FormBook/XLoader Malware Is Leveraged to Target Ukrainian Government Bodies: CERT-UA Warning

Table of contents:
This article highlights the original research conducted by CERT-UA: https://cert.gov.ua/article/37688
On March 9, 2022, the Computer Emergency Response Team of Ukraine (CERT-UA) reported that Ukrainian government bodies were hit by a cyber-attack using the FormBook/XLoader malware. The malware was delivered if the user opened a malicious email attachment.
FormBook and its more recent successor XLoader are information stealers distributed as Malware-as-a-Service (MaaS). They are used to get user input, take screenshots, and even search for and interact with files on the infected machine.
Ukrainian Government Targeted by FormBook/XLoader: CERT-UA Research
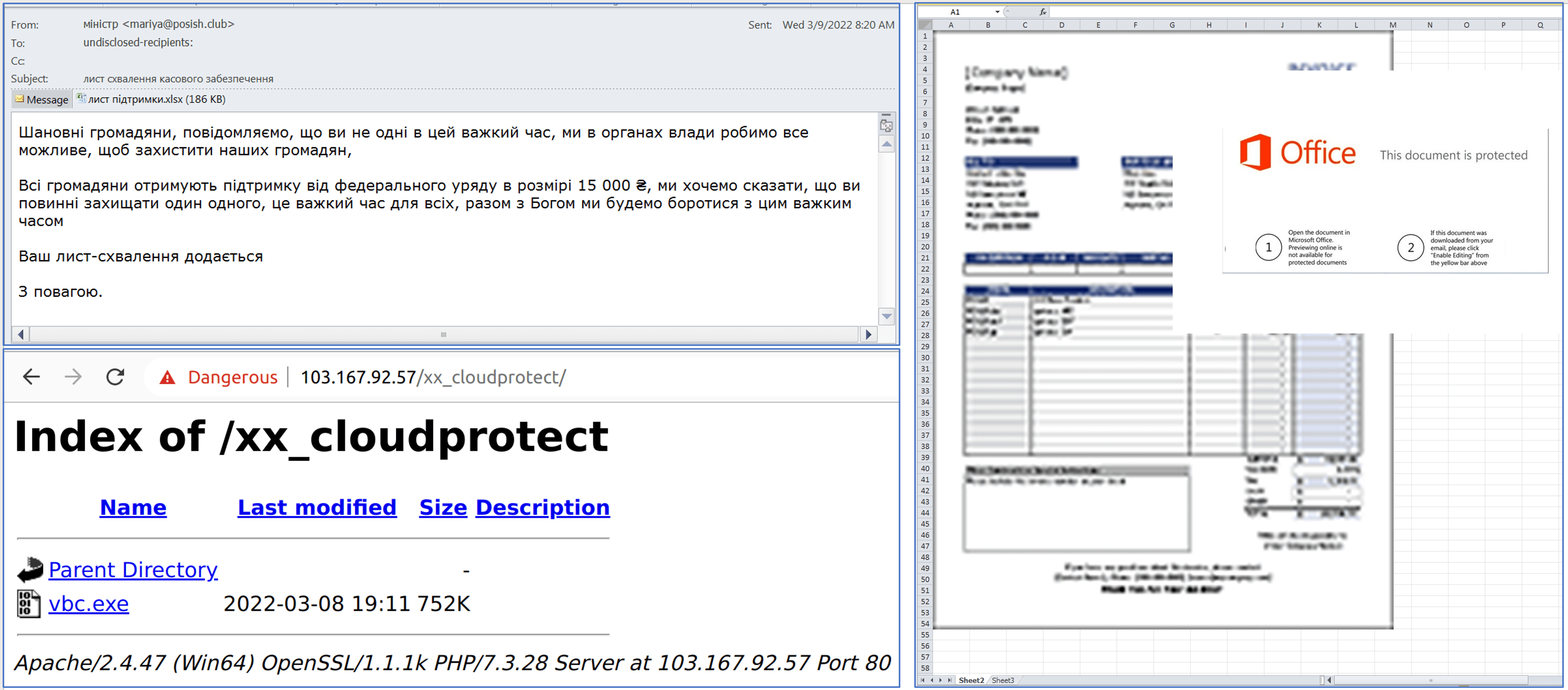
An email with the subject “Letter on approval of cash provisioning” was massively sent to Ukrainian government bodies. The content of the email is related to the war and providing financial aid (apparently, the text was automatically translated into Ukrainian).
