The ever-growing volumes of ransomware attacks, the increased number of financially motivated hacking collectives, and soaring global ransomware damage costs are shaking up the modern cyber threat arena. The FBI and CISA have recently issued a novel alert notifying defenders of the emergence of the BlackSuit ransomware, the evolution of Royal ransomware enriched with enhanced offensive capabilities. BlackSuit maintainers have already demanded ransom payments amounting to $500+ million in total, posing escalating risks to global organizations.
Detect BlackSuit (Royal) Ransomware
This summer has been intense not only because of the heat but also due to the surge in ransomware activity. Following the recent emergence of Zola and increased activity of Akira ransomware, CISA and FBI are now warning cyber defenders about a new malicious strain dubbed BlackSuit. As the successor to the infamous Royal ransomware, the BlackSuit variant features enhanced capabilities, escalating ransom demands and targeting organizations worldwide.
To stay ahead of potential BlackSuit attacks, security professionals can rely on the SOC Prime Platform aggregating a set of relevant detection rules paired with advanced threat detection & hunting solutions. Just hit the Explore Detection button below and immediately drill down to a dedicated rules collection to detect BlackSuite ransomware attacks.
All detection rules are compatible with over 30 SIEM, EDR, and Data Lake solutions and are mapped to the MITRE ATT&CK framework. Furthermore, the detection algorithms are enriched with extensive metadata, including CTI references, attack timelines, and triage recommendations, streamlining threat investigation.
Additionally, security professionals might use Uncoder AI, the industry-first AI co-pilot for Detection Engineering, to instantly hunt for indicators of compromise provided in CISA’s AA23-061A advisory. Uncoder AI acts as an IOC packager, letting CTI and SOC analysts and Threat Hunters seamlessly parse IOCs and convert them into custom hunting queries ready to run in the SIEM or EDR of their choice.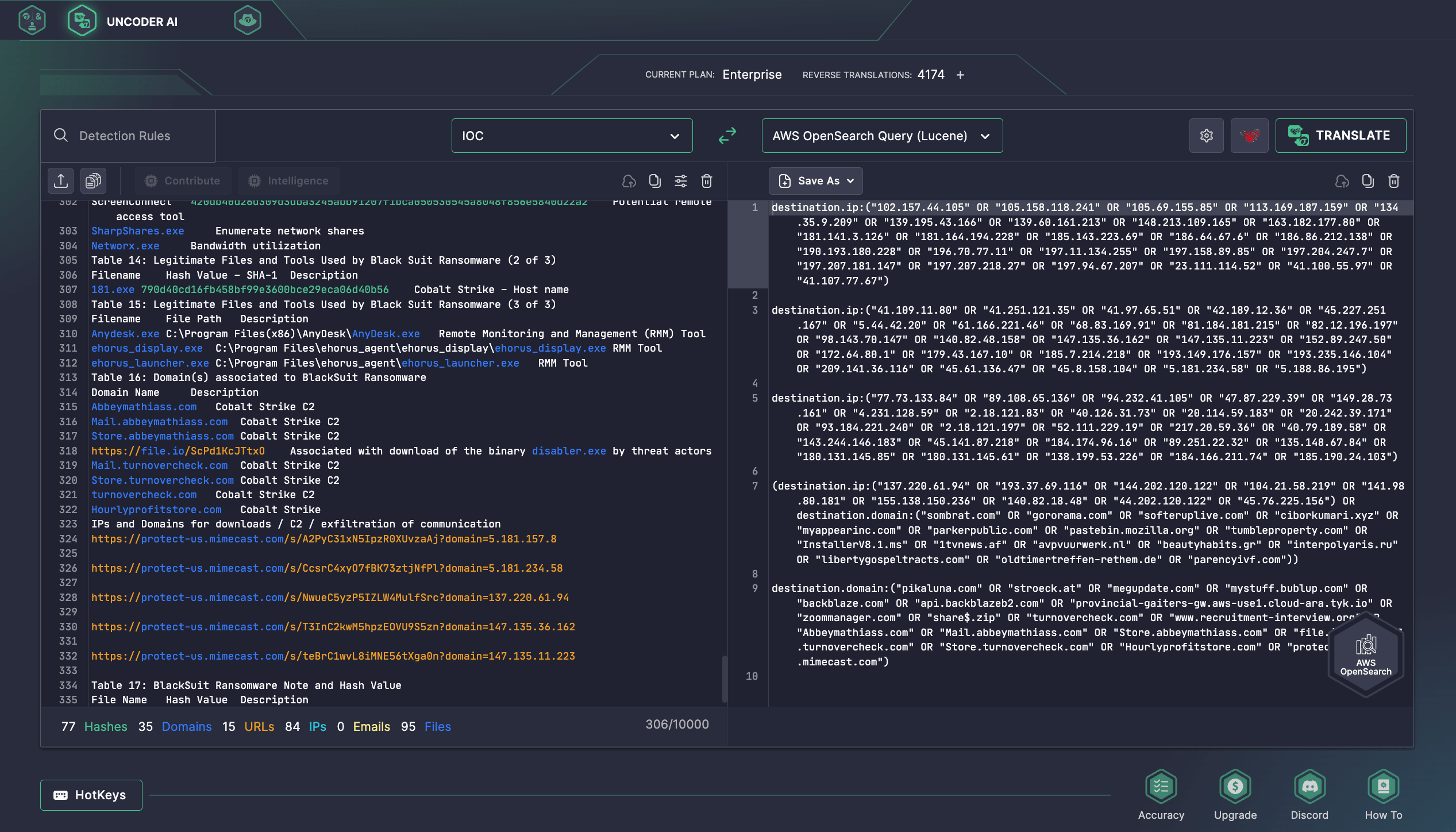
Security experts looking for additional detection content to tackle the Royal ransomware family attacks and investigate their evolution retrospectively can rely on SOC Prime’s Threat Detection Marketplace. By applying the “Royal” and “Blacksuit” tags, cyber defenders can find a comprehensive collection of relevant rules and queries.
BlackSuit (Royal) Ransomware Analysis
