With the release of the SOC Prime Platform for collaborative cyber defense, threat hunting, and threat discovery, the capabilities to fully automate detection content streaming have been also taken to a new level. Now, the Continuous Content Management module is available to all users registered on the SOC Prime Platform with a corporate email address, on a threshold-based availability depending on their active Subscription plan.
With a broad set of supported security solutions for integration, Continuous Content Management enables streamlined threat detection operations for the following cloud-based SIEM & XDR platforms:
- Microsoft Azure Sentinel
- Elastic Cloud
- Humio
- Sumo Logic
- Google Chronicle Security
Apart from the cloud-native SIEM & XDR stack, the Continuous Content Management module also supports on-premise Splunk and Elastic Stack solutions. Leveraging the SOC Prime CCM App for Splunk, security engineers can continuously stream new rules and update the existing ones into their on-premise Splunk instance. Check out the installation guidelines and get the SOC Prime CCM App for Splunk right from the Splunkbase. Streaming of detection content to both the Splunk and Elastic Stack on-premise instances is available via the TDM API Integration Tool.
The cloud-native support for the Splunk App is coming soon, which will enable security engineers to stream detections into their cloud Splunk instance via the SOC Prime Threat Detection Marketplace API.
Content Lists
To automatically deploy detections into the security solution in use, SOC teams can arrange content into structured Content Lists. SOC Prime has arranged Global Content Lists with detections addressing the most common areas of concern.
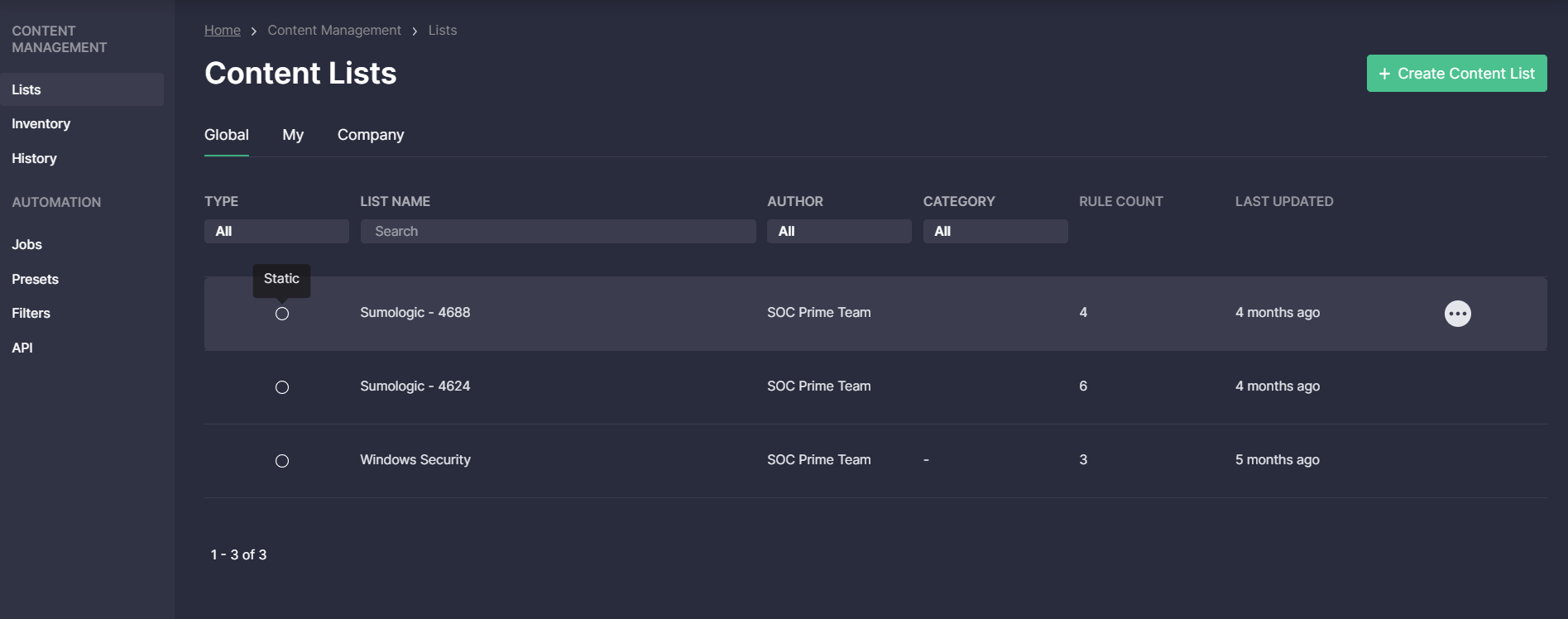
These lists are available to all security teams using the SOC Prime Platform. In a similar way, security engineers can create Content Lists and share them with their teams within the SOC Prime Platform.
