Update (October 8, 2025): This article has been updated to feature a dedicated detection rule set focused on CVE-2025-61882 exploitation. The updated rule collection now contains 19 content items, accessible via the ‘Explore Detections’ button below.
Another day brings another security concern. Hot on the heels of CVE-2025-41244, a recently weaponized flaw impacting VMware Tools and VMware Aria Operations, researchers have uncovered a new zero-day flaw. The novel critical Oracle E-Business Suite vulnerability tracked as CVE-2025-61882 has reportedly been exploited in the latest Cl0p-linked data theft campaign.
Detect CVE-2025-61882 Exploitation for Cl0p Ransomware Attacks
In 2025, ransomware groups increasingly rely on vulnerability exploitation as a primary entry point into enterprise systems. While social engineering and stolen credentials remain significant attack vectors, vulnerability exploits have become one of the most common methods for initial access. Threat actors show a clear preference for low-friction, high-impact flaws, particularly unauthenticated RCE and vulnerabilities with publicly available proof-of-concept (PoC) exploits.
With over 37,500 new vulnerabilities logged by NIST this year, the race is on for cybersecurity teams. While vulnerability exploitation remains the leading attack vector, and as cyber threats grow more sophisticated, proactive detection is essential to reducing the attack surface and mitigating risk.
Register now for the SOC Prime Platform to access an extensive library of context-enriched detection rules and AI-driven threat intelligence addressing CVE-2025-61882 exploitation attempts. Just press the Explore Detection button below and immediately drill down to a relevant detection stack.
For those interested in exploring the full set of rules and queries related to vulnerability exploitation, our extensive library of Sigma rules is available for browsing with a dedicated “CVE” tag.
All the rules are compatible with multiple SIEM, EDR, and Data Lake formats and mapped to the MITRE ATT&CK® framework. Additionally, each rule is enriched with CTI links, attack timelines, audit configurations, triage recommendations, and more relevant context.
Security engineers can also leverage Uncoder AI, an IDE and co-pilot for detection engineering. With Uncoder, defenders can instantly convert IOCs into custom hunting queries, craft detection code from raw threat reports, generate Attack Flow diagrams, enable ATT&CK tags prediction, leverage AI-driven query optimization, and translate detection content across multiple platforms. For instance, users can seamlessly generate the Attack Flow based on CrowdStrike’s overview of the latest attacks, leveraging CVE-2025-61882.
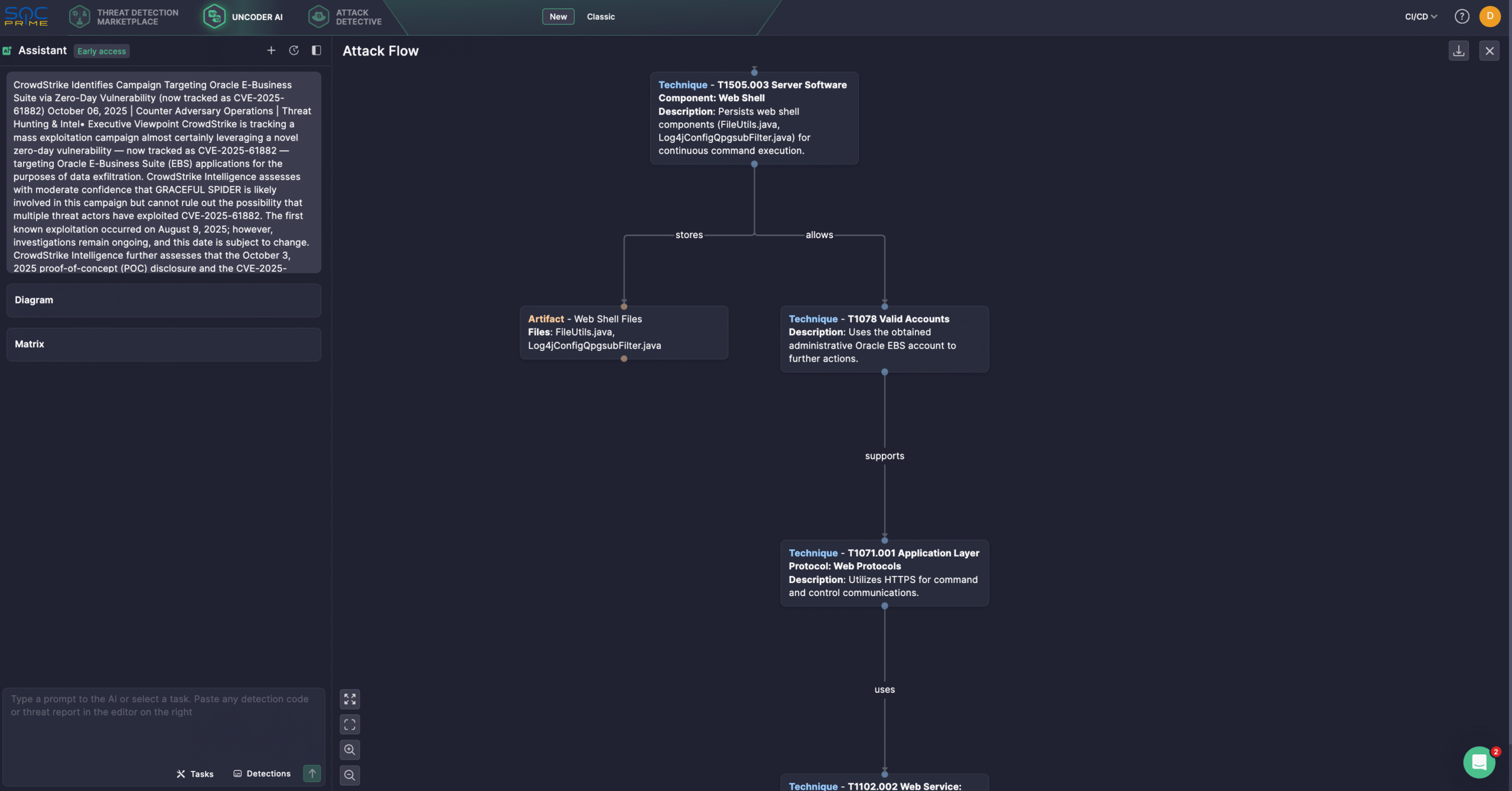
CVE-2025-61882 Analysis
Oracle has recently rolled out an emergency update to fix a critical vulnerability in its E-Business Suite, which has been actively exploited in recent Cl0p ransomware data theft attacks. The flaw, tracked as CVE-2025-61882 with a CVSS score of 9.8, allows unauthenticated remote attackers to compromise the Oracle Concurrent Processing component via HTTP and gain full control over affected systems. Impacted versions include 12.2.3 through 12.2.14.
Oracle’s advisory confirms that the vulnerability can be exploited remotely without credentials, leading to potential RCE. The patch also addresses additional exploitation vectors discovered during the company’s internal investigation. The fix requires prior installation of the October 2023 Critical Patch Update. With a public PoC available and evidence of active exploitation, the vendor urges administrators to apply the patch immediately as a feasible CVE-2025-61882 mitigation step.
Google-owned Mandiant reported that adversaries are conducting a large-scale email campaign using hundreds of compromised accounts. The Mandiant CTO Charles Carmakal confirmed that Cl0p leveraged this and other Oracle EBS vulnerabilities, with some of them patched in mid-summer 2025, to steal large volumes of data from multiple victims in August 2025. He emphasized that, given the scale of exploitation and the likelihood of continued attacks by other actors, organizations should proactively investigate for signs of compromise, regardless of patching status.
The surge in zero-day attacks on mainstream products, combined with their increasing exploitability, is forcing organizations to adopt faster and more robust strategies to stay ahead of attackers. SOC Prime curates a comprehensive product suite that combines top cybersecurity expertise and AI, is built on zero-trust principles, and is backed by automated technologies and real-time threat intelligence, enabling security teams to outscale modern-day cyber threats, no matter their sophistication.




