Before the release of the Continuous Content Management (CCM) module, our Threat Detection Marketplace users had to download content items and import them manually into their SIEM. We are big fans of Anton Chuvakin’s “Detection as Code” approach to threat detection, which has driven us to bring enhanced automation to the deployment of SOC content. This meant rethinking how to streamline threat detection operations and achieve enhanced security capabilities. Now, with the launch of CCM, our customers can automatically deploy content items right into your SIEM, make changes to them on the fly, and re-deploy these changes to the platform you use.
CCM is available for Microsoft Azure Sentinel and Elastic Cloud, with Sumo Logic and other cloud-native SIEM support coming up very soon. Depending on the SIEM solution in use, you can deploy content items of the following types:
- For Azure Sentinel
-
- Query
- Rule
- Functions/Parsers
- For Elastic Cloud
-
- Rule Alert
- Watcher
- Saved Search
How to Set Up Continuous Content Management Integration
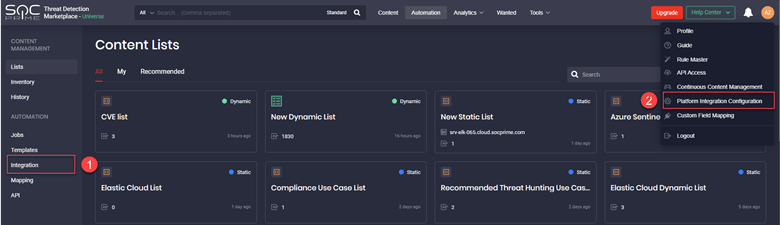
Before setting up CCM, you need to configure integration for Azure Sentinel or Elastic Cloud from the Automation page or user settings:
- Automation > Integration
- User Settings > Platform Integration Configuration
Depending on the type of content and SIEM, specific system requirements need to be met.
Microsoft Azure Sentinel
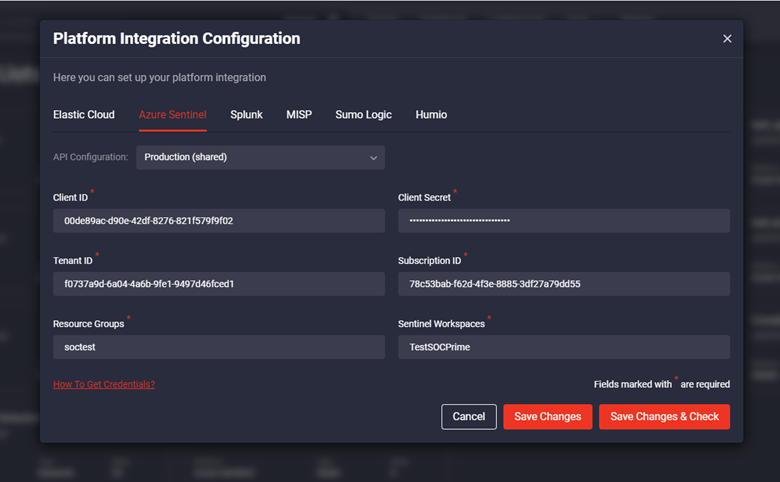
For the Azure Sentinel platform, you need to have API access to the Azure Sentinel subscription with the relevant permissions to read and deploy resources in the appropriate workspace:
- Client ID
- Client Secret
- Tenant ID
- Subscription ID
- Resource Group
- Workspace
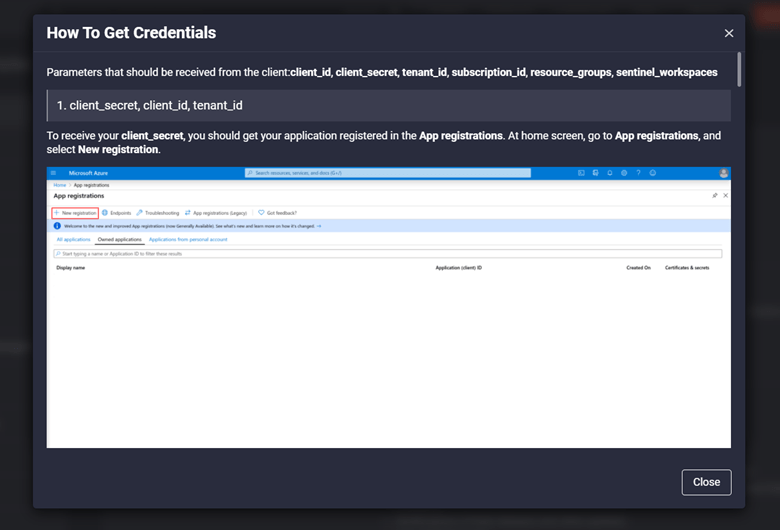
To receive these credentials:
- Click the How To Get Credentials link in the left bottom corner of the Platform Integration Configuration page.
- Follow the guidelines described in the corresponding pop-up window.
Elastic Cloud
For the Elastic Cloud platform, you need to have access to:
- Kibana for deploying Searches and Rule Alerts
- Kibana Host and port
- Login
- Password
- Space Name
- Index patterns
To receive the Index Pattern ID, click the How To Get Index Pattern ID link in the left bottom corner of the Platform Integration Configuration page, and follow the guidelines you will see.
- Elasticsearch API for deploying Watchers
- Elasticsearch host and port
- Login and password OR an API Key
Once configured, CCM is available from the Automation page or user settings:
- Automation > Content Management & Automation sections
- User Settings > Continuous Content Management
The Content Management section includes the following functionality:
- Lists for proper content organization
- Inventory for comprehensive content overview
- History for streamlined logging of all content management actions (jobs, manual deployments, content updates, etc.)
The Automation section includes:
- Jobs for automated rule deployment and other content management actions
- Templates for creating and managing content items based on custom templates and linking them to jobs
Ready to trial CCM? If you have the Universe subscription tier, you can get the most out of CCM at no charge as part of this plan. As an alternative, you can buy the CCM subscription as a separate license. Contact sales@socprime.com for more details.
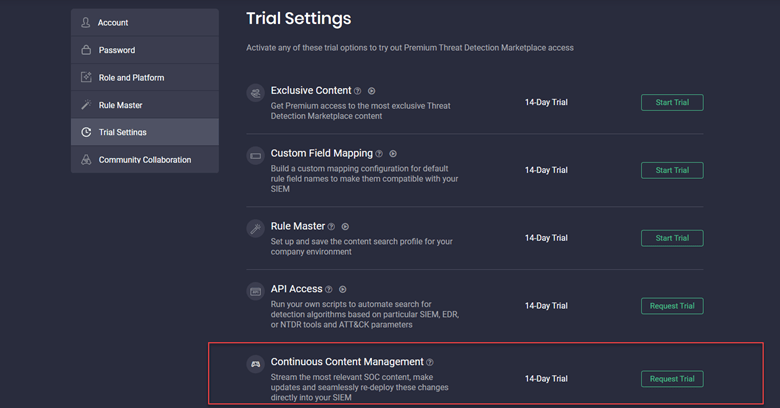
Still, there is one more option at your disposal. SOC Prime is always trying to offer more opportunities for security professionals to explore the community and obtain value from the available SOC content and platform capabilities. The CCM module is now also available as part of Free Trial, so the Threat Detection Marketplace users with the Community subscription can trial the fully automated content management system for a period of 14 days. To activate the CCM module as part of a Free Trial, you need to select Profile > Trial Settings, and then click the Request Trial button next to the Continuous Content Management trial option.
The Free Trial access to the CCM module can be activated either after having a call with the Sales Team representative or directly after the approval of the Threat Detection Marketplace Admin.
Sign up for Threat Detection Marketplace to obtain value from curated SOC content and enjoy the platform threat detection and response capabilities.