- With Statiс Content Lists, teams can arrange content selected for certain purposes.
- Dynamic Content Lists enable to continuously deliver updated and released detections as per pre-configured parameters of the required content.
- With Inventory Content Lists, security engineers can deploy content to their different SIEM & XDR instances separately via a separate Job, as well as keep the local copy of the changes made to the detection content of the Inventory page.
SOC teams can create new Lists from the scratch or make copies of the existing Lists and customize them. Also, to make the most of automated delivery and adoption of content from Threat Detection Marketplace, security engineers can specify filtering parameters within the List to receive only the content that addresses their needs.
Continuous Content Management allows security engineers to administer the process of automated content adoption and gain a clear picture of the deployment results.
Jobs
By scheduling and running Jobs, SOC teams can automatically deploy the latest detections into their SIEM or XDR instance. To add more flexibility to content management operations, a single Job can be created specifically for a certain Content List, linked to the selected platform and a specific content type. Similarly, multiple Jobs can be linked to a single List and pushed to the same or different SIEM or XDR instances. For more convenience, Jobs can be set based on a custom data schema to have more control over content deployment and stream content in the preferred data schema format. In addition, security engineers can set up Jobs for content deployment based on the alternative translation formats for Azure Sentinel, Sumo Logic, and Elastic Cloud environments.
On the Jobs page, teams can keep track of successful and failed Content List deployments performed by a certain job and easily debug logs. In the case of deployment issues with a certain Content List, security engineers can drill down to the History page and find the error details of each content item within the List.
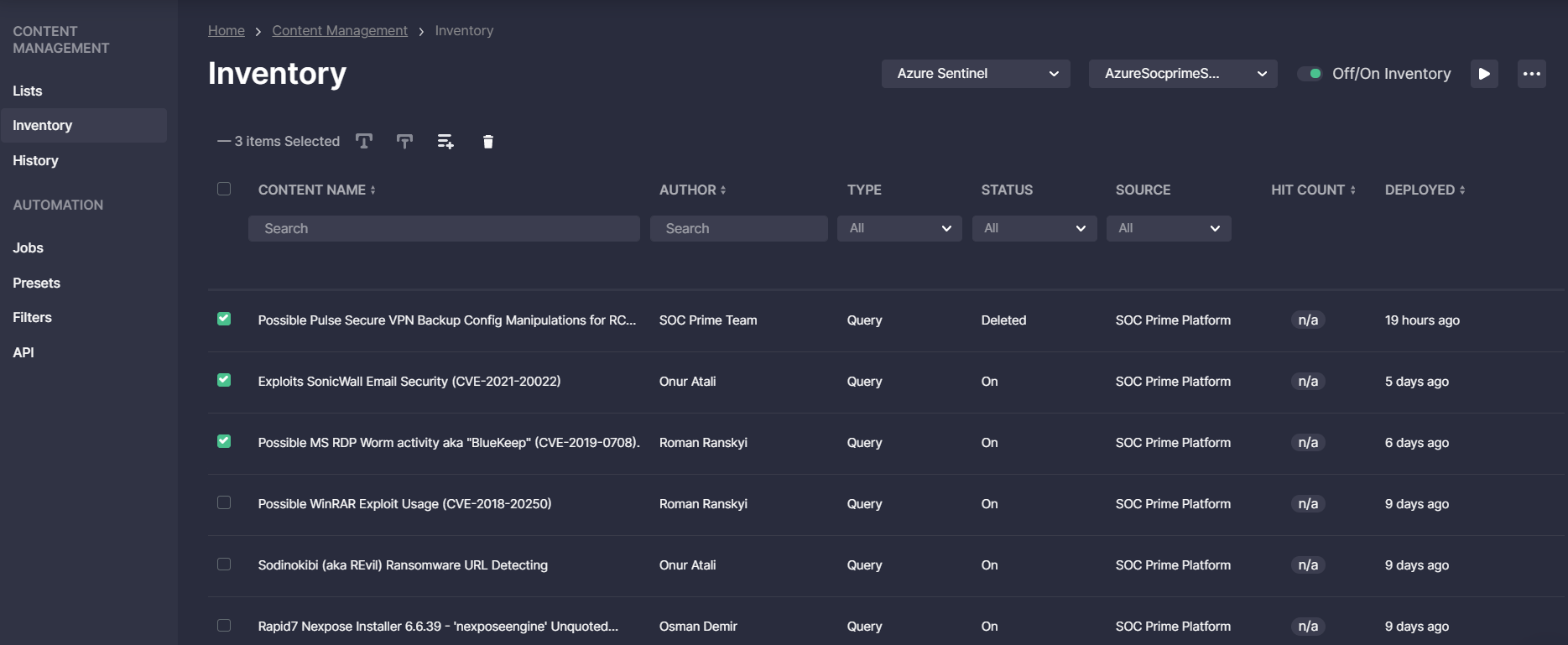
Inventory
With Inventory, SOC teams can review and update detections related to the selected SIEM or XDR instance and linked to a specific environment. Here they can track the content author and its source, the deployment date, hit count, and other details of each content item on the Inventory list. Security engineers can also update detections right from the Inventory page and then deploy the changes into their environment.
