Ransomware continues to rank among the most critical cyber threats. According to the 2025 Verizon Data Breach Investigations Report (DBIR), it was observed in 44% of breaches—an increase from 32% in last year’s report. A relatively new player, Crypto24 Ransomware Group, has been targeting large organizations across the United States, Europe, and Asia, using custom tools to bypass security defenses, steal data, and encrypt files on compromised networks.
Detect Crypto24 Ransomware Attacks
Cybersecurity Ventures warns that by 2031, a ransomware attack could happen every two seconds, making strong and proactive threat detection more important than ever. Ransomware operations continue to evolve, becoming more sophisticated and targeting organizations of all sizes, from large enterprises to small businesses.
Register for the SOC Prime Platform to detect potential threats, like Crypto24 ransomware, at the earliest possible stage. The Platform delivers timely threat intelligence and actionable detection content, backed by a complete product suite for AI-powered detection engineering, automated threat hunting, and advanced threat detection. Click the Explore Detections button below to access a curated stack of detection rules specifically designed to help identify and respond to Crypto24 ransomware activity.
All the rules are compatible with multiple SIEM, EDR, and Data Lake solutions and mapped to the MITRE ATT&CK® framework. Additionally, every rule is packed with detailed metadata, including threat intel references, attack timelines, triage recommendations, and more.
Optionally, cyber defenders can apply the broader “Ransomware” tag to access a wider range of detection rules covering ransomware attacks globally.
Additionally, security experts might streamline threat investigation using Uncoder AI, a private IDE & co-pilot for threat-informed detection engineering. Generate detection algorithms from raw threat reports, enable fast IOC sweeps, predict ATT&CK tags, optimize query code with AI tips, and translate it across multiple SIEM, EDR, and Data Lake languages. For instance, cyber defenders can instantly visualize Attack Flow based on the Trend Micro research on Crypto24 ransomware activity.
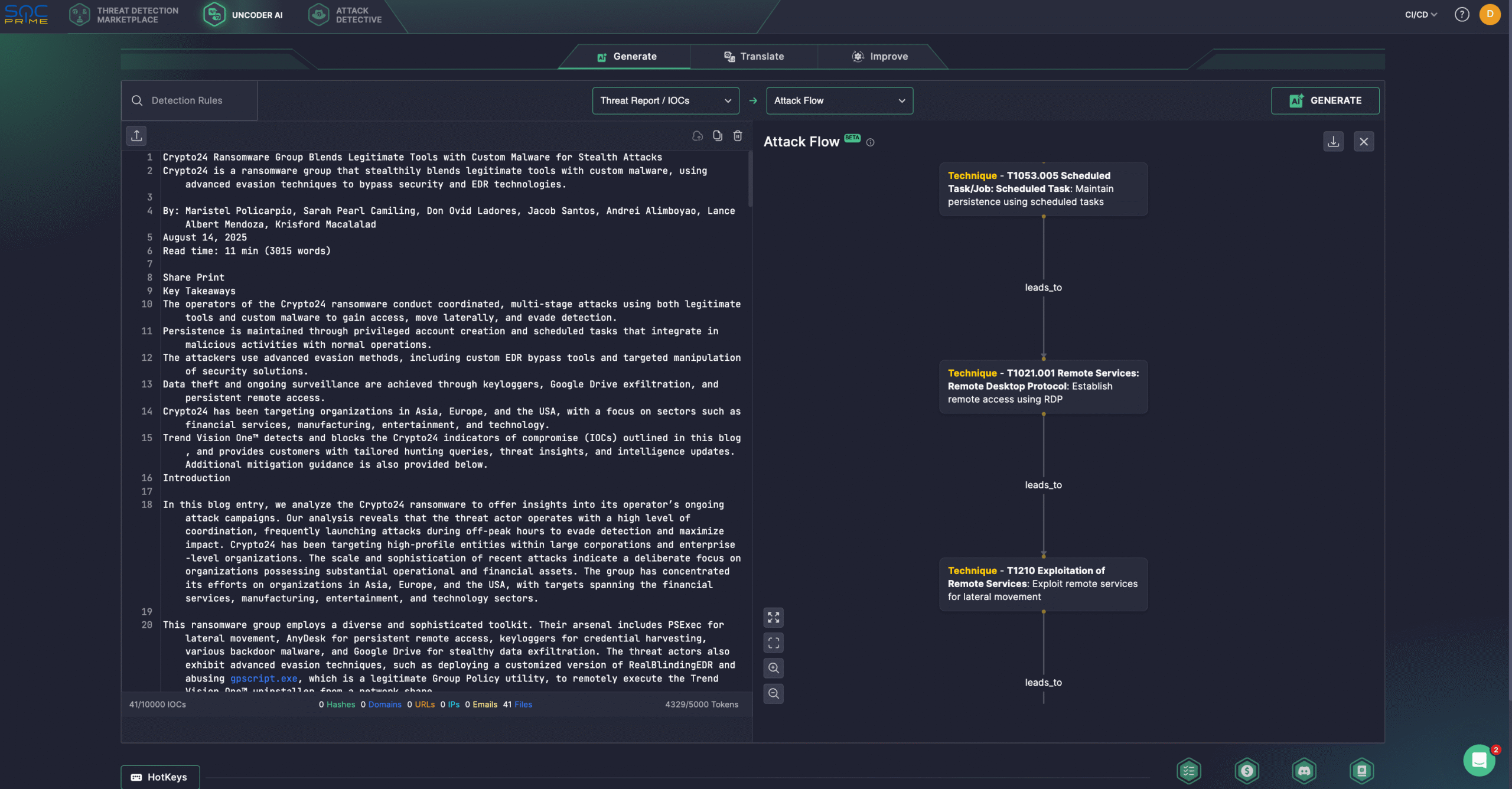
Crypto24 Ransomware Group Analysis
The Crypto24 ransomware group emerged in the cyber threat landscape in the early fall of 2024. Adversaries have targeted organizations across Asia, Europe, and the United States, primarily in the finance, manufacturing, entertainment, and tech sectors.
The group’s operations include privileged account creation and scheduled tasks to maintain persistence while blending malicious activity with routine system operations. The group employs custom EDR bypass utilities and manipulates security solutions to avoid detection. Data theft and surveillance are carried out via keyloggers, Google Drive exfiltration, and persistent remote access.
