Phobos Ransomware Activity Detection: Adversaries Target the Public Sector, Healthcare, and Other Critical U.S. Infrastructure

Table of contents:
The exponential rise and escalation in intrusion complexity of ransomware attacks fuel the need for proactive ransomware detection. FBI and CISA issue a joint cybersecurity heads-up notifying the global defender community of a dramatic increase in Phobos ransomware attacks targeting the U.S. state bodies and other critical infrastructure, resulting in successful ransom demands amounting to several million U.S. dollars.
Detect Phobos Ransomware Activity Covered in the AA24-060A Alert
As Phobos ransomware continues to affect organizations in multiple industry sectors exposing them to severe financial losses, proactive cyber defense is key to minimizing the risks of intrusions. SOC Prime Platform curates a broad collection of detection algorithms to help security teams timely eliminate the risks of Phobos ransomware impact.
Click the Explore Detections button to reach the entire detection stack for Phobos ransomware activity covered in the AA24-060A alert recently released by CISA and FBI. All detection algorithms are enriched with tailored threat intelligence, aligned with MITRE ATT&CK® v.14.1, and are instantly convertible to multiple cybersecurity languages.
Forward-looking organizations that constantly strive to elevate their cybersecurity posture can also gain from the comprehensive collection of SOC content for Phobos ransomware detection available via this link.
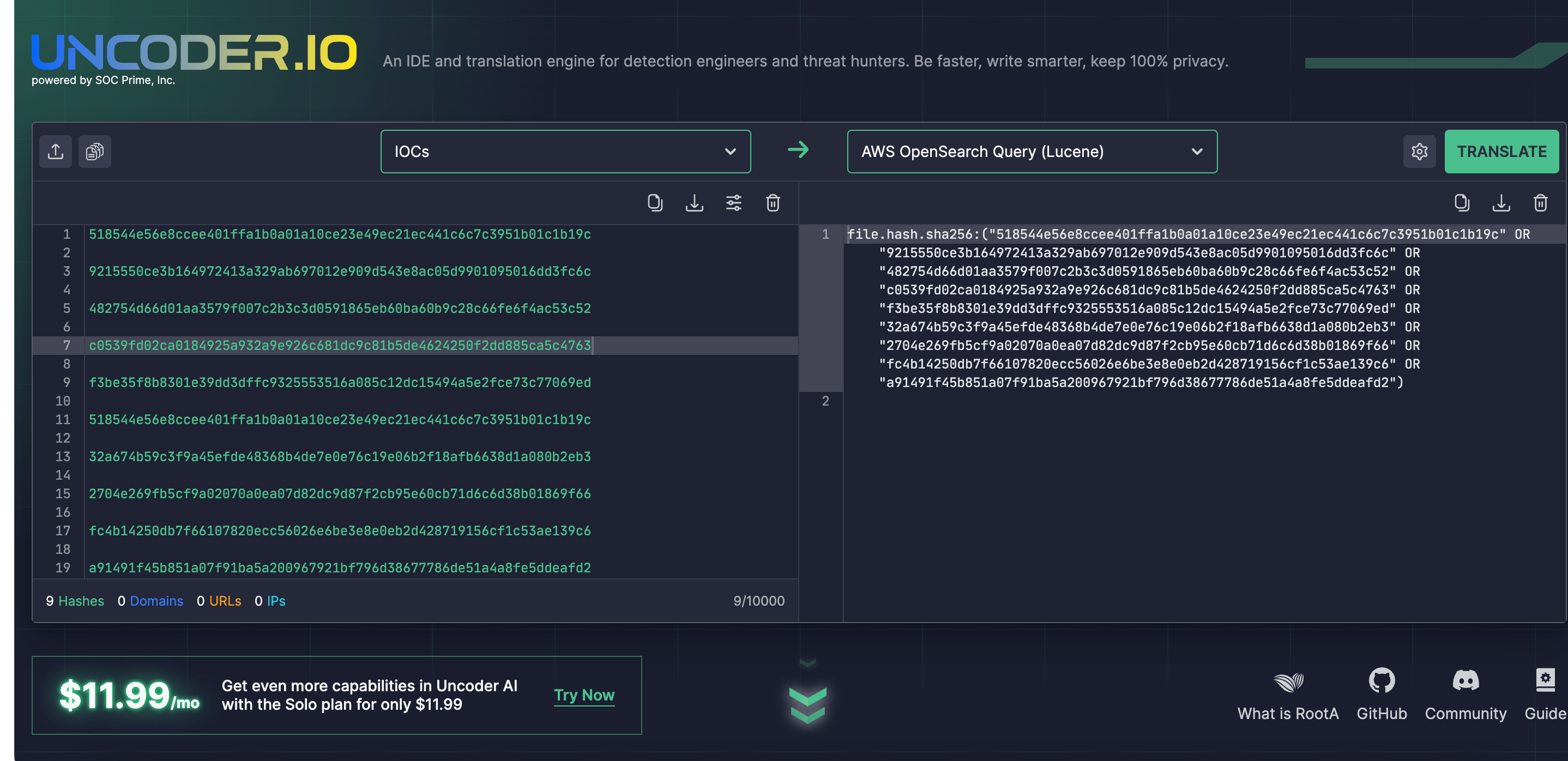
In addition, defenders can search for IOCs related to the Phobos ransomware variants and provided in the AA24-060A alert. Rely on the open-source Uncoder IO to automatically parse relevant threat intel into custom IOC queries and instantly run them within your environment.