The Inventory page allows managing selected content items in a single place by enabling or disabling them, adding to the existing or new Content List, or removing content that is no longer needed. When choosing to remove a single content item or a set of them, security engineers can delete this detection from the Inventory list only or from the SIEM or XDR instance as well.
Presets and Filters
With Continuous Content Management, security teams can customize automated content deployment conditions to address their security requirements and avoid large amounts of false positives.
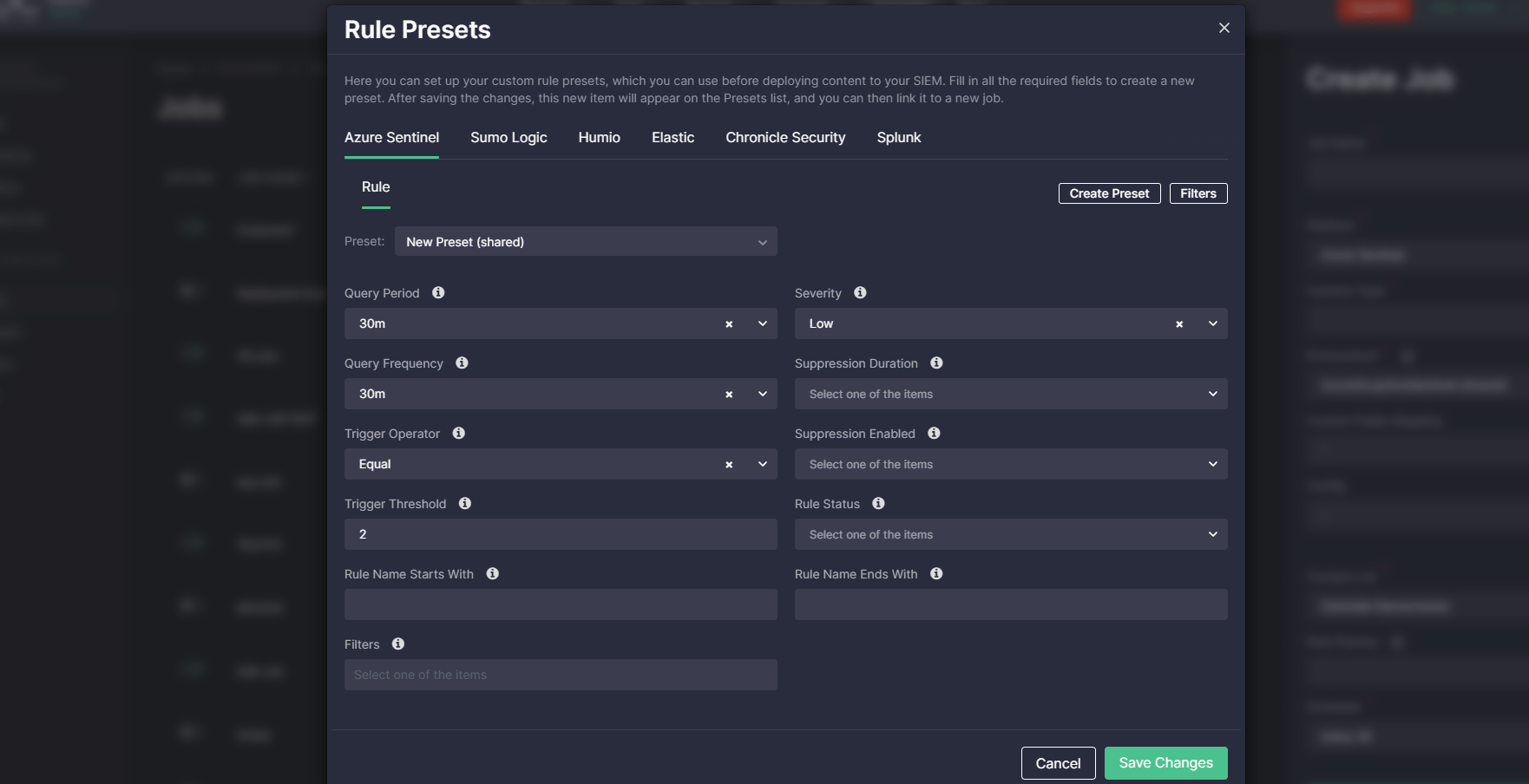
Filters allow security teams to add extra conditions to detection logic before deployment, such as including/excluding specific users, hosts, etc.
