SOC Prime brings to your attention a small digest of the latest community rules developed by participants of the Threat Bounty Program (https://my.socprime.com/en/tdm-developers).
The digest includes 5 rules that help to detect Trojans and Hidden Tear Ransomware. In the future, we will continue to publish such selections of content to detect specific threat actors or popular exploits.
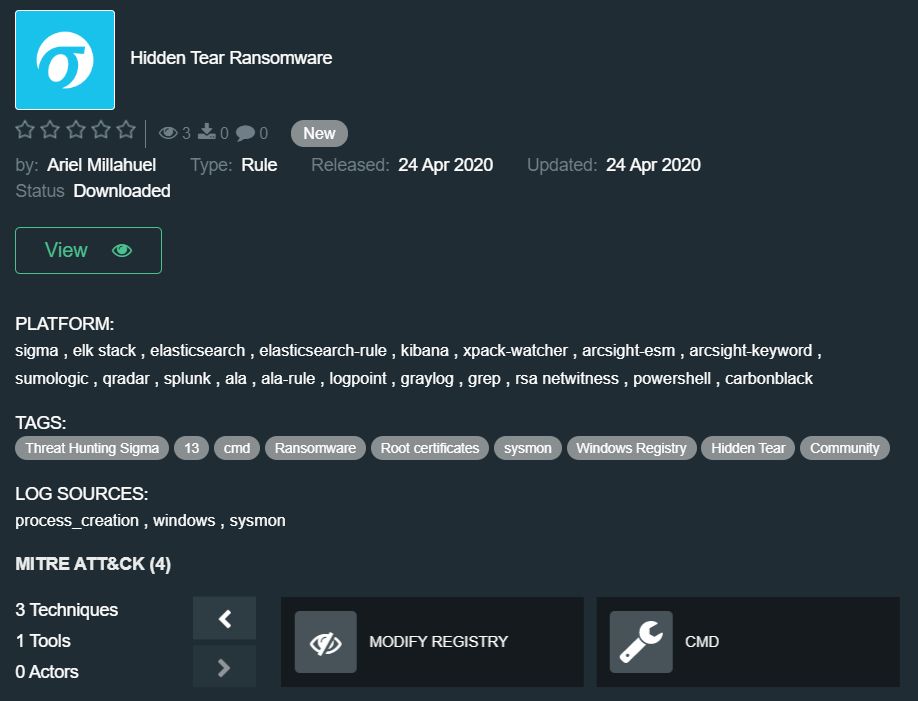
Hidden Tear Ransomware by Ariel Millahuel – https://tdm.socprime.com/tdm/info/K6UvKXunM7lJ/
Hidden Tear ransomware is an open-source project available on GitHub since 2015. Based on this code, adversaries created multiple ransomware samples, which are actively used in attacks by ‘minor league players’. Ransomware continues to be one of the largest cyber threats to businesses, and any successful attack will result in data encryption, disruption of operation, and financial loss.
Supported platforms: Azure Sentinel Query, Azure Sentinel Rule, ArcSight Rule, ArcSight Keyword, Carbonblack, Elasticsearch, Elastic Rule, Graylog, Regex Grep, Kibana, Logpoint, Windows PowerShell, QRadar, RSA NetWitness, Sigma, Splunk, Sumo Logic, X-Pack Watcher
Required log sources: process_creation, windows, sysmon
The rule covers the following techniques according to the MITRE ATT&CK® methodology: Command-Line Interface (T1095), Install Root Certificate (T1130), Modify Registry (T1112)
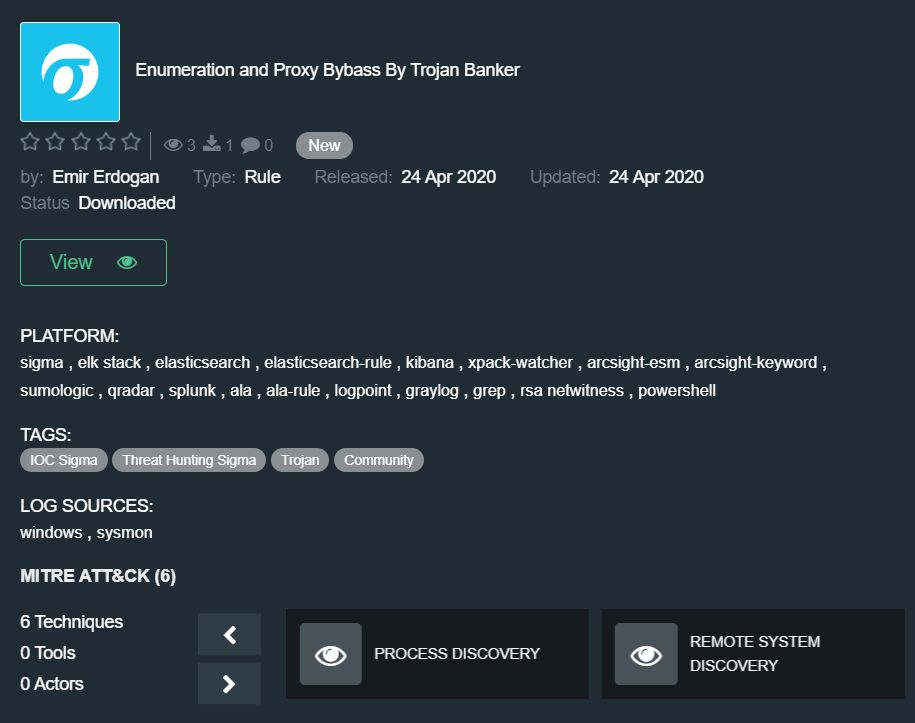
Enumeration and Proxy Bypass By Trojan Banker by Emir Erdogan – https://tdm.socprime.com/tdm/info/jEyi2VylBLJY/
This rule helps to detect the activity of Trojan Banker on an infected machine and to prevent data leakage or further installation of additional malware.
