The nefarious hacking group UAC-0050, known for its persistent phishing attacks against Ukraine, has been observed massively distributing tax-related spoofed emails with PDF attachments imitating requests from the State Tax Service of Ukraine and exploiting a LITEMANAGER tool to gain unauthorized remote access to the targeted systems.
Detect UAC-0050 Phishing Attacks Covered in the CERT-UA#11776 Alert
The increasing volumes of financially motivated threats that use phishing as an attack vector and are tied to the russian UAC-0050 hacking group drive security teams to improve cybersecurity awareness and reinforce their organization’s defenses. To help thwart attacks by UAC-0050 leveraging LITEMANAGER for unauthorized remote access and covered in the latest CERT-UA#11776 research, SOC Prime Platform for collective cyber defense has curated a dedicated list of relevant detection algorithms.
Press the Explore Detections button to drill down to the full collection of relevant Sigma rules aligned with MITRE ATT&CK®, enriched with tailored CTI and operational metadata, and ready to deploy in the chosen language format compatible with 30+ SIEM, EDR, and Data Lake solutions.
With the growing numbers of cyber-espionage campaigns and financially motivated threats attributed to UAC-0050, security engineers might seek more detection content to safeguard their organization’s infrastructure against the group’s attacks. By directly searching Threat Detection Marketplace for relevant detections using the “UAC-0050” custom tag, security teams can enhance their proactive defenses against the group’s persistent activity.
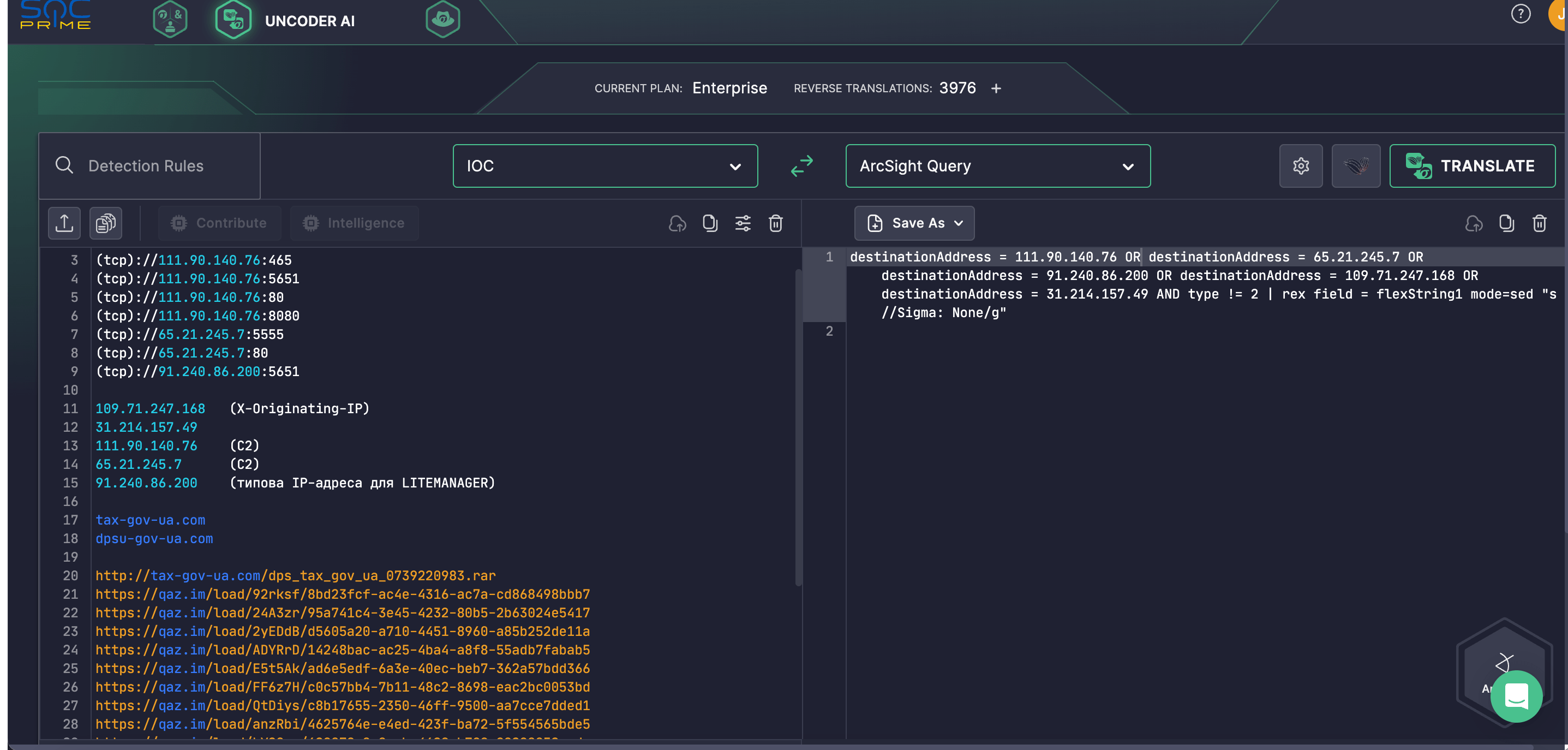
Security teams can also take advantage of Uncoder AI to accelerate IOC matching and hunt for IOCs related to the UAC-0050 threats from the relevant CERT-UA research. Uncoder AI enables automatically converting IOCs from any non-binary format into custom hunting queries matching your chosen SIEM or EDR format.
UAC-0050 Attack Description Using LITEMANAGER
CERT-UA researchers have been thoroughly monitoring the long-standing activity of the the russia-linked UAC-0050 group and recently issued deep-dive research highlighting three key areas of its offensive activity, including cyber espionage, financial theft, and disinformation operations known under the “Fire Cells Group” brand.
UAC-0050 is a Russia-linked hacking group active since 2020, mainly targeting the public sector in Ukraine and also extending its reach to the country’s allies. Adversaries use phishing campaigns to distribute malware like Remcos RAT, often impersonating Ukrainian government agencies in spoofed emails with malicious attachments. Notably, UAC-0050 has been largely weaponizing remote management tools, such as Remote Utilities software, in their campaigns against Ukraine.
The latest CERT-UA alert CERT-UA#11776 uncovered a large-scale distribution of tax-related phishing emails with PDF attachments masquerading the requests from the State Tax Service of Ukraine. The ongoing campaign is financially driven, primarily targeting company accountants who utilize remote banking systems. In some cases, as shown by computer forensic analyses, the time between initial infection and theft of funds can be less than an hour.
The weaponized attachments sent via the phishing attack vector contain links to file-sharing services (qaz.im, qaz.is, qaz.su), which, if followed, will download a malicious archive. The latter, with several nested levels, contains a password-protected archive called “Electronic Request for Tax Service Documents.pdf.rar,” which in turn goes with an SFX file named “Electronic Request for Tax Service Documents.pdf.exe.”
Opening the latter will display a decoy document and launch an MSI package of the LITEMANAGER remote management software on the computer, creating the technical conditions for covert remote access to the system.
Potential mitigation measures against UAC-0050 financially motivated attacks can involve configuring built-in operating system security measures and fully utilizing the authentication capabilties in banking information systems for authenticating accountant operations via one-time codes.
SOC Prime’s complete product suite for AI-powered detection engineering, automated threat hunting, and advanced threat detection equips security teams with a comprehensive solution for proactive defense to minimize the risks of financially motivated threats and data breaches.
MITRE ATT&CK Context
Leveraging MITRE ATT&CK gains detailed insight into the context of the latest UAC-0050 attacks exploiting LITEMANAGER. Refer to the table below to view the comprehensive set of dedicated Sigma rules addressing the corresponding ATT&CK tactics, techniques, and sub-techniques. Tactics Techniques Sigma Rule Initial Access Phishing: Spearphishing Attachment Execution User Execution: Malicious File (T1204.002) Defense Evasion Obfuscated Files or Information (T1027) Masquerading: Double File Extension (T1036.007) Command and Control Ingress Tool Transfer (T1105) Remote Access Software (T1219)




