In today’s rapidly evolving cybersecurity landscape, organizations face numerous challenges in safeguarding their digital assets. SOC Prime offers a suite of solutions designed to address some of the most pressing cybersecurity problems. This blog explores how SOC Prime’s Threat Detection Marketplace (TDM), Uncoder AI, and Attack Detective can solve five common issues.
- Time and Skill Shortages
Challenge: Many organizations struggle with limited security resources and a shortage of skilled cybersecurity professionals. According to research by the World Economic Forum, the global shortage of cyber professionals will reach nearly 4 million in 2024, with a projected talent gap of 85 million by 2030. This significant shortfall could result in an estimated $8.5 trillion in unrealized annual revenue within just six years. Already in 2024, 71% of organizations report unfilled cybersecurity positions, while 95% of cyber leaders believe more effort is needed to recruit talent into the cybersecurity workforce.
Solution: Threat Detection Marketplace, Uncoder AI, Attack Detective
- Threat Detection Rule Feed: Provides continuously updated threat detection content enriched with actionable CTI and metadata , reducing the need for manual rule creation.
- Global Cybersecurity Expertise: Leverages the expertise of a global community of security professionals, ensuring high-quality and effective detection rules, actionable CTI, and peer-to-peer validation
- Detection Engineering Capability Out of the Box: Provides complete CI/CD workflow to research, build, test, fine-tune, and deploy code in an automated fashion to multiple SIEM or EDR solutions.
- Automated Threat Hunting: Automates routine threat hunting tasks while not moving data or compromising on the number of rules to deploy.
“Leveraging SOC Prime Platform as a core source of threat intelligence enables SOC and CTI analysts to save at least 60 hours each month on threat research instead of drowning in overwhelming data.”
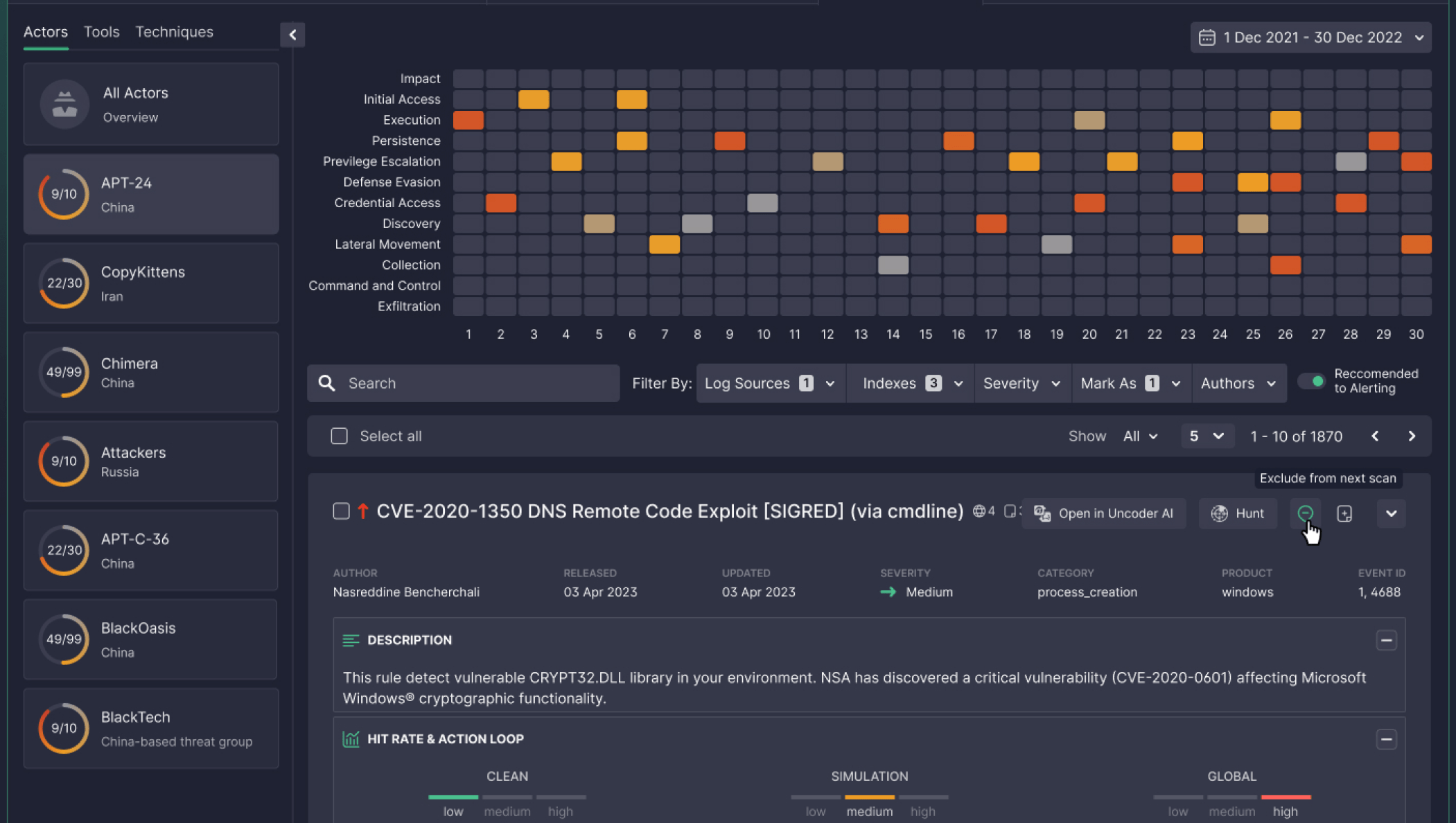
Figure 1. Running threat scans in Attack Detective to preempt attacks by specific adversaries
By automating the delivery and creation of detection rules, providing an enterprise-ready detection engineering suite, and serving packaged threat hunting capability, SOC Prime saves organizations considerable time. Security teams can rely on the updated repository of threat detection content and tools within SOC Prime Platform to suit their use cases and fortify the organization’s security posture while advancing threat detection & hunting at scale.
- Content Quality and Accuracy
Challenge: High rates of false positives can overwhelm security teams and obscure genuine threats, leading to alert fatigue and potential oversight of real incidents.
Solution: Threat Detection Marketplace, Attack Detective, Uncoder AI
- Custom Crafted Content: Each piece of detection content is crafted from scratch, ensuring high quality and specificity to each security environment. Additionally, cyber defenders can seamlessly customize any content piece within TDM using Uncoder AI to tailor detection rules & queries to their current security needs, environments, and objectives.·
- Quality Checks: Detection content in TDM undergoes thorough quality checks, guaranteeing its effectiveness and relevance before deployment.
- Experienced Security Team: Rules & queries are developed by a team with years of industry and SIEM-specific experience, ensuring that the strategies and methods are both proven and effective.
- Continuous Updates: TDM rule feed is continuously updated within a 24-hour SLA for emerging threats, keeping defenses up-to-date and effective against new and evolving threats.
- High-fidelity Alerting: SOC Prime’s Attack Detective provides security teams with prioritized SIEM rules perfectly aligned with their threat profile to generate low-noise, high-value alerts for comprehensive threat detection.
- Detection Content Validation: Implements an automated query validation process to assess your detections before promoting them to alerts and continuously check your SIEM rules for accuracy.
“Neurosoft has significantly improved MTTD and MTTR and cut down the false positive rate by up to 50% over the first 6 months of using the Platform.”
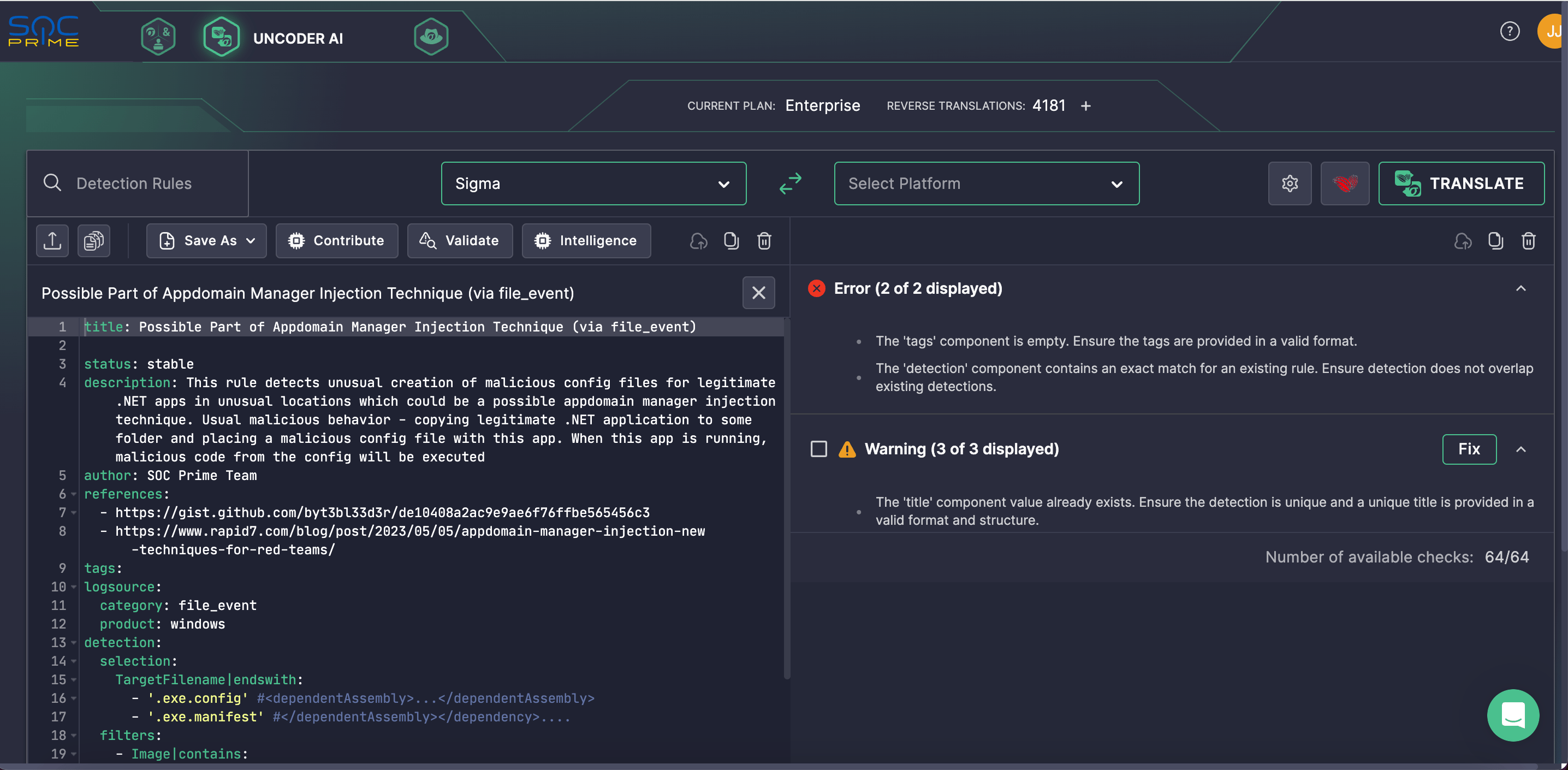
Figure 2. Running automated Sigma rule logic and syntax checks with a built-in Warden tool in Uncoder AI.
SOC Prime helps effectively combat the issue of high false positives, which can lead to alert fatigue and overlook real threats. It achieves this through custom-crafted content, developed from scratch and tailored to specific environments, ensuring high relevance and accuracy. Each content piece undergoes thorough quality checks by an experienced security team, guaranteeing its effectiveness. Furthermore, the content is continuously updated to keep pace with the latest threats, maintaining robust defenses against evolving cyber challenges.
- Staying Ahead of Emerging Threats
Challenge: The cybersecurity landscape is constantly evolving, with new threats emerging regularly. Staying ahead of these threats requires timely updates to detection content and strategies.
Solution: Threat Detection Marketplace
- Rapid Content Delivery: Ensures that detection rules are updated promptly to address new and emerging threats.
- Community-Driven Intelligence: Benefits from a collaborative approach, where experts share the latest threat insights and detection methods.
- Proactive Defense: Helps organizations maintain a proactive security posture by providing up-to-date threat detection content.
- Automation: Automates the updating and deployment of detection content, reducing manual effort and ensuring timely responses to new threats.
“DIRECTV Latin America relies on SOC Prime’s follow-the-sun detection engineering operations that ensure round-the-clock protection and proactive defense, leaving no chance for emerging threats, critical exploits, or adversary TTPs to go undetected.”
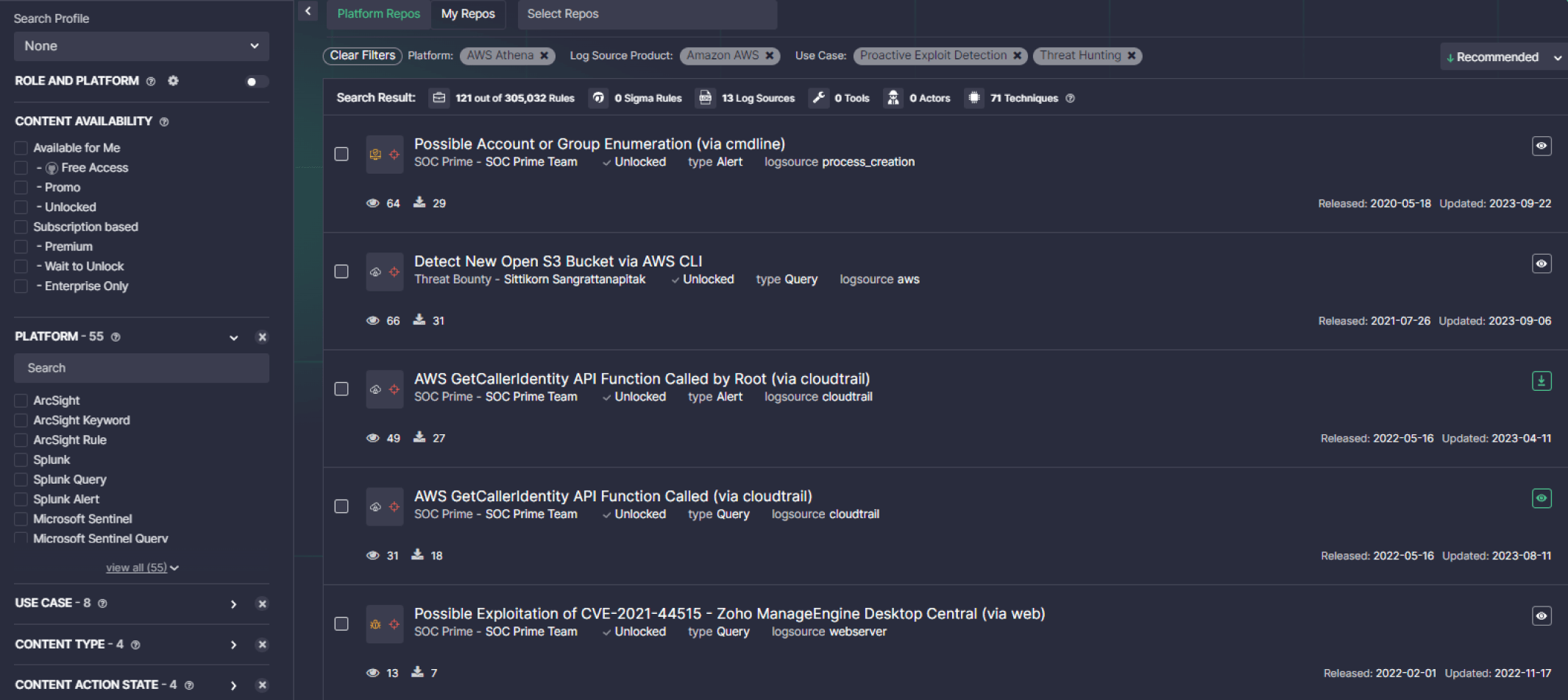
Figure 3. Searching Threat Detection Marketplace for prioritized detection content matching current security needs
Threat Detection Marketplace delivers content rapidly, ensuring organizations are always prepared for the latest threats. This proactive approach is supported by community-driven intelligence, where contributions from Threat Bounty hunters and other experts enrich the detection library. Organizations benefit from a diverse and comprehensive set of detection rules that keep them ahead of emerging threats.
