With a 250% surge of cyber attacks against Ukraine in 2022 and over 2,000 of them launched by russia-affiliated threat actors since the outbreak of the full-fledged war, cyber defenders are looking for ways to help Ukraine and its allies boost their cyber resilience.
On April 3, 2023, CERT-UA issued a new alert covering the observed malicious activity with unauthorized access to the information and communication technologies of one of the Ukrainian utility companies. As a response to the cyber incident, CERT-UA immediately provided a digital forensic investigation and revealed the infection chain was triggered by the unlicensed Microsoft Office 2019 software installation that enabled threat actors to deploy DarkCrystal RAT malware on the compromised systems. The tracked adversary activity is attributed to the UAC-0145 hacking group.
Detecting DarkCrystal RAT Spread by UAC-0145 Group
To help organizations timely identify the malicious activity associated with the DarkCrystal RAT malware spread by the UAC-0145 hacking collective in the latest cyber incident targeting Ukraine, SOC Prime Platform curates a set of relevant Sigma rules. All detection algorithms are filtered by the corresponding custom tags “CERT-UA#6322” and “UAC-0145” based on the CERT-UA alert and group identifiers to streamline the SOC content selection.
Click the Explore Detections button to reach the entire collection of dedicated Sigma rules aligned with the MITRE ATT&CK® framework v12 and enriched with in-depth cyber threat context. Sigma rules to detect the malicious activity covered by the CERT-UA#6322 alert are compatible with 27+ SIEM, EDR, and XDR solutions to fit particular security needs.
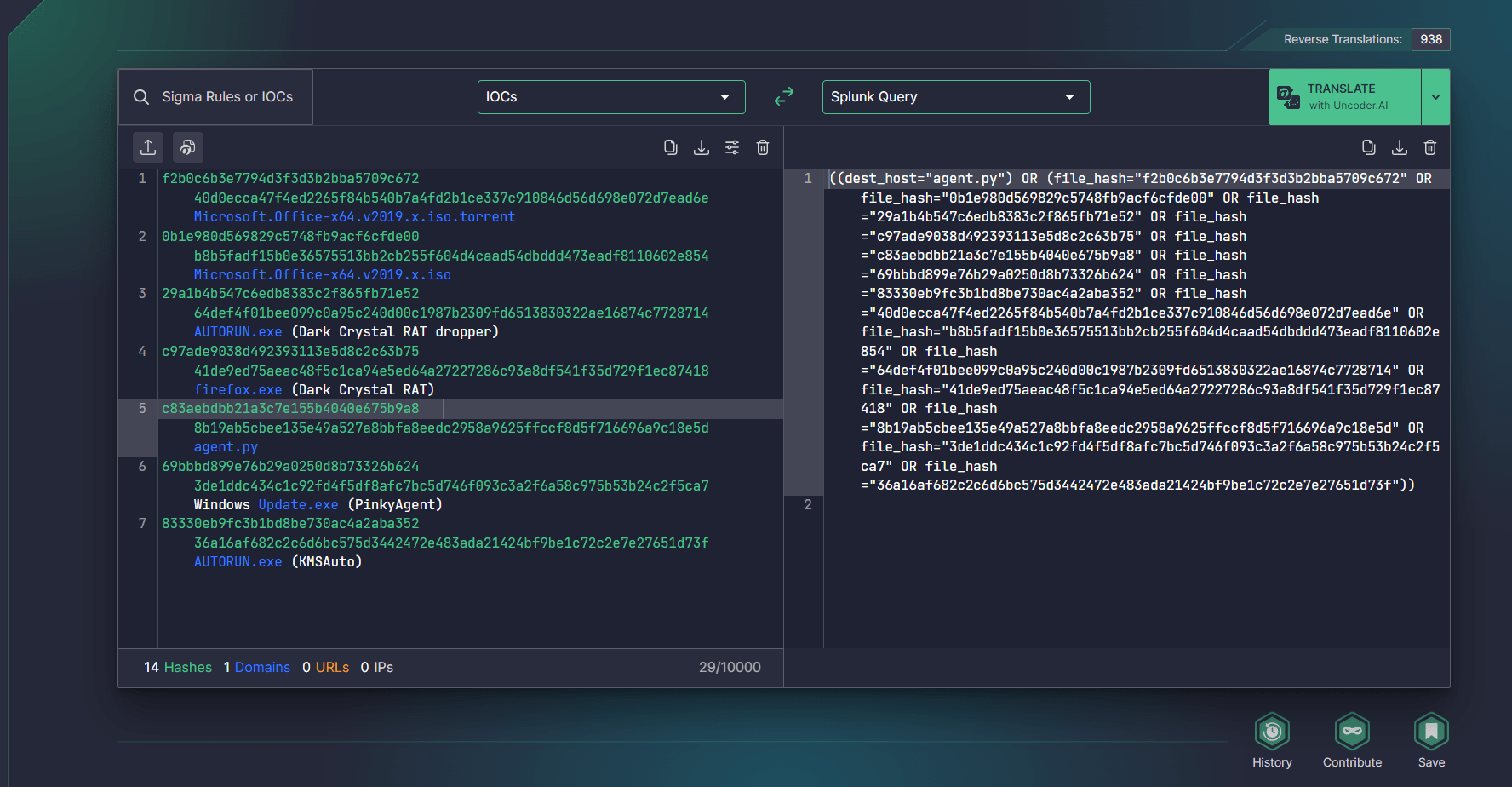
Security engineers can also automate IOC matching by instantly hunting for file, host, or network IOCs related to the latest CERT-UA#6322 alert in the selected SIEM or EDR environment via SOC Prime’s Uncoder AI tool.
Unlicensed Microsoft Office Used As the Initial Compromise Vector by UAC-0145: Attack Analysis
A novel CERT-UA#6322 alert details the exploitation of the unlicensed Microsoft Office software leveraged as the initial attack vector to distribute the DarkCrystal RAT malware in the recent cyber incident targeting the Ukrainian utility organization. According to the investigation, CERT-UA researchers revealed that the initial compromise took place on March 19, 2023, due to the installation of the unlicensed Microsoft Office 2019 version on the targeted systems. The software was downloaded from the public BitTorrent tracker along with the malicious executable file. Once launched, the latter leads to XOR decryption and decoding from the Base64 format, creating and running the malicious executable file identified as DarkCrystal RAT malware, which initiates the installation of Microsoft Office 2019 and spreads the infection further. DarkCrystal RAT is capable of duplicating itself and creating up to 20 versions on the compromised system, as well as adding the corresponding keys in the “Run” branch of the Windows registry and creating scheduled tasks via WMI.
On March 20, 2023, threat actors leveraged the already installed DarkCrystal RAT malware to download the Python interpreter v. 2.7.18, remote access software DWAgent, along with another executable file to run the DWAgent tool on the targeted computer. As a result of installing the DarkCrystal RAT and DWAgent remote access utility, threat actors managed to gain unauthorized access to the targeted organization’s environment.
According to CERT-UA, adversaries leveraged this initial compromise vector in previous malicious campaigns. In addition to exploiting Microsoft Office products, the infection chain can also be triggered by downloading OS updates from unofficial web resources or other software types, like password recovery utilities or malware scanner tools. To remediate the risks of such cyber attacks, organizations should raise cybersecurity awareness and use only official sources for software installation and updates.
MITRE ATT&CK® Context
To explore the context behind the March cyber incident covered by the CERT-UA#6322 alert, all relevant Sigma rules are aligned with MITRE ATT&CK addressing the corresponding tactics and techniques:




