Overview and Analysis, Top Data Sources, and Relevant Sigma Rules to Detect Lateral Movement
SOC Prime operates the world’s largest and most advanced platform for collaborative cyber defense that enables threat-centric selection of detection content backed by particular adversary tactics, techniques, and sub-techniques as per the MITRE ATT&CK® framework v.10. In this blog article, we are going to provide insights into the Lateral Movement definition, overview, and analysis and explore Sigma rules addressing this ATT&CK tactic.
SOC Prime has recently released On Demand subscriptions for its Detection as Code platform that provide access to curated detection content addressing the Lateral Movement tactic (TA0008) enabling security practitioners to address their most relevant content needs.
Explore Platform Book a Meeting
What is Lateral Movement (TA0008)?
Adversaries have different goals but they generally affect the confidentiality, integrity, or availability of critical systems. Luckily for defenders, they cannot wish their way onto such critical systems, often these systems exist behind a hard boundary (NAT’d network, Firewall, Gateways, VPNs, logically isolated by account management, etc). Once adversaries gain initial access (commonly referred to as gaining a foothold) on victim systems, they often must weasel around, probing for new vulnerabilities, weaknesses, and misconfigurations to exploit to further their foothold. The act of moving from one system to another is known as lateral movement in cybersecurity. There are many methods to achieve this. Leveraging the MITRE ATT&CK framework, these adversary operations are called lateral movement “techniques”.
Lateral Movement Detection Rules
When it comes to MITRE ATT&CK tactics and techniques, there is no “one rule to rule them all”. Detecting lateral movement requires many rules and a process that accounts for new techniques, tools, and implementations as they arise.
Sigma rules are detections that work for most SIEM / Log Analytics Platforms, including Microsoft Sentinel, Humio, Elastic Stack, QRadar, Sumo Logic, Splunk, and other widely used security solutions. For more information on the Sigma language, please refer here or visit the Sigma repository on GitHub. SOC Prime’s Detection as Code platform provides on-the-fly translations from Sigma to 25+ SIEM, EDR, and XDR formats. Alternatively, you can use the online Sigma translation engine, Uncoder.IO, or if you are handy on the command line, you can use the Sigma project’s SIGMAC (Sigma Converter).
Here are some of the highest value Sigma rules to help you get started with detecting lateral movement:
Behavior Rule: Possible Lateral Movement via WinRM (via process_creation)
Windows Remote Management provides adversaries with valid credentials to pivot between WinRM configured endpoints. The most commonly abused Windows feature that uses WinRM is PSRemoting. This rule identifies WinRM spawning child processes on remote hosts.
Exploit Rule for Log4j Lateral Movement Detection: Log4j RCE [CVE-2021-44228] Post-Exploitation Detection Patterns (Windows)
Once adversaries gain initial access, their options greatly increase, especially from an exploit perspective. They will likely have access to many systems that require internal access to exploit. One such exploit leveraged today is Log4j tracked as CVE-2021-44228.
Tool Rule: Possible Lateral Movement via PsExec or Similar (via audit)
PsExec is a tool maintained by Windows that enables administrators to remotely execute commands on Windows hosts. Adversaries with valid credentials can leverage PsExec to do the same. This type of activity is commonly referred to as “living off the land”, where adversaries take advantage of tools that already exist in environments.
Cloud Rule: Connection with suspicious User Agent (via office365)
Lateral movement can be used to impact cloud systems as well. Often trusts and delegations are abused to move between cloud tenants. Recently high-profile attacks against the cloud have involved the cases in which threat actors forgot to change the default user agent (e.g. Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:53.0) Gecko/20100101 Firefox/53.0.) provided by the library they leveraged, most commonly via Python requests.
Explore Platform Book a Meeting
Lateral Movement Detection: Most Common Log Sources
Sigma depends on data sources that exist in the organization’s environment. Below are five common log sources generally required to detect lateral movement:
Native Authentication Logs
If the technology in your organization’s environment can be logged into, then your SIEM should have the resulting authentication logs.
Here are the most common authentication log sources:
- Windows Security Event Log
- 4624
- 4625
- 4648
- 4768
- 4668
- Linux Auth Logs
- Azure Sign-in Logs
- AWS CloudTrail Sign-in Logs
Process Creation
Process Creation on Windows, Linux, and OSX provides invaluable insight into tools, behaviors, and even exploits being leveraged for lateral movement. Most of the time, lateral movement results in a remote process being spawned.
Here are some common process creation log sources:
- Windows Security Logs
- 4688, validate that command line details are included
- Sysmon for Windows and Sysmon for Linux
- Event Id 1
- Linux Auditd Logs
- execve event type
- Endpoint Detection & Response (EDR) | eXtended Detection and Response (XDR)
- Some EDR services do not provide passive or enriched process creation events.
Service Creation and Scheduled Task Creation Data Sources
It is common for adversaries to create remote services and scheduled tasks using valid administrative credentials.
Here are some common service and scheduled tasks creation log sources:
- Windows Security Logs
- 7045
- 4698
- Endpoint Detection & Response (EDR) | eXtended Detection and Response (XDR)
- Some EDR services do not provide passive or enriched scheduled task / service creation events
Network Analytics
There is a network component to almost every lateral movement technique. Therefore, it is critical to capture network traffic in your environment.
Here are some of the most common network analytics log sources:
- Corelight’s Zeek
- Firewall Logs
- Proxy Logs
- IDS Logs
- NetFlow
SOC Prime’s Detection as Code platform delivers near real-time detection content backed by the collaborative expertise of the in-house team of content developers and the contribution of 600 crowdsourced Threat Bounty researchers. Here are the top five content authors who contribute curated Sigma rules for lateral movement detection:
- SOC Prime Team
- Florian Roth
- Threat Bounty Program developers, including Nattatorn Chuensangarun, Emir Erdogan, and Sittikorn Sangrattanapitak
Explore Platform Book a Meeting
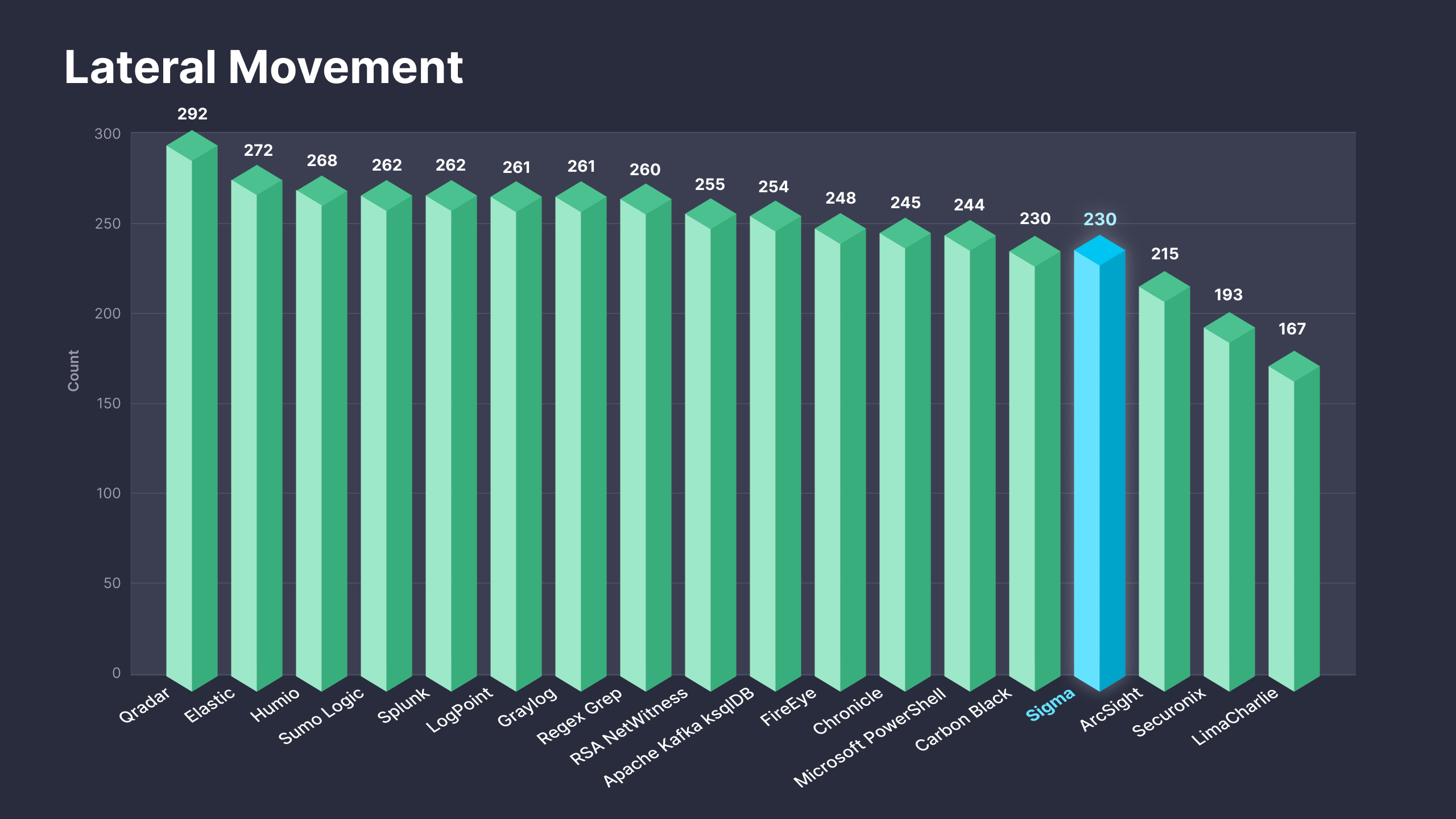
Fig. 1. Sigma rules addressing the Lateral Movement tactic (TA0008) along with translations to 25+ supported platforms
Newly released On Demand subscription plans are designed to enable security practitioners to drive immediate value from SOC Prime’s platform by instantly gaining access to detection content matching the organization’s threat profile. With on-demand access, security practitioners can obtain 230 curated Sigma-based detections addressing the Lateral Movement tactic along with translations to 25+ SIEM, EDR, and XDR formats. For more details on the On Demand subscriptions, please refer to https://my.socprime.com/pricing/.