On January 12, 2026, the CERT-UA team disclosed a targeted cyber-espionage campaign against the Ukrainian Armed Forces that abused charity-themed social engineering to deliver the PLUGGYAPE backdoor. The activity, observed between October and December 2025, is attributed with medium confidence to the russia-aligned threat actor known as Void Blizzard (Laundry Bear), tracked by CERT-UA as UAC-0190.
Detect UAC-0190 Attacks Leveraging PLUGGYAPE Malware Against Ukraine
As Ukraine approaches the fifth year of Russia’s full-scale invasion, the volume and intensity of offensive cyber campaigns targeting Ukraine and its allies remain exceptionally high. Security researchers estimate that approximately 40 Russia-aligned APT groups targeted Ukraine in the first half of 2023, with the number and sophistication of intrusions steadily increasing. In this latest case, the Armed Forces of Ukraine were targeted in a malicious campaign attributed to UAC-0190, which relied on the deployment of the PLUGGYAPE backdoor.
Register for SOC Prime Platform to keep abreast of the malicious activity linked to UAC-0190 and PLUGGYAPE. SOC Prime Team has recently released a curated set of detection rules addressing the ongoing group’s campaign against the defense and government sectors covered in the CERT-UA#19092 alert. Click the Explore Detections button to access relevant detections enriched with AI-native CTI, mapped to the MITRE ATT&CK® framework, and compatible with dozens of SIEM, EDR, and Data Lake technologies.
Security engineers can also use the “CERT-UA#19092” tag based on the relevant CERT-UA alert identifier to search for the detection stack directly and track any content changes. For more rules to detect attacks related to the UAC-0190 adversary activity, security teams can search the Threat Detection Marketplace library leveraging the “UAC-0190,” “Void Blizzard,” or “Laundry Bear” tags based on the group identifier, as well as relevant “Pluggyape.v2” tag addressing the offensive tools used by threat actors in the latest campaign.
Additionally, users can refer to a relevant Active Threats item to access the AI summary, related detection rules, simulations, and the attack flow in one place.
Security teams can also rely on Uncoder AI to create detections from raw threat reports, document and optimize code, and generate Attack Flows. By leveraging threat intel from the latest CERT-UA alert, teams can auto-convert IOCs into custom queries ready to hunt in the selected SIEM or EDR environment.
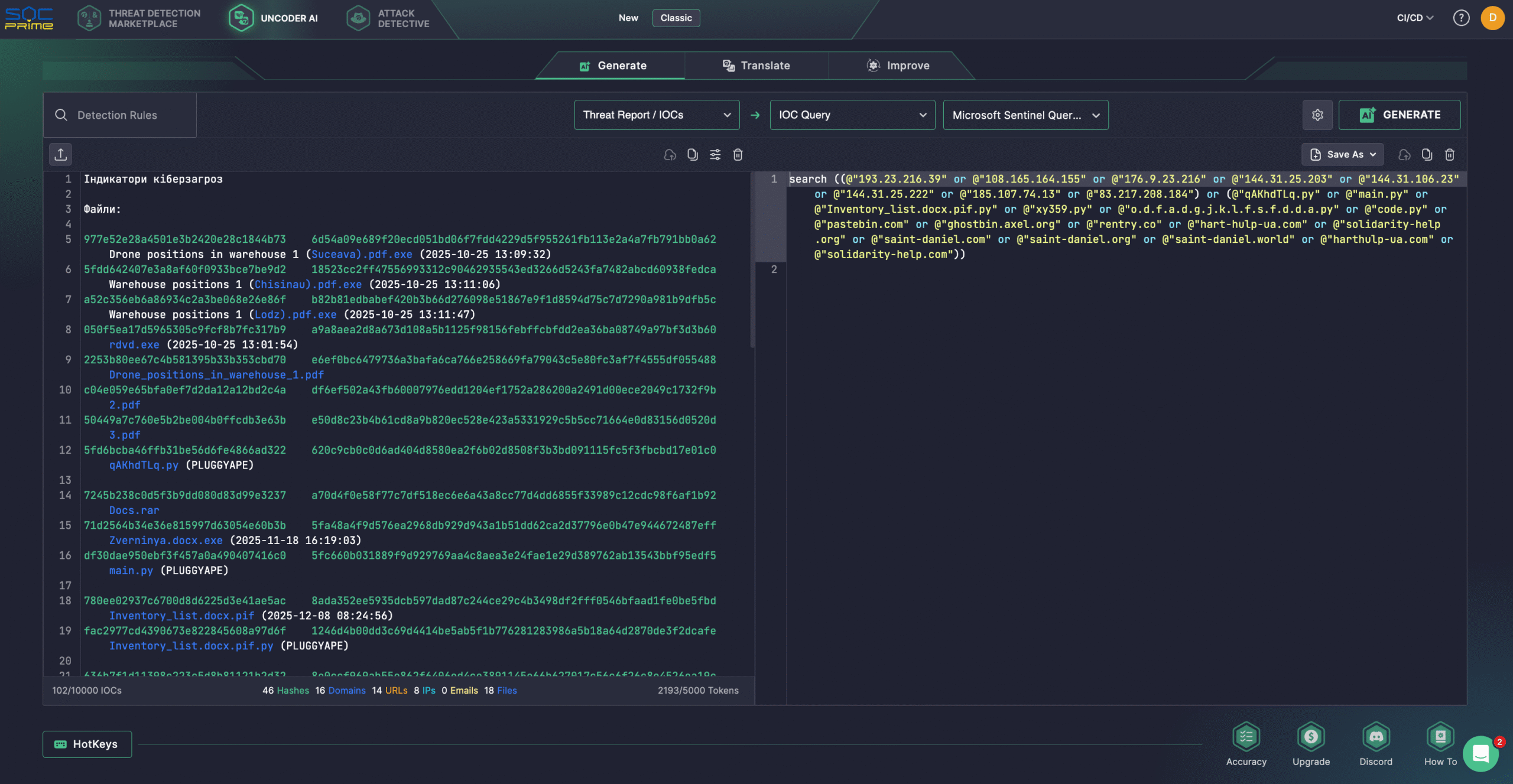
Analyzing UAC-0190 Malicious Activity Covered In CERT-UA#19092 Alert
Between October and December 2025, in coordination with the Cyber Incident Response Team of the Armed Forces of Ukraine, CERT-UA investigated a series of targeted cyberattacks against members of the Ukrainian Armed Forces. The activity was conducted under the guise of legitimate charitable organizations and relied on the deployment of the PLUGGYAPE backdoor.
