Defending Against Ransomware Attacks in 2021

Table of contents:
The cybersecurity community is facing a crisis caused by the escalating threat of high-profile ransomware attacks. Advancing the trend of 2020, ransomware continues to be the number one problem in 2021, with the increasing sophistication of intrusions and a constantly growing number of malicious affiliates.
Big enterprises remain to be the primary target. Yet, the rates are rising, and starting from 2019, ransom payments show over 170% increase yearly, according to the 2021 Ransomware Report from Palo Alto Networks. Furthermore, the research conducted by Sophos shows that victims (32%) tend to pay the ransom despite really huge payout demands.
In these guidelines, we are going to take a deep dive into 2021 ransomware statistics, trace major trends, explore the Tactics, Techniques, and Procedures (TTPs) applied by ransomware collectives, summarize the best practices to defend against ransomware threat, and provide a batch of curated detections from SOC Prime to secure your organizational infrastructure:
Also, to learn about the ransomware trends of the last year, you can inspect our Detection as Code Innovation Report 2020, particularly the “Top 2020 Exploits & Threats” section.
2021 Ransomware Stats and Trends
The F.B.I. director Christopher A. Wray compares the ransomware menace to the problem of global terrorism in the days after the Sept. 11, 2001 attack. To get a better understanding of why ransomware became a critical challenge for security practitioners, let’s take a look at major trends in the 2020-2021 threat landscape.
Large Enterprises Are in Danger
Ransomware actors go after big money. They are less concerned about the industry while putting more effort to attack companies of larger scope and scale. The list of big-name ransomware victims includes the world-leading technology manufacturers (Acer, Quanta, Bombardier), top goods suppliers (JBS, Royal Shell), major educational institutions (Stanford University, University of California, University of Colorado), critical infrastructure vendors (Colonial Pipeline, Companhia Paranaense de Energia), global law firms (Jones Day), financial institutions (Travelex, Flagstar), insurance companies (AXA), healthcare institutions (Capital Medical Center, Bridgeway Senior Healthcare), and more. In fact, adversaries do simple math and expect to receive the biggest possible ransom from high-profile targets. Therefore, large companies are now constantly in danger since hackers are motivated by the successful extortion practice.
Sky-high Ransom Payouts
In 2021, the cybersecurity community observed a significant shift in ransom payouts compared to 2019-2020. Palo Alto Networks states that currently, the average ransom payment equals $312,493, while in 2019 it was $115,123. Hackers’ appetites are growing harshly. In 2019, the highest ransom demand was $15 million, while in 2020 it escalated to $30 million.
Despite growing ambitions, hackers frequently fulfill their financial cravings. Victims tend to pay enormous ransoms to get their data back and prevent data breaches. In March 2021, CNA Financial Corp. paid $40 million to regain control of its network after a ransomware attack. And in June 2021, the prominent meat supplier JBS paid an $11 million ransom to unfreeze its operations.
Double Extortion Is on the Rise
At the end of 2019, Maze RaaS affiliates began to steal sensitive data from the infected network before the encryption process. As a result, despite the ability to restore information from backups, victims were pushed to pay bigger sums to prevent the data leak. This approach set a very popular double extortion trend that was quickly adopted by most Ransomware-as-a-Service (RaaS) maintainers.
According to the analysis from Palo Alto Networks, NetWalker was the most prolific at applying the double extortion approach. During 2020-2021, this ransomware family leaked sensitive data for 113 organizations across the globe. RagnarLocker took second place, with 26 victims having their data compromised globally. Also, such prominent players as REvil and DarkSide widely adopt double extortion practices to increase possible gains.
RaaS Increase
To date, a very little number of threat actors proceed with individual ransomware campaigns. Most of the malicious affiliates are engaged in Ransomware-as-a-Service (RaaS) programs. RaaS allows even script kiddies to be involved in a big game by using the existing ransomware samples to carry out the attacks. As a result, RaaS has a monopoly in the malicious arena for its very simple execution and extreme profits.
For example, REvil maintainers adopted the RaaS program to engage new members and be able to apply a multi-extortion scheme. Now, they serve free of charge DDoS attacks and VoIP calls to media to its affiliates so they can exert further pressure on its victims. A similar pattern is used by the DarkSide RaaS ring as well as DoppelPaymer and NetWalker.
