CERT-UA researchers notify defenders of the persistent malicious campaign impacting more than 11 telecom providers. The UAC-0165 group behind these destructive attacks has been targeting the Ukrainian telecom sector for a period of over 5 months aiming to cripple the critical infrastructure, which fuels the need for thorough research among defenders to preempt potential threats.
UAC-0165 Attack Analysis Targeting Telecom
On October 15, 2023, a newly released security alert CERT-UA#7627 warned industry peers of the long-running campaign against Ukraine with the telecom providers being the target of destructive cyber attacks. Cybercriminals tracked as UAC-0165 are behind intrusions in the information communication systems of at least 11 providers leading to service disruptions for the telecom consumers. Collaboration with one of the compromised telecom providers enabled CERT-UA researchers to gain insight into the incident, identify the common attacker TTPs, and thoroughly investigate offensive intentions to prevent further intrusions in the telecom sector.
At the initial attack stage, UAC-0165 scans the provider’s subnetworks using a common set of network ports backed by the Masscan utility. Once attackers identify management interfaces, like SSH or RDP, provided that access to them is not restricted, they attempt authentication. Adversaries also look for vulnerabilities and exploit them once revealed. Further on, UAC-0165 actors analyze publicly accessible services, like web applications, such as billing, personal user accounts, and hosting servers, by leveraging ffuf, DirBuster, gowitness, nmap, and other scanning utilities.
Notably, UAC-0165 performs reconnaissance and exploitation activities from previously compromised servers and applies proxy servers such as Dante, SOCKS5, etc., to route traffic through these nodes.
Researchers also point to a set of additional indicators of compromise, including the installation of a RAM module referred to as POEMGATE that allows adversaries to authenticate with a statically defined password. Moreover, the latter stores user credentials entered during authentication in an XOR-encoded format. Such backdoors are pre-installed to enable attackers to collect up-to-date admin authentication data over time. These credentials are often used to access other server and network equipment. To bypass the settings restricting the use of a command shell, the original files “/bin/false” and “/bin/nologin” are replaced with “bash.” UAC-0165 hackers also commonly remove the signs of unauthenticated access via the WHITECAT utility.
Additionally, a variant of the POSEIDON program may be installed on the server. Its functionality includes a full range of remote management tools. The persistence of POSEIDON is ensured by replacing or modifying the legitimate binary file, into which a program code is added, creating a thread with an argument “start_routine” in the form of the “RunMain” function, which is imported from the “libc.so” library.
In case the targeted telecom provider delivers hosting services, after the website compromise, a backdoor called Weevely may be deployed into the web server. If the server is within the provider’s network, hackers can take advantage of it to advance an attack on other elements within the DMZ or the local computing network.
Apart from specific utilities, adversaries gain persistent unauthorized access to the provider’s infrastructure through regular VPN accounts. This can be achieved if multi-factor authentication based on one-time codes from an app is missing. An obvious sign of VPN compromise is a connection from IP addresses of a TOR network and from VPN services, including those that are “classified” as Ukrainian. Hackers also can steal credentials to the official accounts in messengers along with the tokens for sending text messages.
At the final attack stage, threat actors attempt to disrupt active network and server equipment, as well as cripple data storage systems. This can be achieved by leveraging identical passwords and unrestricted access to the management interfaces of this equipment. Furthermore, the absence of backup copies of current configurations can have a negative impact on the ability to promptly restore the system functionality.
To remediate the threats associated with the UAC-0165 activity and boost cyber resilience, defenders strongly telecom providers to enable multi-factor authentication and follow the best security practices highlighted in the CERT-UA recommendations.
Detecting UAC-0165 Long-Lasting Campaign Targeting Ukrainian Critical Infrastructure
Russia-backed offensive counterparts continuously target Ukrainian organizations with the aim of disrupting the national online infrastructure and extending their proven malicious tactics to a wider range of global targets. To assist cyber defenders in the proactive detection of possible cyber attacks affiliated to russian threat actors, SOC Prime Platform for collective cyber defense offers a dedicated set of curated Sigma rules, including those specifically aimed at UAC-0165 attack detection.
Detection algorithms are filtered based on the group ID and the corresponding CERT-UA alert, allowing cybersecurity experts to search for the content by “CERT-UA#7627” or “UAC-0165” tags. All the related Sigma rules are aligned with MITRE ATT&CK® and can be automatically converted to 28 SIEM, EDR, XDR, or Data Lake platforms. Hit the Explore Detections button below to access the detection stack aimed at the latest UAC-0165 campaign against the Ukrainian telecom sector.
Also, you can dive into the extended detection content set covering UAC-0165 malicious activity.