To initiate the infection chain, adversaries contacted victims via popular messaging applications, like Signal and WhatsApp, encouraging them to visit a website impersonating a well-known charitable foundation. They were prompted to download so-called “documents,” which in reality were malicious executable files, most often distributed inside password-protected archives. In some cases, the executable was delivered directly through the messenger and commonly used the misleading extension “.docx.pif”. The PIF file was a PyInstaller-packaged executable, and the embedded payload was written in Python and identified as the PLUGGYAPE backdoor.
Notably, earlier iterations of the campaign, observed in October 2025, leveraged executables with the “.pdf.exe” extension. These files acted as loaders responsible for downloading a Python interpreter and an early version of PLUGGYAPE from public platforms such as Pastebin.
Starting December 2025, CERT-UA identified a significantly enhanced and obfuscated version of the malware, designated PLUGGYAPE.V2. This version introduced support for the MQTT protocol for command-and-control communications and implemented multiple anti-analysis and anti-virtualization checks aimed at evading detection and sandbox execution.
CERT-UA highlights the continued evolution of the cyber threat landscape, noting that initial access increasingly relies on trusted communication channels, including legitimate user accounts, Ukrainian mobile phone numbers, and the use of Ukrainian-language text, voice, and video communications. In many cases, attackers demonstrate detailed knowledge of the targeted individual or organization. As a result, widely used messaging platforms on mobile devices and workstations have become a primary malware delivery vector.
To minimize the risks of exploitation attempts, rely on SOC Prime’s AI-Native Detection Intelligence Platform, which equips SOC teams with cutting-edge technologies and top cybersecurity expertise to stay ahead of emerging threats while maintaining operational effectiveness.
MITRE ATT&CK Context
Leveraging MITRE ATT&CK offers in-depth insight into the latest UAC-0190 malicious campaign against Ukraine. The table below displays all relevant Sigma rules mapped to the associated ATT&CK tactics, techniques, and sub-techniques. Tactics Techniques Sigma Rule Initial Access Phishing: Spearphishing Attachment (T1566.001) Execution Command and Scripting Interpreter: Python (T1059.006) User Execution: Malicious Link (T1204.001) Persistence Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder (T1547.001) Discovery System Information Discovery (T1082) Command and Control Application Layer Protocol: Web Protocols (T1071.001)




