The Lazarus Group, a notorious North Korea-backed hacking collective also tracked as APT38, Hidden Cobra, and Dark Seoul, has built a long-standing reputation as one of the most dangerous advanced persistent threat groups. Active since at least 2009, Lazarus has consistently targeted financial institutions and, more recently, cryptocurrency and blockchain businesses to fuel the regime’s illicit revenue streams.
Over the past years, researchers have observed multiple campaigns by a Lazarus subgroup (aka AppleJeus, Citrine Sleet, UNC4736, Gleaming Pisces), all focusing on crypto exchanges, trading platforms, and high-profile financial organizations. One of the most high-profile examples was the TradeTraitor campaign in April 2022, which targeted investment firms, wallet holders, and NFT users through sophisticated social engineering tactics.
True to their playbook, Lazarus often exploits older vulnerabilities to deploy custom RATs. Their latest campaign highlights this continued strategy, delivering cross-platform malware families PondRAT, ThemeForestRAT, and RemotePE via social engineering tricks and zero-day exploitation, demonstrating not only the group’s persistence but also its evolving technical sophistication.
Detect Lazarus Group Attacks Using PondRAT, ThemeForestRAT, and RemotePE
Cybercrime is projected to cost the world $10.5 trillion annually by the end of 2025, driven by increasingly sophisticated, financially motivated attacks. As digital threats grow more complex, financially driven groups like Lazarus cluster remain active, inventing novel malicious methods to increase their profits.
Register for the SOC Prime Platform to obtain a curated set of Sigma rules to detect malicious activity associated with the Lazarus Group, leveraging the triple RAT arsenal. The detections are backed by a complete product suite for AI-powered detection engineering, automated threat hunting, and advanced threat detection. Just hit the Explore Detections button below and immediately drill down to a relevant detection stack.
Cyber defenders seeking more relevant content to detect cyber-attacks linked to the Lazarus Group might access the entire сollection of relevant detection algorithms by searching the Threat Detection Marketplace with the “Lazarus” tag.
All the rules are compatible with multiple SIEM, EDR, and Data Lake technologies, and mapped to MITRE ATT&CK® to streamline threat investigation. Additionally, each rule is enriched with extensive metadata, including CTI references, attack timelines, audit configurations, triage recommendations, and more.
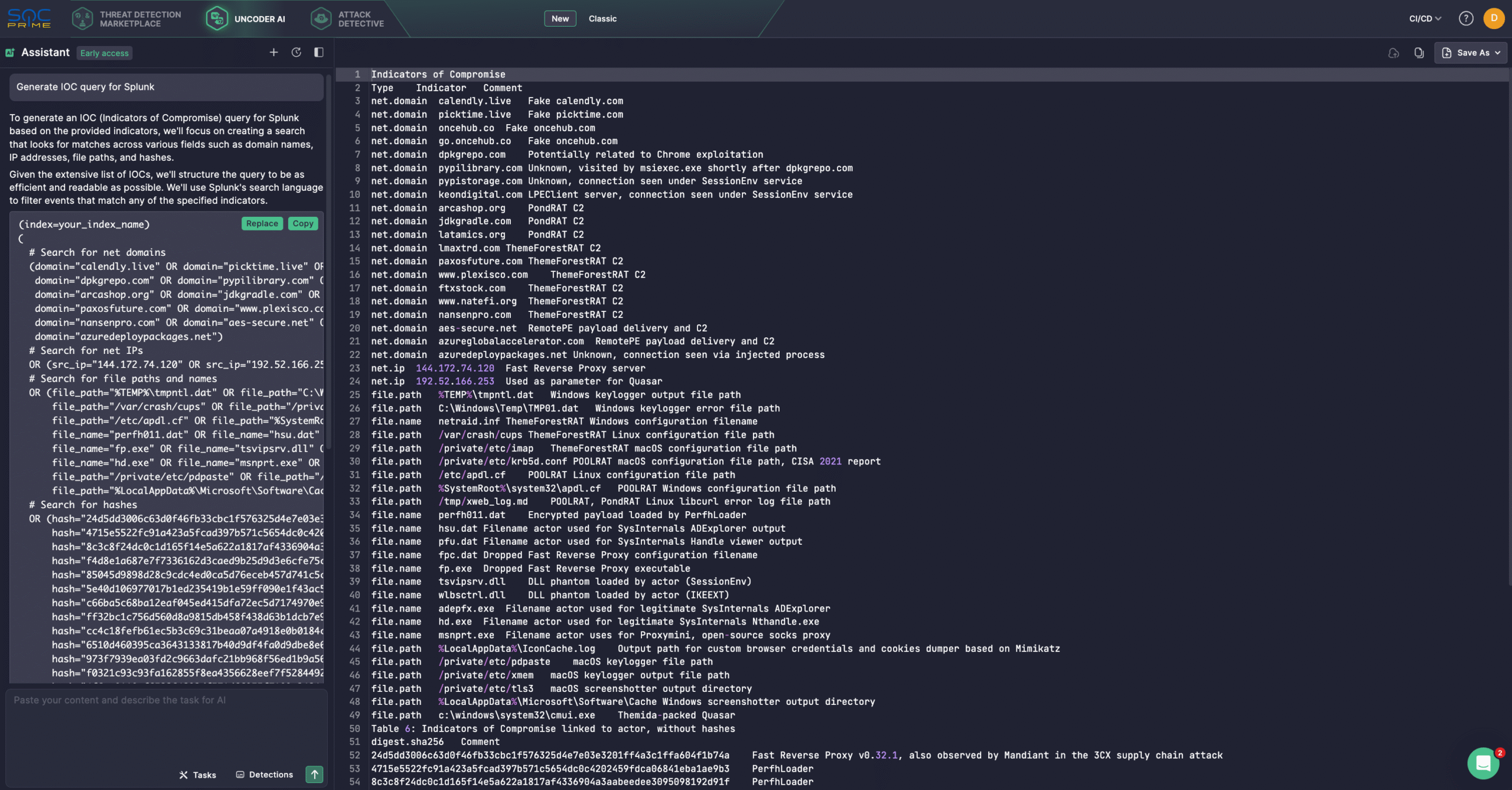
On top of it, security experts might streamline threat investigation using Uncoder AI, a private IDE and co-pilot for threat-informed detection engineering. With Uncoder, defenders can automatically convert IOCs from the dedicated Fox-IT and NCC Group report into actionable hunting queries, enabling efficient investigation of Lazarus activity. Additionally, Uncoder supports crafting detection logic from raw threat reports, ATT&CK tags prediction, AI-driven query optimization, and detection content translation across multiple platforms.
Lazarus Group Attacks Analysis
Researchers from Fox-IT and NCC Group have uncovered new activity tied to a cluster of the Lazarus Group associated with AppleJeus, Citrine Sleet, UNC4736, and Gleaming Pisces. This financially motivated subgroup has been linked to a recent social engineering campaign delivering three distinct pieces of cross-platform malware: PondRAT, ThemeForestRAT, and RemotePE.
The campaign, observed in 2024, specifically targeted organizations in the decentralized finance (DeFi) sector, ultimately compromising an employee’s system. Once inside, the attackers used a mix of remote access trojans and supporting tools to conduct internal discovery, steal credentials, and perform other malicious activities.
The attack chain starts with social engineering, where Lazarus operators pose as employees of trading companies on Telegram and direct victims to fake scheduling sites mimicking Calendly and Picktime. In 2024, researchers suspect a Chrome zero-day was exploited in some cases. This mirrors earlier reporting on Citrine Sleet’s use of Chrome exploits to deliver the FudModule rootkit.
While the initial access vector is not fully confirmed, investigators found that the intrusion led to the deployment of a loader called PerfhLoader, which dropped PondRAT, a stripped-down variant of POOLRAT. Alongside PondRAT, the attackers delivered additional tools, including a screenshotter, keylogger, Chrome credential stealer, Mimikatz, FRPC, and proxy software.
PondRAT has been in use since 2021. It provides basic RAT functionality, such as reading and writing files, running processes, and executing shellcode. For several months, the group combined PondRAT with ThemeForestRAT before switching to a stealthier RAT known as RemotePE.
Specifically, once deployed, PondRAT can load ThemeForestRAT directly in memory or through a dedicated loader. ThemeForestRAT offers far broader functionality, supporting more than twenty commands to enumerate files and drives, manipulate processes, delete data securely, test network connections, and inject shellcode. It also demonstrates environmental awareness by monitoring RDP sessions and USB device activity.
The final stage in the attack chain is RemotePE, a more sophisticated C++ RAT retrieved via RemotePELoader and DPAPILoader. Reserved for high-value targets, RemotePE leverages Windows Data Protection API (DPAPI) for environmental keying, making it far harder to analyze without access to the original victim system.
This progression, from PondRAT to ThemeForestRAT and ultimately RemotePE, shows how Lazarus carefully layers tooling, starting with simple loaders and escalating to stealthier, feature-rich implants. To stay ahead of potential intrusions. SOC Prime Platform equips security teams with a complete enterprise-ready product suite powered by the fusion of AI, automation capabilities, and real-time threat intel to enable progressive organizations to preempt sophisticated attacks and minimize the risks of data breaches.




