Malware stands for malicious software and denotes software that is designed to execute computer instructions that are destructive to a user’s system or in any other way hazardous for targeted individuals and enterprises.
Rapid technology development has brought a proliferation of various kinds of malware. It can do a range of bad things, such as stealing sensitive information, spying, disabling digital assets, tampering with data, and more.
Malware developers are usually called cyber attackers, hackers, or adversaries. These persons and groups of people hide their identities to escape legal liability. Yet, sometimes they want to do it to make a statement; that’s why they go public about their malicious activities.
Now that we figured out what is malware, let’s explore some common types of malware. It’s important to understand attack vectors to be able to use proper cyber defense. For organizations that practice cybersecurity on an enterprise level, timely Threat Detection rules are necessary to stay ahead of the attackers. Discover SOC Prime’s Detection as Code platform as well as SOC Prime Search Engine to detect known malware and hunt for stealthy exploits that aren’t patched yet.
Detect & Hunt Explore Threat Context
What are the Types of Malware?
There are so many types of malware nowadays that it seems like making new types is a new digital trend (next after TikTok challenges). Every day you’ll see another news article with a new -ware word. Cryware, spyware, scareware, rogueware, you name it. In this blog post, I’ll describe the most widely used malware types that can potentially hit anyone today. Enhancing cyber defense measures against these types of malware is a high-priority task of any SOC team.
The terms listed below might also be used interchangeably. For example, a virus can be ransomware, spyware can be a trojan, and ransomware can be a botnet.
Viruses
A virus is a type of malware that can replicate itself countless times and needs a host to execute. Viruses want to run as part of legitimate processes. Often, the user knows nothing about the viral activity until it’s too late.
Viruses have been known since the first days of the Internet and still keep infecting millions of computers around the world. Over twenty years ago, the infamous strain ILOVEYOU infected over 10 million computers, including those inside reputable institutions. Like any true love, it didn’t ask anything for itself – it just disabled those computers which brought billions in damage.
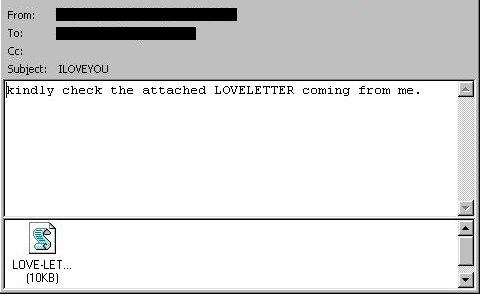
Unlike those old viruses, new ones are more financially oriented. Statista shows that the biggest share of all viruses throughout the world belongs to crypto miners. Viruses can be purchased on the dark web, so it’s fair to suggest that for many attackers, it’s more about a business venture than an evil-genius coding experience.
Worms
Worms can also replicate multiple times, digging deeper and deeper into networks and consuming their bandwidth. Unlike viruses, they don’t attach themselves to other programs and don’t require human interaction like clicking a link or a file. Worms often exploit vulnerabilities in operating systems which let them abuse automated routines and spread uncontrollably.
WannaCry is perhaps the biggest ransomware worm that has recently targeted Windows OS. It used EternalBlue exploit that was stolen from NSA. Interestingly enough, the exploit was patched at the time when the attack campaign started. Lesson learned: never ignore the updates.
Logic Bombs
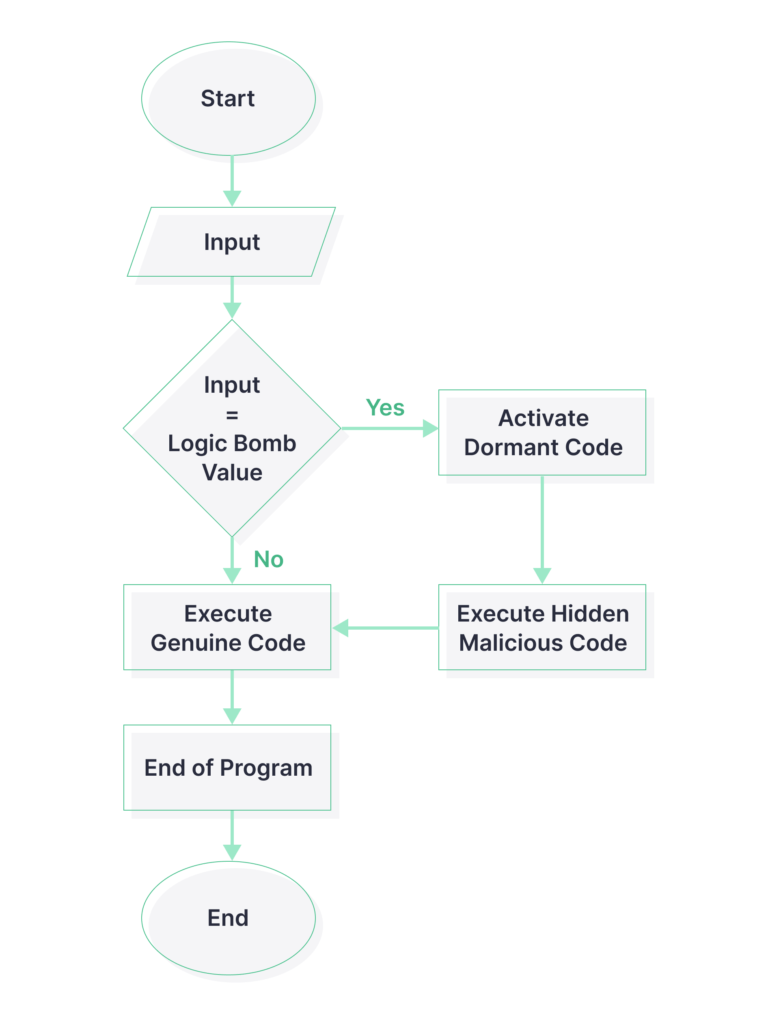
Logic bomb is a type of malware that executes upon certain conditions. It belongs to a new type of “fileless” malware since it’s enough to inject a string of code or a script for the logic bomb to start ticking.
A famous case of the logic bomb tells a story of a software developer that was laid off by one of the companies. As soon as he left, a massive data wiper hit the company’s network. Malware analysis showed that the bomb trigger was the absence of employee’s name on a payroll.
Backdoors
As the name indicates, a backdoor is a type of malware that allows attackers to bypass a standard authentication and authorization method. Basically, they can walk in and out of the infected system unnoticed until the suspicious activity is detected. Backdoors are often installed by related malware files that first intend to gain Initial Access and then connect to a malicious server. Backdoors can operate for a long time, serving as gateways for multiple payloads.
However, some backdoors are available as a default feature in legitimate software and hardware. Obviously, attackers gladly abuse this functionality. There’s also an interesting overview of common backdoors made by OWASP Top 10 – definitely worth considering.
Trojans
Trojan viruses masquerade as something that the victim wants to have. It can be a game or a piece of software downloaded from an untrusted source. One of the nastiest examples is a free antivirus program that is actually a virus. It can even come as a browser extension. Researchers also refer to infected Word documents as trojans. They are being sent in phishing emails.
The trojan payload may vary depending on the goals of the attackers. It can demand payments, steal or encrypt data, lock the screen, consume system resources, disable controls, and distribute other viruses. One of the biggest malware botnets, Emotet, started out as a banking trojan and resurfaced even after a massive special operation was conducted by the governments of several countries.
RAT
RAT stands for Remote Access Tool. It allows adversaries to take remote control of the victim’s system. Immediate damage or financial gain is rarely a primary goal of such malware. In this case, attackers might take time to discover other machines on the network, as well as users and their privileges. They might move laterally to more important assets that are more critical to the infrastructure. RATs can also log credentials, keystrokes, messages in emails and chats, and take screenshots. After the data is obtained, it can be sent to a malicious server. Some types of malware like SUNBURST can communicate with a C&C server on a special schedule which is called beaconing.
Ransomware
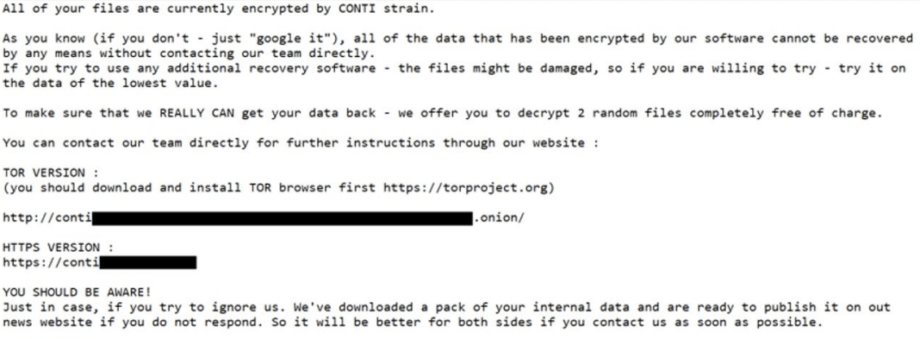
Ransomware is a type of malware that encrypts and locks a victim’s data and demands a ransom to get things back to normal. The latest ransomware stats show that this kind of malware has its highs and lows, possibly due to spikes in running attack campaigns. It’s one of the biggest cyber-attack markets. Ransomware infrastructure consists of botnets and Ransomware-as-a-Service networks as well as groups that compete with each other for a bigger chunk of the market share.
