Hot on the heels of the massive email distribution in the recent malicious campaign targeting Ukrainian state bodies and leveraging Remcos (Remote Control and Surveillance) Trojan, threat actors exploit another remote administration software dubbed Remote Utilities to hit Ukrainian organizations. CERT-UA warns the global cyber defender community of ongoing phishing attacks attributed to the UAC-0096 hacking group.
Analysis of the Latest Phishing Attacks by UAC-0096 Hackers Leveraging Remote Utilities
On February 13, CERT-UA researchers issued a new CERT-UA#5961 alert detailing the massive email distribution impersonating the National Security and Defense Council of Ukraine. In this ongoing malicious campaign, threat actors exploit the phishing attack vector to target Ukrainian organizations via Remote Utilities, the legitimate remote administration software.
Just a few days before this phishing campaign, CERT-UA researchers spotted another malicious activity targeting Ukrainian state bodies and leveraging a different remote administration tool known as Remcos RAT. Notably, the previous adversary activity was attributed to the UAC-0050 hacking collective, which used to apply the Remote Utilities software in their earlier campaigns.
In the ongoing phishing attacks against Ukraine, adversaries apply a lure email subject related to critical security updates and a malicious RAR attachment with the details of the fake updates. The RAR file, in turn, contains an image lure with fake guidelines and a split archive hiding an executable file. By launching the latter, compromised users will install the Remote Utilities software on their computers to further be leveraged by hackers for their malicious activity. The observed adversary behavior patterns are attributed to the activity of the UAC-0096 hacking group.
Detecting UAC-0096 Malicious Activity Covered in the CERT-UA#5961 Alert
Since russia’s full-scale invasion of Ukraine, cyber defenders are observing the increasing volumes of phishing attacks targeting Ukrainian state bodies and organizations in multiple industry sectors. SOC Prime has been on the cyber frontline helping Ukraine and its allies proactively defend against russia-affiliated attacks of any scale and detect adversary TTPs. To help organizations timely spot the malicious activity of the UAC-0096 hacking abusing the Remote Utilities software, SOC Prime’s Detection as Code platform provides access to the comprehensive list of curated Sigma rules addressing attacker’s TTPs covered in the latest CERT-UA alert. All detections can be used across dozens of SIEM, EDR, and XDR solutions to help teams tackle the challenge of SIEM migration and time-consuming manual fine-tuning.
Click the Explore Detections button below to reach the dedicated high-quality alerts and hunting queries enriched with relevant cyber threat context, including MITRE ATT&CK® references and CTI links. To simplify the search for dedicated Sigma rules, SOC Prime Platform supports their filtering by the custom tags “CERT-UA#5961” and “UAC-0096” based on the alert and group identifiers. For your convenience, any of these tags is available for browsing the relevant detection content.
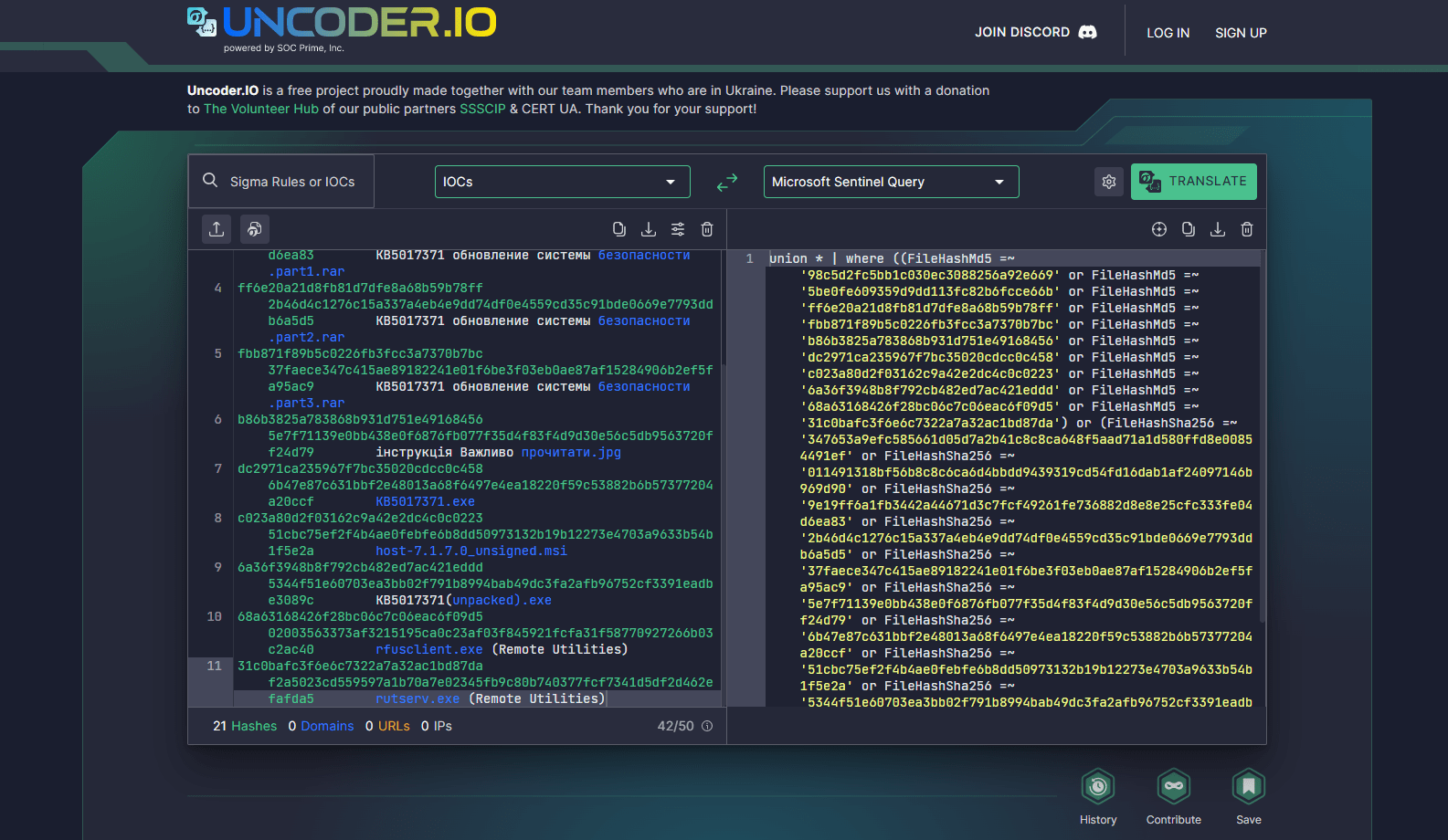
Security engineers can also automate their search for indicators of compromise associated with the malicious activity of UAC-0096 by leveraging the new version of Uncoder.IO tool that now supports IOC conversion to multiple SIEM & XDR platforms. Just paste the file, host, or network IOCs provided by CERT-UA into the UI and select the content type of your target query to instantly create performance-optimized IOC queries ready to run in the chosen environment. Uncoder.IO is a free project developed with privacy in mind — no authentication, no log collection, and all data is kept session-based for your peace of mind.
MITRE ATT&CK Context
To delve into the in-depth context behind the malicious campaign of the UAC-0096 hacking collective covered in the latest February’s CERT-UA alert, all above-referenced Sigma rules are tagged with ATT&CK v12 addressing the relevant tactics and techniques:
Tactics | Techniques | Sigma Rule |
Defense Evasion | Virtualization/Sandbox Evasion (T1497) | |
File and Directory Permissions Modification (T1222) | ||
System Script Proxy Execution (T1216) | ||
Indicator Removal (T1070) | ||
Hide Artifacts (T1564) | ||
Subvert Trust Controls (T1553) | ||
Deobfuscate/Decode Files or Information (T1140) | ||
Domain Policy Modification (T1484) | ||
Execution | Scheduled Task/Job (T1053) | |
Impact | Inhibit System Recovery (T1490) | |
System Shutdown/Reboot (T1529) | ||
Data Manipulation (T1565) | ||
Data Destruction (T1485) | ||
Looking for more curated rules and queries to enhance the organization’s cybersecurity posture? Explore SOC Prime’s Sigma Rules Search Engine to obtain relevant Sigma rules for attack detection exploiting Remote Utilities and make sure your team is always armed with proactive cyber defense capabilities.