Trend Micro reports that Crypto24 executes highly coordinated campaigns, often timed for off-peak hours to reduce visibility and maximize damage. Recent activity shows a focus on large enterprises and high-profile corporate entities, with the scale and sophistication of attacks pointing to a deliberate targeting of organizations with significant financial and operational assets.
Crypto24 employs a highly sophisticated toolkit that blends legitimate tools with custom malware and applies advanced detection evasion techniques. Their operations leverage PSExec for lateral movement, AnyDesk for persistent access, keyloggers for credential theft, backdoors, and Google Drive for data exfiltration.
After gaining initial access, the Crypto24 ransomware attack chain involves reactivating default accounts, creating new privileged users, and leveraging Windows utilities (like net.exe, sc.exe, or runas.exe) to maintain persistence, enable RDP access, and deploy payloads. Reconnaissance is performed via batch files and WMIC commands to collect system, hardware, and account data for lateral movement planning.
Persistence is reinforced through scheduled tasks, malicious services, and patched DLLs (e.g., termsrv.dll to allow multiple RDP sessions). Attackers deploy keyloggers (WinMainSvc.dll) for credential theft, use Google Drive for exfiltration, and install TightVNC for remote control.
For defense evasion, Crypto24 weaponizes customized RealBlindingEDR variants and abuses gpscript.exe to run the legitimate Trend Vision One uninstaller, disabling protections before executing the ransomware payload. While the uninstaller itself is not a vulnerability, attackers exploit it post-compromise with elevated privileges, thus employing a “living off the land” tactic.
The Crypto24 ransomware campaign highlights the escalating operational sophistication and adaptability of modern threat actors. By leveraging a strategic combination of legitimate IT tools, alongside LOLBins, custom malware, and advanced evasion techniques, the operators successfully gain initial access, execute lateral movement, and establish persistent footholds within targeted environments. As potential Crypto24 ransomware mitigation measures, organizations should strengthen account and access controls, restrict RDP and remote tools to authorized systems with MFA, and closely monitor for abnormal use of Windows utilities, new services, or scheduled tasks. Equally critical are enforcing Zero Trust principles, auditing backups, monitoring for data exfiltration, and training users on phishing and credential risks as part of a robust incident response strategy. By leveraging SOC Prime’s complete product suite backed by AI, automation capabilities, real-time threat intel, and built on zero-trust milestones, global organizations can outscale ransomware attacks and any threats of increasing sophistication and adaptability.




