Extended Community Access and Free Trials at the Threat Detection Marketplace

At SOC Prime, we are constantly developing our products that help cybersecurity practitioners to be in sync about the latest threats and attack methods as well as have detections and analytical data tailored to each corporate environment at their fingertips. For more transparency, the newly introduced Dashboard page allows getting a line on activities of your company on Threat Detection Marketplace (TDM) to analyze how your company has excelled in threat detection and identify the trend as compared with the industry leaders.
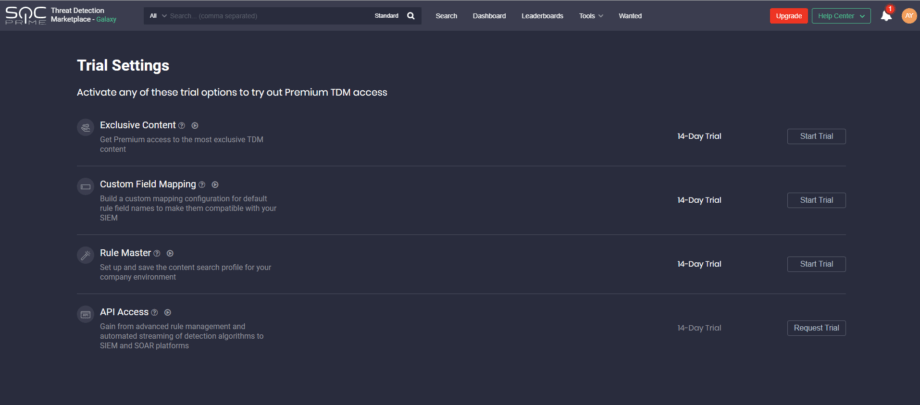
Free Trial Access to Premium features
“Until today, we have run TDM as a freemium / premium SaaS platform which was working out quite well for both community and paid clients. One shortcoming we saw is that getting a taste of premium features and rules was a process that involved too many manual steps. With the latest update, it is now possible to get more value out of community access by actively collaborating with your peers and try paid features previously available only as part of paid subscriptions. This includes API Access, Exclusive threat detection and threat hunting content including Threat Bounty, Custom Field mapping and redesigned Rule Master that is getting more filtering improvements.” – Andrii Bezverkhyi, CEO, SOC Prime
The latest update of SOC Prime Threat Detection Marketplace unleashes the full power of the TDM functionality by introducing the Free Trial access to Premium features for enhanced community experience depending on the individual security needs.
Open access to Exclusive content
TDM Free Trial opens access to Exclusive content that allows exploring a unique rule set mapped to MITRE ATT&CK® and covering the latest threats. Users who have activated this trial feature can now try out viewing and downloading Exclusive threat hunting content that was previously available for paid subscriptions only. The prominent amount of the most relevant detection content developed by Threat Hunters of SOC Prime Threat Bounty Program, including the rules developed exclusively to address the Wanted List requests, is also easily accessible with the Exclusive Content option enabled.
The unlimited access to Community threat detection content is available at Sigma rules repository mirror empowered with full-text sub-second search on CVEs, MITRE ATT&CK techniques, and more.
Custom Field Mapping
The enhanced Custom Field Mapping functionality was earlier accessible only to users with paid subscriptions. Now, this feature is available as part of the Free Trial. Users can configure their environment profile with customized SIEM field names to minimize manual fine-tuning of the downloaded content and avoid parsing issues. With the enabled Custom Field Mapping feature, TDM users can create a customized data schema profile of their SIEM instance and deploy threat hunting content tailored to their SIEM environment on the fly. Read more about the Custom Field Mapping here.
Rule Master
TDM Free Trial uncovers another feature for obtaining the most relevant content depending on the company infrastructure. For security practitioners who are exploring the Threat Detection Marketplace to get the best fitting content, SOC Prime suggests trying out Rule Master that allows setting up a company profile with the specified environment characteristics. With Rule Master configured and enabled, you can search for the threat detection content which is not only the most relevant to address the specific security needs, but also neatly matching your company’s infrastructure and your particular threat profile based on MITRE ATT&CK.
TDM API
One more advantage is unlocking access to the TDM API that was earlier available only for a limited number of paid subscriptions. Users who have started the trial can test out the advanced management of Sigma rules. With the activated API access, working with rules is much easier. Instead of logging in to the platform and using the interface to search for the rules you wish to obtain, you can simply set up an automated query to find particular rules. You can download all Sigma rules with enabled API access on the fly gaining from the content streaming functionality directly into your SIEM such as Microsoft Azure Sentinel, Sumo Logic, Elastic stack, Splunk, and others.
With Free Trial features enabled, users with the Freemium subscription can look up to the best practices introduced by 9,000+ TDM cyber community members through active participation in determining the vector and priorities of new threat detection research and development.
Free Trial access to Premium features allows not only trying out the enhanced platform functionality, but also getting valuable feedback on users’ experience with Threat Detection Marketplace and sharing it with the community. Users with Community subscription now have an unprecedented chance to run these Premium features during the trial period.
We are working on the next set of advanced community features which will proportionally reward most active members and contributors with exclusive features and content. The release is set for later this summer.