New OS Platforms
Adversaries are expanding their horizons while leaving less secure space for organizations globally. The year 2021 shows a tendency to target Linux systems alongside traditional Microsoft Windows and Apple macOS. For example, prolific DarkSide ransomware has the ability to deliver ELF binaries (Executable and Link Format) to attack data on Linux machines. Also, there are ransomware samples designed to target Linux devices exclusively, like Tycoon ransomware.
More Commodity Malware
Ransomware actors frequently utilize commodity malware to gain initial access to the targeted network and deliver the final payload. This trend only intensifies during 2021, with more developers being involved in the ransomware game. According to Group-IB inquiry, the most popular samples utilized by ransomware operators are Trickbot, Qakbot, Dridex, IcedID, Zloader, Buer, and Bazar.
Evoke of DDoS Attacks
Ransomware actors are constantly seeking new approaches to boost their profits. Last year, several ransomware families re-introduced the “good old” practice of launching distributed denial-of-service (DDoS) attacks against victims’ web resources to put additional pressure on them. Particularly, Avaddon and DarkSide ransomware operators launched DDoS attacks against victimized companies after they refused to cooperate during ransom negotiations.
Expanding Ransomware Ecosystem
Throughout the last years, ransomware became an organized crime. High-profile attacks usually involve an impressive number of affiliates supplying services to each other. For example, botnet maintainers and account resellers help ransomware actors to get initial access to the network. Collectives use this initial access to take control over the whole infrastructure and exfiltrate sensitive data. In some cases, this data is transferred to the team of Black Hat analysts who assess the financial status of the company, search for any security holes, and look for potentially incriminating data. Then, the ransomware actor purchases relevant ransomware software from dark web developers and contacts commodity malware maintainers to proceed with the intrusion. At least, 15 new ransomware affiliate programs occurred in 2020, including DarkSide, Phobos, Avaddon, and LockBit. And more strains are about to surface in the upcoming years.
APT Actors Involved in Big Ransomware Game
In 2020, prominent advanced persistent threat (APT) groups started to launch financially motivated campaigns. For example, Lazarus and APT27 were identified to use their malicious infrastructure for ransomware attacks. This means that the ransomware landscape is going to become even more sophisticated due to TTPs borrowed from state-sponsored collectives.
Ransomware Escalation: From Malware to e-Crime
Summarizing the trends described above, it becomes clear that Ransomware has already transformed into a sophisticated cybercrime business, with numerous players, subcontractors, supply chains, additional revenue streams, and of course, competitors fighting for the most prolific targets. As every mature market, the Ransomware business goes through the segmentation process so each player can take the proper niche and contribute to the overall “market” growth. Analyzing the skills, capacities, targets, and approaches of the ransomware maintainers, the SOC Prime Team can identify three major types of players in the current ransomware arena. Every segment has its strengths and limitations.
Mass-market Ransomware. As its title suggests, this type of threat prefers mass attacks instead of pinpoint strikes. Mass-market ransomware has the widest area of coverage and does not care much about the victim profile. The distribution and orchestration are automated in most cases, and the targets are standalone computers (home, corporate, public). In this case, threat actors rely on the density of attacks, which compensates for the low conversion from targeted machines into infected ones. Furthermore, as the victims are mostly individuals or small to middle-sized organizations, the ransom payouts per successful hit are rather modest and rewards for the attacks are moderate. Yet, mass-market ransomware requires low to medium investments to start the malicious business, which gains this segment a lot of dedicated affiliates.APT-like Ransomware. This niche of the Ransomware “market” is concentrated on highly targeted, complex, and sophisticated intrusions. Skilled and mature players thoroughly choose their victims, which are the world-leading businesses, high-profile government entities, or other big-name targets. Before launching the attacks, APT-like ransomware actors spend months investigating the financial status of the victim and weak points inside the targeted network. Such a thorough preparation allows reaching the highest possible infection/targeted conversion rate. Furthermore, the sum of payouts for the successful attack is impressive. However, to enter the APT-like ransomware segment, threat actors require medium to high investments, making the go-off a complex task. Therefore, the number of actors in this segment tends to be stable.
Ransomware-as-a-Service (RaaS). This segment involves cybercrime actors who serve as the “consumers” of the ransomware variants delivered by the ransomware developers. Similar to the Software-as-as-Service business model, ransomware deliverables are sold or leased to the adversaries who exploit them for targeted attacks.