Hard on the heels of the emergence of the novel Proton ransomware variant dubbed Zola, another rebranded ransomware variant comes to the scene. The FBI and CISA issued a new alert, AA23-061A, aimed at increasing cybersecurity awareness of BlackSuit ransomware, which has evolved from Royal. BlackSuit possesses similar coding capabilities as its predecessor, which was active in the cyber threat arena from around early fall 2022 to summer 2023, however, the rebranded ransomware is more sophisticated.
BlackSuit performs data exfiltration and extortion before encryption, threatening to release victim data on a leak site unless the victim pays the ransom. For initial access, adversaries largely rely on the phishing attack vector. Other frequent infection methods involve exploiting RDP or vulnerable internet-facing applications and gaining entry through access bought from initial access brokers.
After infiltrating a network, BlackSuit maintainers establish communication with C2 servers and download various utilities. They often abuse legitimate Windows software and leverage open-source projects for offensive purposes. Their Royal precessors relied on tools like Chisel, SSH client, OpenSSH, or PuTTY to connect with their C2 infrastructure. Once inside a network, BlackSuit operators disable antivirus software, steal large volumes of data, and then deploy the ransomware to encrypt the targeted systems. Adversaries leverage popular utilities, such as Mimikatz and Nirsoft for credential stealing. BlackSuit affiliates also repurpose legitimate penetration testing utilities like Cobalt Strike and leverage malware such as Ursnif/Gozi for data collection and exfiltration.
BlackSuit ransomware demands typically range from $1 million to $10 million in Bitcoin, with the highest individual demand reaching $60 million. While BlackSuit actors are open to negotiating payment, ransom amounts are not specified in the initial note and require direct communication with adversaries via a .onion URL through the Tor browser.
To reduce the risks of BlackSuit ransomware attacks, the FBI and CISA recommend applying mitigations listed in the AA23-061A alert that are in line with the CPGs created by CISA and the NIST. In addition to the provided practices and protections, defenders also recommend evaluating the effectiveness of the organization’s current security controls by validating them against the ATT&CK techniques highlighted in the advisory. To help organizations proactively thwart emerging ransomware attacks and other critical threats, SOC Prime curates a complete product suite for AI-powered detection engineering, automated threat hunting, and detection stack validation acting as a future-proof enterprise-ready solution for elevating defenses at scale.




