CVE-2020-3452: Unauthenticated File Read in Cisco ASA & Cisco Firepower Detection

Table of contents:
Again, we go off the usual publication schedule due to the emergence of an exploit for the critical vulnerability CVE-2020-3452 in Cisco ASA & Cisco Firepower, as well as the emergence of rules for detecting exploitation of this vulnerability.
CVE-2020-3452 – one more headache in July
CVE-2020-3452 was discovered late last year, but it wasn’t disclosed until last week Cisco released an update to fix this vulnerability. The Security Advisory was published yesterday, and a few hours later the researcher released the first PoC exploit. The number of critical vulnerabilities discovered in July is disheartening: only IT security specialists managed to catch their breath after installing updates and/or detection content for CVE-2020-1350 (SIGRed), and a new threat is already on the doorstep. Usually, a few days or even hours pass between the publication of a proof-of-concept exploit and the beginning of exploitation by attackers.
CVE-2020-3452 vulnerability in the web services interface of Cisco ASA and Cisco Firepower allows unauthenticated remote attackers to conduct directory traversal attacks and read sensitive files on a targeted system. They could exploit this vulnerability by sending a crafted HTTP request containing directory traversal character sequences to an affected device. In case of success, attackers will be able to view arbitrary files within the web services file system on the targeted device.
At the time the first PoC exploit appeared, there were about 80,000 vulnerable devices in the world, and attacks began within 24 hours after the publication of the technical analysis. During these attacks, adversaries only read LUA source files, but potentially the vulnerability is much more dangerous, since cybercriminals can gain access to web cookies, partial web content, bookmarks, HTTP URLs, and WebVPN configuration.
Detection content
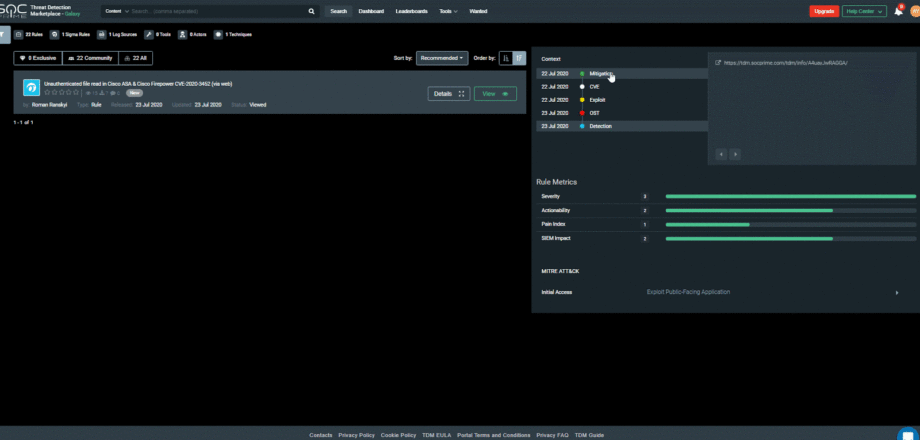
The new Threat Hunting rule developed by Roman Ranskyi to detect this vulnerability will help uncover threats to your organization until the necessary updates are installed: https://tdm.socprime.com/tdm/info/A4uayJwRAGGA/
The rule has translations for the following platforms:
SIEM: ArcSight, QRadar, Splunk, Graylog, Sumo Logic, ELK Stack, RSA NetWitness, Logpoint, Humio
EDR: Elastic Endpoint
NTA: Corelight
MITRE ATT&CK:
Tactics: Initial Access
Techniques: Exploit Public-Facing Application (T1190)
Update! Emir Erdogan released community rule that detects CVE-2020-3452 via web logs: https://tdm.socprime.com/tdm/info/1HGUIE7X8ZYj/iAAR2HMBQAH5UgbB9i-1/
Ready to try out SOC Prime TDM? Sign up for free. Or join Threat Bounty Program to craft your own content and share it with the TDM community.