Top Ransomware Families of 2021
The distinctions between the three major ransomware business actors are considerable, therefore, they cannot be compared directly. Let’s delve into each segment separately to make an overview of the most active collectives. The comparison made for mass-market ransomware families allows identifying Nefilim, DoppelPaymer, Avaddon, Defray777 as the most active actors in this segment. While exploring the APT-like ransomware division, SOC Prime experts identify Ryuk, REvil (Sodinokibi), DarkSide as the most notorious groups. Also, security researchers from Group-IB, Palo Alto Networks, and Coveware set off Maze, Egregor, Conti, NetWalker, Pysa, Clop, Ragnar Locker, MedusaLocker, and LockBit as prolific RaaS rings.
Tactics & Techniques
Ransomware actors continuously increase the complexity of their operations and introduce new tools to compromise their targets. SOC Prime’s analysis of major TTPs results in several key points that describe current malicious approaches typical for each ransomware market segment.
Mass-Market Ransomware
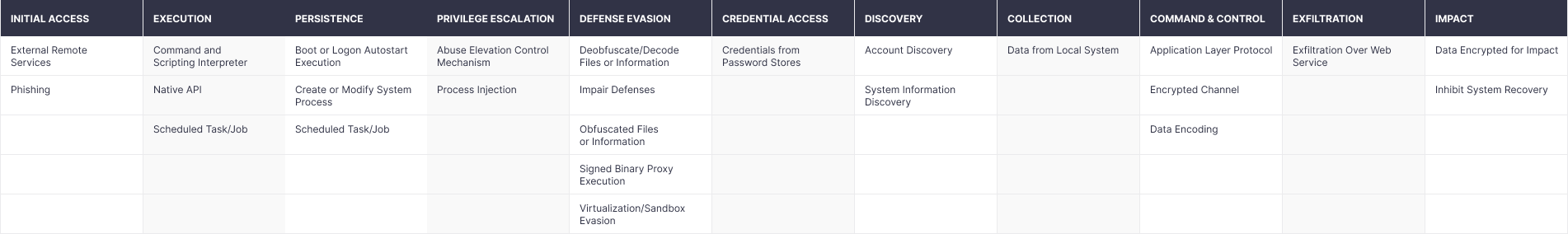
While speaking about the mass-market ransomware segment, adversaries leverage simple but reliable tools and approaches to proceed with the attack. Generally, the encryption is triggered right after the initial infection, without further network propagation. The primary infection vector is phishing. Also, the mass ransomware niche frequently relies on exposed RDP services, VPNs lacking two-factor authentication (2FA), and commodity malware (Trickbot, Bazar, SDBBot, Qakbot). To download or execute the malicious payload, threat actors use such tools as PowerShell, Windows Command Shell, and Visual Basic. Also, they abuse native OS API for a similar purpose. The whole structure of popular tactics and techniques applied by mass-market ransomware actors you can explore in the table below.
Figure 1. Tactics and Techniques Applied by Mass-Market Ransomware Segment
APT-like Ransomware
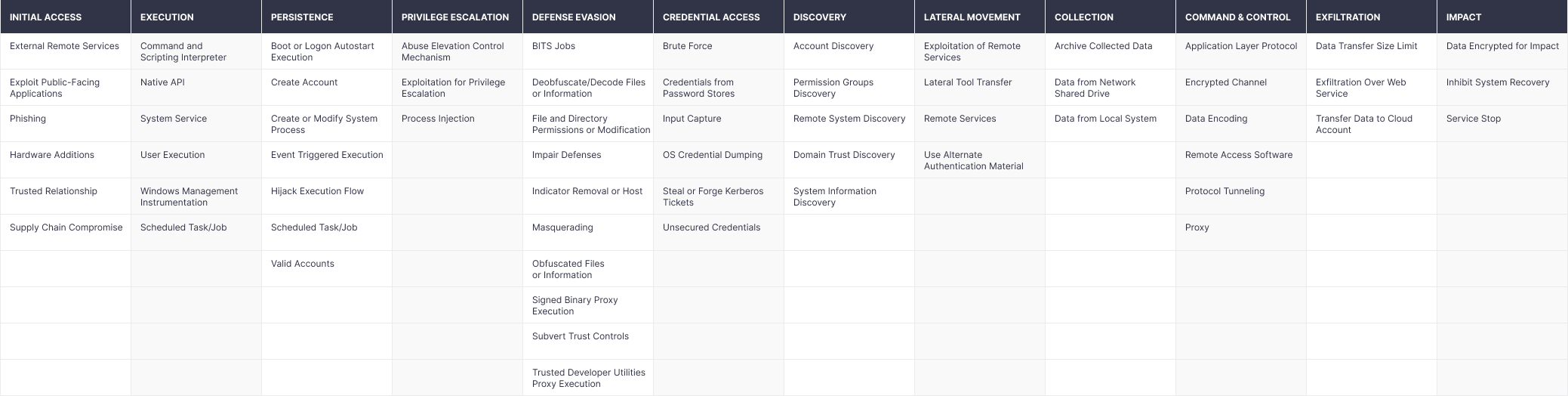
APT-like ransomware actors usually leverage sophisticated tools and methods to infiltrate the network and propagate across it for reconnaissance. Generally, the attacks are highly targeted and adversaries spend months inside the corporate network exploring its weak points. The encryption starts only after hackers are sure about all security gaps that might be used for the successful intrusion. Such