Attack Detective
Automated retrospective threat search across your security stack – query data where it lives
“It Made a Security Operations Life Easier”
Features
Turn ATT&CK Coverage
Into Action
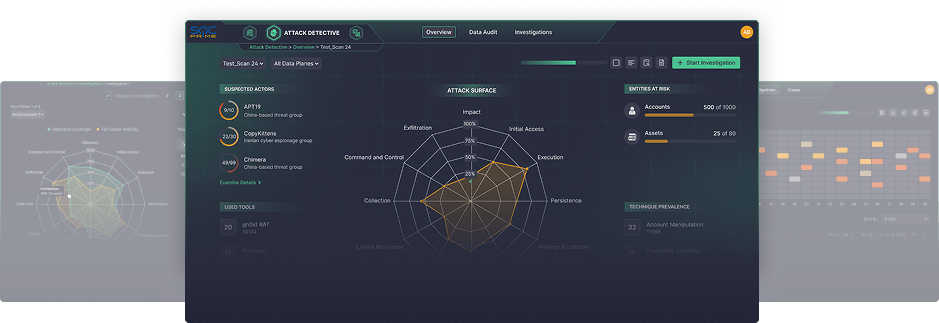
Run Data Audit
- Audit your ATT&CK coverage
- Identify blind spots to start logging what matters
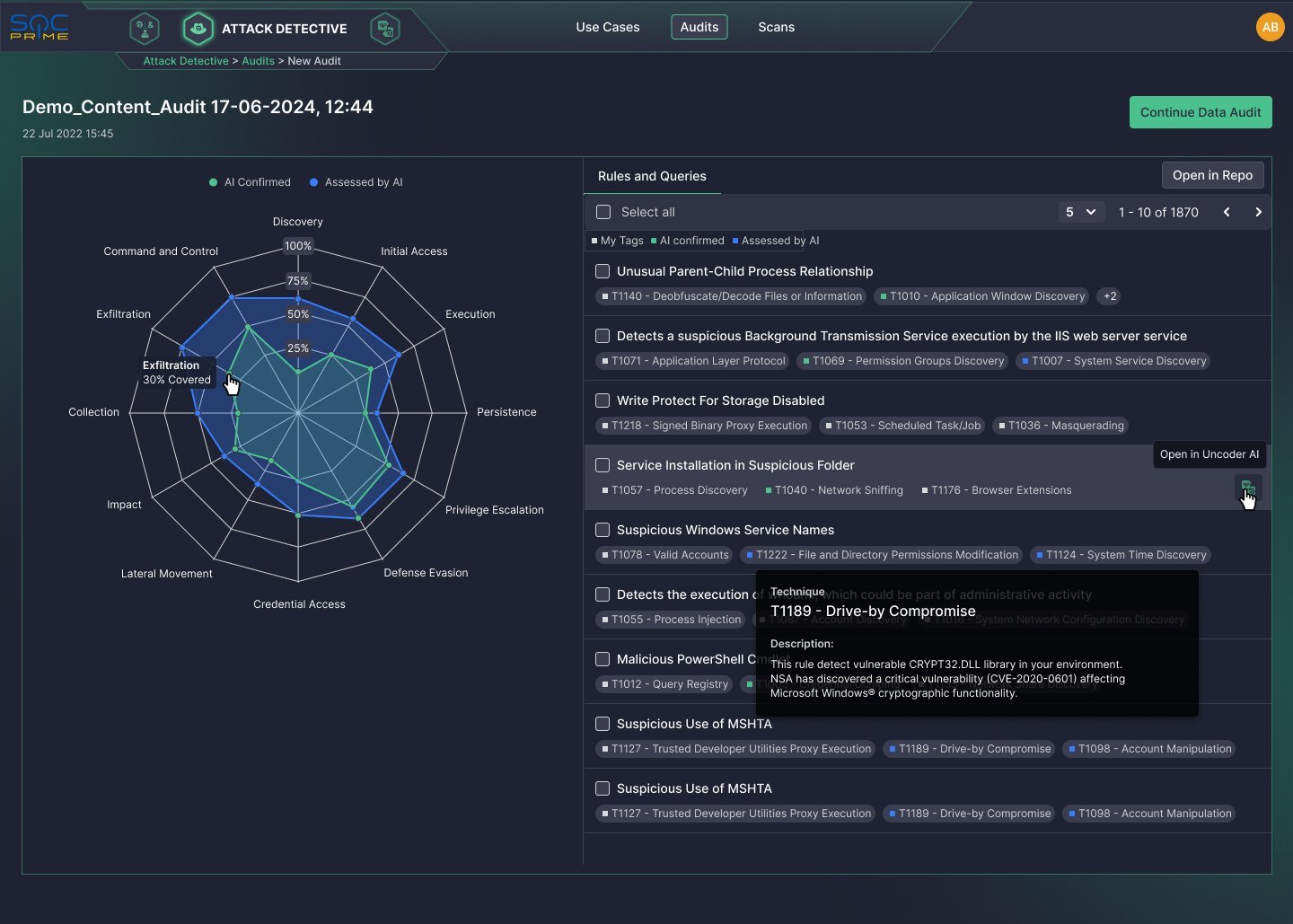
Audit Your Content
- Improve threat visibility by auto-mapping your rules & queries to MITRE ATT&CK
- Use AI that does not leak your code
Search for Threats Automatically
- Automate threat search across your connected environments, correlating findings with ATT&CK
- Run predefined scenarios to find widespread threats or validate your ad-hoc hypotheses using ready-made queries


OVER 12
Vendor Integrations
- Founded the Detection-as-Code industry in 2015
- Partnered with Fortune 100 + global MDRs
- Covering full pipeline from detection to simulation
- Magic threat search instead of filters
- 750,000+ detection rules
- Daily new threats
- Line-Speed ETL Detection
- Shift-Left Detection, Done Right
Frequently Asked Questions
What is Attack Detective, and what problems does it solve for threat detection?
Attack Detective is SOC Prime’s SaaS for advanced threat hunting that helps teams automatically validate their detection stack, get real-time attack surface visibility, investigate risks using custom hunting scenarios, and prioritize detection procedures to find breaches earlier.
It targets common SOC pain points like blind spots from incomplete/fragmented visibility, overwhelming data volumes, and the difficulty of scaling manual hunting and validation.
Does Attack Detective support SIEM/EDR/XDR tools across both on-prem and multi-cloud environments?
Yes. SOC Prime states Attack Detective works “no matter your cloud or on-premises security solution,” connecting SIEM/EDR/XDR tech in one place and consolidating data across on-premises and multi-cloud environments.
