WinRAR as Cyberweapon: UAC-0165 Targets Ukrainian Public Sector with RoarBat

Table of contents:
Since the outbreak of the global cyber war, state bodies of Ukraine and its allies have become targets of diverse malicious campaigns launched by multiple hacking collectives. Experts estimate a 250% surge of cyber attacks against Ukraine in 2022 and over 2,000 of them launched by russia-affiliated threat actors since the beginning of the full-fledged invasion.
On April 29, 2023, CERT-UA issued a new alert covering a massive cyber attack misusing WinRAR and relying on RoarBat malicious script to disrupt the IT infrastructure of Ukrainian governmental organizations. CERT-UA assumes that russia-backed Sandworm APT might be responsible for the intrusion due to significant overlaps with the attack against informational and communication system of the National Information Agency “Ukrinform” that occurred in January 2023.
Analysis of the Latest Destructive Cyber Attack Against Ukraine by UAC-0165 Group (Sandworm APT)
The latest CERTUA#6550 alert warns cyber defenders of a massive cyber attack aimed at crippling the IT infrastructure of the Ukrainian public sector. Specifically, server equipment and data storage systems operation was disrupted as a result of the most recent malicious operation attributed to the Sandworm APT group.
Particularly, Windows systems were targeted with RoarBat .BAT script that recursively searched for files on disks or in specific directories subsequently archiving them with legitimate WinRAR program using “-df” feature. This eventually resulted in the deletion of both the source file and created archives. Simultaneously, Linux systems were attacked with the BASH script leveraging a standard “dd” utility to overwrite files with zero bytes.
CERT-UA experts estimate that this destructive operation has a lot in common with the attack against the informational and communication system of the National Information Agency “Ukrinform.¨ Consequently, the latest attack against the Ukrainian public sector, with a moderate level of confidence, is attributed to russia-backed Sandworm APT. Yet, for the focused attacks tracking CERT-UA uses UAC-0165 identifier.
Notably, adversaries managed to successfully proceed with the attack due to the lack of multi-factor authentication during remote VPN connection and insufficient network segmentation. Users are urged to enhance cybersecurity protections according to CERT-UA recommendations.
Detecting UAC-0165 Malicious Activity Covered in the CERT-UA#6550 Alert
To help organizations timely identify the malicious activity associated with the UAC-0165, SOC Prime Platform curates a set of relevant Sigma rules. All detection algorithms are filtered by the corresponding custom tags “CERT-UA#6550” and “UAC-0165” based on the CERT-UA alert and group identifiers to streamline the SOC content selection.
Click the Explore Detections button to reach the entire collection of dedicated Sigma rules detecting the latest UAC-0165 attack. All rules are aligned with the MITRE ATT&CK® framework v12, enriched with in-depth cyber threat context, and compatible with 28+ SIEM, EDR, and XDR solutions to fit particular security needs.
