According to Accenture research, around 97% organizations experienced a surge in cyber threats since the onset of the russia-Ukraine war in 2022, highlighting the significant impact of geopolitical tensions on global businesses. State-sponsored hacking groups have been using Ukraine as a testing ground, broadening their attack strategies to target European and North American regions. For example, in October 2023, Russian APT28 (UAC-0001) targeted both public and private sectors in France, exploiting the same vulnerabilities and tactics observed in Ukraine during 2022-2023. Therefore, it is crucial for the international cybersecurity community to investigate attacks against organizations in Ukraine to stay ahead of the latest advancements in malicious toolkits that are being applied globally.
UAC-0180 Attack Description: Leveraging GLUEEGG, DROPCLUE, and ATERA to Target Ukrainian Defense Contractors
On July 17, 2024, CERT-UA issued an alert regarding the escalating malicious activity of the UAC-0180 group. This hacking collective has persistently targeted Ukrainian defense companies using a wide range of malware.
According to CERT-UA, threat actors frequently rely on the phishing vector to proceed with the intrusion. Specifically, hackers disseminate fraudulent emails themed around the UAV procurement to trick victims into opening an attached ZIP file containing a PDF document. In case unsuspecting users follow one of the malicious URLs within the PDF, it triggers the “adobe_acrobat_fonts_pack.exe” turning out to be GLUEEGG malware payload. GLUEEGG’s primary function is to decrypt and execute DROPCLUE loader which in turn drops “UA-2024-07-04-010019-a-open.pdf” and “font-pack-pdf-windows-64-bit” EXE file onto the targeted device. This further initiates the execution of a BAT file that uses standard “curl.exe” utility to install the MSI file of the legitimate remote management software ATERA.
Despite the wide geography of UAC-0180’s attacks, these threat actors relentlessly attempt to gain unauthorized access to the networks of Ukrainian defense contractors and the Defense Forces of Ukraine. The adversaries utilize an evolving arsenal of malware developed in multiple programming languages, including C (ACROBAIT), Rust (ROSEBLOOM, ROSETHORN), Go (GLUEEGG), and Lua (DROPCLUE). Furthermore, PDF documents with malicious links are often employed in the initial infection stage.
Detecting UAC-0180 Malicious Activity Covered in CERT-UA#10375 Alert
The ever-increasing number of cyber-attacks against the Ukrainian public and private sectors requires ultra-responsiveness from cyber defenders to identify and mitigate potential threats proactively. SOC Prime Platform empowers security teams with advanced and cost-effective threat detection tools to boost cyber defense capabilities and maximize the value of SOC investments.
To detect UAC-0180 attacks at the earliest stages, the SOC Prime Platform provides a comprehensive collection of curated detections, enriched with detailed cyber threat intelligence and mapped to the MITRE ATT&CK® framework. These detection algorithms can be effortlessly converted into various SIEM, EDR, and Data Lake formats, with automated conversion support provided.
Each detection rule is tagged with relevant identifiers linked to specific groups and alerts, such as “CERT-UA#10375” and “UAC-0180”. This tagging system allows users to efficiently filter and search content based on their needs. To explore the full set of detection rules related to the UAC-0180 campaign against Ukrainian defense contractors, click the “Explore Detections” button below.
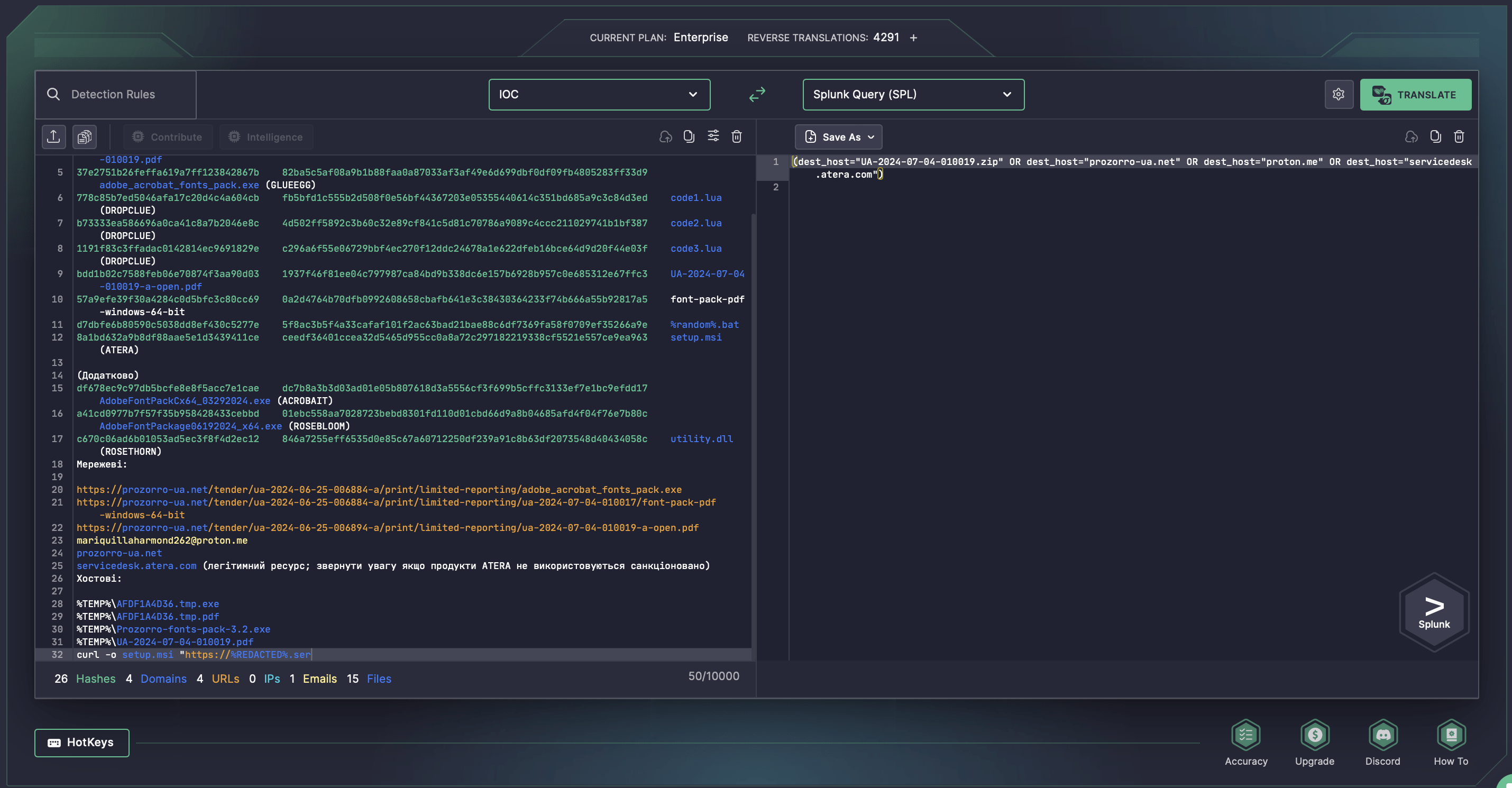
Security professionals are also welcome to take advantage of Uncoder AI, SOC Prime’s IDE for detection engineering, to accelerate threat research with instant IOC query generation based on indicators of compromise suggested in the latest CERT-UA alerts.
MITRE ATT&CK Context
Leveraging MITRE ATT&CK provides granular visibility into the context of the latest offensive operation attributed to UAC-0180 and covered by CERT-UA research. Explore the table below to see the full list of dedicated Sigma rules addressing the corresponding ATT&CK tactics, techniques, and sub-techniques. Tactics Techniques Sigma Rule Execution Command and Scripting Interpreter (T1059) User Execution: Malicious File (T1204.002) Defense Evasion System Binary Proxy Execution: Msiexec (T1218.007) Command and Control Application Layer Protocol: Web Protocols (T1071.001) Ingress Tool Transfer (T1105) Remote Access Software (T1219)




