CERT-UA has observed a wave of increasing offensive activity leveraging spearphishing and targeting the Defence Forces and local state agencies of Ukraine. The attacks orchestrated by the UAC-0239 group impersonate the Security Service of Ukraine and compromise the targeted organizations using the OrcaC2 framework and FILEMESS stealer.
Detect UAC-0239 Attacks Covered in the CERT-UA#17691 Alert
According to Check Point Research’s Q2 2025 Brand Phishing report, in the second half of 2025, phishing remained a key cybercriminal tactic, with attackers increasingly impersonating globally trusted brands that millions of people use. Amid increasingly complex and sophisticated offensive campaigns targeting critical infrastructure and government sectors, CISA has developed its 2025–2026 International Strategic Plan to strengthen global risk reduction and resilience efforts.
Register for SOC Prime Platform to keep abreast of increasing spearphishing cyber-attacks linked to the UAC-0239 hacking collective. SOC Prime Team has recently released a curated set of Sigma rules addressing the ongoing group’s campaign against the defense and government sectors covered in the latest CERT-UA alert. Click the Explore Detections button to access relevant detections enriched with AI-native CTI, mapped to the MITRE ATT&CK® framework, and compatible with dozens of SIEM, EDR, and Data Lake technologies.
Security engineers can also use the “CERT-UA#17691” tag based on the relevant CERT-UA alert identifier to search for the relevant detection stack directly and track any content changes. For more Sigma rules to detect attacks related to the UAC-0239 adversary activity, security teams can search the Threat Detection Marketplace library leveraging the “UAC-0239” tag based on the group identifier, as well as relevant “OrcaC2” and “FILEMESS” tags addressing the offensive tools used by threat actors in the latest campaign.
Security teams can also rely on Uncoder AI to create detections from raw threat reports, document and optimize code, generate Attack Flows, and enable ATT&CK tags prediction. By leveraging threat intel from the latest CERT-UA alert, teams can auto-convert IOCs into custom queries ready to hunt in the selected SIEM or EDR environment.
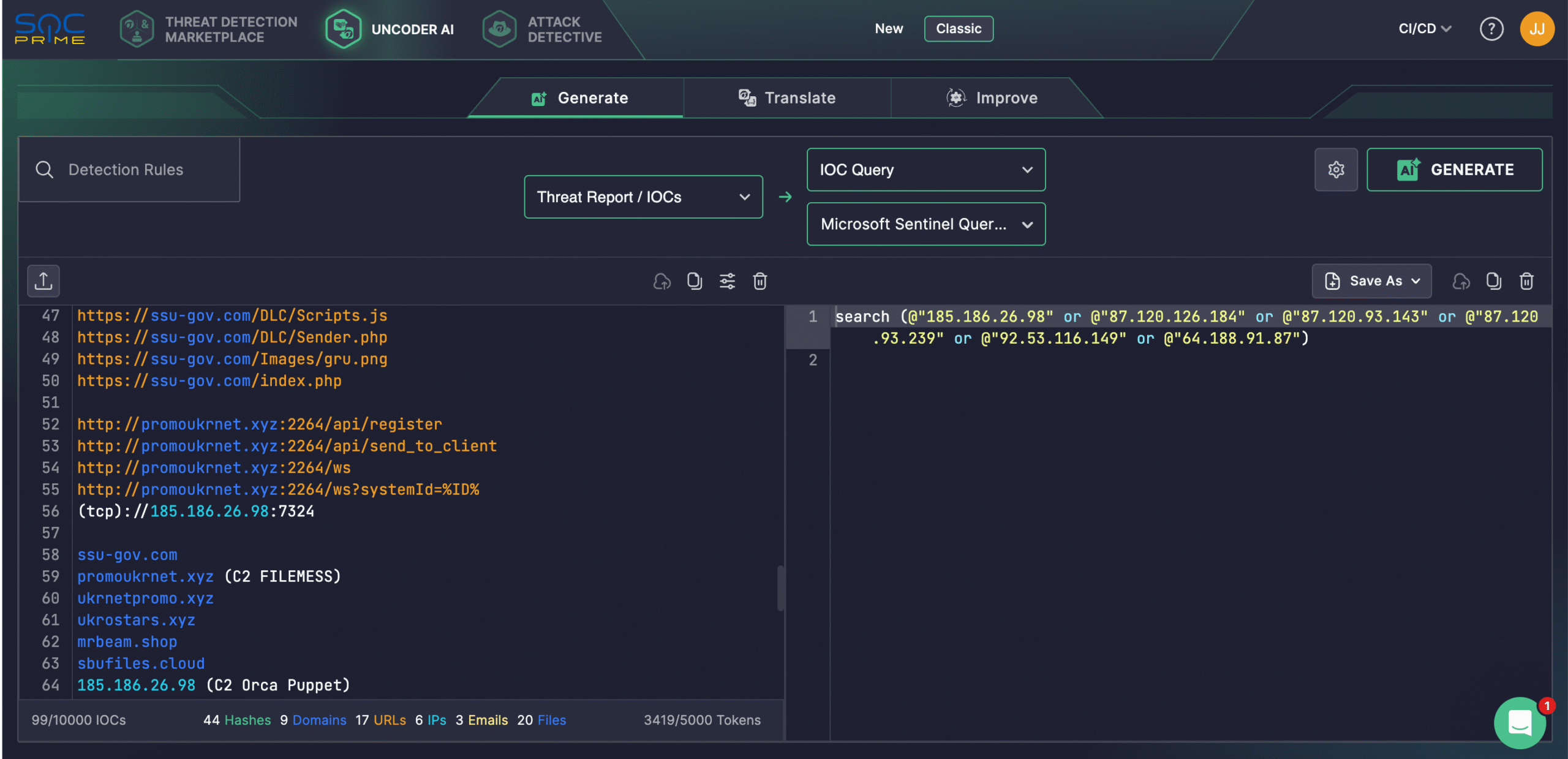
UAC-0239 Attack Analysis
Since the second half of September 2025, CERT-UA has observed attempts at targeted cyber-attacks against the Defence Forces and local government bodies across several Ukrainian regions linked to the UAC-0239 hacking collective. The malicious campaign covered in the corresponding CERT-UA#17691 alert uses a theme of “countering russian sabotage-reconnaissance groups” and disguises the sender as the Security Service of Ukraine.