The email has an XLS attachment named лист підтримки.xlsx. If opened, it activates a macro that downloads and runs FormBook/XLoader v2.5 malware. Yet, the document’s bait content does not seem to be relevant for Ukrainian citizens.
The malware steals credentials stored in the software on the affected machine and sends them to the attackers’ command-and-control (C&C) server.
Such attacks have a systemic nature and are associated with the activity cluster tracked under UAC-0041 identifier.
Global Indicators of Compromise (IOCs)
Files
93feeeab72617e4f5630fd79f2fdd4b6 лист підтримки.xlsx 95d60664267d442e99c41e2aa3baff68 vbc.exe 5a2c58b9ad136ecaea903e47ca7d0727 formbook.exe (Formbook)
Network Indicators
mariya@posish[.]club 104[.]168.247.233 hxxp://103[.]167.92.57/xx_cloudprotect/vbc.exe 103[.]167.92.57 gobits3[.]com
The list of false domain names: humamzarodi[.]info cillacollection[.]com phy[.]wiki londonkhaboos[.]com robostetics[.]com bryanheritagefarm[.]com writingdadsobituary[.]com uitzendstudent[.]online kaeltefath[.]com ooop63[.]website oncasi-tengoku[.]com weihiw[.]store gameshill[.]net clublebron[.]com fromuktosa[.]com hilversumrp[.]com formigocerdanya[.]com jokeaou[.]com bvgsf[.]xyz reallyreadyservices[.]com zrbusiness[.]com homephotomarketing[.]com evpunk[.]com hermanmitchels[.]com globalprotectionllc[.]com carlab[.]rentals aocpaysage[.]com g3kbwq[.]xyz ojosnegroshacienda[.]com greenvilletaxfirm[.]com circuitoristorazione[.]com chicklet[.]biz allegiancebookkeeper[.]com xyyvivo[.]com cassandracheatham[.]com gobits3[.]com upcxi[.]xyz adjd[.]info hdwix[.]online sbxtv[.]info abodhakujena[.]com yhomggsmtdynchb[.]store jeffreylau[.]xyz lovelypersonal[.]com lwmdqj[.]com tapelm[.]com ulasan-online[.]com roleplayhr[.]com avilarts[.]com marygracerenella[.]com yellowumbrellamarketing[.]com ilyapershin[.]com bellkennedy[.]online muhammadsaqib[.]tech certuslogistics[.]com unforgettableamour[.]com jtelp[.]com movinonuprva[.]com xn--ltda-epa[.]com knolmail[.]xyz houstonorganicpestcontrol[.]com befancie[.]com typejitem[.]store zqt2578[.]com astrologyplatform[.]com
Hosts Indicators
%PUBLIC%\vbc.exe
IOC-Based Hunting Queries to Detect FormBook/XLoader
To enable security practitioners to automatically convert the above-mentioned IOCs into custom hunting queries ready to run in nearly 20 most popular SIEM or XDR environments, SOC Prime Platform offers the Uncoder CTI tool — now available for free for all registered users through May, 25, 2022.
Sigma Behavior-Based Rules to Detect FormBook/XLoader
To detect FormBook/XLoader behavior patterns and activity associated with this malware, security professionals can use the dedicated Sigma behavior-based content published in the SOC Prime Platform:
FormBook Malware Behaviour (ColorCPL-LSASS Spawns CMD)
Suspicious execution of colorcpl.exe (via cmdline)
MITRE ATT&CK® Context
To help security practitioners better understand the context of an attack using FormBook/XLoader, all Sigma-based rules that detect it are aligned with the MITRE ATT&CK framework addressing the following tactics and techniques:
Tactics | Techniques | Sub-techniques | Sigma Rules |
Execution | Command and Scripting Interpreter (T1059) | ||