A coordinated advisory from cybersecurity and intelligence agencies across North America, Europe, and Australia confirms a two-year-long cyberespionage campaign by russian GRU Unit 26165 (APT28, Forest Blizzard, Fancy Bear). The campaign targets logistics and tech providers facilitating foreign aid to Ukraine.
Detect APT28 (Forest Blizzard, Fancy Bear) Attacks Against Western Companies
Since a full-scale invasion of Ukraine, cybercriminal groups of russian origin have relentlessly targeted Ukraine and its allies for espionage and destruction. Among them, like APT28, are continuously using Ukraine as a testing ground to further expand their attack surface to European and North American political arenas, which is what we are, in fact, currently observing.
For instance, in October 2023, russian APT28 hacked the public & private sectors in France, using the same vulnerabilities and TTPs as in Ukraine during 2022-2023. Also, in May 2024, Germany revealed a long-lasting campaign by APT28, drawing condemnation from the European Union (E.U.), the North Atlantic Treaty Organization (NATO), and the U.K. According to CISA, russia will remain a top cyber threat by fusing cyber espionage, influence, and attack capabilities and keeping its primary focus on targeting critical infrastructure in the U.S. as well as in allied and partner countries.
Starting from the full-fledged war outbreak, SOC Prime has been helping Ukraine and its allies defend themselves from russian aggression. Our team constantly researches, develops, and tests detection rules based on CERT-UA reports and global CTI, delivering detection content to help thwart destructive russia’s attacks.
Register for the SOC Prime Platform to access a broad collection of detection rules addressing TTPs used by APT28 in the ongoing attack. Hit the Explore Detections button below and immediately drill down to a relevant set of detection algorithms compatible with multiple SIEM, EDR, and Data Lake solutions, aligned with MITRE ATT&CK, and enriched with actionable CTI.
Cyber defenders looking for more content addressing TTPs used by russian state-sponsored actors might browse Threat Detection Marketplace using “CERT-UA” tag. Additionally, security professionals might apply “APT28,” “BlueDelta,” “Fancy Bear,” and “Forest Blizzard” tags to narrow down the search.
