Proactive ransomware detection remains one of the top priorities for defenders, marked by a rise in intrusion complexity and continuously increasing high-profile ransomware attacks. FBI and CISA notify defenders of the growing volumes of cyber attacks spreading Snatch ransomware. Snatch ransomware operators have been in the limelight in the cyber threat landscape for about five years, constantly upgrading their TTPs to make the most of the latest trends in the cybercriminal arena and experimenting with multiple ransomware variants leveraged in other malicious campaigns.
Snatch Ransomware Detection
The ongoing ransomware attacks by Snatch threat actors covered in the latest AA23-263A alert encourage cyber defenders to proactively detect potential adversary activity while boosting their cyber resilience. SOC Prime Platform offers a curated list of Sigma rules for Snatch ransomware detection directly related to the offensive operations listed in the AA23-263A alert. Follow the link below to drill down to the entire collection of relevant Sigma rules filtered by the corresponding “AA23-263A” tag:
Environment Variables in Command Line Arguments (via cmdline)
Possible Manual Service Install for Persistence (via cmdline)
Possible Windows Save Mode Abuse (via registry_event)
Shutdown Used For Forcing a System Halt or Reboot (via cmdline)
Suspicious Svchost Processes (via process_creation)
Possible Windows Save Mode Abuse (via cmdline)
Suspicious Bcdedit Execution (via cmdline)
Suspicious VSSADMIN Activity (via cmdline)
All detection algorithms are aligned with the MITRE ATT&CK framework, enriched with tailored intelligence, and are automatically converted to industry-leading cloud and on-prem language formats.
Progressive organizations aimed to continuously improve their cybersecurity posture are also welcome to explore the entire collection of Sigma rules for Snatch ransomware attack detection, covering the group’s offensive operations over a couple of years. Click the Explore Detections button to reach relevant SOC content and dive into CTI linked to them.
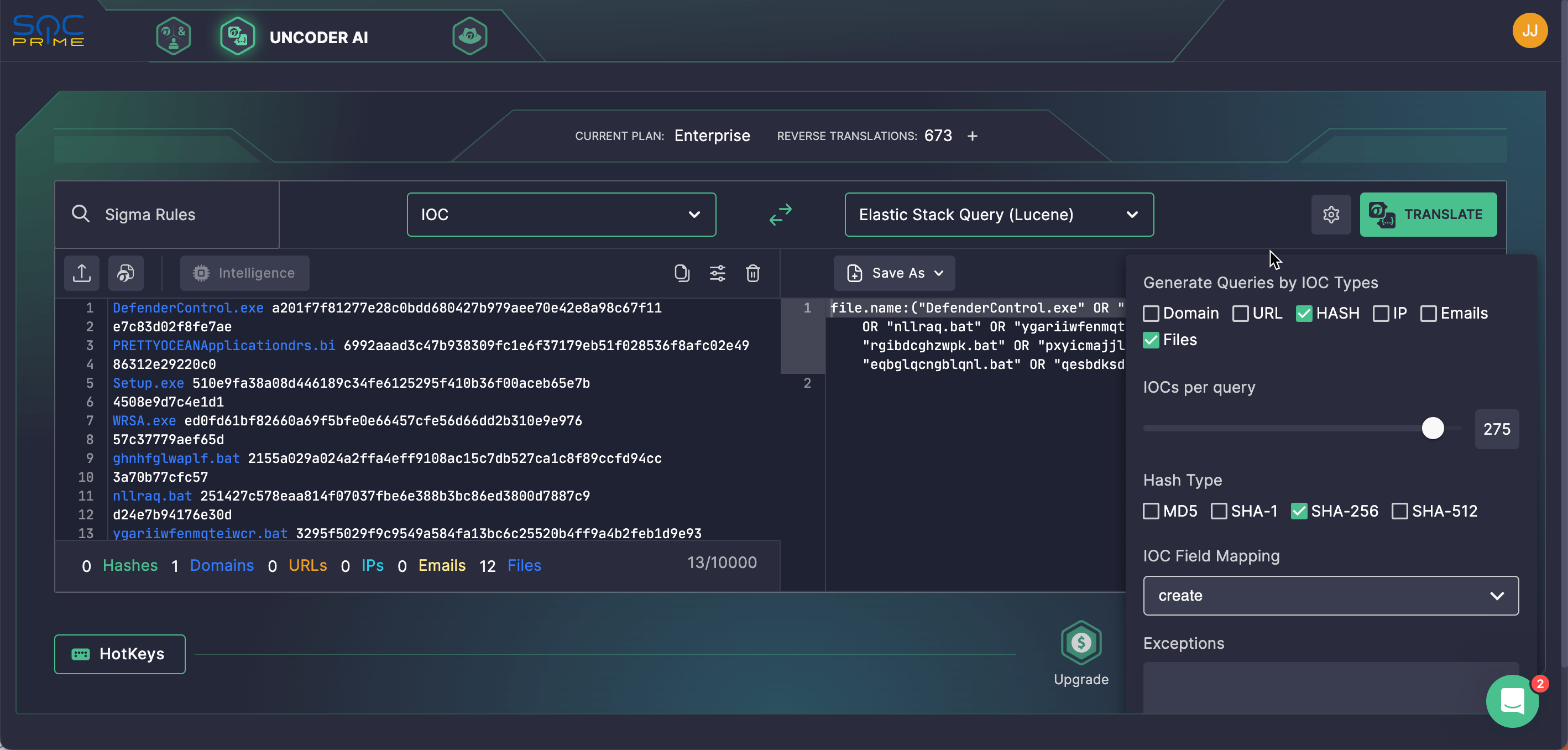
Security engineers can also hunt for Snatch IOCs obtained via FBI research and provided in the joint CSA. Leverage Uncoder AI to auto-parse file, domain, and other related IOCs into performance-optimized search queries that can be instantly run in your environment.
Snatch Ransomware Description
On September 20, 2023, FBI and CISA issued a joint cybersecurity advisory warning the global cyber defender community of the increasing risks of Snatch ransomware distribution.
The hacking group linked to this malicious activity emerged in the cyber threat arena in 2018, with the first victims of Snatch ransomware attacks being the U.S. organization. Initially, the hacking collective was known as “Team Truniger,” based on the moniker given to one of its leaders, who had previously worked as an associate of the GandCrab RaaS. Snatch ransomware operators apply a tailored ransomware iteration that stands out for its ability to reboot devices into Safe Mode. This allows ransomware to evade detection, proceeding to encrypt files when only a limited number of services are active.
Since mid-2021, adversaries leveraging the RaaS business model have continuously advanced their adversary toolkit and the scope of attacks targeting multiple industry sectors. Cybersecurity researchers have been monitoring the latest surge in the Snatch ransomware attacks since early summer 2023.
Snatch threat actors target multiple industry vectors, including the Defense Industrial Base, Food and Agriculture, and IT domains, striving to cripple the critical infrastructure. Adversaries tend to exfiltrate data and demand ransom from targeted users by threatening them to publish the compromised data on the group’s extortion blog also leveraging the leaked data associated with other ransomware affiliates, like Nokoyawa and Conti.
Adversaries employ multiple tactics to access and maintain their presence within a victim’s network, such as weaponizing security bugs in Remote Desktop Protocol (RDP), leveraging brute force, and acquiring admin credentials to gain initial access to the targeted networks. To maintain persistence within a compromised environment, hackers abuse administrator accounts and establish a connection with a C2 russia-affiliated server via port 443.
Snatch ransomware affiliates leverage multiple attacker TTPs, including data discovery, lateral movement, and data exfiltration. They employ a set of software utilities to perform their malicious operations, like the “sc.exe” tool via the Windows Command line to configure and manage system services, along with Metasploit and Cobalt Strike.
At the initial stages of ransomware deployment, Snatch threat actors take steps to disable security protection to evade detection and run the malicious executable file to drop ransomware. Once executed, the Snatch ransomware modifies registry keys, applies various built-in Windows tools to gather information about the system, identifies running processes, and creates benign processes for launching Windows batch files. After executing those BAT files, adversaries remove them from the impacted system. Snatch hackers commonly communicate with their victims via email and the Tox platform, using IDs provided in ransom notes or through their extortion blog.
To lower the chances of the Snatch ransomware intrusions, defenders urge organizations to follow the mitigation guidelines provided in the latest joint advisory, including closely monitoring the Remote Desktop Protocol activity, securing data backups, enabling multi-factor authentication against phishing attacks in addition to other best security practices.
Search SOC Prime to equip your team with over 800 detection algorithms against current and existing ransomware attacks to timely identify malicious cyber activity and safeguard your organization backed by collective industry expertise.
MITRE ATT&CK Context
To streamline threat hunting procedures and obtain additional context on Snatch ransomware attacks, dive into the table below listing associated ATT&CK tactics, techniques, and sub-techniques:
Tactics | Techniques | Sigma Rule |
Execution | Command and Scripting Interpreter (T1059) | |
System Services: Service Execution (T1569.002) | ||
Defense Evasion | Masquerading: Masquerade Task or Service (T1036.004) | |
Impair Defenses: Safe Mode Boot (T1562.009) | ||
Credential Access | OS Credential Dumping: NTDS (T1003.003) | |
Impact | System Shutdown/Reboot (T1529) | |
Inhibit System Recovery (T1490) | ||




