Since the outbreak of the global cyber war, SOC Prime stays on the frontline helping Ukraine and its allies defend from russian aggression. On December 8, 2022, CERT-UA researchers received information from the cybersecurity department of the state Railway Transport Organization of Ukraine “Ukrzaliznytsia” about the distribution of phishing emails impersonating the State Emergency Service of Ukraine. In addition, hackers applied a fake domain email to masquerade their malicious activity. The phishing emails used in this cyber attack applied a lure related to the use of Iranian Shahed-136 drones.
DolphinCape Malware Description: The Latest Cyber Attack on Ukrainian State Organizations
The latest CERT-UA#5683 alert details a new malicious campaign against the state Railway Transport Organization of Ukraine “Ukrzaliznytsia” leveraging the phishing email attack vector and attributed to the UAC-0140 hacking collective. In this attack, threat actors distribute emails with a subject lure promising to unveil information on how to identify the Iranian Shahed-136 drones.
The infection chain is triggered by opening a lure attachment with a RAR file that contains a PPSX document with malicious VBScript code. The latter is designed to generate a scheduled task, as well as to decrypt, create, and launch a PowerShell script. Hackers apply an RC4 encryption algorithm and a key created by a string concatenation of the attribute value “Manager” and the file name. The malicious PowerShell script applies the BITS component of Microsoft Windows to download DLL and EXE files and create a scheduled task to launch the latter via a DLL side-loading technique.
The DLL file is identified as DolphinCape malware developed with Delphi. This malicious software collects information about the hostname, username, OS version, and exfiltrates other data from the compromised computers, launches EXE and DLL files, and displays the list of files and their upload. DolphinCape malware is also capable of capturing screenshots from the targeted machines.
Detecting DolphinCape Malware Campaign by UAC-0140
Multiple phishing campaigns keep targeting the Ukrainian critical infrastructure and online assets as the war escalates in the cyber domain. Following several massive attacks by Armagedon APT (UAC-0010), the latest CERT-UA alert reveals yet another campaign leveraging DolphinCape malware to target the Ukrainian transportation system. As russia-backed hackers frequently test malicious tools and approaches on the battlefield in Ukraine before expanding their activities globally, security practitioners from all over the world need a reliable source of detection content to stay proactive and leave no chance for adversaries to hit.
SOC Prime’s Detection as Code platform offers a batch of curated Sigma rules to identify the related malicious activity covered in the CERT-UA#5683 alert at the earliest stages of the attack lifecycle. Hit the Explore Detections button and access the dedicated detection stack. All Sigma rules are aligned with the MITRE ATT&CK® framework and enriched with extensive cyber threat context, including CTI links, mitigations, executable binaries, and more relevant metadata. Detection rules are packed with translations to the industry-leading SIEM, EDR, and XDR solutions.
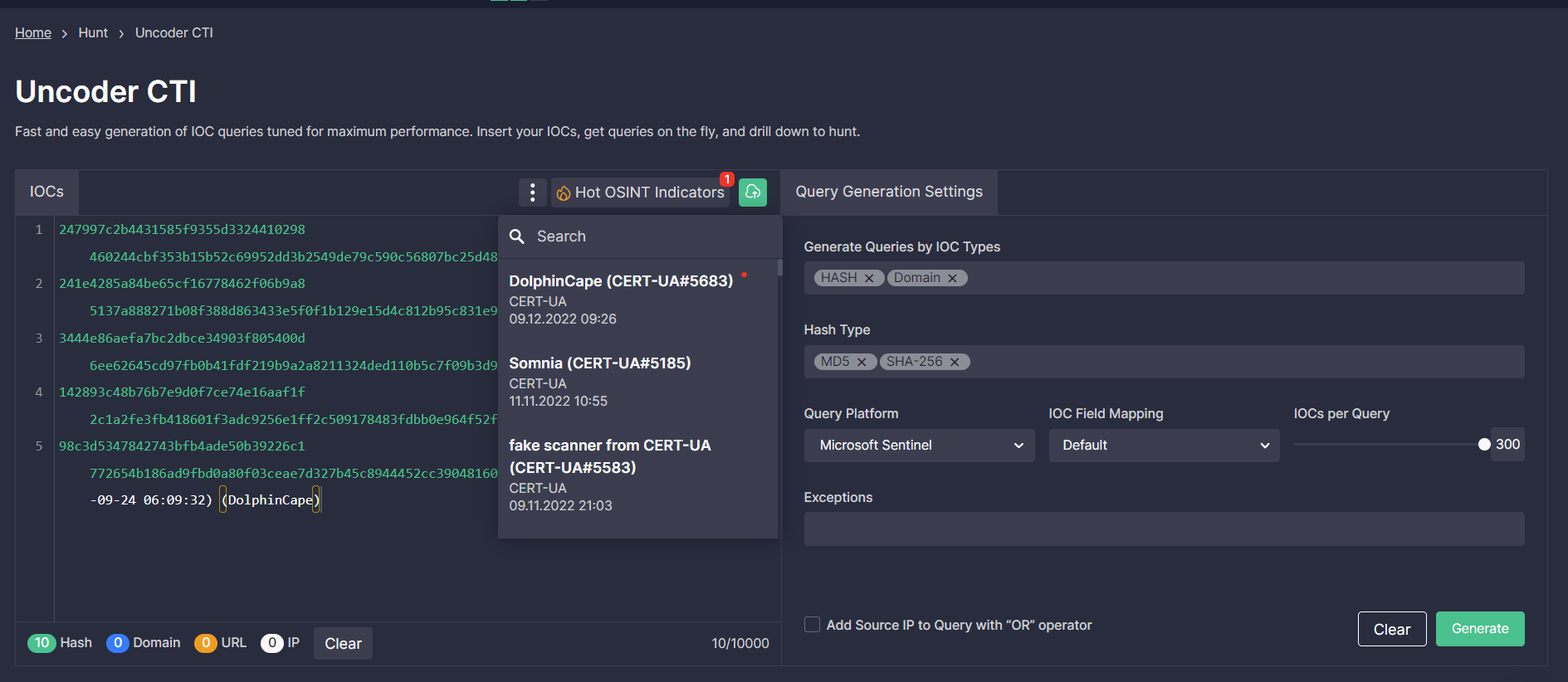
Security engineers can also streamline their search for threats related to the DolphinCape malware distribution using file, host, and network IOCs covered by the CERT-UA#5683 alert. With the help of Uncoder.CTI, teams can instantly generate performance-optimized IOC queries and drill down to search for relevant threats in the selected SIEM or XDR environment.
MITRE ATT&CK® Context
To explore the MITRE ATT&CK context related to the DolphinCape malware distribution by the UAC-0140 threat actors in the latest phishing campaign against Ukraine, check out the table below. All dedicated Sigma rules are aligned with MITRE ATT&CK addressing the corresponding adversary tactics and techniques:




