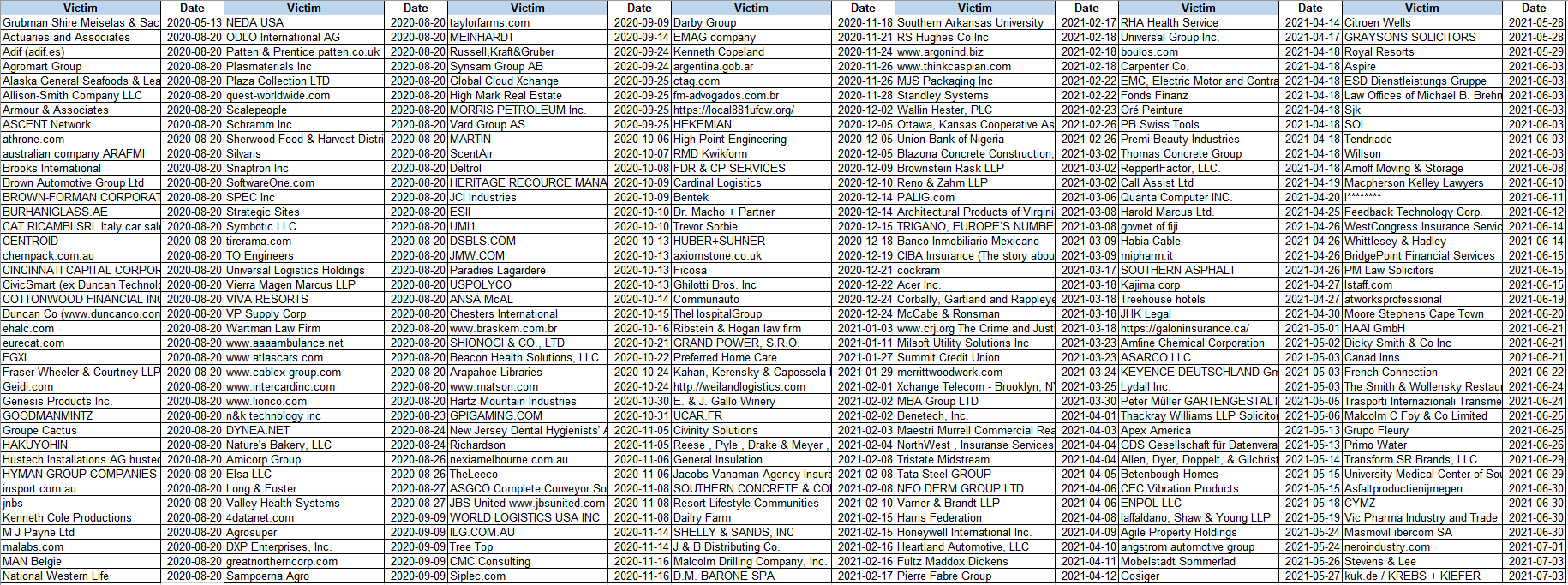
Hundreds of companies have been recently exposed to a massive supply chain attack on the software company Kaseya. A zero-day bug in Kaseya’s VSA software was nefariously leveraged by the REvil gang to infect 30 managed service providers (MSPs) and multiple their customers with ransomware.
Although the vendor has been aware of the vulnerability since July 2, 2021, Kaseya is still investigating the issue and about to release the official patch in the upcoming days. This minor delay allowed REvil threat actors to push the malicious upgrades on July 4, 2021, proceeding with intrusion while defenses are weakened due to the long weekend in the US.
Kaseya VSA Supply Chain Attack
According to Huntress, the initial indicators of compromise were traced on July 2 when the company’s Incident Response team was on alert due to a potential security incident involving Kaseya’s VSA software.
The researchers believe that REvil threat actors managed to exploit a zero-day vulnerability in Kaseya’s VSA servers to bypass authentication on the web panel and execute SQL commands on the appliance to deploy REvil payload to all connected clients. The customers received the malicious “VSA agent hotfix” pack that was able to overcome anti-virus protections by leveraging the old flawed version of the Microsoft Defender application.