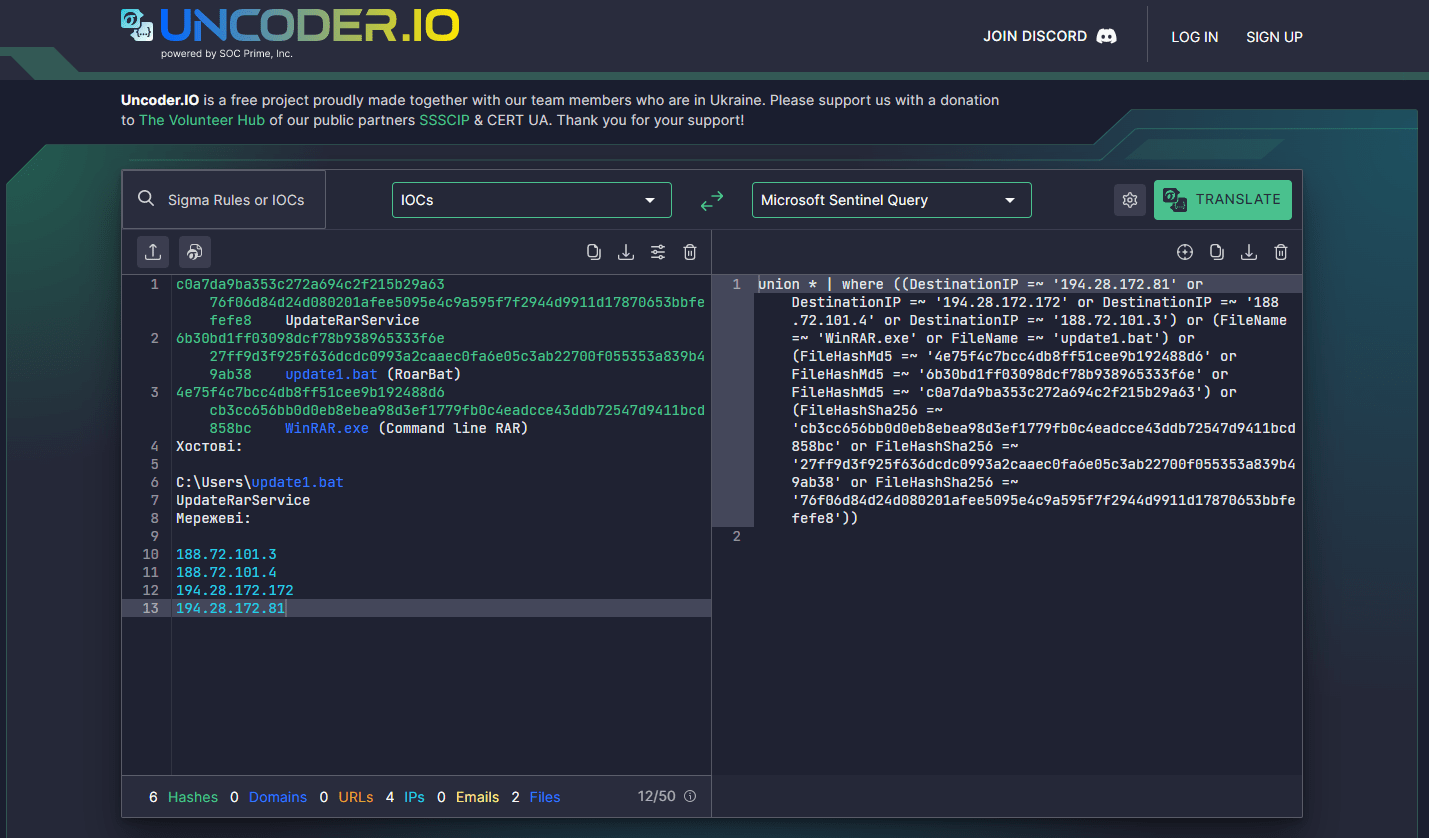
Cyber defenders can also automate their threat hunting activities by searching for indicators of compromise (IoCs) associated with the latest Sandworm operation against Ukrainian government bodies using Uncoder.IO. Just paste the file, host, or network IOCs provided by CERT-UA into the tool and select the content type of your target query to instantly create performance-optimized IOC queries ready to run in the chosen environment.
MITRE ATT&CK Context
To delve into the in-depth context behind the destructive cyber attack of UAC-0165 covered in the latest CERT-UA alert, all above-referenced Sigma rules are tagged with ATT&CK v12 addressing the relevant tactics and techniques:
Tactics Techniques Sigma Rule Defense Evasion Virtualization/Sandbox Evasion (T1497) File and Directory Permissions Modification (T1222) System Script Proxy Execution (T1216) Indicator Removal (T1070) Hide Artifacts (T1564) Subvert Trust Controls (T1553) Deobfuscate/Decode Files or Information (T1140) Domain Policy Modification (T1484) Execution Scheduled Task/Job (T1053) Impact Inhibit System Recovery (T1490) System Shutdown/Reboot (T1529) Data Manipulation (T1565) Data Destruction (T1485)