The state-sponsored russia-linked Gamaredon (aka Hive0051, UAC-0010, Armageddon APT) hacking collective comes to the spotlight launching a new wave of cyber attacks. Adversaries have been observed leveraging new iterations of Gamma malware, adopting DNS Fluxing to drop the malicious strains and leading to 1,000+ infections per day. The infection chain displays a novel, aggressive, multi-layered adversary approach for rapidly deploying multiple independent malware branches.
Detecting Hive0051 (aka UAC-0010, Gamaredon APT) Latest Attacks
Hive0051, aka Gamaredon, also identified as UAC-0010, remains one of the most prominent russia-backed advanced persistent threats in the international cyber arena, being specifically active on the Ukrainian cyber frontline. Notably, the malicious methods applied against Ukrainian organizations are systematically polished and further extrapolated to a broader range of international targets of interest for the Moscow government.
To help organizations spot the malicious activity associated with the latest Hive0051 attacks, SOC Prime Platform for collective cyber defense offers a set of curated detection content addressing relevant adversaries’ TTPs. All the rules are compatible with 28 SIEM, EDR, and Data Lake solutions, mapped to the MITRE ATT&CK® framework and enriched with extensive threat intelligence to smooth out threat investigation. Just hit the Explore Detections button below and immediately drill down to a relevant detection stack.
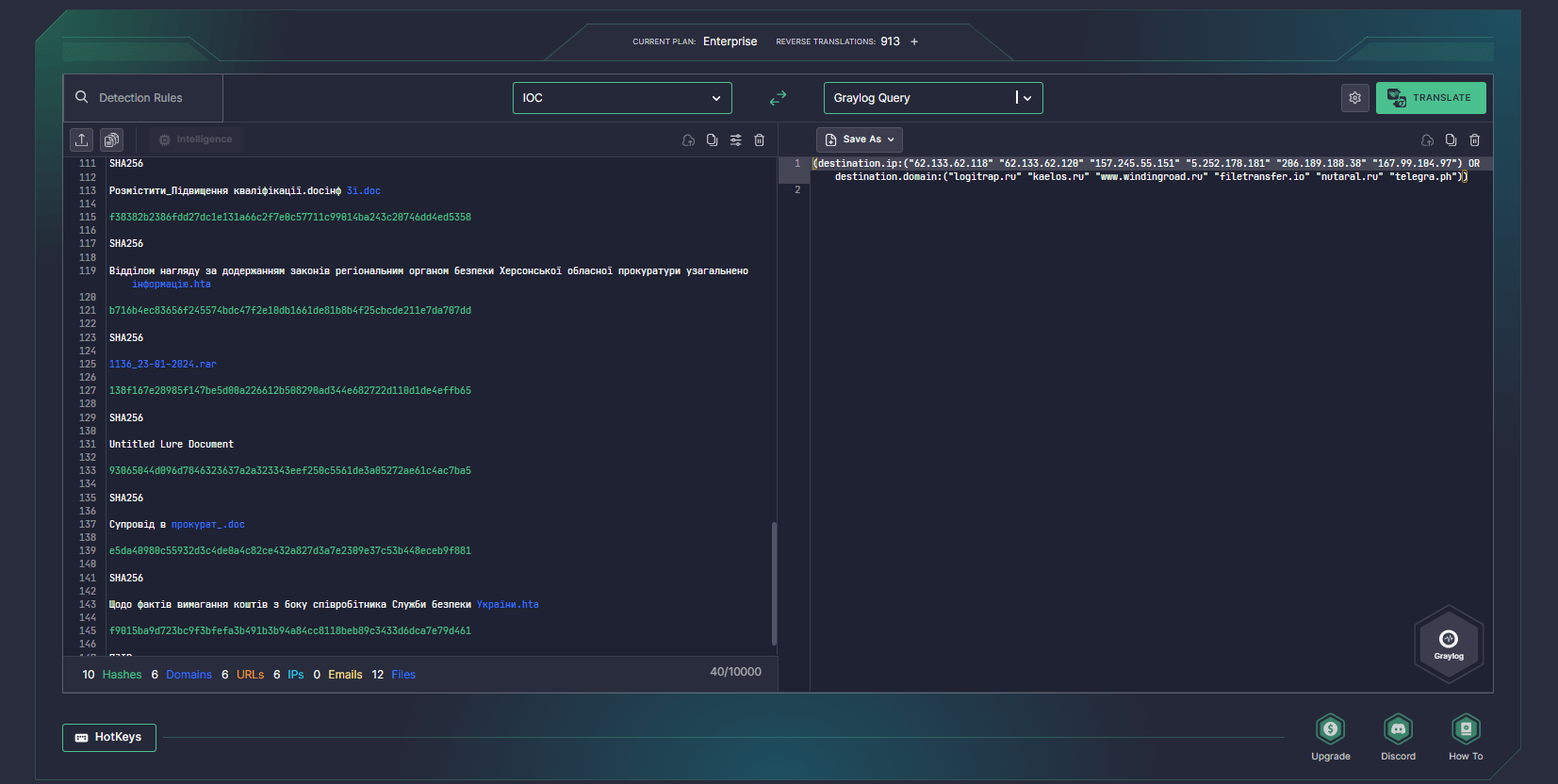
Also, to proceed with the investigation, security professionals might launch instant hunts using IoCs provided in the corresponding IBM X-Force research. Rely on SOC Prime’s Uncoder AI to create custom IoC-based queries in a matter of seconds and automatically work with them in your chosen SIEM or EDR environment.
