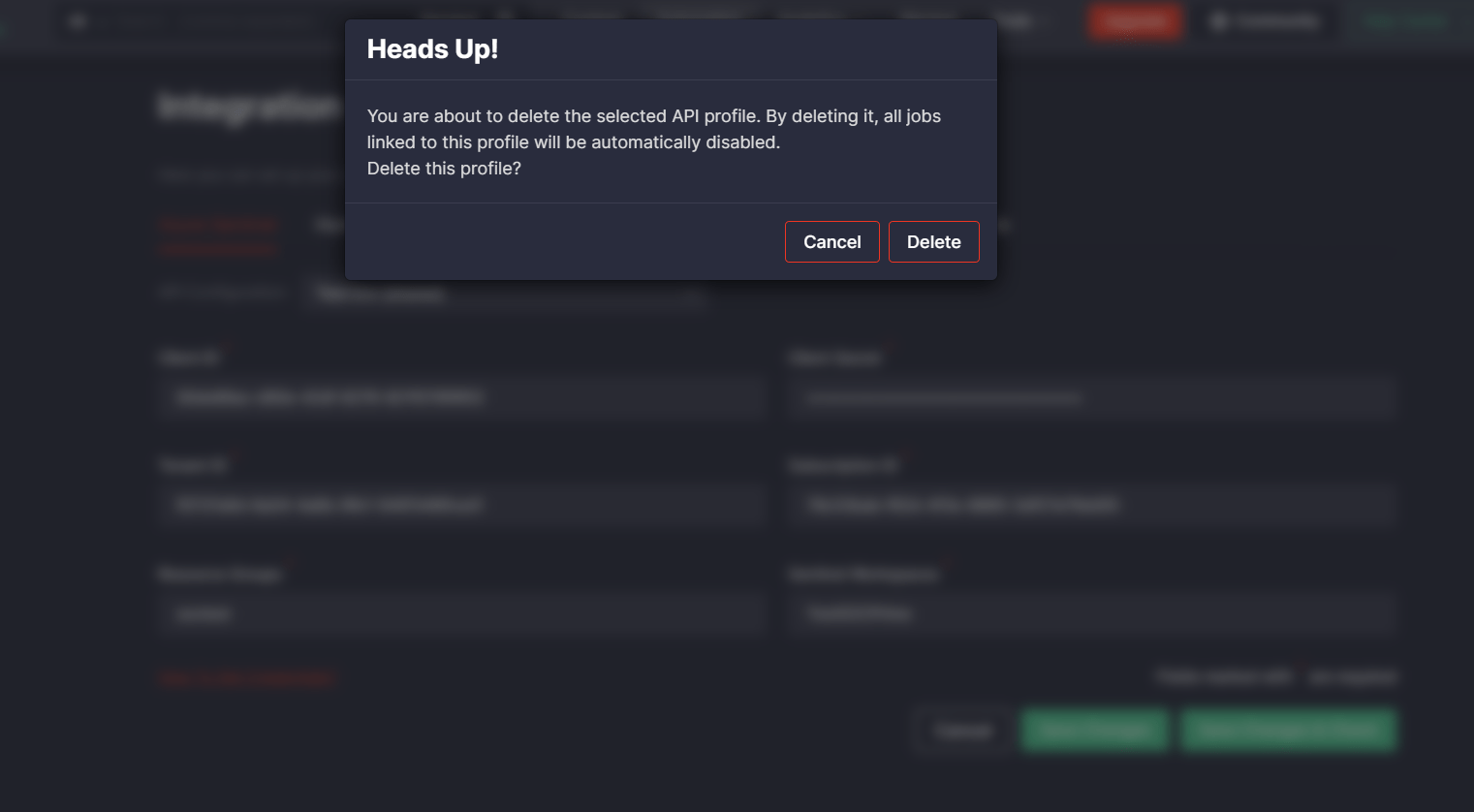
Added the ability to notify CCM users when they try to delete a certain API profile that has active jobs linked to it. For a better user experience, security performers will be notified by the system that deleting this profile will automatically disable all jobs linked to it.
Also, with the latest releases we’ve fixed a number of minor bugs to ensure the best platform experience for our customers:
- Fixed the issue with redundant integration settings for Elastic Cloud when trying to deploy Detection Rules or Saved Search. Before this update, users who had already set up their Kibana integration, saw the pop-up that prompted them to configure access to the Elasticsearch API when they tried to deploy either Detection Rules or Saved Search content. This step seemed confusing since enabling access to the Elasticsearch API was required only for Watcher deployment and wasn’t needed for other Elastic types of content supported by CCM. With this release, security performers can seamlessly deploy the selected Detection Rules or Saved Search content without additional configurations.
- Fixed the issues with global content lists:
- Fixed the issue that occurred when trying to delete content in these list types.
- For a better user experience, fixed the issue with displaying the content list name that was partly hidden.
3. Fixed the alignment of content list icons and the list names on the Create Job pop-up for a better user experience: