UAC-0006 Attack Detection: Overview of the Financially Motivated Group’s Campaigns Based on CERT-UA Research

Table of contents:
The infamous hacking group known as UAC-0006 has been launching offensive operations against Ukraine since 2013 primarily driven by financial gain. CERT-UA researchers recently issued a compiled overview of the group’s adversary activity aimed at raising cybersecurity awareness and minimizing risks. The group is notorious for committing financial theft by leveraging malware like SmokeLoader to withdraw money from the accounts of Ukrainian enterprises. Being the top financially motivated hacking collective in the Ukrainian cyber threat landscape, UAC-0006 requires immediate attention from defenders.
UAC-0006 Attack Analysis Based on CERT-UA Research
At the turn of December 2023, CERT-UA released an in-depth overview of the long-lasting cyber attacks by the UAC-0006 group that attempted to commit financial crimes with amounts reaching up to one million hryvnias per week.
In 2023, UAC-0006 was observed behind a series of attacks against Ukraine. For instance, in October 2023, UAC-0006 launched at least four cyber attacks targeting Ukrainian organizations. Attackers employed again the phishing attack vector and used an offensive toolkit similar to the one they leveraged in July
CERT-UA states that the current cybersecurity posture of Ukrainian organizations still requires significant effort to enhance the level of protection for the automated workstations of accountants. The vulnerability of such computers can potentially lead to significant financial losses due to cybercriminal activity.
Unauthorized access and subsequent adversary control of compromised systems are carried out by weaponizing at least 13 malware strains and utilities, including SmokeLoader (SMOKELOADER), RedLine Stealer (REDLINESTEALER), DanaBot (DANABOT), Lumma Stealer (LUMMASTEALER), etc.
The infection chain commonly starts with the initial system compromise and the delivery of SmokeLoader malware. Attackers leverage the latter to download and execute other programs and modules on the targeted computer. Despite the precision of phishing campaigns, primarily targeting accountants, hackers commonly identify “accounting” computers via TALESHOT. This involves analyzing window and program process names running on the computer and regularly sending screenshots to the adversaries. If a targeted computer arrests the adversary’s attention (based on the name of the financial institution, account balance, etc.), a software bundle consisting of RMS, LOADERX3, and RDPWRAPPER is downloaded onto the system. This enables hackers to interactively access the remote desktop in a concealed mode simultaneously with the legitimate user, providing attackers with a detailed analysis of a potential victim.
Further on, hackers attempt to prepare a chain for money withdrawal, like identifying intermediary fake firms. In certain cases, an operator can either independently initiate an unauthorized payment or modify the account details in a document already prepared and sent for the director’s signature. After sending the payment document to the bank, attackers try to mask their intrusion or gain time by disabling the computer via specialized software, like HANGTHREAD. The latter is used to launch a DoS attack, depleting computational resources and causing consistent system hangs or freezes.
Part of the UAC-0006 group responsible for receiving the stolen money may communicate with bank employees by providing them with misinformation, including fake documents that certify the legitimacy of the payments.
Since the accountant’s workstation involves processing a large volume of incoming emails and interaction with multiple information systems, it’s highly critical to proactively safeguard their computers against intrusions and reduce potential attack vectors.
To minimize the risks, computers used by accountants require the implementation of specific cybersecurity measures, like restricting the execution of files and scripts by applying a “whitelist” approach through the use of Software Restriction Policies (SRP) or AppLocker.
Detect UAC-0006 Attacks Against Ukraine
With the increasing volumes of financially motivated cyber attacks primarily targeting Ukrainian accountants and attributed to the UAC-0006 group, defenders are striving to supercharge their cyber resilience and increase cybersecurity awareness. SOC Prime Platform provides organizations with a comprehensive list of detection content against UAC-0006 offensive operations.
Click Explore Detections to reach the full collection of Sigma rules for UAC-0006 attack detection. Explore relevant metadata and dive into adversary TTPs for streamlined attack attribution. Defenders can also automatically convert detection code into multiple cybersecurity languages for streamlined cross-platform content translation.