SOC Prime’s Uncoder AI can also be used to hunt for relevant IOCs provided by CERT-UA by creating custom queries and automatically running them in your cloud environment. 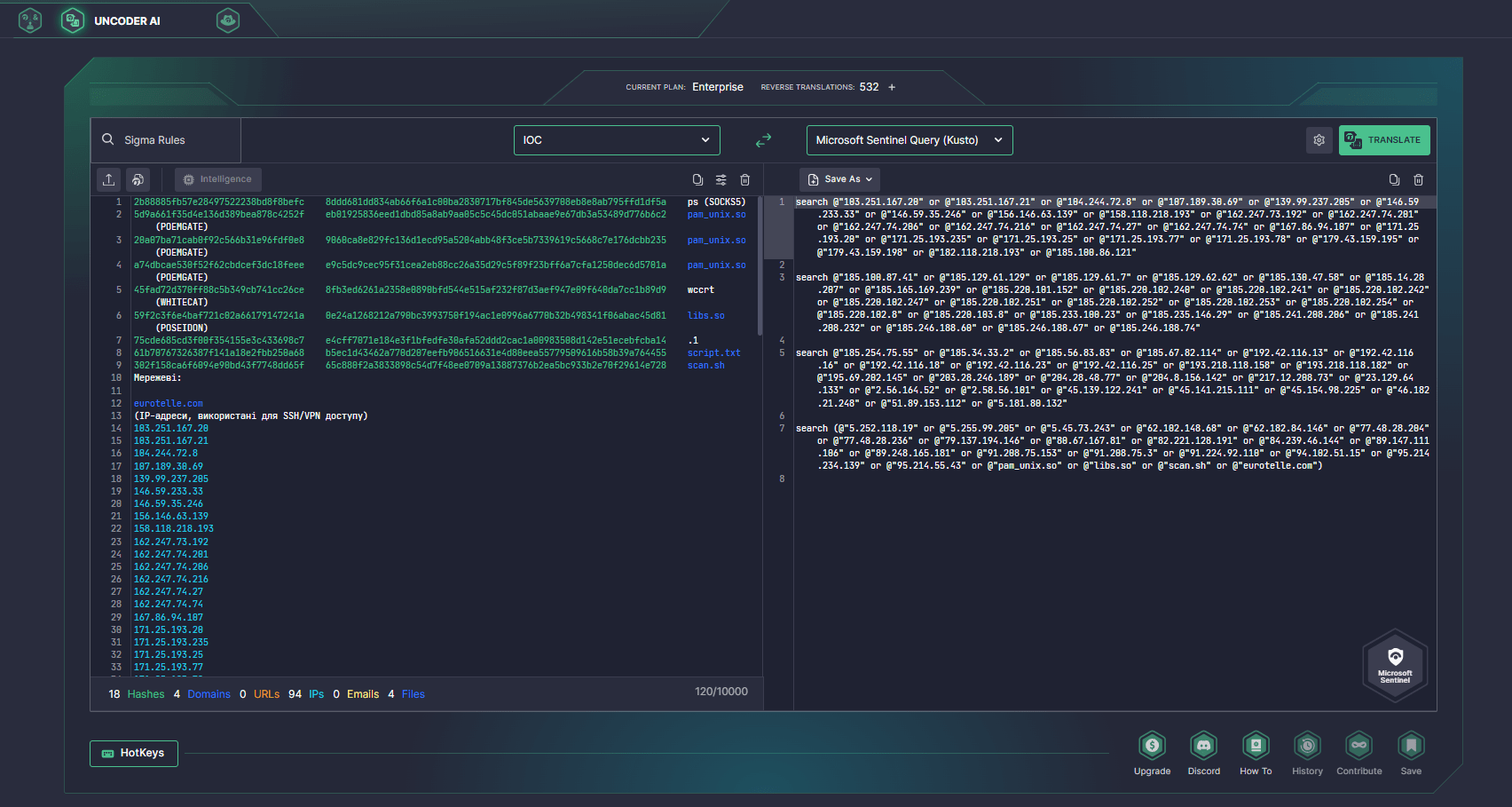
MITRE ATT&CK Context
SOC team members can also explore the attack details covered in the CERT-UA#7627 alert. Dive into the table below to find the list of all applicable adversary tactics, techniques, and sub-techniques linked to the above-mentioned Sigma rules for in-depth analysis:
Tactics | Techniques | Sigma Rule |
Execution | Command and Scripting Interpreter: Unix Shell (T1059.004) | |
Privilege Escalation | Exploitation for Privilege Escalation (T1068) | |
Defense Evasion | Abuse Elevation Control Mechanism (T1548) | |
Abuse Elevation Control Mechanism: Sudo and Sudo Caching (T1548.003) | ||
Hide Artifacts: Hidden Files and Directories (T1564.001) | ||
| Exploitation for Credential Access (T1212) | |
Modify Authentication Process: Pluggable Authentication Modules (T1556.003) | ||
Collection | Data from Local System (T1005) | |
Command and Control | Non-Application Layer Protocol (T1095) | |
Exfiltration | Exfiltration Over Web Service (T1567) |