an approach results in a full network freeze for the maximum damage. Alongside the exposed RDP servers, threat actors frequently leverage known vulnerabilities for initial access. Furthermore, APT-like ransomware groups might rely on supply chain attacks for penetration. The variety of attack methods is broad, with a batch of them being introduced from the toolset of APT groups, making such attacks dangerous and hard to detect. The full overview of techniques and tactics used by this segment of ransomware you can explore below.
Figure 2. Tactics and Techniques Applied by APT-Like Ransomware Segment
Hot Points
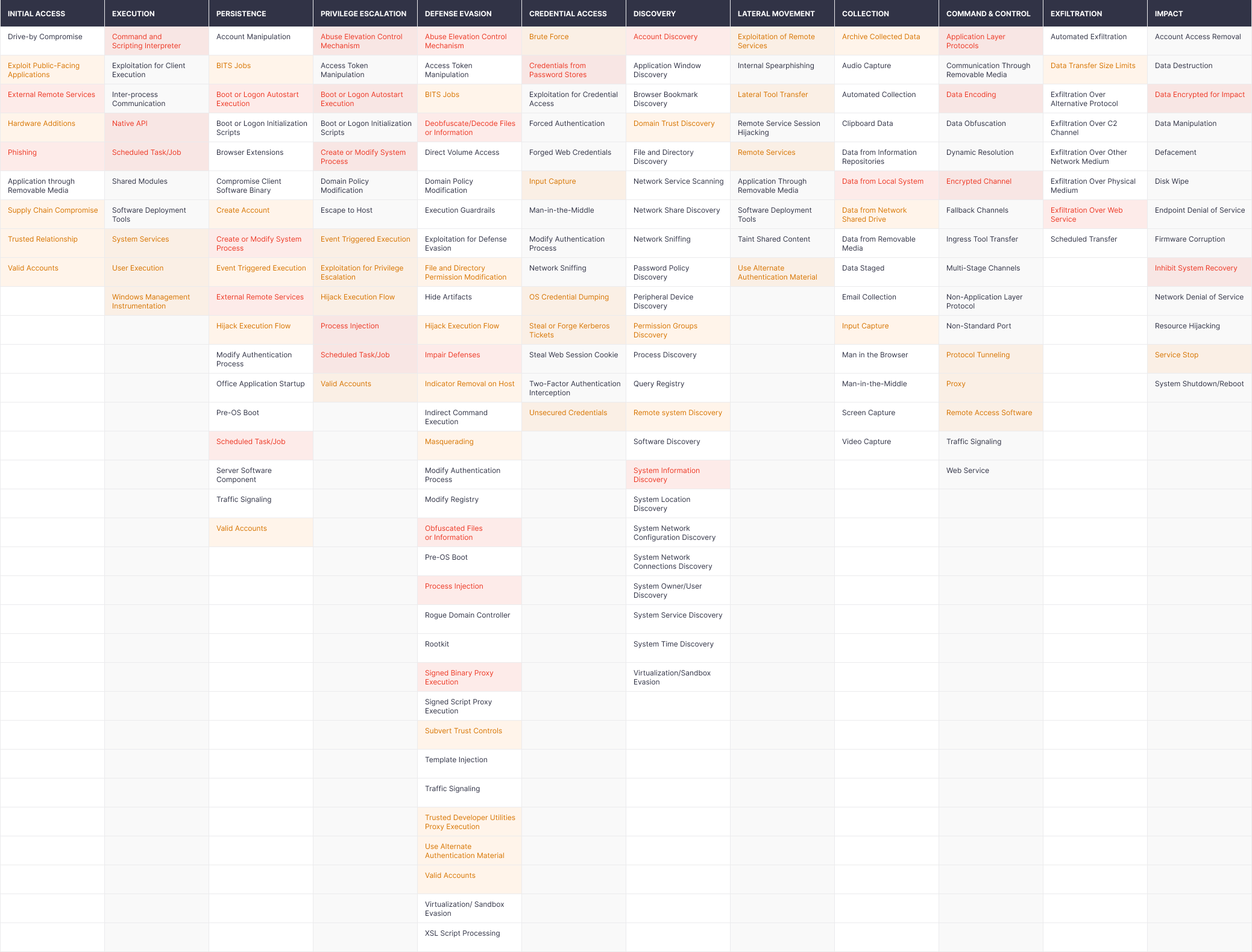
The analysis of TTPs used by various ransomware actors shows that there is a list of hot points most frequently used by different ransomware groups, regardless of their niche. Actually, the SOC Prime Team identifies these as the most important spots that should be constantly checked by the Security Operations Center (SOC) and Cyber Defense Center (CDC) to prevent intrusion. The list of such hot points you can see below. Red color highlights the most popular techniques, followed by orange highlighting the frequent ones and white marking those observed in the attacks.
Figure 3. Hot Points Map of Tactics and Techniques Used by Ransomware Actors
SOC Prime’s core product, Threat Detection Marketplace, can significantly help SecOps and CDC practitioners in their battle against the ransomware threat. Our platform aggregates thousands of SOC content items that allow detecting the infection before the encryption routine is launched. Threat Detection Marketplace rules, parsers, configs, and other types of content are mapped directly to the MITRE ATT&CKⓇ Framework, giving the ability to detect both — particular tactics, techniques, and sub-techniques applied by a specific ransomware actor and TTPs that are related to the ransomware threat in general. In fact, the majority of ransomware “hot points” are covered by Threat Detection Marketplace content.
The most devastating attacks often involve a set of sophisticated techniques that allow adversaries to affect the network under cover while remaining hard to detect. SOC Prime’s content is sharpened to identify specific behavioral patterns tied to a particular ransomware group, which allows detecting the intrusion on the earliest attack stages before the damage is done.
Best Practices for Ransomware Defense
Since TTPs differ for each ransomware segment, the defense practices should vary accordingly.
-
Mass-Market Ransomware. While talking about the mass segment, the attack kill chain is rather straightforward, therefore, defense practices are as follows:
-
Email Security Gateways. Services of such kind from the ransomware prevention toolkit are used to protect the organization’s email servers from malicious notifications that can be used for spreading ransomware. -
Antivirus Protection. Choosing reliable antivirus solutions can also safeguard the organization’s infrastructure against mass-market ransomware attacks.
-
-
APT-like Ransomware. To protect against intrusion launched by this segment actors, the organizations need more advanced layers of defense.
- Monitoring, Detection, and Response. Taking into account that the reconnaissance stage for these attacks requires a considerable amount of time, the best opportunity to prevent a compromise is to identify the earliest signs of malicious activity inside your network. It is important to log all the possible telemetry and keep it at hand in storage. Access to the complete pool of telemetry enables retrospective hunt and allows SecOps teams to master their security operations. Threat Detection Marketplace might be a helpful instrument on the way. SOC Prime’s platform provides complete threat context, which works well for real-time alerting and retrospective hunting. Furthermore, our 100K+ content base is enriched every day by a community of 300 seasoned threat hunters, ensuring cutting-edge content on the latest threats.
- SOC. Investing into the organization’s SOC can play a crucial role in strengthening the cyber defense capabilities against the constantly emerging ransomware campaigns. Organizations can also apply to the reliable third-party vendors delivering SOC as a Service to receive 24/7 protection ranging from thorough threat investigation, continuous monitoring, and timely incident response leveraging the organization’s SIEM and XDR stack in use.
- EDR Solutions. Taking advantage of the next-gen Endpoint Detection and Response (EDR) solutions can serve as a valuable investment to defend the company’s infrastructure against APT-like ransomware. With EDRs, security teams gain comprehensive real-time monitoring of endpoint data enabling them to timely detect the wildest adversary attempts and prevent them from spreading across the organization’s environment.
- Threat Hunting Operations. BlueTeam specialists are vital for the fight against the APT-like ransomware threat. Although the automation of SOC is crucial, automated solutions can miss the sophisticated and unique attack vectors. Therefore, the skills and expertise of threat hunting engineers are required to identify security incidents that automated detections do not catch. To learn more about threat hunting best practices, you can explore an insightful manual from our Senior Threat Hunting Engineer Adam Swan or sign up to Cyber Library to deepen your cybersecurity knowledge for free.
Apart from the above-mentioned recommendations, security awareness, backups, and patching remain key points to preventing ransomware.
Awareness. Educating in-house employees on ransomware-induced data breaches and other critical business issues in the form of regular training or workshops can help raise security awareness on a company-wide level and prevent potential losses.
Backups. Ensuring that all vital information within your business environment regularly goes through backup procedures might save the organization from devastating consequences of the attack. Back up confidential files and configurations, regularly test the backups, make sure they are offline and not connected to the business network. It is important because many ransomware samples attempt to encrypt or delete accessible backups.
Timely Patching. It is crucial to make sure that all operating systems, apps, and firmware within the organization are updated to the latest secure version. Centralized patch management systems and proper risk-based assessment strategy can power organizational patch management efforts and block the majority of intrusions.
Also, to learn the general best practices for ransomware protection, you can explore a dedicated memo released by the White House against the backdrop of escalating ransomware attacks.
SOC Content to Detect Ransomware Attacks
Continuously boosting the ransomware detection capabilities of the security platforms in use enables proactive cyber defense for your organization. Every month, Threat Bounty Program developers and SOC Prime Content Team publish to Threat Detection Marketplace dozens of SOC content items that help detect techniques, tools, and suspicious activity, which may indicate an active phase of a ransomware attack.
To assist security practitioners in fighting critical threats, we gathered top Sigma rules useful for ransomware attack detection. All content is directly mapped to the MITRE ATT&CK® framework and contains the corresponding references and descriptions:
SINGLEMALT / KEGTAP / Ryuk Techniques and Procedures
Possible Ryuk or Another Sender of magic Wake-On-Lan packet (via network_connection)
Phorpiex bot Implant DriveMgr strings & Download Avaddon Ransomware
Egregor RaaS (Ransomware as a Service) Continues the Chaos
Anti-forensic commands executed by Defray777
Maze Ransomware threat Actors use reg.exe (Sysmon Behaviour)
EKANS/SNAKE Ransomware (Sysmon detection)
CLOP Ransomware detection (Sysmon)
Nemty Ransomware (LOLBins abuse)
Persistence Of Ryuk Ransomware
New Version of Ryuk Ransomware (08.04.2021)
Detection of Clop Ransomware (22/03/2021)
Detection of LockBit ransomware
Avaddon Ransomware Detection (Sysmon Behaviour)
Conti Ransomware Target on Health Sector
Gootkit and REvil Ransomware Targeting German Users – November 2020
NEMTY Successor, Nefilim/Nephilim Ransomware
DoppelPaymer Ransomware Detection
Malspam Campaign Drops IcedID and Leads to REvil Ransomware
Ransomware Behaviour Analysis (MedusaLocker)
Possible privilege escalation attack using Dllhost.exe
Sodinokibi IoCs (Sysmon detection)
Suspicious GPUpdate No Command Line Arguments
Sodinokibi ‘REvil’ Malware Sample (Sysmon Behavior) (22-July-2020)
Also, you can check the full list of Threat Detection Marketplace content associated with ransomware attacks here.
References:
- https://start.paloaltonetworks.com/unit-42-ransomware-threat-report.html
- https://www.group-ib.com/resources/threat-research/ransomware-2021.html
- https://secure2.sophos.com/en-us/content/state-of-ransomware.aspx
- https://www.esentire.com/resources/library/six-ransomware-gangs-claim-290-new-victims-in-2021-potentially-reaping-45-million-for-the-hackers
- https://www.documentcloud.org/documents/20796934-memo-what-we-urge-you-to-do-to-protect-against-the-threat-of-ransomware
- https://www.coveware.com/blog/ransomware-attack-vectors-shift-as-new-software-vulnerability-exploits-abound
Looking for more threat detection content? Sign up for Threat Detection Marketplace to leverage 100K+ curated SOC content items addressing the latest attacks and customized to your environment. Eager to participate in threat hunting activities and craft your own detection rules? Join our Threat Bounty Program!