At the end of summer, 2024, the FBI, Department of Defense, and CISA issued a joint advisory warning cybersecurity experts of a rise in operations by Iran-affiliated adversaries known as Pioneer Kitten. The U.S. cybersecurity authoring agencies in collaboration with international partners have recently issued another advisory AA24-290A covering the increasing activity of Iranian threat actors leveraging brute force and credential access in their offensive operations to compromise organizations in various critical infrastructure sectors. Iran-linked adversaries are aimed at stealing credentials and network information, which can be sold to cybercriminals to facilitate further access.
Detecting Cyber-Attacks by Iranian Hackers Described in AA24-290A CISA Advisory
In 2024, APT groups from various global regions, including Iran, China, North Korea, and russia, showcased a notable surge in dynamic and innovative offensive capabilities. Iranian-backed hackers, recognized as one of the most formidable APT threats, are creating significant challenges for the global cybersecurity landscape through persistent attack strategies. The most recent AA24-290A advisory by U.S. state agencies and international partners warns of a surge in credential access and brute-force attacks by Iranian state-sponsored adversaries, underscoring the heightened risks facing critical infrastructure, government, healthcare, and energy sectors worldwide.
To stay on top of the avalanche of attacks, security professionals can rely on SOC Prime Platform for collective cyber defense serving a complete product suite for advanced threat detection, AI-powered detection engineering, and automated threat hunting. Platform users might access the latest threat intel and curated detection rules for emerging threats released under 24-hour SLA.
Press the Explore Detections button below to immediately drill down to a dedicated Sigma rule stack addressing TTPs described in AA24-290A advisory. All the Sigma rules are mapped to the MITRE ATT&CK® framework, enriched with tailored intelligence, and convertible to 30+ SIEM, EDR, and Data Lake language formats. Alternatively, cyber defenders might use “AA24-290A” tag for a tailored search in Threat Detection Marketplace.
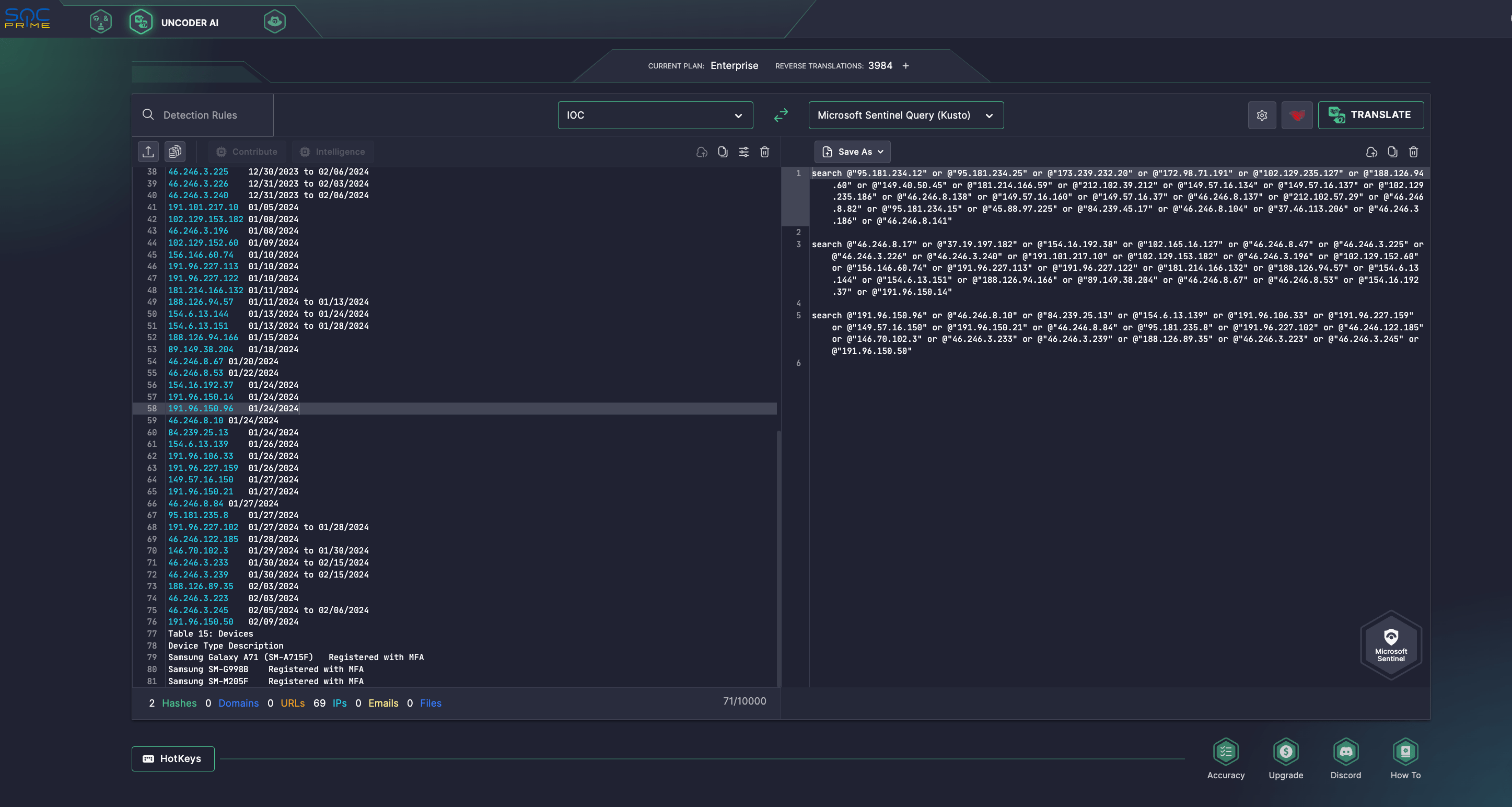
Security engineers can also take advantage of Uncoder AI to accelerate IOC packaging and retrospective hunting for adversaries TTPs used in credential access and brute-force attacks using IOCs from the corresponding advisory by instantly converting them into custom queries matching specific SIEM, EDR, and Data Lake languages.
Iran-Linked Activity Analysis Covered in the AA24-290A Alert
The latest security advisory AA24-290A from the U.S. leading authoring organizations, including the FBI, CISA, NSA, and international partners notifies defenders about the growing risks from a large-scale offensive operation led by Iranian hacking groups. Adversaries apply multiple brute-force attack techniques and credential access activity to target critical infrastructure organizations, including the healthcare, government, IT, engineering, and energy sectors.
Since mid-fall 2024, Iranian hackers have been employing brute force techniques, including password spraying and MFA “push bombing” to compromise user accounts and gain access to organizations. They conducted network reconnaissance to gather more credentials and information that could provide further access points. The agencies believe that Iranian actors sell this information on cybercriminal forums, where it may be used by others for further malicious activities.