- Attack Surface Visibility and Blind Spots
Challenge: Ensuring all relevant logs are collected is foundational for robust cybersecurity. It enables organizations to detect and respond to incidents promptly, provides forensic data necessary for investigating breaches, and helps maintain compliance with regulatory standards.
Solution: Attack Detective
- Data Audit: Analyze log data collected in your data planes to determine your coverage and potential gaps in log sources.
- Content Audit: Improve threat visibility by auto-mapping your rules & queries to MITRE ATT&CK with AI which does not leak your code.
- Rules for Alerting: Get prioritized SIEM use cases, easily configurable and ready-to-deploy as low-noise and high-value alerts.
- Threat Hunting: Deliver real-time, researched, and packaged threat hunting capability to your organization.·
“This allowed Deloitte Brazil to maximize available threat hunting resources while increasing the speed of threat detection operations, including a 200% increase in identification to expedite investigation and remediation.”
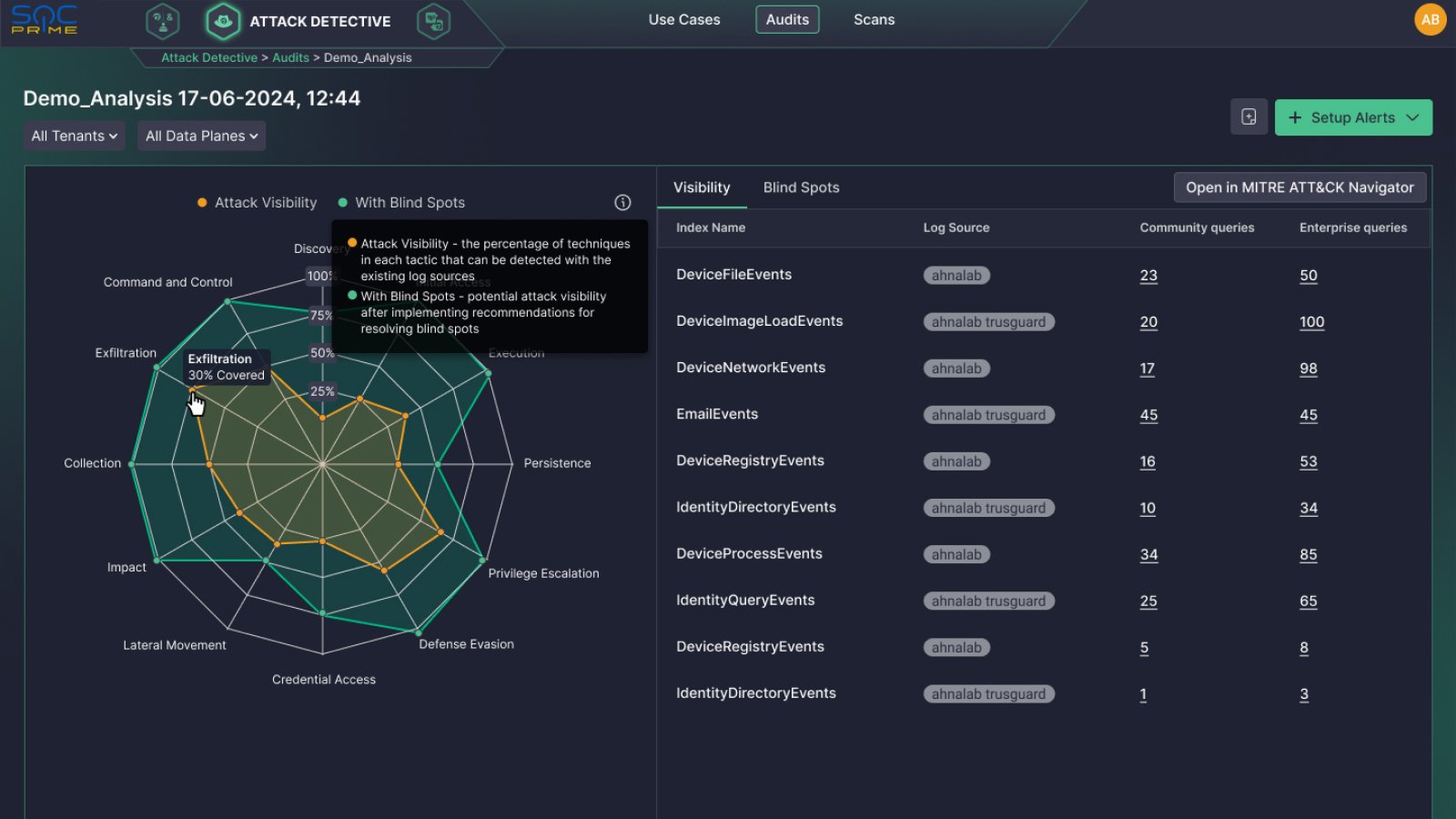
Figure 4. Running a Data Audit via Attack Detective to address threat detection blind spots with an actionable plan generated by mapping the data collected in your SIEM to MITRE ATT&CK®
Attack Detective enhances attack surface visibility by examining the data collected by the SIEM solution and mapping it to the MITRE ATT&CK® framework. This analysis helps identify any blind spots in the SIEM’s coverage, revealing which critical log sources are missing. This insight enables organizations to strategically adjust their SIEM configuration to capture a more comprehensive set of data. Importantly, the Data Audit component of Attack Detective also reveals which threat actors and tools the SIEM is blind to, as it identifies logs generated by these entities that are not being collected.
Additionally, Attack Detective allows for scanning the environment with custom hunting scenarios. It quickly filters through the results, maps them to ATT&CK, and then assists the users with verifying these results in their data plane. This crucial functionality helps organizations understand their exposure to specific threats and refine their data collection practices, ensuring no critical security data is overlooked. This comprehensive approach not only improves detection capabilities but also ensures that potential threats are accurately identified and addressed promptly.
- Unified Detection Content Management and Improved Efficiency
Challenge: Managing and automating security content across multiple platforms can be complex and time-consuming, leading to inefficiencies and potential gaps in security coverage.
Solution: Uncoder AI and Threat Detection Marketplace
- Unified Platform: SOC Prime’s Threat Detection Marketplace provides a centralized repository for threat detection content, simplifying its management and deployment.
- Cross-Platform Compatibility: Uncoder AI enables automated cross-platform rule and query translation for multiple SIEM, EDR, and Data Lake languages, ensuring consistent and comprehensive threat detection.
- Customization and Fine-Tuning: Tailor detection rules to fit specific environments and reduce false positives with filtering, exclusions and custom field mapping. Utilize Uncoder AI’s powerful Sigma rule editor for an IDE-style experience, enabling conversion of detection content across multiple SIEM, EDR, and Data Lake formats, and parsing security reports or advisories into actionable queries.
- Streamlined Use Case Management Lifecycle. Save hours on repetitive tasks and adopt a full CI/CD workflow, allowing security teams to focus on what matters most rather than routine maintenance. Rely on Threat Detection Marketplace and Uncoder AI to customize out-of-the-box use cases for complex Detection-as-Code projects, seamlessly deploy no matter the complexity of your infrastructure, save and manage detections in a separate encrypted storage hosted at SOC 2 Type II AWS private segment, and automate code documentation with AI.