Another lucrative business is ransomware negotiation services that are run primarily by lawyers. One of the biggest ransoms paid ($40 million) by CNA Financial Corp. is said to be a reduction from $60 million. Some negotiators don’t afraid to get their hands dirty, too. Bloomberg reported a case where hackers demanded documented proof of the ransom amount from the negotiators. Turns out, the hackers were conned by negotiators before. The latter said that victims were ready to pay a less amount and pocketed the difference between the actual sum and what they gave to the attackers. As Bloomberg puts it, “Scammers said they were worried about being scammed.”
Ransomware has its trends, too. For example, double and triple extortion. Double extortion is when an attacker steals and encrypts the data, threatening to sell it if the ransom isn’t paid. Triple extortion is when attackers are threatening not only the company which they hacked but also affected third parties.
Sometimes, miracles happen, too. For example, the Colonial Pipeline’s ransom was almost fully recaptured by DOJ from a previously “reliable” Bitcoin blockchain that has been used by adversaries very often.
To stay resilient, organizations need to implement data recovery procedures and always have backups in places that are unlikely to be destroyed. By the way, experts suggest that infrastructure reproducibility should become a common cyber metric to track.
Keyloggers
Keylogger is short for keystroke logger. In other words, it’s malware that records every action on a computer’s keyboard. Yet, it might record other inputs as well:
- Everything that’s copied to the clipboard
- Mouse clicks
- Activity (opened programs, folders, etc.)
- Can make screenshots
- Can retrieve text value (passwords behind a mask)
Keyloggers might want to log credentials, credit card numbers, conversations in chats and emails, browsing history, and even remotely control a victim’s machine. The malware can be downloaded without a user’s awareness and run stealthily in the background. The logs are usually stored in files, so one way of detecting a keylogger is to examine files that often update. These files are also being sent to a C&C server, so it makes sense to look for an established connection.
Spyware
Spyware is a type of malware that is designed to monitor, log, encrypt and exfiltrate the victim’s personal data to a malicious server. It might also do beaconing and notify the C&C server when to download additional malware. Spyware is interested in human behaviors, so its primary target is a personal computer or a mobile device.
However, advanced spyware can infiltrate a large organization instead of targeting individuals. A widely known example is a presumably state-sponsored malware that infected the Starwood chain of hotels and then spread to Marriott as soon as they acquired Starwood. This malware could obtain information about passport details, so it could track a person’s appearance, location, and financial records.
All in all, spyware can spy on every possible piece of information: web browsing, data inputs and outputs, location, and software in use. It might gather audiovisual content as well as secretly turn on microphones and cameras and record on its own. Some examples include capabilities like hijacking privileged accounts and making database queries if spying on an organization.
Perhaps, one of the most notorious spyware examples is the Pegasus project. The latest version could leverage zero-click exploits and leave no detectable traces on a target device. About a year ago, Amnesty International published a detailed report with Pegasus detection guidelines.
Adware
Adware might take different forms. Some of it is benign, meaning that it doesn’t intend to cause any harm, but it does collect data and show advertising within the software application. For example, it might be a free version of a mobile app in which you agree to view apps, but you can upgrade to a premium version to stop seeing those. However, for the purpose of this article, let’s take a quick look at malicious adware.
Some websites that provide free content like songs and videos have been infected with common malware types like adware quite extensively. Most users will recognize this story: you visit a website, click play, and suddenly get redirected to another webpage, and numerous pop-ups appear. In a worst-case scenario, the adware can open annoying unclosable ads, lock the screen, demand payment, and do some background actions like adding the victim’s device to a botnet infrastructure.
Bots and Botnets
A bot itself is also not a bad thing. Numerous customer support bots let you speak with a robot before an actual human employee. Google search engine crawlers are also bots. However, in the cybersecurity world, there are different kinds of malware called bots. They secretly hijack the victim’s computer controls to execute malicious tasks.
A botnet is an interconnected network of bots that work together to reach a common goal. They are often orchestrated by a malicious C&C server or a network of such servers. Bots have the ability to self-replicate just like viruses and worms. A victim might be unaware of the fact that their machine is part of a botnet. Some signs like sudden crashes, slow shutdown process, slow software execution, or slow Internet traffic for no apparent reason might indicate a connection to a botnet.
It’s getting worse when bots become part of a P2P infrastructure instead of simply being connected to one malicious server. In this case, it’s more difficult to detect the source of a cyber-attack. Also, a victim might perform an attacker’s job without even knowing it. For example, GameOver Zeus used an especially predatory move by utilizing a domain generation algorithm (DGA) for botnet communication.
Rootkits
Rootkit is a type of malware that gains unauthorized access to a computer’s root directory, a.k.a. kernel. This is the heart of any operating system, so as you already guessed, it’s possible to make a lot of mess once the adversary gains root access.
First of all, a rootkit can block antivirus calls to the system. As a result, the antivirus scan report says that everything is fine, while the malware has gained complete control over the victim’s device. A typical rootkit is a collection of malware containing keyloggers, botnets, backdoors, data harvesting and exfiltration tools, bootloader replacements, RAM eaters, and more. In kernel mode, the rootkit might change system settings and be impossible to remove. One of the widely discussed rootkits is Stuxnet which led to serious problems in Iran’s nuclear plant and other industrial facilities.
Cryptojacking & Co
All-time-high is a word that’s commonly used in the crypto industry. However, lately, it’s been not only about crypto prices but also about crypto crime, with illicit addresses receiving $14 billion in 2021.
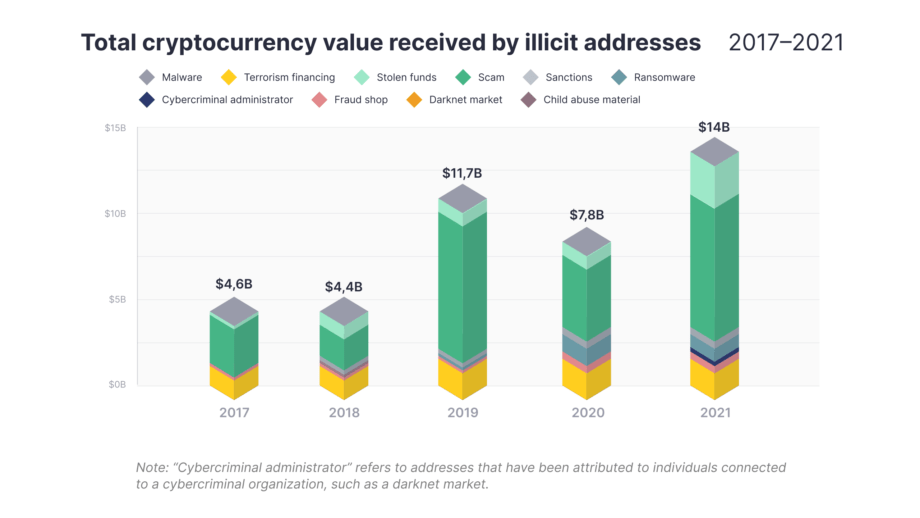
As you can see, scams, stolen funds, and darknet markets were dominant in 2021. Crypto-oriented types of malware attacks apply in all those cases. So, what are those types?
- Scams – might be part of social engineering attacks
- Stolen funds – might refer to many types of malware. They mostly try to infiltrate a device with hot wallet access
- Ransomware – operators receive ransoms in digital currencies.
Cryptojacking refers to a type of malware designed to quietly mine cryptocurrencies on a victim’s device. It consumes system resources and tries to stay disguised for as long as possible.
As for stealing funds, common forms of malware include keyloggers that want to find a combination of a public and private key (sometimes a seed phrase) and get access to a crypto wallet. Info-stealers can also scan system memory, text documents, browser sessions, regular expressions – anything that gives them some credential clue. Non-custodial wallets are generally more susceptible to theft than custodial ones. And if an attacker performs a blockchain transaction – it’s irreversible. If you’re interested in crypto attacks, check out Microsoft’s report with attack surface details and common kill chain examples.
Malware Detection with SOC Prime
Once registered at SOC Prime Detection as Code platform, you will access thousands of Sigma-based detection rules that are also translated to 26+ vendor-specific formats. More than 7000 organizations worldwide use these rules daily to streamline their threat detection processes. New detection items targeted at different types of malware appear on the platform within 24 hours after an official disclosure.
Threat Hunting queries are crafted by the industry’s leading security professionals and are intended for custom searches on SIEM, EDR, and XDR platforms. Discover new and undisclosed threats within a network before attackers cause any harm. Every search query and detection rule comes with threat intelligence context and MITRE ATT&CK® mapping that allows SOC teams to analyze new threats quickly and efficiently.
Established Threat Hunting professionals and Detection Engineers also join Threat Bounty – our crowdsourcing initiative that brings together time-sensitive detection content on a global scale of threat landscape. Content authors get repeated payouts for their effort and Detection as Code platform users enjoy the benefits of collaborative cyber defense that sets them free from siloed security approach and its consequences.