After obtaining access to targeted networks, Iran-linked adversaries employed various methods to collect additional credentials, elevate privileges, and gather information about the organization’s systems and network. They also moved laterally within the network and downloaded data that could help other hackers with further access and exploitation.
Adversaries applied legitimate user and group email accounts, often obtained through brute-force methods like password spraying, to gain initial access to Microsoft 365, Azure, and Citrix systems. They also exploited the “MFA fatigue” by sending repeated push notifications until users approved them. Once inside, the actors registered their own devices with MFA to secure their access. In some cases, they leveraged open MFA registrations or used a self-service password reset tool to reset expired accounts and enable MFA. Their activities often involved VPNs, with many IP addresses linked to the Private Internet Access VPN service.
Iranian hackers also leveraged RDP for lateral movement and employed open-source tools and methods like Kerberos SPN enumeration and directory dumps via the Active Directory Microsoft Graph API for gathering credentials. They also used tools like DomainPasswordSpray.ps1 for password spraying and Cmdkey to display usernames and credentials. For privilege escalation, adversaries attempted domain controller impersonation, likely exploiting the nefarious Zerologon vulnerability tracked as CVE-2020-1472.
Attackers also relied on LOTL techniques, utilizing Windows command-line tools to gather information on domain controllers, trusted domains, domain administrators, and enterprise administrators. They also ran LDAP queries in PowerShell to collect details about Active Directory, such as computer names and operating systems. In some cases, they likely used msedge.exe to connect to Cobalt Strike Beacon C2 infrastructure. Additionally, they downloaded files related to remote access and the organization’s inventory, possibly exfiltrating them to maintain persistence or sell the data online.
To mitigate the risks of brute force attacks and credential access operations affiliated with the Iran-backed adversary activity, cyber defenders recommend ensuring that IT helpdesk password management follows company policies on user verification and password strength, disabling accounts for departing staff to minimize system exposure, implementing phishing-resistant MFA, regularly reviewing settings for all public-facing protocols, ensuring password policies align with the latest corresponding NIST guidelines, and disabling RC4 for Kerberos authentication.
In view of the increasing risks to global critical infrastructure across different industries, it is crucial to bolster proactive cyber defense measures against Iranian hackers. SOC Prime Platform for collective cyber defense equips progressive organizations with a feasible solution to proactively thwart emerging and existing threats launched by state-sponsored APT groups, ransomware affiliates, and any kinds of attacks most challenging their business to ensure comprehensive security protection and strengthening defenses at scale.