It supports environments like Amazon Security Lake, Amazon Athena, AWS OpenSearch, Microsoft Sentinel, Microsoft Defender for Endpoint, Splunk Cloud, and Elastic Cloud. SOC Prime also provides a Splunkbase app that supports scanning/validating via a Splunk instance (commonly used on-prem).
How can Attack Detective increase detection coverage?
Attack Detective increases coverage by measuring what you can actually detect with your current data and then guiding you to close gaps:
– It runs an automated, read-only MITRE ATT&CK data audit to identify blind spots in log source coverage and help you track coverage mapped to ATT&CK.
– It helps you launch scans aligned to your available log sources and platform, using prioritized detection content / Sigma rules, then maps outcomes to ATT&CK techniques and affected assets/accounts so teams can validate results in their SIEM/EDR and prioritize what to operationalize.
How does Attack Detective validate my detection stack and improve visibility across environments?
Attack Detective validates your detection stack by safely exercising real attacker behaviors and verifying that the right telemetry, alerts, and workflows trigger end-to-end across your SIEM, EDR, cloud controls, and detection rules. This confirms what actually fires in production (not just in theory) and quickly exposes gaps caused by missing logs, misconfigurations, parsing issues, or broken pipelines.
It improves visibility by unifying results across cloud, endpoint, identity, network, and hybrid environments and mapping them to attacker techniques, so you can clearly see what’s covered, what’s partial, and what’s missing. The output is actionable: prioritized blind spots, concrete fixes (data to enable, rules to tune, logic to add), and continuous re-validation so coverage stays strong as your environment changes.