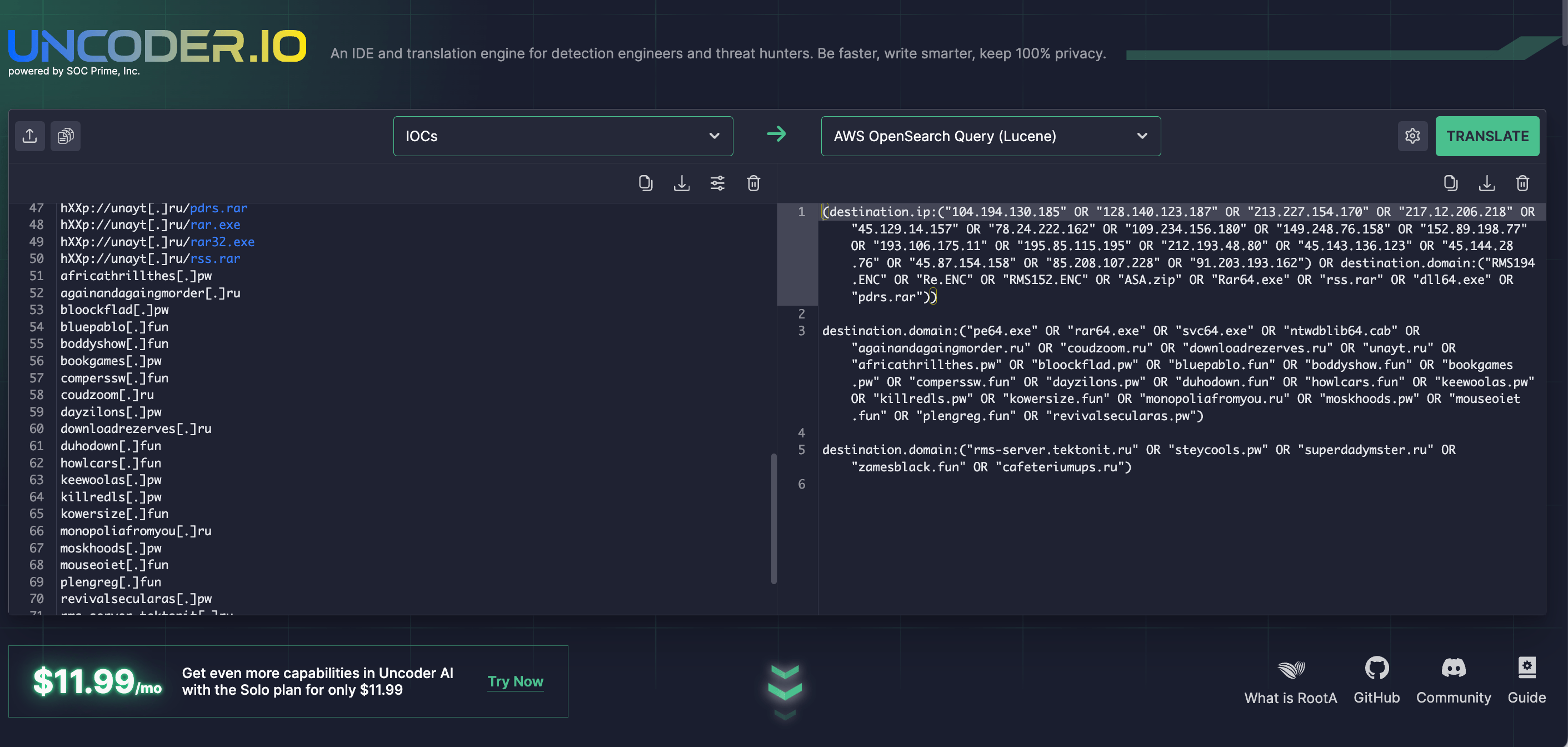
Also, leverage Uncoder IO as an open-source IOC packager to quickly parse IOCs covering the UAC-0006 activity from the latest CERT-UA alert and convert them into search queries ready to run in your environment.
MITRE ATT&CK® Context
To explore the in-depth context behind the latest cyber attacks launched by the UAC-0006 group, defenders can leverage the table below with the full list of relevant detection content mapped to ATT&CK and addressing adversary TTPs.
Tactics | Techniques | Sigma Rule |
Initial Access | Phishing: Spearphishing Attachment | |
Phishing: Spearphishing Link (T1566.002) | ||
Execution | Exploitation for Client Execution (T1203) | |
User Execution: Malicious File (T1204.002) | ||
Command and Scripting Interpreter (T1059) | ||
Command and Scripting Interpreter: PowerShell (T1059.001) | ||
Command and Scripting Interpreter: Windows Command Shell (T1059.003) | ||
Command and Scripting Interpreter: Visual Basic (T1059.005) | ||
Command and Scripting Interpreter: JavaScript (T1059.007) | ||
| Masquerading (T1036) | |
Masquerading: Match Legitimate Name or Location (T1036.005) | ||
Masquerading: Double File Extension (T1036.007) | ||
Masquerading: Masquerading File Type (T1036.008) | ||
Subvert Trust Controls: Mark-of-the-Web Bypass (T1553.005) | ||
Obfuscated Files or Information (T1027) | ||
System Script Proxy Execution (T1216) | ||
System Binary Proxy Execution (T1218) | ||
Process Injection: Process Hollowing (T1055.012) | ||
Hide Artifacts: Hidden Window (T1564.003) | ||
Command and Control | Application Layer Protocol: DNS (T1071.004) | |
Ingress Tool Trasfer (T1105) |