At least for two decades, we have been witnessing relentless changes in the threat landscape towards growth and sophistication, with both rough actors and state-sponsored collectives devising sophisticated offensive campaings against organizations globally. In 2024, adversaries, on average, proceed with 11,5 attacks per minute. Simultaneously, it takes 277 days for SecOps teams to detect and contain a data breach, according to research by IDM and Ponemon Institute. One of the reasons for such a layoff is the massive talent shortage within the industry, with 71% of organizations having unfilled positions.
In view of the existing talent gap and ever-growing attack surface, it is essential to make informed decisions about proper prioritization and resource-effective cyber defense operations.
Defining Threat Intelligence
Gartner states that threat intelligence, also known as cyber threat intelligence (CTI), is a crucial element of security architecture. It aids security professionals in detecting, triaging, and investigating threats, thus enhancing an organization’s security posture. By improving alert quality, reducing investigation times, and providing coverage for the latest cyber attacks and actors, CTI plays a vital role in modern cyber defense.
According to Gartner, threat intelligence is defined as “evidence-based knowledge (e.g., context, mechanisms, indicators, implications, and action-oriented advice) about existing or emerging menaces or hazards to assets.” In other words, threat intel is comprehensive and actionable data aimed at anticipating and thwarting organization-specific cyber threats. CTI empowers security teams to take a data-driven approach to proactively and effectively withstand cyber attacks before they escalate while facilitating detection and hunting efforts.
A study by Statista forecasts that the CTI market will exceed 44 billion U.S. dollars by 2033, highlighting the increasing importance of informed, data-driven defenses in contemporary business strategies. This prediction aligns with the outcomes from the Recorded Future 2023 State of Threat Intelligence report, revealing that 70.9% of respondents have a dedicated team for gathering and analyzing threat intelligence.
Integrating threat intelligence into your cybersecurity strategy can be challenging. It requires prioritizing your organization’s specific information needs and evaluating your security controls to effectively operationalize threat intelligence. Misusing CTI can result in an overload of alerts and an increase in false positives, highlighting the importance of proper implementation.
Threat Intelligence Types
Threat intelligence can be grouped into tactical, strategic, and operational depending on the organization’s objectives, parties engaged, specific requirements, and overall goals in a lifecycle scenario.
- Strategic threat intel provides high-level insights into the global attack surface and how an organization fits into it. It is mainly used for long-term decisions that transform the processes and foster the advancement of cybersecurity programs. Stakeholders leverage strategic threat intelligence to align organizational cybersecurity strategies and investments with the cybersecurity landscape.
- Tactical threat intel involves indicators of compromise (IOCs), such as IP addresses, domains, URLs, or hashes consumed by security controls but also used manually during investigations. It helps Security Operations Centers (SOCs) detect and respond to ongoing cyber attacks, focusing on common IOCs, like IP addresses linked to adversary C2 servers, file hashes from identified incidents, or email subject lines associated with phishing attacks. This type of threat intel assists in filtering out false positives and uncovering hidden attackers, aiding security teams in their daily SOC operations. In a nutshell, tactical CTI is intended to serve short-term decisions, like issuing urgent alerts, escalating cybersecurity processes, or adjusting configurations within the existing infrastructure.
- Operational threat intel, also known as technical CTI, enables organizations to proactively thwart cyber attacks by focusing on known adversary TTPs. Information security leaders like CISOs and SOC Managers take advantage of this type of CTI to anticipate potential threat actors and implement targeted security measures to combat attacks that are most challenging the business.
Who Can Gain From Threat Intelligence?
Threat intelligence encompasses extensive and actionable data designed to anticipate and counteract threats specific to an organization no matter its size, industry, or level of cybersecurity maturity. CTI equips security teams with the data necessary to proactively and effectively defend against cyber attacks, facilitating both detection and response efforts and enabling businesses to gain a holistic understanding of existing threats or proactive measures not yet linked to cyber attacks.
For small and medium-sized businesses, threat intelligence provides a level of protection that might otherwise be unattainable. Large-scale enterprises with extensive security teams can reduce costs and skill requirements by using external threat intelligence, making their analysts more effective.
Depending on the type of threat intelligence, any member of a security team can make the most of CTI to elevate the organization’s defenses:
- Security and IT analysts can enhance detection capabilities and fortify defenses. They correlate CTI by collecting raw threat data and security-related details from a wide range of sources, including open-source CTI feeds, information exchange peer-driven communities, or internal organization-specific log sources.
- SOC analysts correlate and analyze tactical threat intel to identify trends, patterns, and adversary behaviors and rank incidents by their risk and potential impact, which in turn improves the accuracy of threat identification and reduces false positives.
- Threat hunters rely on operational CTI in their hypothesis-driven investigations, providing insights into attacker TTPs to prioritize the most critical threats. They also leverage tactical threat intel to facilitate IOC-based hunting and document indicators of compromise linked to emerging and existing threats. CTI also facilitates proactive threat hunting, enabling detecting potential threats at the earliest attack stages before they cause significant harm.
- CSIRT (Computer Security Incident Response Team) can leverage threat intelligence to accelerate incident response capabilities. Threat intelligence provides CSIRT with crucial insights into the latest threats, including IOCs and attack patterns used by malicious actors, to promptly identify and remediate incidents within the organization. By integrating CTI into their workflows, CSIRT can enhance the efficiency of incident prioritization and response, resulting in quicker actions and lessened impact from cyber attacks.
- Executive management, such as CISOs, SOC Managers, and other information security decision-makers, leverage strategic threat intel to gain comprehensive visibility into the threats most challenging the business. This fosters strategic planning to anticipate future threats and vulnerabilities and effectively mitigate their impact.
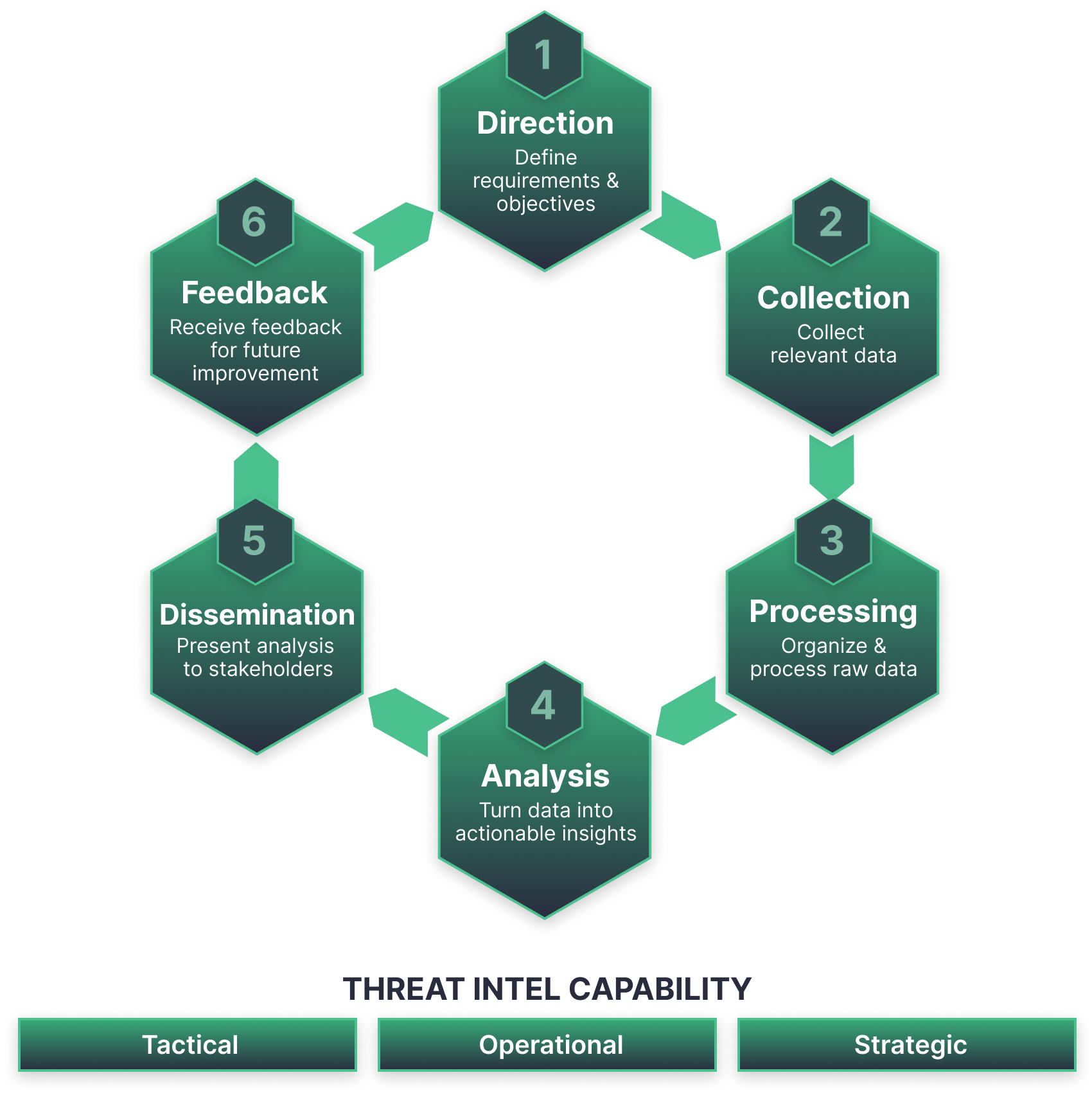
Threat Intelligence Lifecycle
CTI-related operation is a continuous process of transforming the raw data into actionable insights for informed decision making. The CTI lifecycle acts as a simple framework to enable SecOps departments to optimize their efforts and resources toward threat-informed cyber defense. Although the approaches might slightly vary, normally, the threat intelligence lifecycle consists of 6 major milestones resulting in an effective workflow and continuous feedback loop for improvement at scale.
- Direction. At this stage, security teams establish the requirements and goals for a particular CTI operation. During this planning stage, teams create a roadmap, with goals, methodology, and tools defined depending on the needs of the parties involved.
- Collection. Once the goals and objectives are clear, teams can start the data collection process. This involves gathering data from various sources, including security logs, threat feeds, forums, social media, subject matter experts, etc. In fact, the idea is to collect as much relevant information as possible.
- Processing. Once all the required information is available, the next stage of the lifecycle presumes its processing and organization into usable form. Normally, it includes evaluating data for relevance, filtering, removing irrelevant details, translating info from foreign sources, and structuring the core data for further analysis.
- Analysis. Having a ready dataset at hand, teams proceed with the thorough analysis to convert disparate data pieces into actionable CTI, including threat actors profiling, threat correlation, and behavious analysis.
- Dissemination. Once analysis is performed, at the dissemination phase teams ensure that key conclusions and recommendations are received by stakeholders.
- Feedback. The final stage is receiving feedback from the parties and stakeholders involved to determine adjustments and improvements to be made during the next cycle.
SOC Prime Platform for collective cyber defense provides out-of-the-box CTI capability, enabling teams to significantly reduce the time and effort required for each threat intelligence lifecycle stage. By relying on SOC Prime, security experts can swiftly navigate through large volumes of data and explore researched and packaged context on any cyber attack or threat, including zero-days, MITRE ATT&CK® references, and Red Team tooling to proactively identify and thwart threats that matter most. All the threat intel and actionable metadata are linked to 13K+ Sigma rules, which include triage and audit configuration recommendations, to make your threat research perfectly matching your current needs.
Threat Intelligence Use Cases
Threat intelligence is an essential element of a comprehensive cybersecurity program that has hands-on applications across multiple security areas to enhance detection, response, and future-proof the overall cybersecurity posture. From accelerating incident triage and prioritizing alerts to supporting daily security operations and conducting proactive threat hunting, it offers critical insights into common threat intelligence use cases.
- Alert Triage and Prioritization. Threat intelligence assists SOC analysts in accelerating alert triage by helping them gain contextual information to fully comprehend and prioritize alerts and easily assess whether escalation or remediation of the incident is necessary. By enriching alerts with actionable CTI, defenders can easily cut through the noise and reduce false positive rates.
- Proactive Threat Detection and Hunting. Threat intelligence is crucial in TTP-based threat hunting, enabling security teams to proactively search for signs of advanced threats within their environment. By operationalizing threat intel, security teams can uncover hidden threats and vulnerabilities that evade traditional security controls, quickly identify suspicious behavior during hunts, and disrupt threats before they strike. Threat intelligence also facilitates the tracking of critical performance metrics, like Mean Time To Detect (MTTD), helping evaluate the efficiency of threat detection and response efforts.
- Vulnerability Management. Threat intelligence provides insights into emerging vulnerabilities and zero-day exploits. This allows organizations to prioritize patching and mitigation efforts based on the real-world threats relevant to their infrastructure.
- Phishing & Fraud Detection. In the year of AI, phishing attacks increased by 58.2%, as compared to the previous year, indicating the increased sophistication and expansion of adversaries, which underscores the need for strengthening defensive measures against phishing campaigns. Threat intelligence helps in identifying phishing campaigns, malicious domains, and suspicious IP addresses associated with fraudulent activities. This enables organizations to block malicious communications and proactively defend against phishing attacks of any scale.
- Strategic Decision Making. Threat intelligence assists in mapping the threat landscape, evaluating risks, and offering essential context for making timely decisions to refine cybersecurity strategies in line with the current business priorities. By understanding the evolving threat landscape, organizations can allocate resources effectively to strengthen their overall cybersecurity posture.
- Community Collaboration & Knowledge Sharing. Threat intelligence fosters information exchange and global industry collaboration by providing valuable insights into emerging threats, attack trends, and adversary tactics. Security teams can share CTI with industry peers, government agencies, and peer-driven communities to collectively strengthen defenses and mitigate risks while enhancing situational awareness across the cybersecurity landscape. Moreover, threat intelligence fosters a community-driven approach where organizations can share their expertise with aspiring security engineers and adapt strategies together to effectively combat cyber threats. SOC Prime’s Discord serves as a community-driven platform where cybersecurity professionals of diverse experience levels and backgrounds connect to exchange their knowledge and insights with newcomers, share behavior-based detection algorithms and threat intelligence, and discuss the latest cybersecurity trends to gain a competitive advantage against adversaries.
SOC Prime’s product suite for advanced threat detection, AI-powered detection engineering, and automated threat hunting serves out-of-the-box CTI capability, helping security teams save time & effort on threat intel operations. By relying on SOC Prime Platform, organizations can seamlessly keep up with the latest TTPs used by adversaries in the wild, as well as proactive methods not yet linked to cyber attacks. Explore relevant context linked to 13K+ Sigma rules addressing any cyber attack or threat, including zero-days, CTI and MITRE ATT&CK references, or Red Team tooling to facilitate operationalizing your threat intelligence.