“LTI saved 4K hours per year on content R&D while increasing SOC efficiency by continuously streaming the latest detection algorithms directly into customers’ SIEM & EDR.“
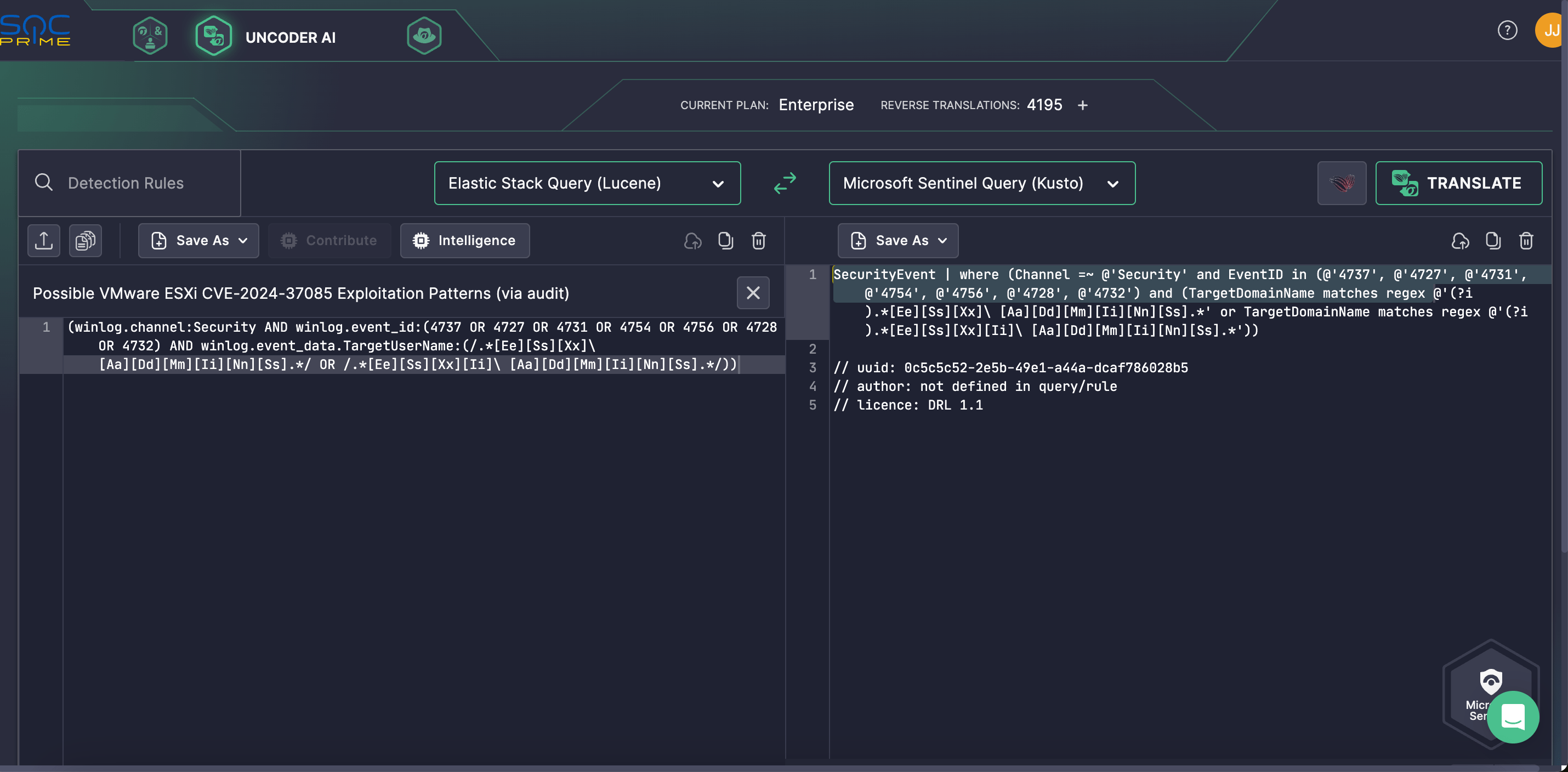
Figure 5. Automated cross-platform query translation via Uncoder AI
SOC Prime’s unified approach to detection content management and automation enhances operational efficiency. By providing a centralized platform and automating routine tasks, security teams can manage their detection content more effectively. This reduces the complexity and time associated with maintaining consistent threat detection across multiple platforms, ensuring a robust and cohesive security strategy.