Kaseya supply chain attack resulted in more than a million individual devices being encrypted and frozen out of operation, according to the update on the official REvil blog. Simultaneously, security experts were able to identify over 30 MSPs and over 1,000 businesses in the US, AUS, EU, and LATAM being infected.
According to the REvil statement, hackers plan to release a single decryptor for all victims in case hackers have $70,000,000 ransom paid in Bitcoins.
Actions Taken by the Global Cybersecurity Community
Immediately after the supply chain attack revelation, Kaseya took prompt action and started working on resolving the issue and restoring their customers to service backed by the community of third-party cybersecurity experts. The vendor instantly took preventive measures by shutting down the SaaS servers in order to protect their on-premise customers and strongly recommending to keep the hosted VSA servers offline until further notice, which was announced in the company’s Important Notice July 4th, 2021. On July 4, Kaseya introduced a new Compromise Detection Tool to enable checking the system for indicators of compromise (IoC). As soon as the incident broke out, the global cybersecurity community was engaged in active collaboration to help Kaseya withstand the attack and research the incident. Based on the technical analysis carried out by the Huntress researchers, adversaries appear to have exploited an SQLi vulnerability. Based on Update #12 from July 4 from the Huntress research, adversaries applied an authentication bypass to gain access to the compromised VSA servers, upload the original payload, and run commands using the SQL injection.
Kaseya Supply Chain Attack Detection
To help organizations proactively defend against this huge ransomware incident hitting numerous MSPs around the globe, SOC Prime Team together with Florian Roth have released dedicated Sigma rules. Download these SOC content items for free right from Threat Detection Marketplace:
This rule written by the SOC Prime Team detects possible SQLi exploitation attempts against Kaseya VSA and has translations to the following language formats:
SIEM & SECURITY ANALYTICS: Azure Sentinel, Chronicle Security, ArcSight, QRadar, Splunk, Sumo Logic, ELK Stack, LogPoint, Humio, RSA NetWitness, FireEye, Apache Kafka ksqlDB, Securonix
MITRE ATT&CK
Tactics: Initial Access
Techniques: Exploit Public-Facing Application (T1190)
This Sigma behavior-based detection from the GitHub repo owned by Florian Roth detects process command-line patterns and locations used by the REvil group engaged in the Kaseya mass MSP ransomware incident. Apart from this supply chain attack, this rule can also be applied to detect other similar malware.
This Sigma rule can be translated to the following language formats:
SIEM & SECURITY ANALYTICS: Azure Sentinel, Chronicle Security, ArcSight, QRadar, Splunk, Sumo Logic, ELK Stack, LogPoint, Humio, RSA NetWitness, FireEye, Sysmon, Apache Kafka ksqlDB, Securonix
EDR: Carbon Black, CrowdStrike, SentinelOne
MITRE ATT&CK
Actors: GOLD SOUTHFIELD
SOC Prime has recently released the Industry Guidelines: Defending Against Ransomware Attacks in 2021 covering best practices for ransomware defense and offering the latest detections against ransomware attacks to help the leading MSPs and organizations in various sectors proactively withstand industry-specific intrusions. Check out these Industry Guidelines to stay updated on the latest ransomware trends and strengthen the cyber defense capabilities of your organization’s SOC. Also, you can refer to our Sigma Rules Guide for beginners to enhance your threat hunting skills and start creating your detections to boost collaborative cyber defense against emerging threats.
Sign up for Threat Detection Marketplace to gain access to 100,000+ curated cross-tool detection and response algorithms tailored to the SIEM & XDR stack in use and aligned with MITRE ATT&CK methodology. Keen to engage in threat hunting activities and craft your own detection content? Join our first-ever Bounty Program and help make threat detection easier, faster, and simpler together!