The russia-linked Armageddon APT aka Gamaredon or UAC-0010 has been launching a series of cyber attacks on Ukraine since the outbreak of the global cyber war. On November 8, 2022, CERT-UA released the latest alert detailing the ongoing spearphishing campaign of this russia-backed cyber-espionage hacking collective, in which adversaries massively distribute spoofed emails masquerading as State Special Communications Service of Ukraine. In this targeted adversary campaign, Armageddon APT hackers exploit the malicious email attachment attack vector.
Armageddon APT (UAC-0010) Cyber Attacks: Analysis of the Latest Phishing Campaign Against Ukraine
Since russia’s full-scale invasion of Ukraine, the notorious russia-linked Armageddon APT group also tracked as UAC-0010 or Primitive Bear has been actively exploiting phishing and malicious email attachment attack vectors in targeted campaigns against Ukraine. In May and July 2022, the hacking collective has been massively distributing the GammaLoad.PS1_v2 malicious software, while in August 2022, adversaries applied GammaSteel.PS1 and GammaSteel.NET malware for spreading infection on the compromised systems.
In the ongoing adversary campaigns reported by the CERT-UA#5570 alert, the infection chain is triggered by phishing emails containing a malicious attachment, which, if opened, downloads an HTML file with JavaScript code. The latter creates a RAR archive with a shortcut LNK file on the vulnerable computer. Once opened, the above-mentioned LNK file downloads and launches an HTA file, which, in turn, runs malicious VBScript code. As a result, this leads to deploying a series of malicious strains on the targeted systems, including info-stealing malware samples.
CERT-UA researchers report that phishing emails are being delivered via the @mail.gov.ua service. In addition, Armageddon APT hackers apply their common adversary patterns to launch cyber attacks using a third-party service or Telegram to identify the IP address of the C2 server.
Detecting the Latest Armageddon APT Campaign Against Ukrainian Entities
A series of phishing campaigns by the russia-linked Armageddon APT repeatedly targeting Ukraine since March 2022 pose an escalating threat that requires timely detection and ultra-responsiveness from security practitioners. SOC Prime’s Detection as Code platform offers a batch of curated Sigma rules to identify the related malicious activity covered in the CERT-UA#5570 alert at the earliest stages of the attack lifecycle. Follow the link below to reach relevant detection content tagged “CERT-UA#5570” based on the corresponding cybersecurity alert:
To proactively defend against existing and emerging Armageddon APT cyber attacks tracked by cyber defenders since russia’s full-scale invasion of Ukraine, hit the Explore Detections button and access the dedicated detection stack. All Sigma rules are aligned with MITRE ATT&CK® and enriched with extensive cyber threat context, including relevant CTI links, mitigations, executable binaries, and more relevant metadata. Detection rules are packed with translations to the industry-leading SIEM, EDR, and XDR solutions.
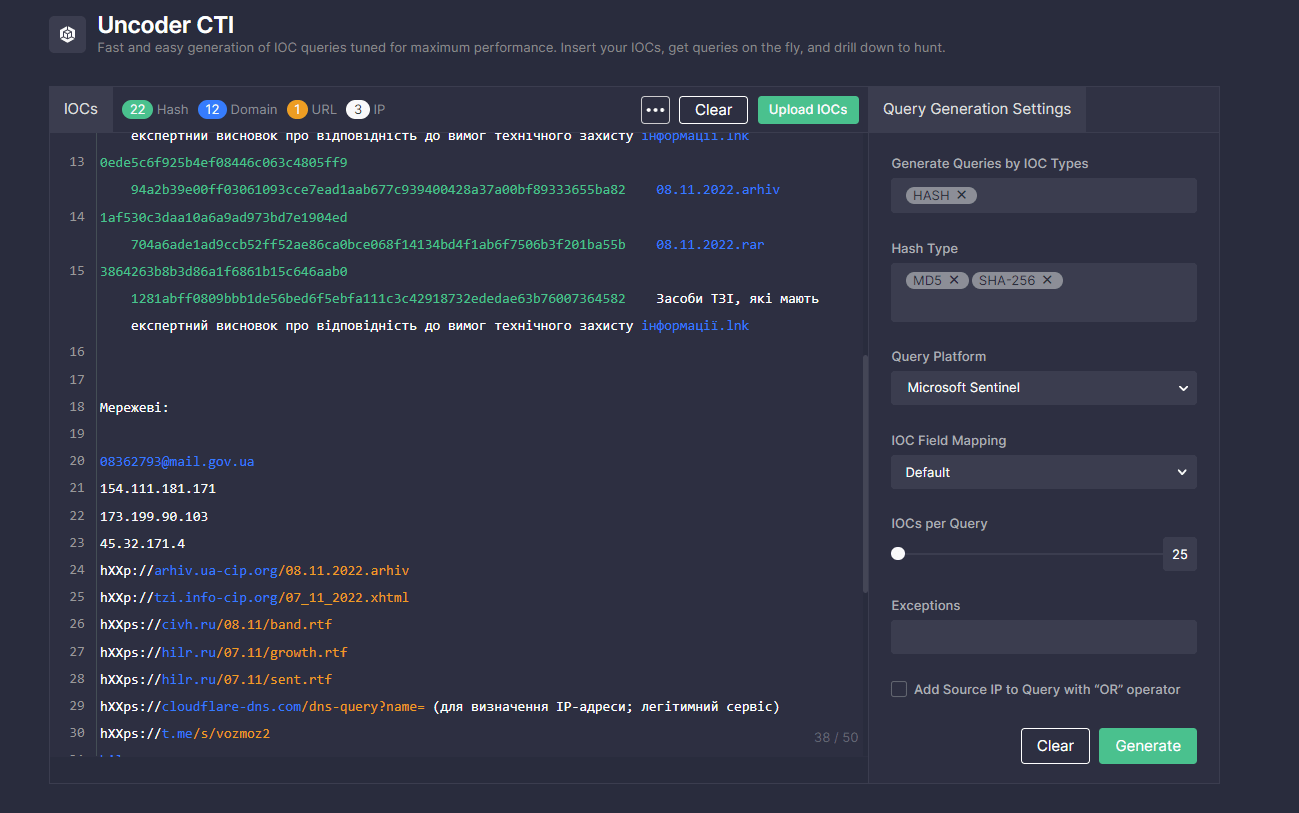
To simplify threat hunting routine and boost detection engineering capabilities, security experts can search for IOCs associated with the malicious activity of the UAC-0010 adversaries covered in the CERT-UA#5570 alert. Just paste the text containing relevant IOCs to Uncoder CTI and get custom IOC queries ready to run in a chosen environment.
MITRE ATT&CK® Context
To dive into the context behind the latest cyber attacks of the russia-linked Armageddon APT group aka UAC-0010 covered in the CERT-UA#5570 alert, all dedicated Sigma rules are aligned with MITRE ATT&CK® framework addressing the corresponding tactics and techniques:




