Some MITRE ATT&CK tactics require special attention from security experts, and Initial Access is one of them. Because if attackers don’t break in, they won’t be able to take their kill chain to another level.
Earlier this year, Microsoft paid $13.7 million in bug bounties in return for discovering 1,091 vulnerabilities and a whopping $200,000 for one undisclosed Hyper-V vulnerability. That shows how valuable proactive cyber defense is. And most likely, a great deal of those new vulnerabilities is about initial access. Because as you will see later in this post, it’s much more than just stolen credentials. Initial access is potentially everywhere.
Common Entry Points for Initial Access
Initial Access tactic is, most commonly, the next step after such tactics as Reconnaissance and Resource Development. In other words, before actually entering the door, someone needs to decide where to go and, once they did, decide which door to enter and how. Same is true for cyber-attacks. First, attackers might actively scan the network and see if there are any vulnerable points that they can exploit. In the event of a recon success, they would select specific targets, for example, IPs, and choose the method of invasion.
Mind that if you apply an APT-based approach, your threat detection activities should expand beyond the capabilities of a certain attacker’s behavior at the initial access stage. Put simply, once someone gains the initial access, a whole variety of things can be done. Even those unusual for a suspected threat actor. For example, groups called Initial Access Brokers specialize in just compromising networks and then selling the access to other threat actors. Let’s take a high-level look at how they gain initial access.
Before diving into theory, don’t forget to check out what our Cyber Threats Search Engine has regarding the Initial Access tactic. You can also search for any threat- or vulnerability-related keywords that you like, exploring relevant information and detection algorithms.
Phishing
Prompting a legitimate user to take common action like opening a document in an email is one of the easiest ways for the attackers to plant malware with a backdoor or even a direct payload (T1566).
Malware-infected emails often look nothing like spam or fake. This form of initial access has been around for decades, and indeed it’s surprising why qualified professionals that work in top organizations still “buy it” and click on malicious links or download attachments. The thing is, adversaries put a lot of effort into making phishing messages seem like trusted ones.
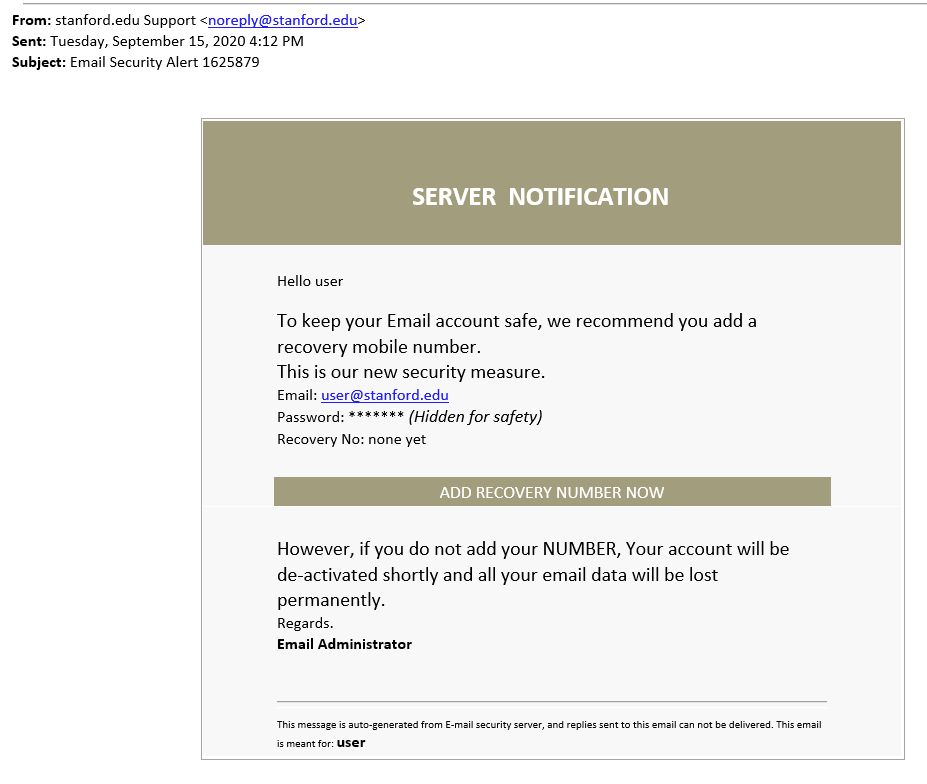
Source: Stanford
Notice that the email comes from noreply@stanford.edu which looks like a legitimate address. The email mimics a security alert that urges a recipient to act asap.
By the way, it might not even be an email – MITRE ATT&CK shows cases where malware was delivered through fake job offers and messages on social media.
Malicious links might be built based on a variety of threat models, depending on the goals of attack campaigns. Sometimes they will bring the user to a spoofed login page or a billing page for making a payment. Others will quietly steal session tokens or initiate a drive-by download. When it comes to attachments like trojan Word documents, zip files, images, and executables, ATT&CK added them to a Spearphishing Attachment sub-technique (T1566.001). Spearphishing implies precise targeting of victims. However, malicious attachments can also be sent in massive campaigns without a specific focus on companies or individuals.
Drive-By Compromise
A technique (T1189) in MITRE ATT&CK framework describes a scenario when attackers try to deliver an exploit code through a browser while a victim does some normal activity like Internet browsing.
You’ve probably heard about typosquatting – a type of attack when a rogue domain is registered that looks almost like a legitimate one but includes one small typo that is hard to recognize. However, genuine domains might also be compromised if adversaries inject malicious code in JavaScript, iFrames, or cross-site scripting (XSS).
Some other instances of initiating a drive-by download include malicious advertising and abusing built-in web application interfaces for injection attacks. Any kind of input field is an opportunity for the attackers to make a target system read some arbitrary script or code.
Examples of a web application interface:
- CLI – command line interface
- GUI – graphical user interface
- MDI – menu-driven interface
- FBI – form-based interface
- NLI – natural language interface
Another type of attack that deals with initial access is called a watering hole – it is when adversaries want to plant malware into a website that hosts content for a community of people. It’s a “good deal” because instead of attacking every victim separately, they attack only the supplier, and once compromised, it does the job for them.
Public-Facing Applications Exploitation
The technique (T1190) is dedicated to a range of sophisticated exploits on an Internet-facing software level. Attackers try to exploit bugs, glitches, collisions, and design flaws to enter victims’ systems. If the compromise happens on a cloud, which is often used these days, they will try to escape the underlying instance or container and move laterally or further down to the host.
To get an idea of what kind of software can potentially be compromised, take a look at the table below.
|
Vulnerability |
Associated Software |
|
CVE-2017-3066 |
Apache BlazeDS library |
|
CVE-2017-7269 |
Microsoft Windows Server 2003 R2 |
|
CVE-2017-10271 |
Oracle WebLogic Server |
|
CVE-2018-13379 |
Fortinet FortiOS and FortiProxy |
|
CVE-2019-0604 |
Microsoft SharePoint |
|
CVE-2019-19781 |
Citrix Application Delivery Controller |
|
CVE-2019-11510 |
Pulse Connect Secure |
|
CVE-2019-9670 |
Synacor Zimbra Collaboration Suite |
|
CVE-2019-18935 |
ASP.NET AJAX |
|
CVE 2020-0688 CVE-2021-26855 CVE-2021-26857 CVE-2021-26858 CVE-2021-27065 CVE 2020-17144 |
Microsoft Exchange Server |
|
CVE-2021-44228 |
Apache Log4j2 |
|
CVE-2020-10189 |
Zoho ManageEngine Desktop Central |
|
CVE-2020-5902 |
BIG-IP |
See https://cve.mitre.org/ to discover affected versions and detailed technical descriptions.
As you can see, at the stage of initial access, attackers tend to exploit software for communication, management, web services, and even security solutions. That’s why updating public-facing applications as soon as new versions are available is crucially important. Otherwise, it’s very challenging to maintain the cybersecurity posture. For effectively dealing with unpatched vulnerabilities, development teams are increasingly considering shifting left and applying secure code practices and security tests throughout the entire CI/CD pipeline.
The table above is only a small portion of what’s been going on across the threat landscape. Understandably, it’s difficult to follow the fluctuations and mutations of an overwhelming variety of vulnerabilities. Security experts have been trying to boil those down to trends to make it easier. For example, OWASP Top 10 and CWE Top 25 highlight the most “popular” types of exploits, so you can think of how to mitigate whole families of vulnerabilities rather than expect the unexpected in every single product, library, or utility that you use.
Legitimate User Accounts Compromise
Valid Accounts technique (T1078) describes a situation when attackers gain access by compromising real user accounts. These can be accounts of employees as well as trusted accounts of third parties like business partners or contractors. This technique is usually multi-stage and implies combining other Initial Access techniques like Phishing, Drive-By Compromise, External Remote Services, and Exploit Public-Facing Application.
For example, according to research, a notorious Uber breach involved quite a few steps:
- A personal device of an Uber contractor was infected with malware that exposed credentials.
- An attacker bought a login/password of an Uber contractor on the dark web.
- Launched an MFA fatigue attack on the chosen victim with a corporate account. The adversary bombarded the user with push notifications and applied social engineering (impersonating the IT team member on WhatsApp) until the victim surrendered and took the final authentication step.
- After that, the attacker registered their own device for MFA and gained access to Uber’s intranet through an internal VPN connection.
- The actor located PowerShell scripts containing hardcoded admin credentials.
- Using those credentials, they logged into a Privileged Account Management (PAM) platform.
- From there, they were able to freely surf across multiple cloud environments of the organization.
Our team has created rules for detecting possible MFA flooding – the exploitation at the start of the Uber attack. Check them out at our Cyber Threats Search Engine.
Exploitation of External Remote Services
Technique T1133 is about initial access attempts through remote services. As you can imagine, remote access to an internal asset over an encrypted channel without the need to break anything is exactly what adversaries need. But how do they actually infiltrate?
The most straightforward way to do this is to obtain access to a legitimate user’s account, which also relates to a Valid Accounts technique (T1078).
When it comes to containerized environments, authentication might not be needed for the initial access. Instead, attackers can exploit an exposed API of a Docker or Kubernetes server, web application, or kubelet. For example, Doki is a crypto-related backdoor that sneaked in through an open Docker daemon’s API port.
By further observing Procedure Examples in MITRE ATT&CK, you might notice that VPN connections are used in the majority of cases of initial access. Other mentioned connections are SSH, VNC, RDP, OWA, and Citrix.
Software Supply Chain Compromise
Modern software is constantly in flux, so the attack surface for supply chains keeps increasing as well. As demonstrated by Google, vulnerabilities can be found in multiple points of development processes. And they have to do with multiple MITRE ATT&CK tactics, including Initial Access and its corresponding technique, Supply Chain Compromise (T1195).
Initial access through supply chain compromise is about utilizing sophisticated methods that don’t necessarily involve hacking the identity and access management tools. For example:
- Malware is packed within good software, like in the case of SolarWinds. The attack reportedly started from the code injection.
- Exploitation of the project infrastructure. A prominent example is dependency confusion, revealed by researcher Alex Birsan.
- Applying new vectors for patched vulnerabilities. For instance, the Iranian APT MERCURY has been exploiting Log4j 2 through SysAid apps for initial access, which hasn’t been observed before.
Entry points for initial access attacks over supply chains may include compromised websites, digital certification authorities, open-source libraries, misconfigured public cloud storage buckets, and more. A quick reference from National Counterintelligence and Security Center (NCSC) might be useful.
Trusted Business Channels Compromise
Trusted partnerships on a software level include collaboration with Managed Service Providers (MSP) that have privileged access to organizations’ digital resources. These providers have been targeted by attackers as a primary vector (T1199) to gain access to more high-profile targets.
It makes sense for adversaries to find a less protected victim who has a trusted relationship with a bigger organization and breach them first. To do this, they might apply a variety of techniques that are also associated with a Credential access tactic (TA0005).
Targeted attacks include intricate sequences of malicious activities, with trusted relationships exploitation integral to a sophisticated operation. For example, the Sandworm group used spearphishing at the beginning of their attacks and continued with a variety of malware strains like NotPetya. They even attempted to mask their own malware to make it look like Lazarus samples. During one of the attack stages, they used a dedicated connection between government organizations to move from one network to another.
Removable Media & Hardware Exploitation
Techniques called Replication Through Removable Media (T1091) and Hardware Additions (T1200) mostly describe the use of physical media and firmware for gaining illicit access to corporate digital infrastructures. Why do adversaries want to exploit different kinds of devices for the Initial Access tactic? Mostly, it’s about one native feature – autorun. For example, as soon as a piece of removable media is inserted into another system, it automatically starts executing certain processes. So, if a malware executable is planted into a device, it will immediately infect a target host.
For example, a modular backdoor dubbed CHOPSTICK has been used by APT28 in multiple campaigns. Essentially, they can choose which variants to use and when, compiling malware before execution and at runtime as well. One of the CHOPSTICK samples was abusing air-gap/closed networks by routing messages between a registry, local directories, and USB devices.
Planting malicious hardware to hack an enterprise might seem impossible, but researchers show that it may cost an attacker as little as $200. The proof-of-concept (PoC) published in Wired suggests how a tiny chip smaller than a pinky fingernail can be seamlessly added to a legitimate motherboard of a Cisco firewall. This PoC is inspired by a fascinating revelation stating that Chinese microchips were found in the motherboards of one of the top manufacturers. Some other types of hardware additions include pwn plugs, ATM card skimmers, WiFi Pineapples, and LAN turtles.
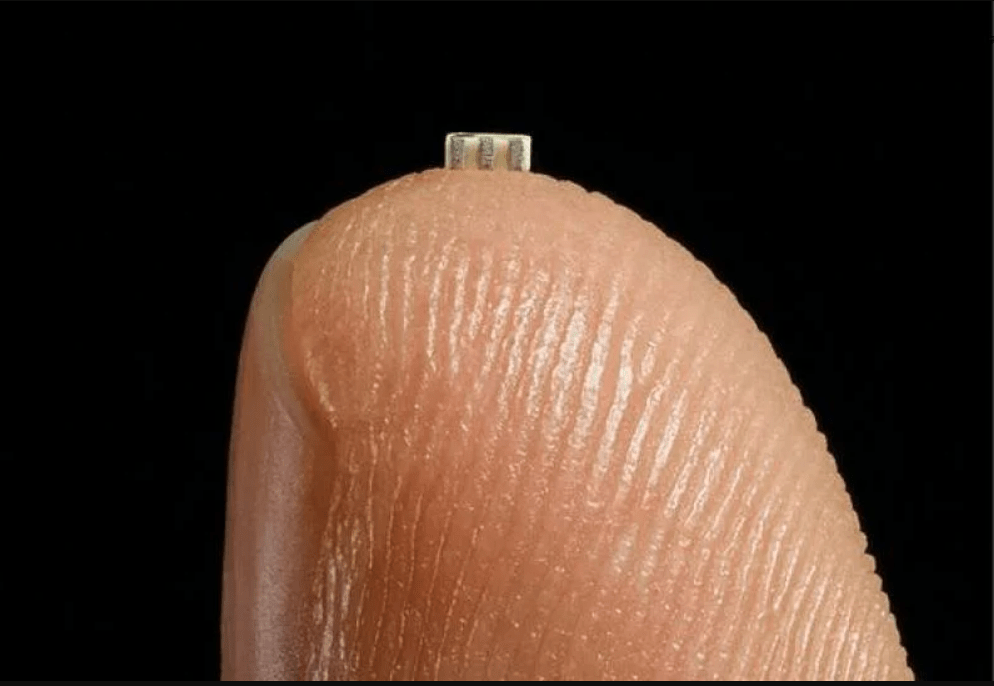
Image credit: Bloomberg. The size of the Chinese spying chip.