To obtain additional context on Hive0051 attacks and retrospectively analyze adversary TTPs, security experts might explore a set of relevant writeups in SOC Prime’s blog to explore the ATT&CK references, relevant content packs, and research details.
Hive0051 (aka Gamaredon APT) Attack Analysis
The nefarious russia-linked cyber-espionage Gamaredon Group also known as Armageddon APT (Hive0051 or UAC-0010), has been observed behind a series of cyber attacks targeting Ukraine since the onset of the global cyber war.
IBM X-Force researchers have been tracking a surge in Hive0051 activity since mid-fall 2023. In a series of ongoing attacks, the APT group has been experimenting with novel Gamma malware variants.
Notably, Gamaredon launched multiple phishing attacks against Ukraine in 2022, employing diverse GammaLoad versions, including GammaLoad.PS1 delivered via the harmful VBScript code and an updated malware iteration tracked as GammaLoad.PS1_v2.
Based on the analysis of the lure samples, regional military, police, and civil government entities in Ukraine remain a primary target for Hive0051. Threat actors primarily collect intelligence on Ukrainian military capabilities, however, new security agreements and partners offering related training and financial support to Ukraine might be another area of adversary interest.
In the ongoing campaign spanning the period from November 2023 up to early March 2024, Gamaredon has displayed a highly sophisticated and aggressive infection approach, resulting in the emergence of three distinct malware branches and enabling near-real-time file exfiltration and hands-on keyboard access. Moreover, the investigation unveiled six Ukrainian-language lure documents predominantly targeting Ukrainian military and government training centers. Additionally, attackers rotate their C2 infrastructure through synchronized DNS fluxing across multiple channels, including Telegram, Telegraph, and Filetransfer.io. The group has also displayed expanding the scope and scale of attacks, having maintained several active C2 clusters associated with different malware while spanning hundreds of domains.
Researchers identify two primary infection chains leading to GammaLoad distribution. The first one leverages HTA files with harmful VBScript code to drop and load the main backdoor. Another commonly employed technique involves leveraging Office documents with remote templates to inject VBA macros, which leads to dropping the same VBScript-based backdoor.
After the malware successful run, it employs diverse, dynamic DNS resolution techniques to resolve the IP addresses of the targeted C2 servers. Notably, even a single successful execution of GammaLoad may lead to the distribution of multiple payloads in just a couple of minutes during intrusion. Researchers identified at least three separate malware branches, including GammaLoadPlus, GammaSteel, and GammaLoad.PS, immediately installed on a single impacted client, each equipped with independent C2 fallback channels, persistence mechanisms, file system artifacts, and objectives.
Amid the ongoing russia-Ukraine war, Gamardeon will highly likely prioritize gathering sensitive data concerning the strength, effectiveness, and combat capabilities of the Armed Forces of Ukraine while remaining a challenging cyber threat to the country and its allies. The group’s focus on increasing sophistication and evolving offensive capabilities underscores the need to continuously maintain cyber vigilance and upscale cyber defense capabilities. SOC Prime Platform for collective cyber defense provides a complete product suite for AI-powered Detection Engineering, automated threat hunting and detection stack validation, enabling organizations of any scale to proactively address emerging threats.