Phobos Ransomware Activity Overview
At the turn of March 2024, the leading U.S. cybersecurity agencies, including the FBI, CISA, and MS-ISAC issued a joint alert tracked as AA24-060A aimed to raise awareness of the increasing attacks by Phobos ransomware actors and share TTPs and IOCs associated with the ongoing adversary activity.
For almost half a decade, Phobos ransomware maintainers have launched cyber attacks affecting the U.S. public sector, with other critical infrastructure sectors, including education and public healthcare, among their targets.
Open-source research indicates that Phobos ransomware is likely linked to several malware variants, including Elking, Eight, Devos, Backmydata, and Faust ransomware, due to the similar TTPs observed in Phobos intrusions. Phobos ransomware is commonly leveraged alongside diverse publicly accessible tools like Smokeloader, Cobalt Strike, Mimikatz, and other utilities. Phobos ransomware actors have adopted a RaaS model, which has contributed to establishing Phobos as one of the more prevalent ransomware strains in recent years.
For initial access, adversaries frequently apply the phishing email attack vector to deliver the payload onto targeted networks. Another adversary technique involves embedding SmokeLoader in email attachments, which, once opened by compromised users, downloads Phobos ransomware onto their systems, and gives attackers the green light to perform data exfiltration
Phobos ransomware operators frequently use multiple remote access utilities to establish a remote connection with the impacted server. They might also target RDP to conduct open-source research, generate a victim profile, and connect the targeted IP addresses to relevant companies.
Phobos actors employ executables, such as 1saas.exe or cmd.exe, to install additional Phobos payloads with elevated privileges and run multiple Windows shell functions. In addition, they exploit built-in Windows API functions to bypass access control, retrieve authentication tokens, and initiate new processes for privilege escalation. Threat actors also apply detection evasion techniques by altering system firewall configurations and frequently rely on specific utilities for anti-malware analysis.
To maintain Phobos ransomware persistence, attackers abuse Windows Startup folders and Windows registry keys to disable functions that facilitate access to backups or assist in the system recovery. As for data exfiltration, they have been observed employing WinSCP and Mega.io. Phobos ransomware actors commonly set their eyes on legal and financial data, as well as technical documentation. After the data exfiltration stage, attackers actively seek out and eliminate any existing data backups that the victims may have implemented, effectively preventing recovery without the payment of the decryption key.
As for Phobos ransomware mitigation guidelines, the AA24-060A alert recommends constantly enhancing the security of remote access software, applying stringent application controls, enforcing best practices for log collection, restricting the use of RDP and similar remote desktop services, disabling command-line and scripting capabilities, and thoroughly monitoring domain controllers, servers, or workstations for new or unrecognized accounts. Defenders also strongly recommend continuously validating the organization’s security program to future-proof its effectiveness against emerging threats.
Browse SOC Prime to empower your team with a comprehensive suite of 800+ detection algorithms against ransomware attacks to continuously supercharge your organization’s defenses with the collective industry expertise. Security engineers can also rely on Uncoder AI to elevate their detection engineering capabilities by writing better code enriched with AI-generated recommendations and threat intel, as well as automatically converting it across various cybersecurity languages.