To streamline threat investigation, security experts might use Uncoder AI – a private IDE & co-pilot for threat-informed detection engineering – now completely free and available without token limits on AI features. Generate detection algorithms from raw threat reports, enable fast IOC sweeps into performance-optimized queries, predict ATT&CK tags, optimize query code with AI tips, and translate it across multiple SIEM, EDR, and Data Lake languages.
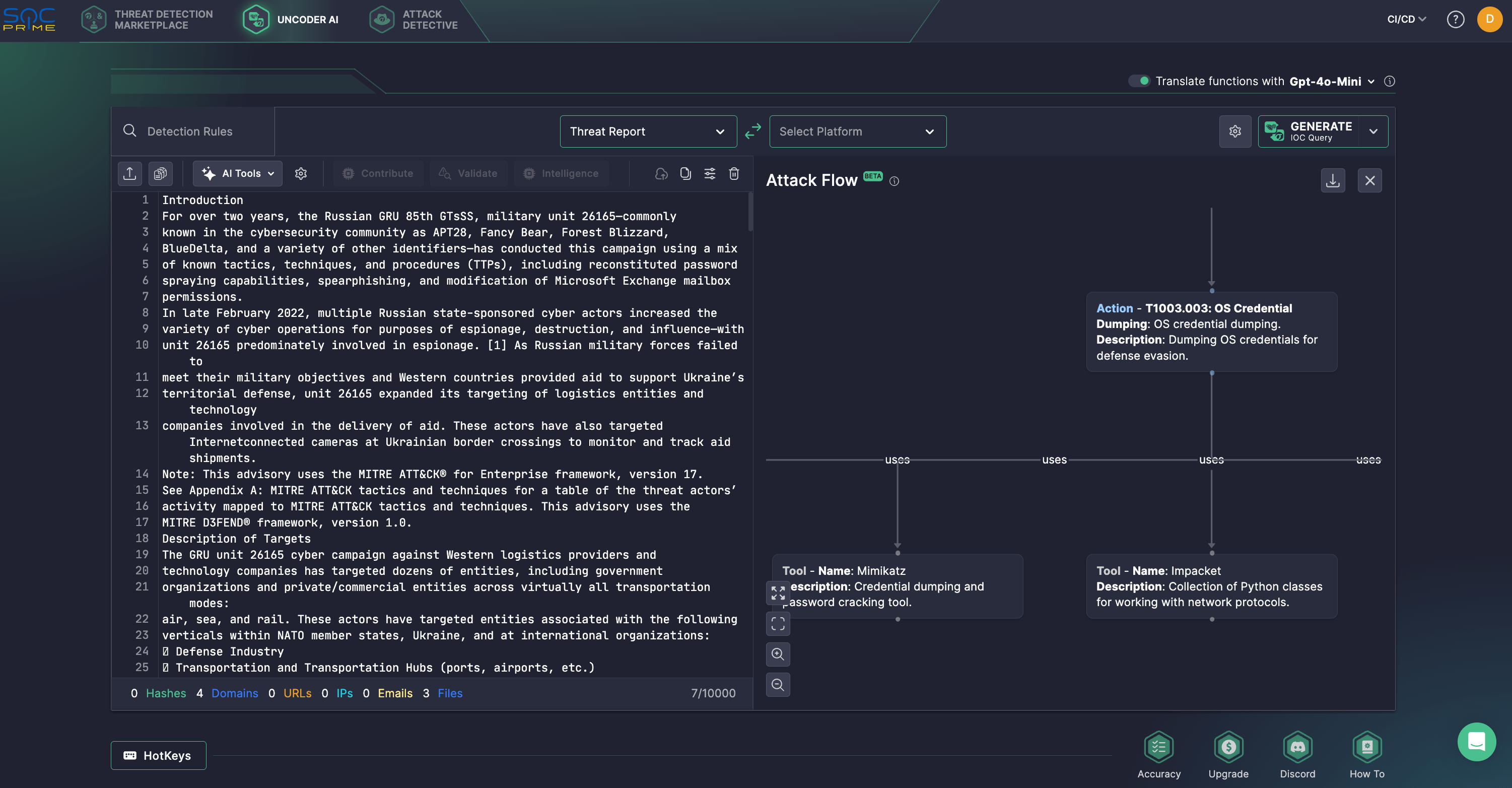
On top of it, Uncoder AI offers novel functionality inspired by the open-source Attack Flow project by MITRE to help defenders move from isolated behaviors to full adversary sequences. Using the joint Cybersecurity Advisory, security professionals might turn it into a visual flow, highlighting TTP chains to inform proactive detection logic, beyond IOCs. For this purpose, Uncoder AI uses Llama 3.3 customized for detection engineering and threat intelligence processing, hosted at SOC Prime SOC 2 Type II private cloud for maximum security, privacy, and IP protection.
APT28 Attack Analysis: Campaign Against Western Logistics and Tech Sector
On May 21, 2025, International cybersecurity partners have issued a joint Cybersecurity Advisory (CISA’s alert AA25-141A) focusing on a cyber-espionage campaign led by the russian state-sponsored actors targeting tech and logistics firms, particularly those involved in delivering and coordinating foreign aid to Ukraine.
Adversaries linked to the russian GRU’s 85th Main Special Service Center (military unit 26165) and widely recognized under aliases such as APT28 (aka BlueDelta, Fancy Bear, or Forest Blizzard) have carried out cyber attacks reportedly leveraging a combination of known TTPs. In late February 2022, multiple russian nation-backed groups intensified their operations to support espionage, disruption, and propaganda efforts. Among them, unit 26165 primarily focused on intelligence gathering. As the aggressor encountered setbacks on the battlefield and Western nations increased aid to Ukraine, this unit broadened its cyber targeting to include logistics and technology firms supporting aid delivery.
The GRU-backed unit 26165 has a history of spearphishing Ukrainian public sector entities. For instance, in late October 2024, the hacking collective, also tracked as UAC-0001 by CERT-UA, leveraged a PowerShell command hidden within clipboard content as an initial access method. This technique served as a gateway for subsequent offensive activities, including data theft and the deployment of METASPLOIT malware.
For over two years, adversaries focused on a broad range of Western logistics and technology providers, compromising or attempting to compromise numerous targets, including both governmental and commercial organizations across nearly all modes of transportation, like air, maritime, and rail. Their targets span multiple sectors within NATO countries, Ukraine, and international organizations. During their operations, threat actors expanded their efforts by identifying and subsequently targeting additional organizations within the transportation industry that maintained business relationships with the original victims, leveraging these trusted connections to gain deeper access to the targeted systems.
Additionally, APT28 carried out reconnaissance activities against at least one organization involved in manufacturing industrial control system components used in railway operations, though there is no confirmation of a successful breach. The attackers also exploited vulnerabilities in a variety of SOHO devices, using them to support their covert offensive activities and route malicious traffic through systems located near their intended targets.
The group’s operations involve credential guessing via anonymized infrastructure with rotating IPs and encrypted TLS connections to evade detection and abusing publicly accessible infrastructure, such as corporate VPNs, through known vulnerabilities and SQL injection attacks. Adversaries also use spearphishing emails impersonating trusted entities that contain malicious links or attachments leading to spoofed login pages or malware downloads, with some attacks relying on MFA and CAPTCHA bypassing. At the initial attack stage, APT28 also relies on vulnerability exploitation to gain access and steal data, including a critical Outlook flaw (CVE-2023-23397), Roundcube vulnerabilities, and CVE-2023-38831, a known WinRAR security issue.
After gaining initial access, adversaries conduct reconnaissance on key personnel and systems, use tools like Impacket, PsExec, and RDP for lateral movement, exfiltrate data using .zip files and OpenSSH, manipulate mailbox permissions for ongoing access, clear event logs to hide activity, and other offensive activities to spread infection further. They also deploy a range of malware in logistics-focused attacks, including HEADLACE and MASEPIE, while other strains like OCEANMAP and STEELHOOK have been seen in campaigns targeting different sectors.
Unit 26165 also establishes persistence via scheduled tasks, run keys, and malicious shortcuts in startup folders. As for exfiltration methods, they use PowerShell to prepare data and exfiltrate it using malware and built-in system tools. By using legitimate protocols, local infrastructure, and delaying exfiltration activities, they are capable of maintaining long-term, stealthy access to sensitive data.
In addition to targeting logistics firms, the group’s offensive operations also extended to compromising IP cameras across Ukraine and neighboring NATO countries. Since March 2022, attackers have run large-scale campaigns using RTSP DESCRIBE requests with default or brute-forced credentials to access live feeds and gather intelligence.
To strengthen defenses against sophisticated attacks like those orchestrated by GRU unit 26165, organizations should implement network segmentation, apply zero-trust principles, restrict lateral movement, and monitor logs for anomalies. Additional safeguards include restricting access to hosting and API mocking platforms, using only approved systems for handling sensitive information, and auditing for any unauthorized use of personal accounts in official communications.
With APT28 attacks reflecting sustained, evolving efforts to compromise entities tied to Western aid and supply chains, proactive cybersecurity measures are crucial for Ukraine and NATO allies to effectively manage and strengthen their cybersecurity posture. SOC Prime’s enterprise-ready product suite, backed by AI, automation, real-time threat intelligence, and built on zero-trust principles, helps security teams outscale emerging APT attacks while giving a competitive edge over the aggressor’s cyber-offensive capabilities.