How to Detect Initial Access
Provided that you’ve got all the necessary logging devices, software, and configurations in place, let’s try to boil down the Initial Access detection patterns into a few general points:
- Like in the Uber case, try to detect the count of MFA push notification events per unique session ID/user over a short timeframe plus their corresponding success/failure outcomes. Outliers might signify an MFA fatigue attack.
- Another Uber problem that became a lesson for everyone is hardcoded credentials in PowerShell scripts. Use source code analysis tools and disassemblers to detect hardcoded secrets and apply mitigation best practices. See recommendations from MITRE on how to do both.
- Improper input validation is a ubiquitous weakness that increases the risks of initial access together with all sorts of code injection attacks. See our Medium blog post where we analyze an AWS-IAM case and offer a detection logic.
- Monitor process creation, file access, drive creation, and file creation on removable media.
- Phishing detection might include the use of detonation chambers and anti-spoofing measures.
Let’s also not forget that cybersecurity is not only about logs monitoring but also about the right management.
That’s why we recommend exploring the following approaches to detecting Initial Access:
- Train your employees. Initial access often starts with social engineering. Employees should be properly trained to recognize and report malicious activity to a security team.
- Do threat modeling. Identify threats, probability of occurrence, priority, and means to detect/remediate. Threat modeling can focus on assets, cybercrime groups, or software. Use methodologies to apply threat modeling to an agile environment, make it scalable, and streamline compliance.
- Be the “bad guy.” Hunt for threats proactively by applying penetration testing, ethical hacking, and fuzz testing. Stress-test and improve your systems before attackers have a chance to exploit them.
Now let’s move on to SOC Prime’s juiciest custom detections for the Initial Access tactic. Our team hand-picked the most recent Sigma rules that are worth exploring right now.
Drive-by Compromise – T1189
DLL dropped to uncommon location (via file_event)
Exploit Public-Facing Application – T1190
Possible CVE-2022-29499 Exploitation Attempt (via webserver)
Possible successful WordPress user credential access using SQL injection (via proxy)
Hardcoded Password in Confluence Data Center/Server [CVE-2022-26138] (via proxy)
External Remote Services – T1133
Suspicious Add User to Remote Desktop Users Group
Phishing – T1566
Possible Malicious ISO Image with LNK (via audit)
Possible Phishing Related Web Browser Activity (via process_creation)
Supply Chain Compromise – T1195
Unusual SolarWinds Child Process (via cmdline)
Valid Accounts – T1078
Possible Domain Privilege Escalation [CVE-2022-26923] Exploitation (via audit)
Suspicious Creation Of A Root User Access Key (via cloudtrail)
Preventing Initial Access By Hackers
To establish a baseline security model for the prevention of initial access, organizations may refer to a CISA Alert AA22-137A. Long story short, it includes measures like
- Zero-trust access management policy
- Absence or multi-level protection of open RDP ports
- Role-based access control
- Restriction of admin access from a remote session
- Phishing-resistant MFA
- Alteration or disabling of vendor-supplied credentials
- Centralized log management
- Antivirus programs
- Threat detection and vulnerability scanning tools
- Asset & patch management
- Configuration management
Finally, knowing what’s popping on a cybercrime scene is essential for leveraging proactive cyber defense. Threat intelligence feeds can bring a lot of value if used to their highest potential. On a basic level, information like IOCs might be ingested into SIEM and/or machine learning tools and used for automated threat detection. On higher levels, intelligence firms monitoring dark web forums can help in making informed security choices.
When it comes to cybersecurity, it’s always good to have a preventive plan. However, attackers specifically seek to exploit overlooked vulnerabilities and hit hard when least expected. For situations like this, visit SOC Prime’s Cyber Threats Search Engine to instantly find actionable detection rules enriched by threat intelligence context and mapped to the MITRE ATT&CK framework.