Supported platforms: Azure Sentinel Query, Azure Sentinel Rule, ArcSight Rule, ArcSight Keyword, Elasticsearch, Elastic Rule, Graylog, Regex Grep, Kibana, Logpoint, Windows PowerShell, QRadar, RSA NetWitness, Sigma, Splunk, Sumo Logic, X-Pack Watcher
Required log sources: windows, sysmon
The rule covers the following techniques according to the MITRE ATT&CK® methodology: Command-Line Interface (T1059), Network Share Discovery (T1135), Process Discovery (T1057), Remote System Discovery (T1018), System Information Discovery (T1082), System Network Configuration Discovery (T1422)
LatentBot malware by Ariel Millahuel – https://tdm.socprime.com/tdm/info/gL01KDZRPL07/
LatentBot is a multi-modular Trojan written in Delphi that has been used in attacks since mid-2013. Its authors implemented several layers of obfuscation and a unique exfiltration mechanism, so LatentBot was very successful at infecting organizations primarily in the financial services and insurance sectors.
Supported platforms: Azure Sentinel Query, Azure Sentinel Rule, ArcSight Rule, ArcSight Keyword, Carbonblack, Elasticsearch, Elastic Rule, Graylog, Regex Grep, Kibana, Logpoint, Windows PowerShell, QRadar, RSA NetWitness, Sigma, Splunk, Sumo Logic, X-Pack Watcher
Required log sources: windows, sysmon
The rule covers the following techniques according to the MITRE ATT&CK® methodology: Install Root Certificate (T1130), Modify Registry (T1112)
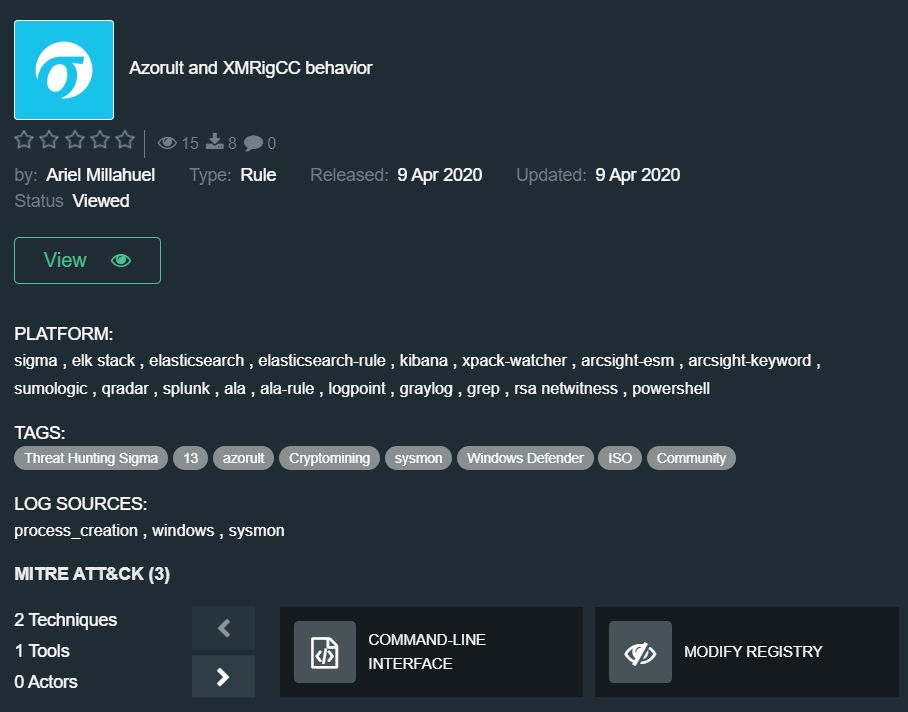
Azorult and XMRigCC behavior by Ariel Millahuel – https://tdm.socprime.com/tdm/info/itC7LOXsrKbf/
The rule detects a new Azorult behavior that attempts to download a variant ot XMRigCC cryptocurrency miner. The Azorult infostealer was discovered in 2016, it can steal credentials, browsing history, cookies, and more. Attackers also use Azorult as a downloader of other malware.
Supported platforms: Azure Sentinel Query, Azure Sentinel Rule, ArcSight Rule, ArcSight Keyword, Elasticsearch, Elastic Rule, Graylog, Regex Grep, Kibana, Logpoint, Windows PowerShell, QRadar, RSA NetWitness, Sigma, Splunk, Sumo Logic, X-Pack Watcher
Required log sources: process_creation, windows, sysmon
The rule covers the following techniques according to the MITRE ATT&CK® methodology: Command-Line Interface (T1095), Modify Registry (T1112)
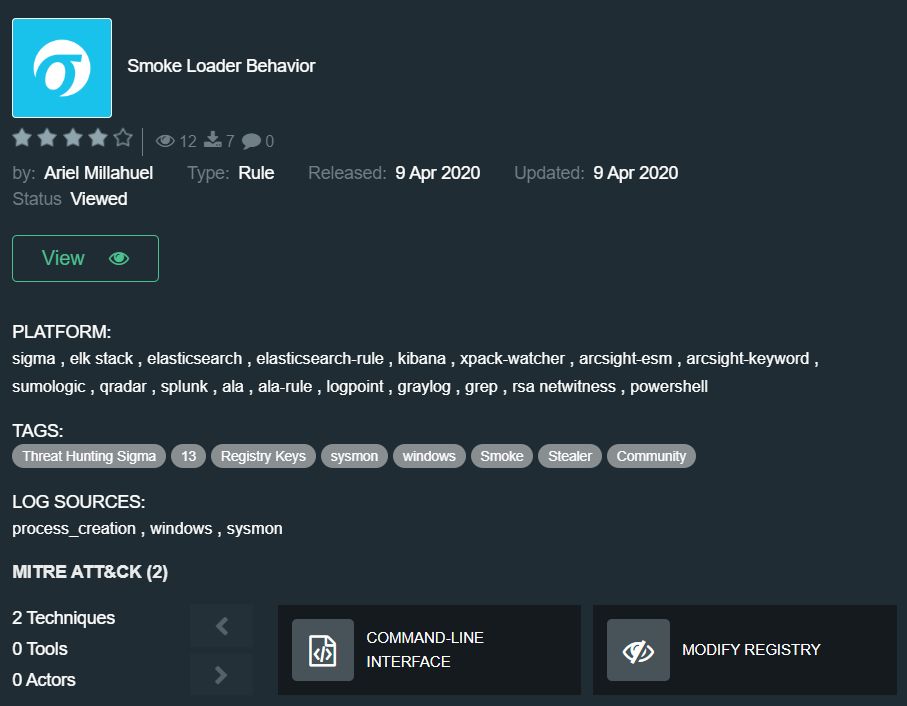
Smoke Loader Behavior by Ariel Millahuel – https://tdm.socprime.com/tdm/info/ApdAHZWWtgd4/
The rule uncovers Smoke Loader behavior via command-line and sysmon. Smoke Loader is a geo-targeting modular loader used by cybercriminals since 2011 to install backdoors, ransomware, crypto miners, password stealers, PoS malware, banking Trojans, etc. It has different modules for 32 and 64 architecture that enable grabbing credentials from browsers and email programs. Smoke Loader is known for its flexibility which makes it even more deceptive and self-protective.
Supported platforms: Azure Sentinel Query, Azure Sentinel Rule, ArcSight Rule, ArcSight Keyword, Elasticsearch, Elastic Rule, Graylog, Regex Grep, Kibana, Logpoint, Windows PowerShell, QRadar, RSA NetWitness, Sigma, Splunk, Sumo Logic, X-Pack Watcher
Required log sources: process_creation, windows, sysmon
The rule covers the following techniques according to the MITRE ATT&CK® methodology: Command-Line Interface (T1095), Modify Registry (T1112)