The attack flow starts with a spearphishing email using services like Ukr.net and Gmail, and others. Malicious emails contain a link to download an archive, which is sometimes password-protected and holds a VHD (Virtual Hard Drive) file, or the VHD is attached directly. The latter includes an executable file along with several lure documents, typically PDFs.
Adversaries employ OrcaC2, a multifunction Go-based C2 framework whose source code is publicly available on GitHub, and FILEMESS, a file stealer that exfiltrates data to Telegram.
The FILEMESS malware core capabilities are recursive searching for files with specified extensions in the “Desktop”, “Downloads”, “Documents” folders, and on logical drives D–Z; computing MD5 hashes of found files; and exfiltrating files via the Telegram API. The malware uses two extension lists: a long list covering diverse document, spreadsheet, presentation, archive, and design formats, and a shorter list applied only to the three user folders with the pdf, txt, csv, jpg/jpeg, png, tif/tiff, webp, zip, or other formats. Persistence is achieved by adding a Run key to the OS registry. Telegram API credentials are XOR-obfuscated and Base64-encoded. To prevent multiple concurrent instances, the program checks for an existing process.
OrcaC2 is capable of RCE, interactive shell, file transfer, screenshots, keylogging, process control (including memory dumps), UAC bypass, shellcode execution, multiple process-injection techniques, proxy support, SOCKS, traffic tunneling (SSH, SMB), port scanning, password brute-forcing, and more. Persistence mechanisms observed or possible include scheduled tasks, Run registry entries, and services.
MITRE ATT&CK Context
Leveraging MITRE ATT&CK offers in-depth insight into the ongoing UAC-0239 malicious campaign against Ukraine. The table below displays all relevant Sigma rules mapped to the associated ATT&CK tactics, techniques, and sub-techniques.
Tactics | Techniques | Sigma Rule |
Initial Access | Phishing: Spearphishing Attachment (T1566.001) | |
Execution | Scheduled Task/Job: Scheduled Task (T1053.005) | |
User Execution: Malicious File (T1204.002) | ||
Persistence | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder (T1547.001) | |
Office Application Startup (T1137) | ||
Office Application Startup: Add-ins (T1137.006) | ||




