In addition to the rising frequency of cyber attacks by the infamous UAC-0050 group targeting Ukraine, other hacking collectives are actively trying to infiltrate the systems and networks of Ukrainian organizations. At the turn of February 2024, defenders identified over 2,000 computers infected with DIRTYMOE (PURPLEFOX) malware as a result of a massive cyber attack against Ukraine. According to the investigation, the UAC-0027 hacking group is behind the latest malicious campaign.
UAC-0027 Attack Analysis
On January 31, 2023, CERT-UA issued a heads-up detailing the latest cyber attack against Ukraine involving the mass distribution of DIRTYMOE (PURPLEFOX) malware. As a result of in-depth research into the operational characteristics of the C2 server infrastructure, over 2,000 user instances within the Ukrainian Internet segment are affected throughout the offensive operation attributed to the UAC-0027 adversary activity.
To reduce the potential attack surface, defenders recommend segregating computers with outdated operating systems via VLAN and/or physical segmentation into separate network segments with mandatory filtering of both inbound and outbound information flows.
DIRTYMOE, also known as PURPLEFOX (or Purple Fox), is modular malware that has been in the spotlight in the cyber threat arena for over half a decade. It is used for establishing remote access to the targeted system and is primarily applied for launching DDoS attacks and cryptocurrency mining. Typically, the initial infection occurs due to launching popular software containing an MSI installer. The DIRTYMOE backdoor is equipped with a rootkit that prevents the removal of components from the file system and the operating system registry in normal mode.
DIRTYMOE is self-propagating malware that can spread via brute-forcing of authentication credentials or vulnerability exploitation. To ensure resilience for communication with the C2 infrastructure, at least three methods are used, one of which involves obtaining A-record values for statically defined domain names using both local and external DNS servers. Moreover, the IP addresses stored in the operating system registry, as well as those obtained from DNS queries, are obfuscated.
During the ongoing investigation, defenders have identified 486 IP addresses of intermediate control servers, the majority of which belong to compromised equipment located in China, with up to 20 new IP addresses being added on a daily basis.
CERT-UA recommends taking the following steps to detect potential signs of infection:
- Network Connections Investigation
Examine network connections based on the list of IP addresses provided in the CERT-UA research. Typically, outbound connections are made on “high” (10,000+) network ports.
- Registry Check Using regedit.exe
Use the standard utility regedit.exe to check values in the operating system registry under the following keys:
For Windows XP: HKEY_LOCAL_MACHINE\ControlSet001\Services\AC0[0-9]
For Windows 7: HKEY_LOCAL_MACHINE\Software\Microsoft\DirectPlay8\Direct3D
- Event Viewer Analysis
Leverage the standard Event Viewer utility in the “Application” log (source: “MsiInstaller”) to investigate entries with event IDs 1040 and 1042.
- “C:\Program Files” Directory Analysis
Check the “C:\Program Files” directory for the presence of folders with arbitrarily generated names, for example, “C:\Program Files\dvhvA.”
- Persistent Execution Check
Check for the persistence of the malicious program by examining the service generation. Additionally, the files of the backdoor and modules are stored in the standard directories provided below. However, using a rootkit impedes the detection and/or removal of the malware directly from the compromised computer.
HKEY_LOCAL_MACHINE\System\ControlSet001\services\MsXXXXXXXXApp
C:\Windows\System32\MsXXXXXXXXApp.dll
C:\Windows\AppPatch\DBXXXXXXXXMK.sdb
C:\Windows\AppPatch\RCXXXXXXXXMS.sdb
C:\Windows\AppPatch\TKXXXXXXXXMS.sdb
To remediate the threat, CERT-UA suggests applying at least one of the following methods:
- Download the software product “Avast Free Antivirus” from the official manufacturer’s website, install it on the computer, and initiate scanning in “SMART” mode. This process will require a subsequent computer reboot followed by proceeding with the scanning process, during which modules will be detected and removed.
- Download the affected computer from LiveUSB (or connect the hard drive of the affected computer to another computer) and manually delete the file “MsXXXXXXXXApp.dll” and “.sdb” modules. Afterward, boot the computer in normal mode and remove the service from the registry.
Notably, in any case, to prevent the subsequent infection through the backdoor’s self-propagating capabilities, it is required to enable the built-in firewall of the operating system (“Firewall”) before performing any of the actions listed above. Additionally, create a rule to block inbound information flows on the specific network ports, including 135, 137, 139, and 445.
Detect UAC-0027 Attacks Leveraging DIRTYMOE (PURPLEFOX) Malware
The emergence of the UAC-0027 group in the Ukrainian cyber threat landscape requires ultra-responsiveness from defenders due to the group’s successful attempts to compromise over 2,000 devices throughout the ongoing offensive operation. SOC Prime Platform equips security teams with a wealth of vendor-agnostic detection algorithms to foster proactive cyber defense against UAC-0027 adversary activity leveraging DIRTYMOE (PURPLEFOX) malware samples. Log in to the Platform and follow the link below to reach the entire collection of Sigma rules filtered by the group-related tag “UAC-0027” to detect the most recent attacks covered in the CERT-UA alert.