With Presets, security engineers can customize automated deployment taking into account the peculiarities of their SIEM or XDR instance settings. Linking Presets to Jobs helps streamline content management operations and avoid errors that can occur when manually editing content.
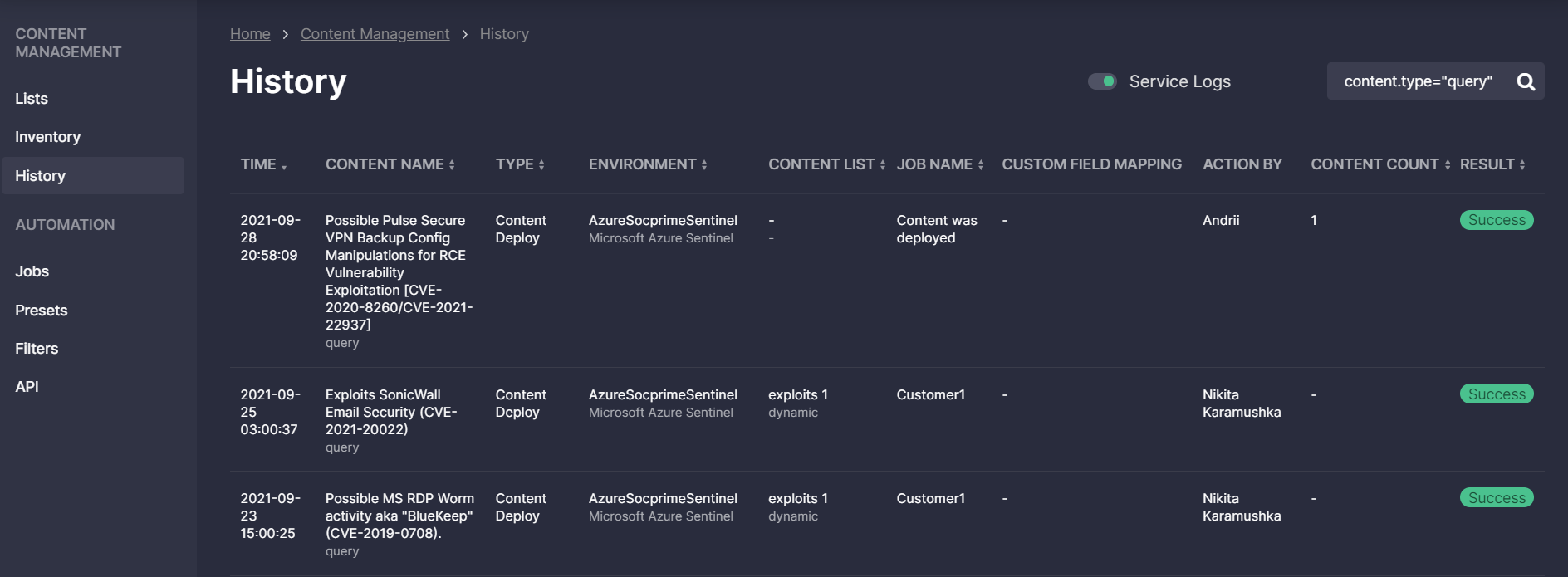
History
Security teams can view the complete history of automatic and manual actions within the Continuous Content Management module. Here engineers can look into all the logs from Jobs, manual deployments, and updates. Selecting log displaying preferences, teams can look into logs that are more informative to them — to focus on content-related activities, like deployment results, and keep the Service Logs hidden from the History page. Continuous Content Management also allows browsing the log history and looking into specific logs using the Lucene search query syntax.
Information about the actions logged in History is also available, with status-related details on content deployments — results of a successful deployment, or issue and error details for a failed content deployment attempt.
Searching for the best SOC content compatible with your SIEM, EDR, and NTDR solutions in use? Explore the SOC Prime Platform to address your custom use cases, boost threat discovery and threat hunting, and get a complete visualization of your team’s progress. Passionate about threat hunting and eager to contribute to the industry-first SOC content library? Join our Threat Bounty Program!