Overview and Analysis, Top Data Sources, and Relevant Sigma Rules to Detect Privilege Escalation
SOC Prime cultivates collaboration from a global cybersecurity community and curates the most up-to-date Sigma rules aligned with the MITRE ATT&CK® framework enabling teams to focus on threats they anticipate most. With the recently released On Demand subscriptions for SOC Prime’s platform, security practitioners can gain immediate access to detection-as-code content matching the attack vectors most relevant to their organization-specific needs. In this blog article, we are going to cover the Privilege Escalation (TA0004) tactic overview and analysis and explore dedicated Sigma rules addressing this ATT&CK tactic.
Explore Platform Book a Meeting
What is Privilege Escalation (TA0004)?
Adversaries have different goals but they generally affect the confidentiality, integrity, or availability of critical systems. Privilege escalation is the act of obtaining higher trusts within a compromised system. These trusts allow them to take further action, such as laterally moving to new hosts, or taking privileged actions like reading or changing protected data.
Privilege Escalation Detection Content
Detecting privilege escalation is a complex process that cannot be limited to a single rule and requires multiple detection algorithms while considering new techniques, tools, and implementations as soon as they arise.
Sigma serves as a de-facto standard for expressing threat hunting queries that can be used to develop detection content applicable to most popular SIEM & XDR solutions. Visit the Sigma repository on GitHub or for more details or explore how Sigma transforms cybersecurity as a vendor-agnostic and future-proof industry standard.
Leveraging Uncoder.IO, teams can instantly translate Sigma rules to the security solution of their choice. Alternatively, using the command-line interface, Sigma rules can be converted to the selected language format via SIGMAC tool.
Below you can find our recommended Sigma rules addressing the Privilege Escalation tactic (TA0004):
Behavior Rule: Windows Debug Privileges Assigned
SeDebugPrivilege is a privilege within Windows that allows adversaries to escalate to the local system account (Windows equivalent of root) by debugging system processes. This rule identifies accounts being assigned the SeDebugPrivilege.
Exploit Rule: Possible Dirty Pipe Privilege Escalation by Overwriting Data in Arbitrary Files [CVE-2022-0847] (via auditd)
CVE-2022-0847 (Dirty Pipe) is a vulnerability that allows a non-root user to overwrite data in any target file. This rule leverages syscall events from auditd to identify probable exploitation attempts.
Tool Rule: Possible AdvancedRun Execution Patterns (via cmdline)
AdvancedRun is a freeware tool provided by the software developer Nir Sofer. The tool has been used by threat actrors to escalate from a local administrator to system privileges.
Cloud Rule: Possible Azure API Permissions Abuse (via azuread)
Azure Apps can be granted the App role “AppRoleAssignment.ReadWrite.All”. With this permission, an app can provide itself any API permission, including the ability to change user roles to Global Admin. This rule identifies apps being granted sensitive App role permissions.
Explore Platform Book a Meeting
Privilege Escalation Detection: Most Common Log Sources
Sigma rules available in the SOC Prime’s platform covers log sources tailored to the organization’s environment. Here are five most common log sources normally required to detect privilege escalation.
Process Creation
Below you can find the most common process creation log sources:
- Windows Security Logs
- 4688, validate that command line details are included
- Sysmon for Windows and Sysmon for Linux
- Event Id 1
- Linux Auditd Logs
- execve event type
- Endpoint Detection & Response (EDR) | eXtended Detection and Response (XDR)
- Some EDR services do not provide passive or enriched process creation events.
Service Creation and Scheduled Task Creation Data Sources
It is common for adversaries to create services and tasks for privilege escalation. Services run with system privileges, and scheduled tasks can be made by administrators. Scheduled tasks are normally created to run as SYSTEM and then are deleted in a short amount of time.
Here are some common service and scheduled task creation data sources:
- Windows Security Logs
- 7045
- 4698
- Endpoint Detection & Response (EDR) | eXtended Detection and Response (XDR)
- Some EDR services do not provide passive or enriched scheduled task / service creation events
Native Cloud Identity and Access Management Logs (IAM)
When user roles are changed, the cloud providers generally log these changes in Identity and Access Management Logs. For instance, Google Cloud Provider includes IAM logs in their Cloud Audit Logs.
Native Cloud Activity Logs
When users access or change cloud resources in the cloud, an audit log is generally created showing the access. For instance, AWS provides CloudTrail logs, while Microsoft — AzureActivity logs. The appropriate activity logs can help security practitioners audit access to sensitive resources.
Linux Auditd Logs and/or Equivalent EDR/XDR Logs
Monitor for activity from the root account using auditd or an equivalent feature provided by an EDR / XDR.
SOC Prime curates detections mainly generated from two primary sources that combine to produce collaborative expertise enabling teams to keep pace with the ever-increasing attack volume. Both the SOC Prime’s in-house team of content developers and Threat Bounty Program researchers, including Emir Erdogan, Osman Demir, Nattatorn Chuensangarun, and Sittikorn Sangrattanapitak, have mainly contributed to the delivery of detection content addressing the Privilege Escalation tactic.
Explore Platform Book a Meeting
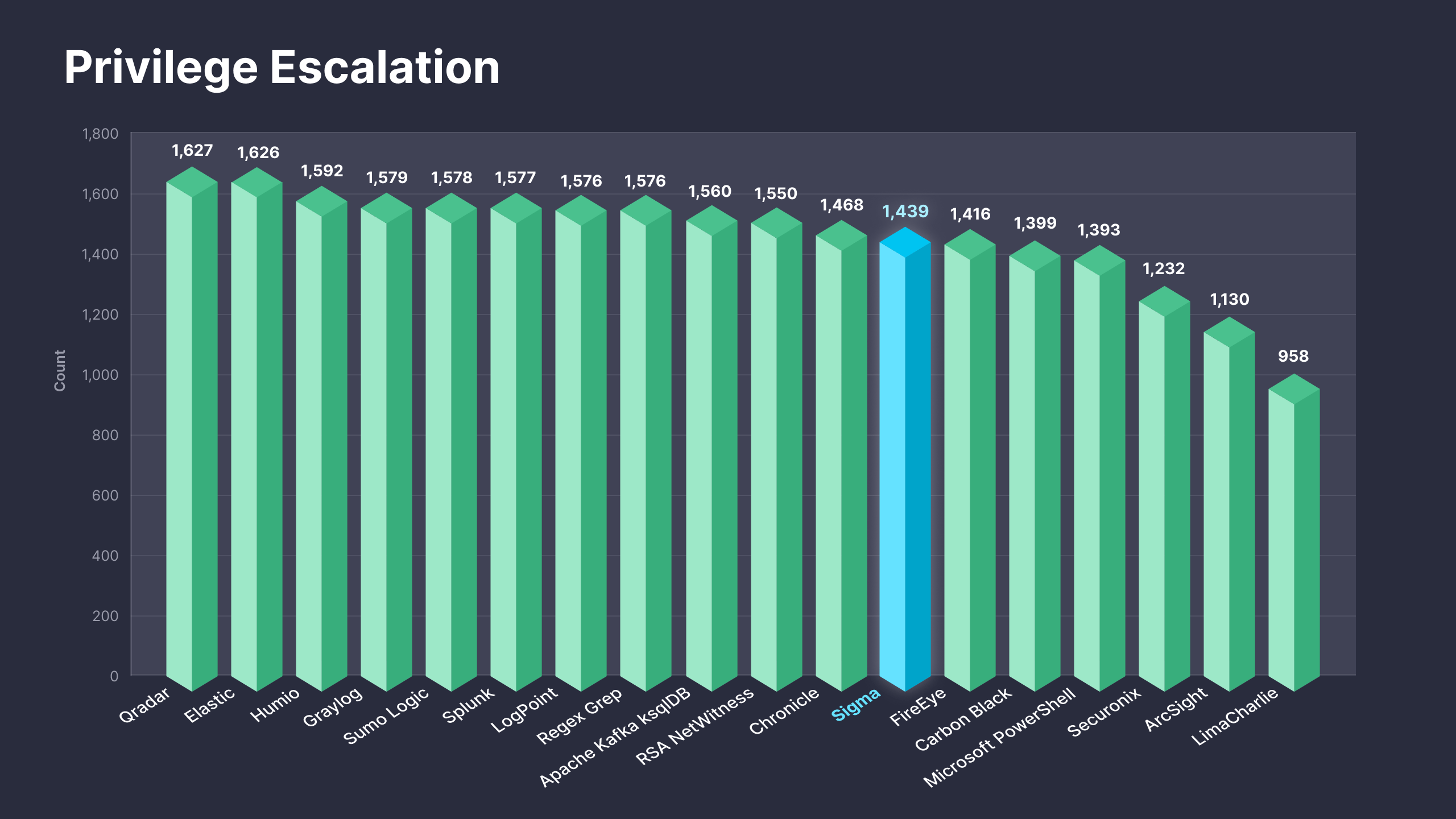
Fig. 1. Sigma rules addressing the Privilege Escalation (TA0004) tactic along with translations to 25+ supported platforms
The newly released On Demand subscriptions are designed to enable security practitioners to drive immediate value from SOC Prime’s platform by offering direct access to detection content matching the organization-specific threat profile. As part of these subscriptions, teams can gain instant access to 1,400+ Sigma-based detection rules addressing the Privilege Escalation tactic along with translations available for 25+ SIEM & XDR formats. For more details on the On Demand subscription tiers, please refer to https://my.socprime.com/pricing/.