Sigma rules to detect UAC-0027 attacks using DIRTYMOE (PURPLEFOX) malware
The detection stack is mapped to MITRE ATT&CK® and can be used across dozens of security analytics platforms to assist defenders in their daily Detection Engineering procedures.
Security engineers can also rely on Uncoder IO to automatically package threat intel from the dedicated CERT-UA report into custom IOC queries tailored for multiple SIEM and EDR environments for simplified threat investigation.
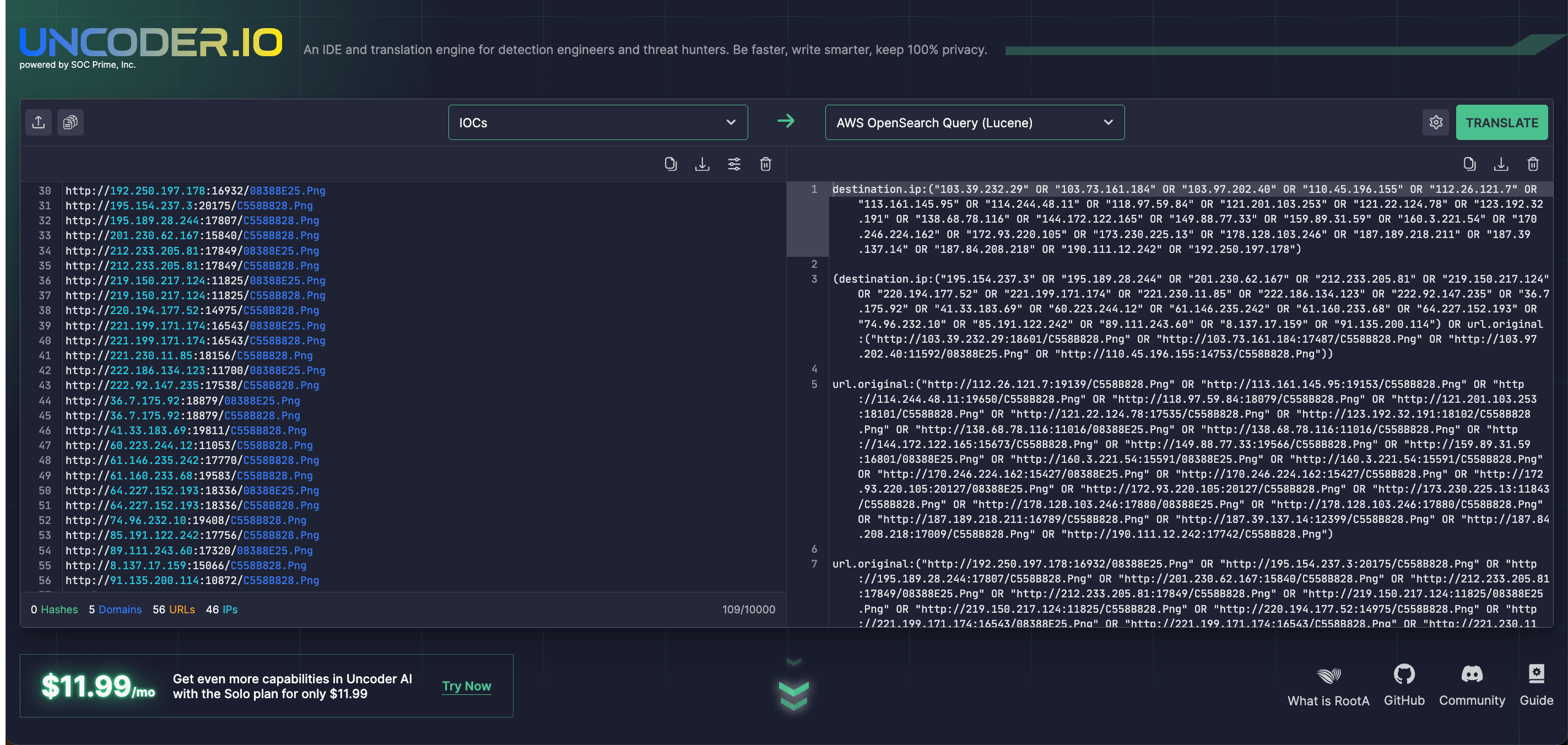
To proactively defend against any kinds of attacks that rely on the use of DIRTYMOE (PURPLEFOX) malicious samples, cybersecurity professionals can also take advantage of more detection algorithms from the world’s largest SOC content library. Click the Explore Detections button below to obtain Sigma rules for DIRTYMOE (PURPLEFOX) detection, with all pieces of content enriched with CTI and relevant metadata.
MITRE ATT&CK Context
Security engineers can also check out the UAC-0027 attack details provided in the most recent CERT-UA alert. Explore the table below to access a comprehensive list of adversary TTPs linked to the relevant Sigma rules, facilitating a thorough analysis:




